This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Snort rule integration
With malicious attacks on web applications, it is important to protect your internal network. Malicious data not only affect your web applications at the interface level but malicious packets also reach the application layer. To overcome such attacks, it is important to configure an intrusion detection and prevention system that examines your internal network.
Snort rules are integrated into the appliance for examine malicious attacks in data packets at the application layer. You can download the snort rules and convert it into WAF signatures rules. The signatures have rule-based configuration that can detect malicious activities such as DOS attacks, buffer overflows, stealth port scans, CGI attacks, SMB probes, and OS Fingerprinting attempts. By integrating Snort rules, you can strengthen your security solution at the interface and at the application level.
Configure snort rules
The configuration begins by first downloading the Snort rules and then importing it into WAF signature rules. Once you have converted the rules into WAF signatures, the rules can be used as WAF security checks. The snort based signature rules examine the incoming data packet to detect if there are malicious attacks on your network.
A new parameter, “VendorType” is added to the import command to convert Snort rules to WAF signatures.
The parameter “VendorType” is set on SNORT only for Snort rules.
Download snort rules by using the command interface
You can download the Snort rules as a text file from the below URL:
https://www.snort.org/downloads/community/snort3-community-rules.tar.gz
Import snort rules by using the command interface
After you download, you can import the Snort rules into your appliance.
At the command prompt, type:
import appfw signatures <src> <name> [-xslt <string>] [-comment <string>] [-overwrite] [-merge [-preservedefactions]] [-sha1 <string>] [-VendorType Snort]
Example:
import appfw signatures http://www.example.com/ns/signatures.xml sig-snort –comment “signatures from snort rules” –VendorType snort
Arguments:
Src. URL (protocol, host, path, and file name) for the location at which to store the imported signatures object.
Note:
The import fails if the object to be imported is on an HTTPS server that requires client certificate authentication for access. Mandatory argument of maximum length: 2047
Name. Name to assign to the signatures object on the NetScaler. Mandatory argument of maximum length: 31
Comment. Description of how to preserve information about the signatures object. Maximum Length: 255 overwrite. Overwrite any existing signatures object of the same name.
Merge. Merges existing Signature with new signature rules.
Preservedefactions. Preserves def actions of signature rules.
VendorType. Third-party vendor to generate the WAF signatures. Possible values: Snort.
Configure snort rules by using the NetScaler GUI
The GUI configuration for Snort rules is similar to configuring other external web application scanners like Cenzic, Qualys, Whitehat.
Follow the steps below to configure Snort:
- Navigate to Configuration > Security > NetScaler Web App Firewall > Signatures.
- In the Signatures page, click Add.
-
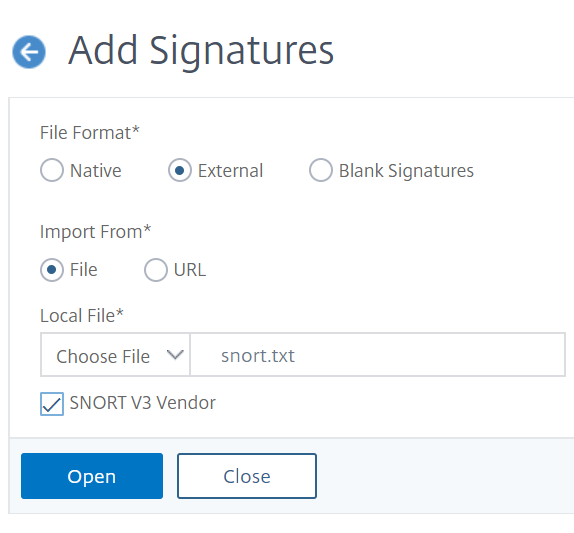
In the Add Signatures page, set the following parameters to configure Snort rules.
- File format. Select the file format as external.
- Import from. Select the import option as a snort file or URL to enter the URL.
- Snort V3 Vendor. Select the check box to import Snort rules from a file or from a URL.
-
Click Open.
The appliance imports the Snort rules as snort-based WAF signature rules.
As a best practice, you must use filter actions to enable snort rules that you prefer to import as WAF signature rules on the appliance.
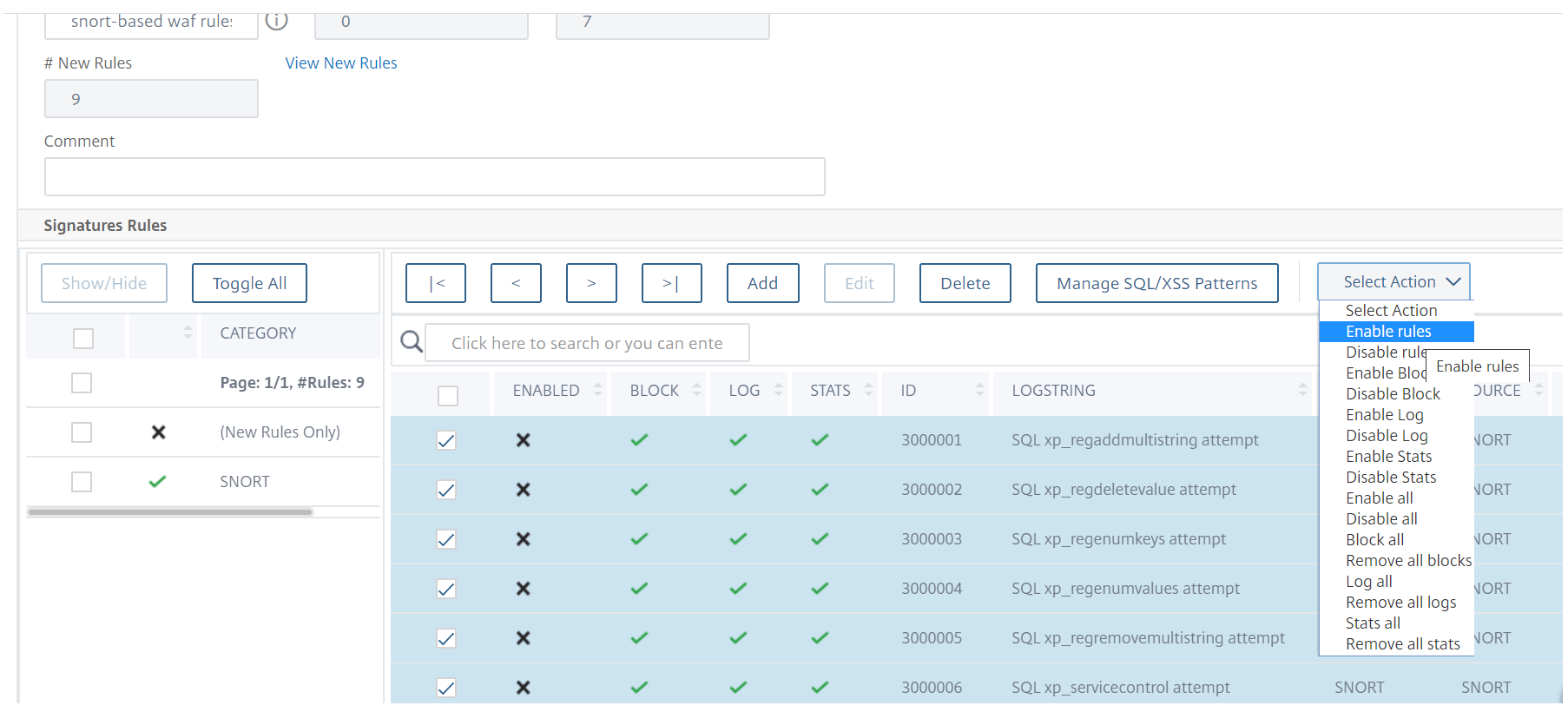
-
To confirm, click Yes.
-
The selected rules are enabled on the appliance.
- Click OK.
In this article
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.