Device policies
You can configure how XenMobile interacts with your devices by creating policies. Although many policies are common to all devices, each device has a set of policies specific to its operating system. As a result, you might find differences between platforms, and even between different manufacturers of Android devices.
For a summary description of each device policy, see Device policy summaries in this article.
Note:
If your environment is configured with Group Policy Objects (GPOs):
When you configure XenMobile device policies for Windows 10 and Windows 11 devices, keep the following rules in mind. If a policy on one or more enrolled devices conflicts, the policy aligned with the GPO takes precedence.
To see which policies the Android Enterprise container supports, see Android Enterprise.
Prerequisites
- Create any delivery groups that you plan to use.
- Install any necessary CA certificates.
Add a device policy
The basic steps to create a device policy are as follows:
- Name and describe the policy.
- Configure the policy for one or more platforms.
- Create deployment rules (optional).
- Assign the policy to delivery groups.
- Configure the deployment schedule (optional).
To create and manage device policies, go to Configure > Device Policies.
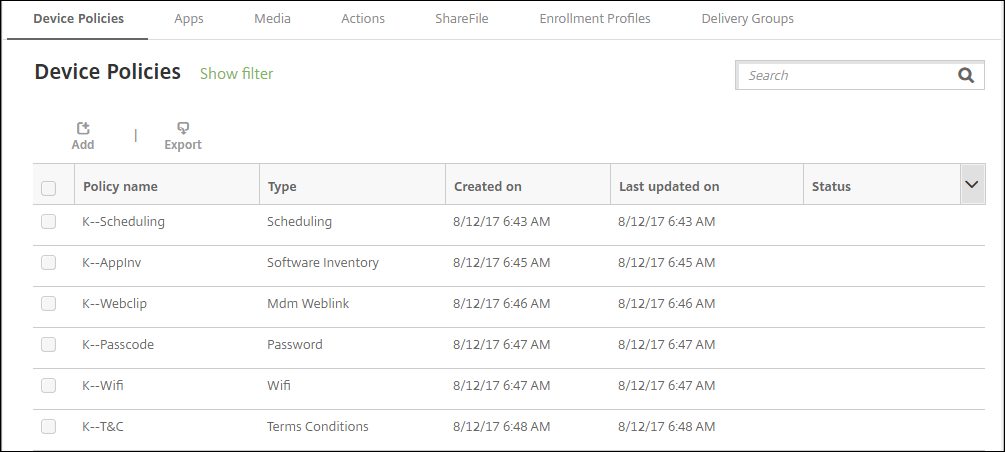
To add a policy:
-
On the Device Policies page, click Add. The Add a New Policy page appears.
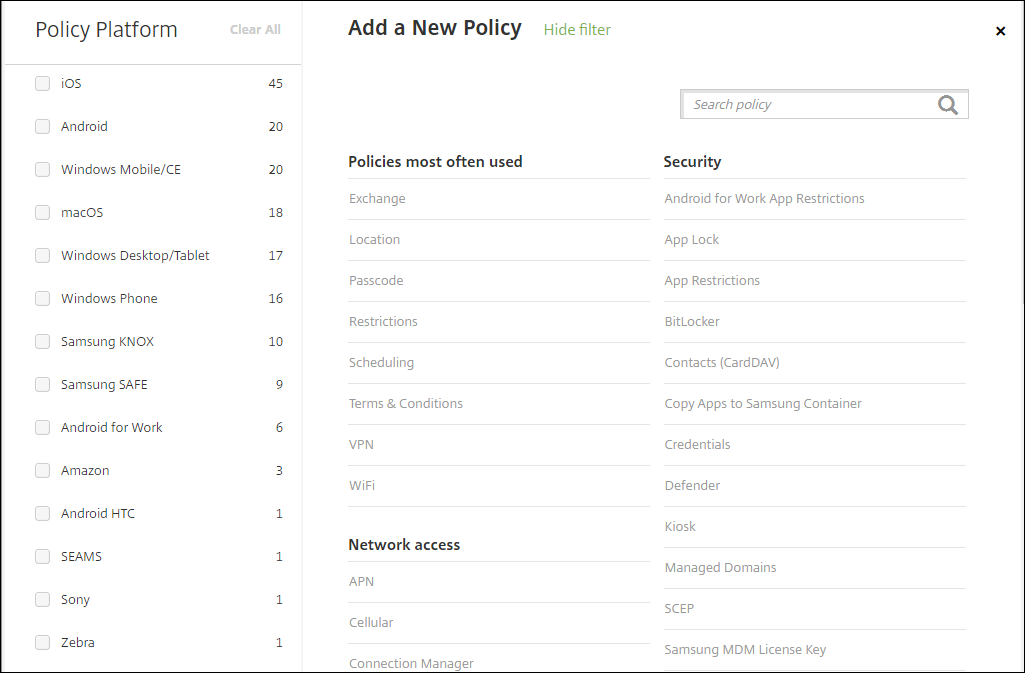
-
Click one or more platforms to view a list of the device policies for the selected platforms. Click a policy name to continue with adding the policy.
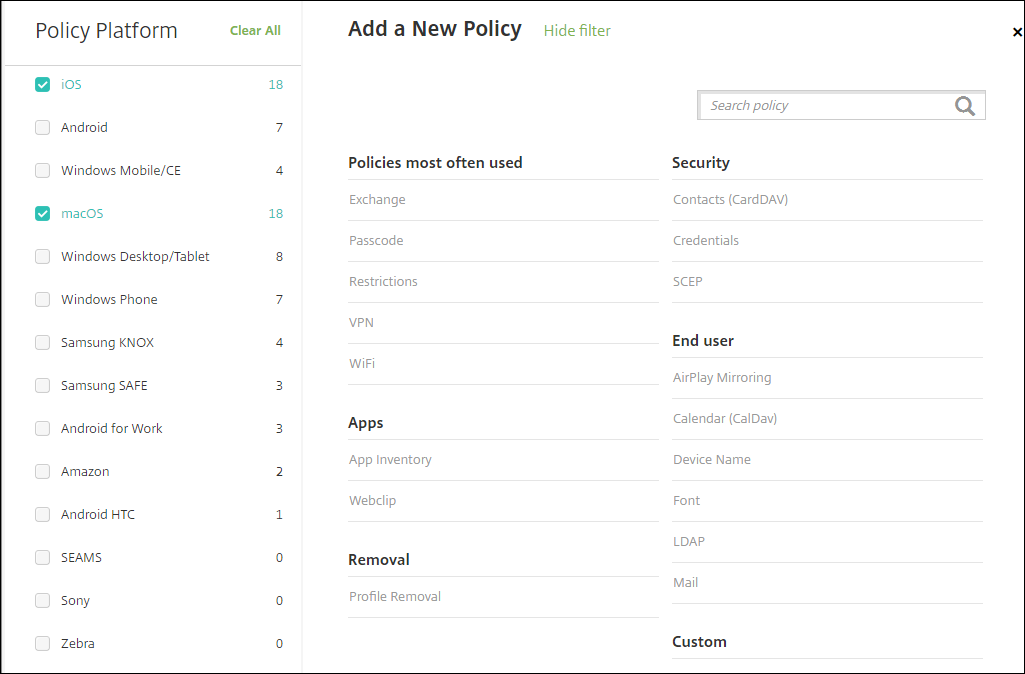
You can also type the name of the policy in the search box. As you type, potential matches appear. If your policy is in the list, click it. Only your selected policy remains in the results. Click it to open the Policy Information page for that policy.
-
Select the platforms that you want to include in the policy. Configuration pages for the selected platforms appear in Step 5.
-
Complete the Policy Information page and then click Next. The Policy Information page collects information, such as the policy name, to help you identify and track your policies. This page is similar for all policies.
-
Complete the platform pages. Platform pages appear for each platform you selected in Step 3. These pages are different for each policy. A policy might differ among platforms. Not all policies apply to all platforms.
Some pages include tables of items. To delete an existing item, hover over the line containing the listing and click the trash can icon on the right side. In the confirmation dialog, click Delete.
To edit an existing item, hover over the line containing the listing and click the pen icon on the right side.
To configure deployment rules, assignments, and schedule
For more information about configuring deployment rules, see Deploy resources.
-
On a platform page, expand Deployment Rules and then configure the following settings. The Base tab appears by default.
- In the lists, click options to determine when the policy should be deployed. You can choose to deploy the policy when all conditions are met or when any conditions are met. The default option is set to All.
- Click New Rule to define the conditions.
- In the lists, click the conditions, such as Device ownership and BYOD.
- Click New Rule again if you want to add more conditions. You can add as many conditions as you would like.
-
Click the Advanced tab to combine the rules with Boolean options. The conditions you chose on the Base tab appear.
-
You can use more advanced Boolean logic to combine, edit, or add rules.
- Click AND, OR, or NOT.
-
In the lists, choose the conditions that you want to add to the rule. Then, click the Plus sign (+) on the right side to add the condition to the rule.
At any time, you can click to select a condition and then click EDIT to change the condition or Delete to remove the condition.
- Click New Rule to add another condition.
-
Click Next to move to the next platform page or, when all the platform pages are complete, to the Assignments page.
-
On the Assignments page, select the delivery groups to which you want to apply the policy. If you click a delivery group, the group appears in the Delivery groups to receive app assignment box.
Delivery groups to receive app assignment doesn’t appear until you select a delivery group.
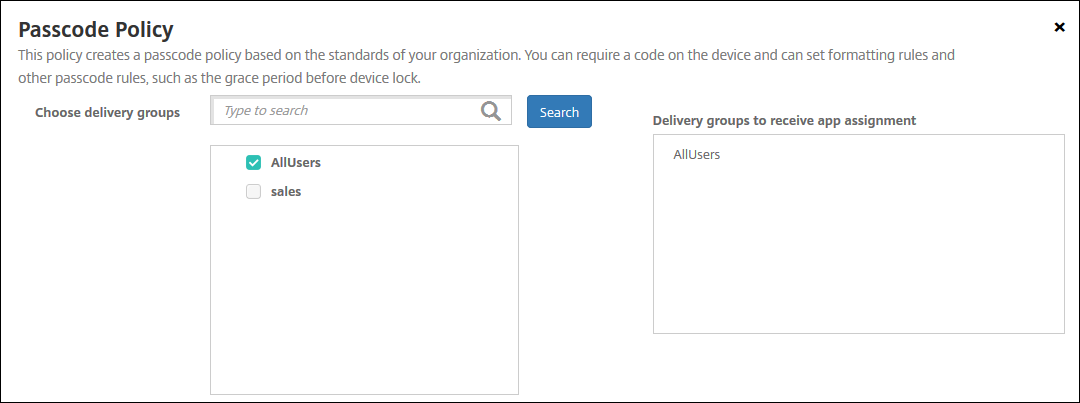
-
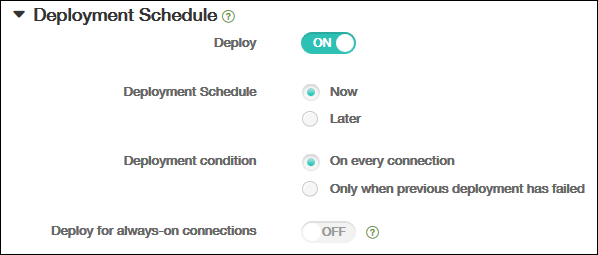
On the Assignments page, expand Deployment Schedule and then configure the following settings:
- Next to Deploy, click On to schedule deployment or click Off to prevent deployment. The default option is set to On.
- Next to Deployment schedule, click Now or Later. The default option is set to Now.
- If you click Later, click the calendar icon and then select the date and time for deployment.
- Next to Deployment condition, click On every connection or click Only when previous deployment has failed. The default option is set to On every connection.
-
Next to Deploy for always-on connection, click On or Off. The default option is set to Off.
Note:
This option applies when you have configured the scheduling background deployment key in Settings > Server Properties. The always-on option is not available for iOS devices.
The deployment schedule that you configure is the same for all platforms. Any changes you make apply to all platforms, except for Deploy for always on connection, which does not apply to iOS.
-
Click Save.
The policy appears in the Device Policies table.
Remove a device policy from a device
The steps to remove a device policy from a device depends on the platform.
-
Android
To remove a device policy from an Android device, use the XenMobile uninstall device policy. For more information, see the XenMobile uninstall device policy.
-
iOS and macOS
To remove a device policy from an iOS or macOS device, use the Profile Removal device policy. On iOS and macOS devices, all policies are part of the MDM profile. Thus, you can create a Profile Removal device policy for just the policy that you want to remove. The rest of the policies and the profile remain on the device. For information, see Profile Removal device policy.
-
Windows 10 and Windows 11
You can’t directly remove a device policy from a Windows Desktop or Tablet device. However, you can use either of the following methods:
-
Unenroll the device and then push a new set of policies to the device. Users then re-enroll to continue.
-
Push a security action to selectively wipe the specific device. That action removes all corporate apps and data from the device. You then remove the device policy from a delivery group that contains just that device and push the delivery group to the device. Users then re-enroll to continue.
-
-
Chrome OS
To remove a device policy from a Chrome OS device, you can remove the device policy from a delivery group that contains just that device. You then push the delivery group to the device.
Edit a device policy
To edit a policy, select the checkbox next to a policy to show the options menu above the policy list. Or, click a policy in the list to show the options menu to the right of the listing.
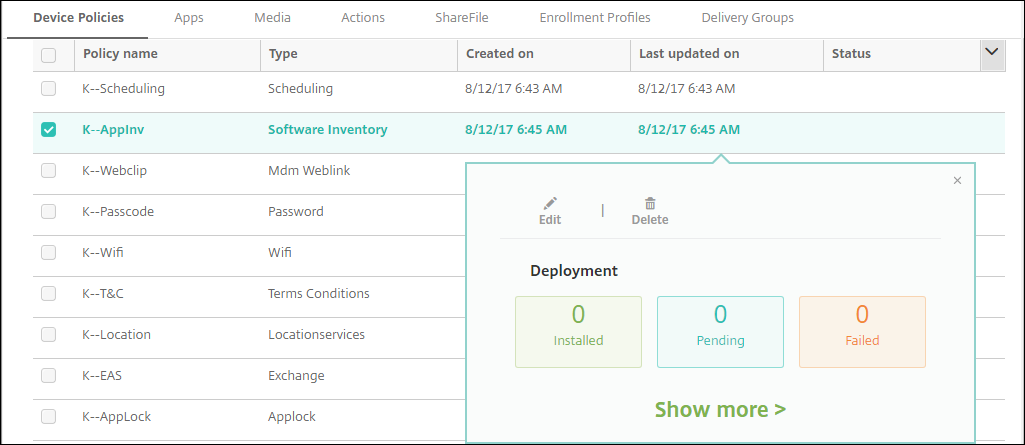
To view policy details, click Show more.
To edit all settings for a device policy, click Edit.
If you click Delete, a confirmation dialog box appears. Click Delete again to delete the policy.
Check policy deployment status
Click a policy row on the Configure > Device Policies page to check its deployment status.
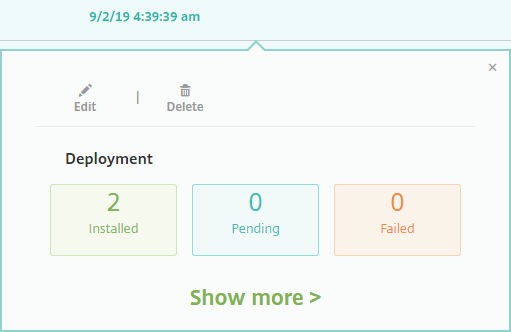
When a policy deployment is pending, users can refresh the policy from Secure Hub by tapping Preferences > Device Information > Refresh policy.
Filter the list of added device policies
You can filter the list of added policies by policy types, platforms, and associated delivery groups. On the Configure > Device Policies page, click Show filter. In the list, select the checkboxes for the items you want to see.
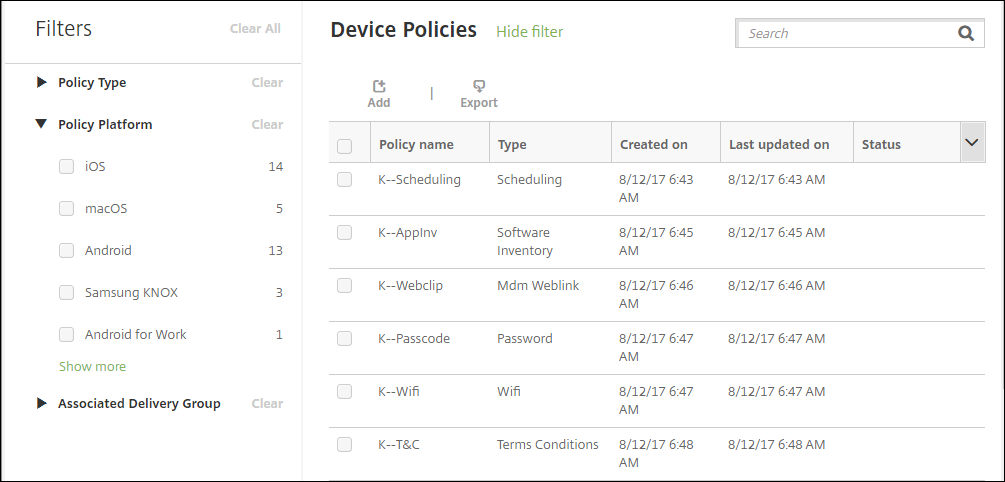
Click SAVE THIS VIEW to save a filter. The name of the filter then appears in a button below the SAVE THIS VIEW button.
Device policy summaries
| Device Policy Name | Device Policy Description |
|---|---|
| AirPlay Mirroring | Adds specific AirPlay devices (such as another Mac computer) to iOS devices. You also have the option of adding devices to an allow list for supervised devices. That option limits users to only the AirPlay devices on the allow list. |
| AirPrint | Adds AirPrint printers to the AirPrint printer list on iOS devices. This policy makes it easier to support environments where the printers and the devices are on different subnets. |
| Android Enterprise App Permissions | Configures how requests to Android Enterprise apps within work profiles handle what Google calls “dangerous” permissions. |
| Android Enterprise App Restrictions | Updates the restrictions associated with Android apps. |
| APN | Determines the settings used to connect your devices to the General Packet Radio Service (GPRS) of a specific phone carrier. This setting is already defined in most new phones. Use this policy if your organization doesn’t use a consumer APN to connect to the internet from a mobile device. |
| App Access | Defines a list of the apps that are required, optional, or prevented on the device. You can then create an automated action to react to the device compliance with that list of apps. |
| App Attributes | Specifies attributes, such as a managed app bundle ID or per-app VPN identifier, for iOS devices. |
| App Configuration | Remotely configures various settings and behaviors of apps that support managed configuration. To do that, you deploy an XML configuration file (called a property list, or plist) to iOS devices. Or, you deploy key/value pairs to Windows 10 phone, or desktop or tablet running Windows 10 or Windows 11 devices. |
| App Inventory | Collects an inventory of the apps on managed devices. XenMobile then compares the inventory to any app access policies deployed to those devices. In this way, you can detect apps that are on an app access allow or block list and then act correctly. |
| App Lock | Defines a list of apps that users either can or can’t run on iOS or certain Android devices. |
| App Network Usage | Sets network usage rules to specify how managed apps use networks, such as cellular data networks, on iOS devices. The rules only apply to managed apps. Managed apps are apps that you deploy to user devices through XenMobile. |
| App Uninstall | Remove apps from user devices. |
| Apps Notifications | Controls how iOS users receive notifications from specified apps. |
| Automatically update managed apps | Controls how installed managed apps are updated on Android Enterprise devices. |
| BitLocker | Configures the settings available in the BitLocker interface on Windows 10 and Windows 11 devices. |
| Calendar (CalDav) | Adds a calendar (CalDAV) account to iOS or macOS devices. The CalDAV account enables users to synchronize scheduling data with any server that supports CalDAV. |
| Cellular | Configures cellular network settings. |
| Connection Manager | Specifies the connection settings for apps that connect automatically to the internet and to private networks. This policy is only available on Windows Pocket PCs. |
| Contacts (CardDAV) | Adds an iOS contact (CardDAV) account to iOS or macOS devices. The CardDAV account enables users to synchronize contact data with any server that supports CardDAV. |
| Control OS Updates | Deploys the latest OS updates to supported, supervised devices. |
| Credentials | Enables integrated authentication with your PKI configuration in XenMobile. For example, with a PKI entity, a keystore, a credential provider, or a server certificate. |
| Custom XML | Customizes features such as device provisioning, device feature enablement, device configuration, and fault management. |
| Defender | Configures Windows Defender settings for Windows 10 and Windows 11 desktops and tablets. |
| Device Health Attestation | Requires that Windows 10 and Windows 11 devices report the state of their health. To do that they send specific data and runtime information to the Health Attestation Service (HAS) for analysis. The HAS creates and returns a Health Attestation Certificate that the device then sends to XenMobile. When XenMobile receives the Health Attestation Certificate, based on the contents of that certificate, it can deploy automatic actions that you configured. |
| Device Name | Sets the names on iOS and macOS devices so that you can identify the devices. You can use macros, text, or a combination of both to define a device name. |
| Education Configuration | Configures instructor and student devices for use with Apple Education. If instructors use the Classroom app, the Education Configuration device policy is required. |
| Exchange | Enables ActiveSync email for the native email client on the device. |
| Files | Adds script files to XenMobile that perform certain functions for users. Or, you can add document files that you want Android device users to be able to access on their devices. When you add the file, you can also specify the directory in which you want the file to be stored on the device. |
| FileVault | This policy lets you enable FileVault device encryption on enrolled macOS devices. You can also control how many times a user can skip FileVault setup during login. Available for macOS 10.7 or later. |
| Font | Adds fonts to iOS and macOS devices. Fonts must be TrueType (.TTF) or OpenType (.OFT) fonts. XenMobile doesn’t support font collections (.TTC or .OTC). |
| Home screen layout | Specifies the layout of apps and folders for the iOS Home screen on iOS 9.3 and later supervised devices. |
| Import iOS & macOS Profile | Imports device configuration XML files for iOS and macOS devices into XenMobile. The file contains device security policies and restrictions that you prepare by using the Apple Configurator. |
| Keyguard Management | Controls the features available to users before they unlock the device keyguard and the work challenge keyguard. You can also control device keyguard features for fully managed and dedicated devices. For example, you can disable lock screen features such as fingerprint unlock, trust agents, and notifications. |
| Kiosk | Restricts app usage on Samsung SAFE devices. You can limit available apps to a specific app or apps. This policy is useful for corporate devices that are intended to run only a specific type or class of apps. This policy also lets you choose custom images for the device home screen and lock screen wallpapers for kiosk mode. |
| Knox Platform for Enterprise Key | Allows you to provide the required Samsung Knox Platform for Enterprise (KPE) license information. |
| Launcher Configuration | Specifies settings for Citrix Launcher on Android devices, such as the apps allowed and a custom logo image for the Launcher icon. |
| LDAP | Provides information about an LDAP server to use for iOS devices, including any necessary account information such as the LDAP server host name. The policy also provides a set of LDAP search policies to use when querying the LDAP server. |
| Location | Lets you geo-locate devices on a map, assuming that the device has GPS enabled for Secure Hub. After deploying this policy to the device, you can send a locate command from the XenMobile Server. The device then responds with its location coordinates. XenMobile also supports geofencing and tracking policies. |
| Configures an email account on iOS or macOS devices. | |
| Managed Domains | Defines managed domains that apply to email and the Safari browser. Managed domains help you protect corporate data by controlling which apps can open documents downloaded from domains using Safari. For iOS 8 and later supervised devices, you can specify URLs or subdomains to control how users can open documents, attachments, and downloads from the browser. |
| MDM Options | Manages Find My Phone and iPad Activation Lock on supervised iOS 7.0 and later phone devices. |
| Organization Info | Specifies organization information for alert messages that XenMobile deploys to iOS devices. |
| Passcode | Enforces a PIN code or password on a managed device. You can set the complexity and timeouts for the passcode on the device. |
| Personal Hotspot | Allows users to connect to the internet when they are not in range of a Wi-Fi network. Users connect through the cellular data connection on their iOS device, using personal hotspot functionality. |
| Profile Removal | Removes the app profile from iOS or macOS devices. |
| Provisioning Profile | Specifies an enterprise distribution provisioning profile to send to devices. When you develop and code sign an iOS enterprise app, you usually include a provisioning profile. Apple requires the profile for the app to run on an iOS device. If a provisioning profile is missing or has expired, the app crashes when a user taps to open it. |
| Provisioning Profile Removal | Removes iOS provisioning profiles. |
| Proxy | Specifies global HTTP proxy settings for devices running iOS. You can deploy only one global HTTP proxy policy per device. |
| Restrictions | Provides hundreds of options to lock down and control features and functionality on managed devices. Examples of restriction options: Disable the camera or microphone, enforce roaming rules, and enforce access to third-party services, such as app stores. |
| Roaming | Configures whether to allow voice and data roaming on iOS devices. If voice roaming is disabled, data roaming is automatically disabled. |
| Scheduling | Required for Android devices to connect back in to the XenMobile Server for MDM management, app push, and policy deployment. If you don’t send this policy to devices and don’t enable Google FCM, a device can’t connect back to the server. |
| SCEP | Configures iOS and macOS devices to retrieve a certificate from an external SCEP server. You can also deliver a certificate to the device using SCEP from a PKI that is connected to XenMobile. To do that, create a PKI entity and a PKI provider in distributed mode. |
| SSO Account | Creates single sign-on (SSO) accounts so users sign on one-time only to access XenMobile and your internal company resources. Users do not need to store any credentials on the device. XenMobile uses the enterprise user credentials for an SSO account across apps, including apps from the App Store. This policy is compatible with Kerberos authentication. Available for iOS. |
| Subscribed Calendars | Adds a subscribed calendar to the calendar list on iOS devices. Ensure that you subscribe to a calendar before you add it to the subscribed calendars list on user devices. |
| Terms and Conditions | Requires that users accept the specific policies of your company that govern connections to the corporate network. When users enroll their devices with XenMobile, they must accept the terms and conditions to enroll their devices. Declining the terms and conditions cancels the enrollment process. |
| Tunnel | Used only for Remote Support. Remote support enables your help desk representatives to take remote control of managed Windows CE and Android mobile devices. Remote support isn’t available for clustered on-premises XenMobile Server deployments. Remote Support is no longer available for new customers as of January 1, 2019. Existing customers can continue to use the product, however Citrix won’t provide enhancements or fixes. |
| VPN | Provides access to back end systems that use legacy VPN gateway technology. This policy provides VPN gateway connection details that you can deploy to devices. XenMobile supports several VPN providers, including Cisco AnyConnect, Juniper, and Citrix VPN. If your VPN gateway supports this option, you can link this policy to a CA and enable VPN on-demand. |
| Wallpaper | Adds a .png or .jpg file to set wallpaper on an iOS device lock screen, home screen, or both. To use different wallpapers on iPads and iPhones, create different wallpaper policies and deploy them to the appropriate users. |
| Web Content Filter | Filters web content on iOS devices. XenMobile uses the Apple auto-filter function and the sites that you add to allow and block lists. Available only for iOS supervised devices. |
| Webclip | Places shortcuts, or web clips, to websites so that they appear alongside apps on user devices. You can specify your own icons to represent the web clips for iOS, macOS, and Android devices. Windows tablet only requires a label and a URL. |
| Wi-Fi | Allows administrators to deploy Wi-Fi router details to managed devices. The router details include SSID, authentication data, and configuration data. |
| Windows Information Protection | Specifies the apps that require Windows Information Protection at the enforcement level you set for the policy. The policy is for Windows 10 and Windows 11 supervised devices. |
| XenMobile Store | Specifies whether a XenMobile Store web clip appears on the home screen of user devices. |
| XenMobile Options | Configures the Secure Hub behavior when connecting to XenMobile from Android devices. |
| XenMobile Uninstall | Uninstalls XenMobile from Android and Window Mobile/CE devices. When deployed, this policy removes XenMobile from all devices in the deployment group. |