Web Application Firewall protection for VPN virtual servers and authentication virtual servers
Starting from NetScaler release 14.1 build 21.57, you can protect the NetScaler Gateway virtual servers, traffic management virtual servers, and authentication virtual servers against malicious attacks by applying Web Application Firewall protection. This functionality provides an additional layer of security to your deployments as it filters incoming requests by validating them using the API schema and then authenticates users to access applications.
When Web Application Firewall protection is enabled, NetScaler leverages the built-in Web Application Firewall profiles ns-aaatm-default-appfw-profile, ns-aaa-default-appfw-profile, and ns-vpn-default-appfw-profile. The profiles contain the associated built-in API specification files ns-aaatm-spec, ns-aaa-spec, and ns-vpn-spec to ensure that network traffic is secure and compliant with the API specifications.
Note:
We recommend that you always upgrade to the latest software version as it contains the latest security fixes.
Licensing requirements
This feature is available with all the licenses (Standard, Enterprise, and Premium).
Configure Web Application Firewall protection
On the GUI
To configure Web Application Firewall protection to the virtual servers:
- Navigate to Security > AAA- Application Traffic > Change Authentication Settings.
-
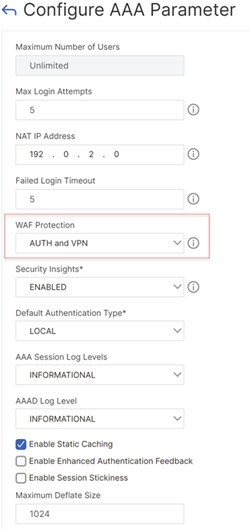
On the Configure AAA Parameter page, configure WAF Protection.
The following options are supported:
-
Disabled - When selected, Web Application Firewall protection is not applied to any virtual server. By default, Web Application Firewall protection is not set to any value.
-
AUTH – Protects the authentication virtual server.
-
VPN – Protects the VPN virtual server.
-
AUTH and VPN – Protects the authentication, traffic management, and VPN virtual servers.
-
- Click OK.
On the CLI
Run the following command to enable Web Application Firewall protection to the virtual servers:
set aaa parameter -wafProtection <DISABLED/AUTH/VPN>
Examples:
The following is an example of Web Application Firewall protection for the authentication virtual servers:
-
The
set aaa parameter -wafProtection AUTHcommand protects the authentication virtual servers. -
The
set aaa parameter -wafProtection VPNcommand protects the VPN virtual servers. -
The
set aaa parameter -wafProtection AUTH VPNcommand protects the authentication, VPN, and traffic management virtual servers.
Configure security insights
To view the violations detected by the built-in Web Application Firewall profiles, configure security insights. When configured, NetScaler sends the insight records to the AppFlow collector (configured in the analytics profile) whenever a request is sent to a virtual server. The security insight records are sent to the AppFlow collector.
Notes:
Before you configure the security insights, as a pre-requisite, ensure that the ULFD mode and AppFlow feature are enabled. On the GUI, you can perform this step by navigating to System > Settings > Modes and Features. On the CLI, you can use the commands
en ns mode ULFDanden ns feature appflow.Ensure that your NetScaler instances are added in NetScaler Console. For details, see Instance management.
On the GUI
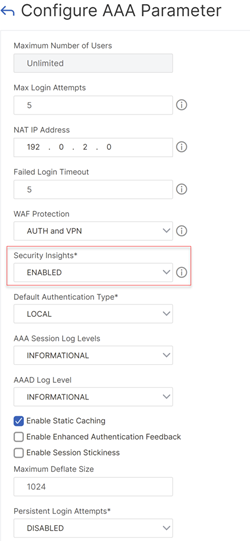
On the Configure AAA Parameter page, enable the Security Insights option. This parameter is disabled, by default.
On the CLI
Run the following command to enable security insights for debug logging. This parameter is disabled, by default.
set aaa parameter -securityInsights <ENABLED/DISABLED>
Configure AppFlow collector and analytics profile on the GUI
-
Navigate to System > Settings. In the Modes and Features section and enable the ULFD mode and the AppFlow feature.
-
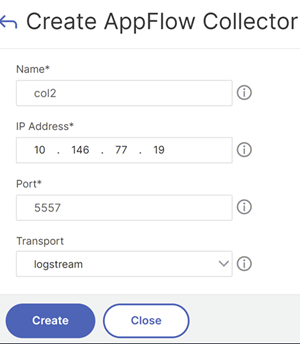
Configure an AppFlow collector.
- Navigate to Configuration > System > AppFlow > AppFlow Collectors. Configure the required parameters and click Create.
-
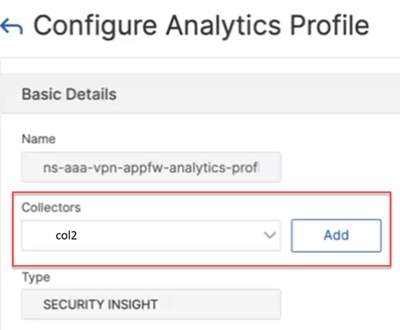
Set the configured AppFlow collector to the analytics profile. In this example, the AppFlow collector is set to the built-in analytics profile
ns-aaa-vpn-appfw-analytics-profile.- Navigate to Configuration > System > Profiles > Analytics Profiles. In the Basic details section, select the AppFlow collector on the Collectors field.
Configure AppFlow collector and analytics profile on the CLI
- add appflow collector col2 -IPAddress 10.146.77.19 -port 5557 -Transport logstream
- set analytics profile ns-aaa-vpn-appfw-analytics-profile -collectors col2 -type securityinsight
<!--NeedCopy-->
For more information about the AppFlow configuration, see Configuring the AppFlow feature.
Note:
Security insights for this feature work only with Logstream messages. They do not work with IPFIX messages.
View the AppFlow records on NetScaler Console
-
On the NetScaler Console on-prem GUI, navigate to Security > Security Violations. In the WAF section, select the VPN or the authentication virtual server. For more details, see View application security violation details.
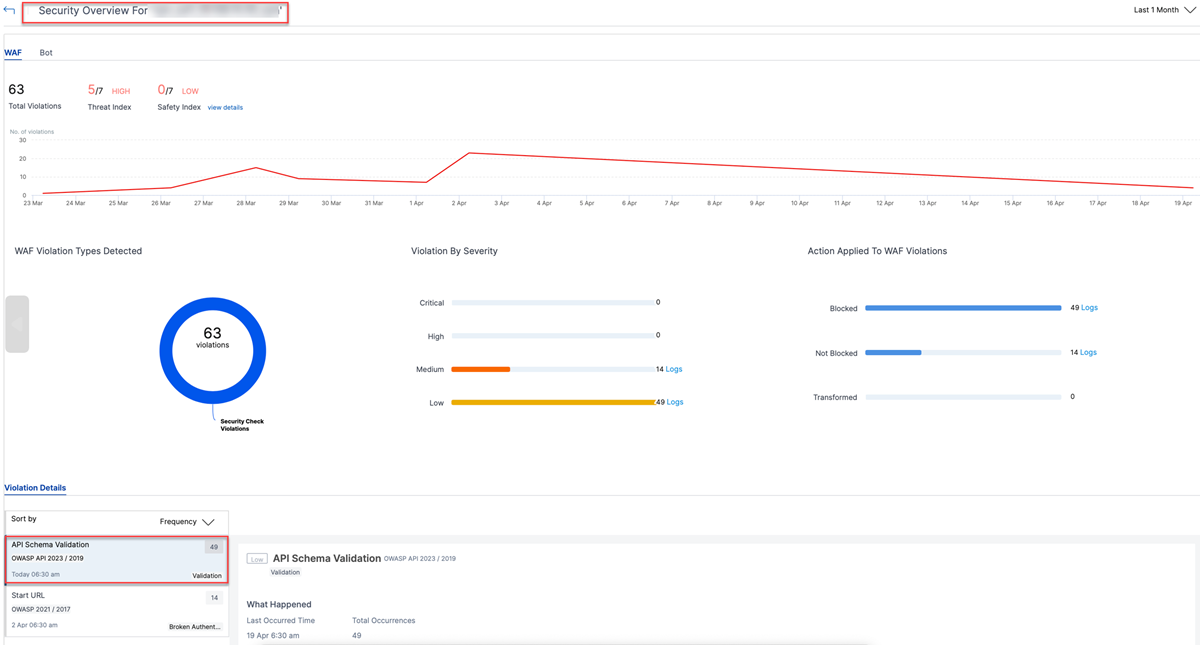
For a detailed view, select the URL in the Request URL field.
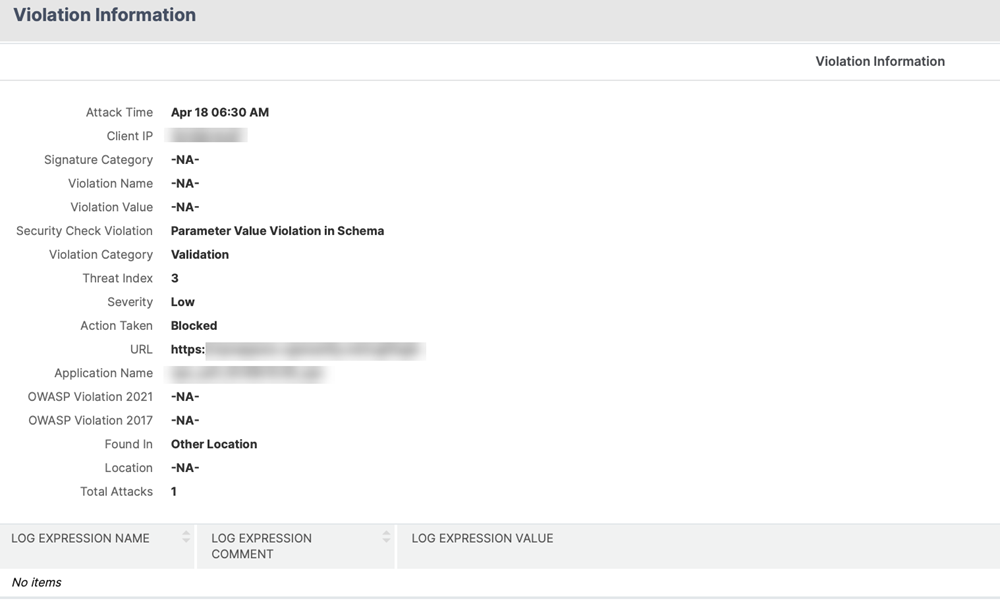
-
Apply the appropriate licenses to your VPN or authentication virtual server.
-
Verify if your virtual server is licensed.
-
In Settings > Analytics configuration section of the NetScaler Console GUI, select your virtual server and apply the licenses. For more details, see Manage licensing and enable analytics on virtual servers.
Note:
This step is required only if you are using NetScaler Console on-prem versions 14.1-17.38 or prior.
-
Configure relaxation rules
You can configure a relaxation rule on the endpoint URLs or the virtual server IP addresses, to bypass certain traffic from being validated against the schema specified in the API specification file.
On the GUI
The following is an example of a REST validation relaxation that you can apply to the "GET:/oauth/idp/login" authentication endpoint URL:
-
Navigate to Security > NetScaler Web App Firewall > Profiles.
-
Select the profile
ns-aaa-default-appfw-profile. -
Under Advanced Settings, click Relaxation Rules.
-
Select the REST API schema validation checkbox.
-
Navigate to the beginning of the Relaxation Rules section and click Edit.
-
Click Add.
-
On the REST API Schema Validation Relaxation Rule page, update the required fields and click Create.
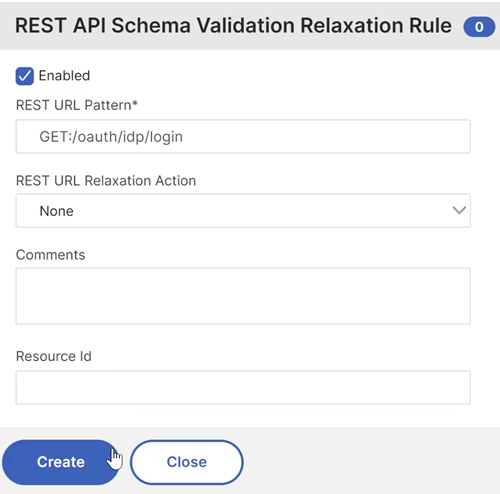
The following is an example of a relaxation that you can apply to a virtual server IP address:
-
Under Advanced Settings, select Profile Settings.
-
In the Common Settings section, select the Enable Bypass List checkbox.
-
Go back to the Advanced Settings section and select Global Bypass/Deny List.
-
In the Global Bypass List section, click Add.
-
On the Create AppFirewall Bypass List Binding page, update the required fields and click Create.
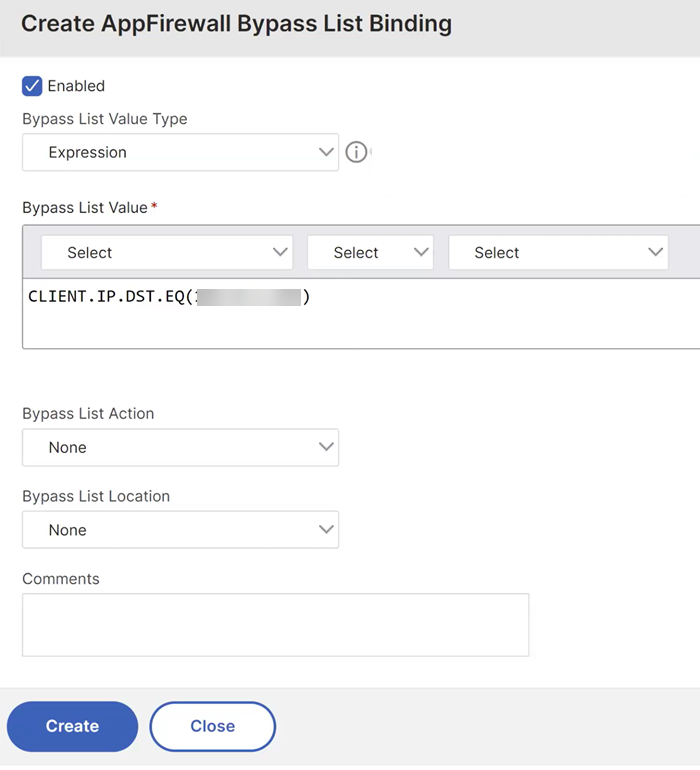
On the CLI
The following is an example of a REST validation relaxation that you can apply to the "GET:/oauth/idp/login" authentication endpoint URL:
bind appfwprofile ns-aaa-default-appfw-profile -restValidation "GET:/oauth/idp/login"
<!--NeedCopy-->
The following is an example of a relaxation that you can apply to a virtual server IP address:
set appfwprofile ns-aaa-default-appfw-profile -bypasslist on
bind appfwprofile ns-aaa-default-appfw-profile -bypasslist "CLIENT.IP.DST.EQ(192.0.2.255)" -valueType expression
<!--NeedCopy-->
For details about the configuration of relaxation rules, see Configure relaxation rule for API schema validation using CLI.
Debug logging
The following is a sample error message that appears in the ns.log file for user requests that NetScaler Web Application Firewall blocks:
Mar 22 07:04:26 <local0.info> 192.0.2.4 03/22/2024:07:04:26 GMT 0-PPE-0 : default APPFW APPFW_SCHEMA_VALUE_INCORRECT 864 0 : 10.106.31.93 107-PPE0 - ns-aaa-default-appfw-profile Parameter value incorrect as per API Spec: (ns-aaa-spec) for Endpoint: (GET https://192.0.2.5/oauth/idp/login?client_id=test&response_type=code&scope=openid%20profile&redirect_uri=https%3A%2F%2Foauthrp.aaa.local%2Foauth%2Flogin&state=Y3R4PU9tNzJ5WkNlTGJaSVhBb1lXM21ZVm40N0ZfQ1JzNjM1OGhvWEpRWkpDVFV1ZkY5U1hoOV9Edndfa282bHZ1ejBqQUFRU0hsbnBJTzF5U0NjbThQdVlqbm1Lb01ESHk5aFVVS19WR0xiaTgtVE9GaHRZZVBYWWJ3Q2F6d2JoZk5QX3hlY09BY2t1NHJUYlFqODZiaHhaZkU3RVdzJTNEA) <blocked>
In the preceding example, the profile name and endpoint URLs are specified to help users with the analysis and configure relaxation rules.
The following stat command displays the counters of the user requests blocked by the traffic management and authentication virtual servers:
stat aaa | grep -i blocked
Total AAA Waf blocked hits 0 15
Total AAATM Waf blocked hits 0 1
<!--NeedCopy-->
The following stat command displays the counters of API specification file:
stat apispec
API spec(s) Summary hits validate unmatched
ns-a...-spec 0 0 0
ns-aaa-spec 15 12 0
ns-vpn-spec 4 4 0
aaa 0 0 0
<!--NeedCopy-->
Dynamic update of the new API specification files provided by NetScaler
When the Web Application Firewall protection parameter is enabled, NetScaler uses the following built-in API specification files for API schema validation.
- ns-aaatm-spec: This file performs API schema validation of the incoming requests to the traffic management virtual servers.
- ns-aaa-spec: This file performs API schema validation of the incoming requests to the authentication virtual servers.
- ns-vpn-spec: This file performs API schema validation of the incoming requests to the VPN virtual servers.
On the GUI, you can locate these files by navigating to Security > NetScaler Web App Firewall > Imports > API Spec Import.
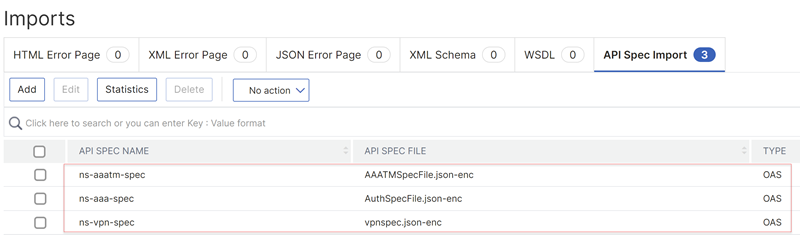
You can dynamically update the built-in API specification files by using the API specification files that NetScaler provides. Perform the following steps on the GUI:
-
Navigate to Security > NetScaler Web App Firewall > Imports > API Spec Import.
-
Select the API specification file and click Edit.
-
On the API Spec Import Object page, click File.
-
Upload the new API schema file and click Continue.
Notes:
- Do not rename API specification files that NetScaler provides.
- Ensure that the Encrypted checkbox is selected.
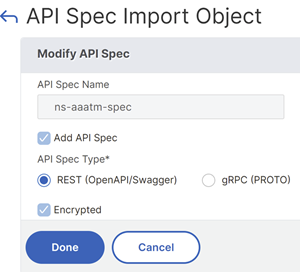
-
Click Done.
For more details about importing files, see Imports.
For details about the API specification validation, see API specification validation.
Limitation
This feature is currently applicable to traffic in the default partition.
References
-
For more information about the NetScaler Web Application Firewall feature, see Introduction to NetScaler Web Application Firewall.
-
For more information about the AppFlow feature, see AppFlow.
-
For FAQ details, see Authentication, Authorization, and Auditing.