This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Deny URL check
The Deny URL check examines and blocks connections to URLs that are commonly accessed by hackers and malicious code. This check contains a list of URLs that are common targets of hackers or malicious code and that rarely if ever appear in legitimate requests. You can also add URLs or URL patterns to the list. The Deny URL check prevents attacks against various security weaknesses known to exist in web server software or on many websites.
The Deny URL check takes priority over the Start URL check, and thus denies malicious connection attempts even when a Start URL relaxation would normally allow a request to proceed.
In the Modify Deny URL Check dialog box, on the General tab you can enable or disable the Block, Log, and Statistics actions.
If you use the command-line interface, you can enter the following command to configure the Deny URL Check:
set appfw profile <name> -denyURLAction [**block**] [**log**] [**stats**] [**none**]
<!--NeedCopy-->
You can create and configure your own deny URLs only in the NetScaler GUI.
- Navigate to Security > NetScaler Web App Firewall > Profiles.
- Select a profile for which you want to add a deny URL and click Edit.
- In the NetScaler Web App Firewall Profile page, select Relaxation Rules from the Advanced Settings section.
- Select Deny URL and click Edit.
- In the Deny URL Rules page, click Add.
-
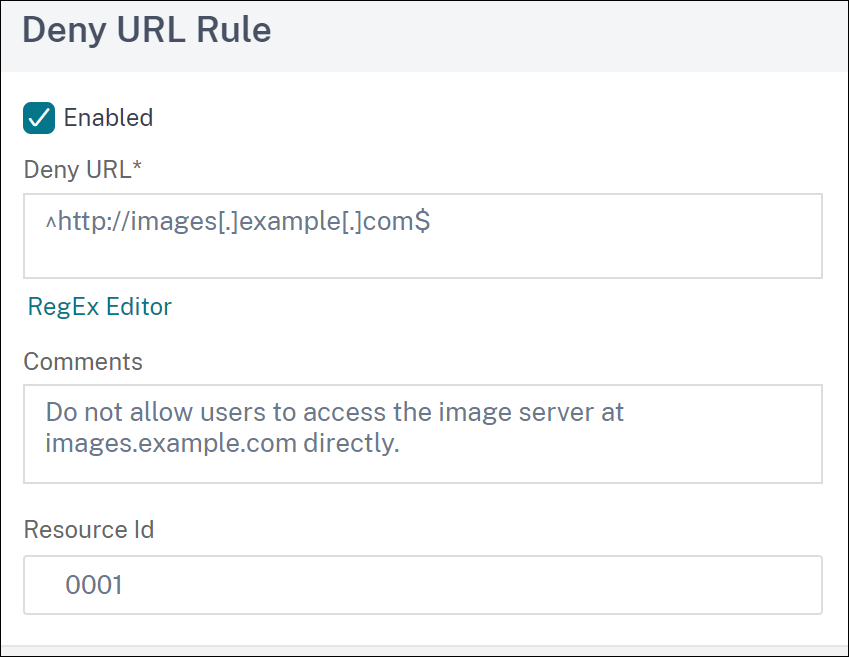
Specify the following details and click Create.
- Deny URL - A regular expression to define a deny URL.
- Comments - Description for the expression.
- Resource ID - Unique ID to identify the deny URL rule.
- Click Close.
- In the NetScaler Web App Firewall Profile page, click Done.
Following are examples of Deny URL expressions:
-
Do not allow users to access the image server at images.example.com directly:
^http://images[.]example[.]com$ <!--NeedCopy--> -
Do not allow users to access CGI (.cgi) or PERL (.pl) scripts directly:
^http://www[.]example[.]com/([0-9A-Za-z][0-9A-Za-z_-]*/)* [0-9A-Za-z][0-9A-Za-z_.-]*[.](cgi|pl)$ <!--NeedCopy--> -
Here is the same deny URL, modified to support non-ASCII characters:
^http://www[.]example[.]com/(([0-9A-Za-z]|x[0-9A-Fa-f][0-9A-Fa-f]) ([0-9A-Za-z_-]|x[0-9A-Fa-f][0-9A-Fa-f])*/)*([0-9A-Za-z]|x[0-9A-Fa-f][0-9A-Fa-f]) ([0-9A-Za-z_-]|x[0-9A-Fa-f][0-9A-Fa-f])*[.](cgi|pl)$ <!--NeedCopy-->
Caution:
Regular expressions are powerful. Especially if you are not thoroughly familiar with PCRE-format regular expressions, double-check any regular expressions you write. Make sure that they define exactly the URL or pattern that you want to block, and nothing else. Careless use of wildcards, and especially of the dot-asterisk (.*) metacharacter/wildcard combination, can have results that you do not want, such as blocking access to web content that you did not intend to block.
Share
Share
In this article
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.