What’s new
Notice about Syslog feature deprecation
We have paused the Syslog deprecation. We will continue supporting this feature until further notice.
April 10, 2024
Analytics
Observability Integration - Support to configure the export of NetScaler metrics and Audit logs to Splunk
In Settings > Observability Integration, you can now configure the export of NetScaler Metrics and Audit logs to Splunk.
For more information, see Configure the export of NetScaler metrics and audit logs to Splunk.
[ NSADM-108858 ]
Infrastructure
Access NetScaler GUI through host name
When you connect to NetScaler through Infrastructure > Instances > NetScaler, clicking on the host name now establishes the connection to the NetScaler GUI through the host name. Previously, clicking on either the host name or the IP address initiated the connection to the NetScaler GUI through the NSIP.
[ NSADM-108790 ]
View discrepancies between high-availability nodes during upgrade
You can now view configuration discrepancies between the primary node and the secondary node while upgrading the NetScaler high-availability deployment. You can review the discrepancies and decide to continue or halt the upgrade. To use this feature, navigate to Infrastructure > Upgrade Jobs, and view the discrepancies in the Pre-upgrade validation tab.
For more information, see Upgrade jobs .
[ NSADM-103826 ]
Fixed Issues
The issues that are addressed in Build April 10, 2024.
Infrastructure
-
The Infrastructure > Events > Syslog Messages page appears blank when the syslog messages contain special characters such as superscripts.
[ NSHELP-37551 ]
-
The count of used and unused certificates displayed in Infrastructure > SSL Dashboard > Usage is incorrect when the SSL certificates have certificate chains.
[ NSHELP-37469, NSADM-106867 ]
Licensing
-
The ports 27000 and 7279 required on agent for Pooled or Flexed licenses might become unavailable after the restart of agent processes. In such scenarios, the NetScaler instances using Pooled or Flexed licenses might go into grace period.
[ NSADM-110461 ]
Security
-
When you navigate to Security > WAF Recommendation, you might see the following error message:
“HTTP Error 500 ([object Object]) while accessing the data endpoint: “apps””
[ NSHELP-37598 ]
March 26, 2024
Fixed Issues
The issues that are addressed in Build March 26, 2024.
Infrastructure
-
While creating or updating an upgrade job, when you try to select an instance in Infrastructure > Upgrade Jobs > Create Job > Select Instance > Add Instances, the Add Instances page displays the Partitions tab which is not applicable to the workflow. If you select a partition, the page becomes unresponsive and you cannot proceed further.
[ NSADM-110118 ]
-
When you create Slack notifications in Settings > Notifications > Slack > Create Slack Notifications and select Notifications with attachment, the notifications do not get displayed and the following error message is seen:
Invalid token[ NSHELP-37313 ]
StyleBooks
-
When the Secure access only option is selected in Settings > Administration > System Configurations > Basic Settings and you try to perform any Device API Proxy operation, the operation fails.
[ NSHELP-37368 ]
March 12, 2024
Licensing
Support to manually select a NetScaler agent as LSA in NetScaler Console service
You can now manually select a NetScaler agent as a license server agent (LSA) for NetScaler Pooled licensing or NetScaler Flexed licensing.
When an LSA is down, the NetScaler Console service waits for 24 hours before auto-electing the next LSA. The admin can manually elect the new LSA in the interim by using this feature. However, the admin must ensure that the status of the new LSA being elected is UP and its diagnostic status is OK.
For more information, see NetScaler agent behavior for Flexed or Pooled licensing.
[ NSADM-105168 ]
Fixed Issues
The issues that are addressed in Build March 12, 2024.
Analytics
-
When you enable Gateway Insight for the Gateway virtual servers, the Analytics Status column in Settings > Analytics Configuration > All Virtual Servers shows Disabled.
[ NSHELP-37400 ]
-
In Gateway > Gateway Insight, the Authentication tab does not display user details for the failed authentications.
[ NSHELP-37465 ]
Infrastructure
-
When a user-defined policy is created and a user is added to that policy, GET API requests for specific resources encounter permission issues and the following error is displayed:
“Not authorized as required permissions were not given”
[ NSHELP-37331 ]
February 28, 2024
Infrastructure
Updates to VIP licensing and NetScaler Console Service storage
-
Unlimited VIPs on NetScaler Console service: Starting from NetScaler Console service release 14.1-21.x, the concept of licensed VIPs is removed. An unlimited number of VIPs are now available in NetScaler Console service. You no longer have to purchase NetScaler Console virtual server licenses because VIP license SKU will be End of Sale (EOS) & End of Renewal (EOR) shortly.
-
NetScaler Console service storage:
-
NetScaler Console service storage SKU will be End of Sale (EOS) & End of Renewal (EOR) shortly.
-
The default NetScaler Console service storage entitlement is now 5GB.
-
Any NetScaler Console service storage licenses purchased in the past are honoured until the term ends.
-
Any NetScaler Console VIP licenses purchased in the past that entitled you to a proportionate entitlement of NetScaler Console Service storage are honoured until the term ends.
-
If you purchase any other licensing package that entitles you to a higher NetScaler Console storage entitlement, the default 5GB is changed to match the entitlement.
-
[ NSADM-108300 ]
Updates to analytics and metrics collector
-
With unlimited VIPs support from 14.1 21.x build, all existing and new virtual servers are now automatically licensed. You can enable analytics on the virtual servers without explicitly licensing them.
-
Metrics collector is now disabled by default for all NetScaler license types in the new NetScaler instances added in NetScaler Console from 14.1 21.x build. The metrics collector configuration for the existing managed instances remain unchanged.
[ NSADM-108803 ]
Analytics
Action policies - Configure notifications for application usage
In Action Policies (Settings > Actions > Action Policies), you can now configure an action policy for Application Usage and select Requests per second, Throughput, and Data Volume options. These options enable you to configure and receive notifications for request per second average, request per second anomalies, throughput average, throughput anomalies, total data volume, and data volume anomalies. For more information, see Configure an action policy to receive application event notifications.
[ NSADM-104833 ]
Observability Integration
The configuration workflow for integration with Splunk and New Relic is now enhanced for better user experience and is available under Settings > Observability Integration. Earlier, the configuration workflow for integration with Splunk and New Relic was available under Settings > Ecosystem Integration.
For more information, see Observability Integration
[ NSADM-104702 ]
Observability Integration - Support to configure the export of NetScaler metrics to Prometheus
In Settings > Observability Integrations, you can now configure the export of NetScaler metrics to Prometheus by selecting the default schema.
For more information, see Prometheus Integration and Observability Integration.
[ NSADM-101426 ]
Gateway Insight - Improvements to export reports
In Gateway > Gateway Insight, you can now export report only with the selected options using the settings icon in all tables under each metric (EPA, Authentication, Authorization Failure, SSO, and Application Launch). Earlier, the exported report displayed all information regardless of the selected options.
[ NSADM-96821 ]
StyleBooks
Updates to Default StyleBooks
Default StyleBooks based on the NetScaler version 10.5 will be deprecated in upcoming releases. A new set of Default StyleBooks is now available in Applications > Configuration > StyleBooks > Default StyleBooks, based on NetScaler version 13.0.
[ NSADM-105513 ]
Option to clone a StyleBook
NetScaler Console now allows admins to create a duplicate of a StyleBook, along with their dependencies. Admins can then use this bundle for additional customization such as updating parameters and components.
To use this feature, navigate to Applications > Configuration > Stylebooks, select a default or custom StyleBook and click Clone.
For more information, see Clone a StyleBook.
[ NSADM-92376 ]
Fixed Issues
The issues that are addressed in Build Feb 28, 2024.
Infrastructure
-
Migration from NetScaler Console to NetScaler Console service fails and certain Azure Active Directory groups are not available in the NetScaler Console service. This issue occurs because of the presence of spaces in the Azure Active Directory group names created in NetScaler Console.
[ NSHELP-37006 ]
-
Users are unable to access NetScaler Console if they belong to multiple Azure Active Directory groups.
[ NSHELP-37005 ]
-
In Web Insight and Security Violations, the Schedule Export workflow in the GUI is enhanced for better user experience.
[ NSADM-106624 ]
-
In Infrastructure > Network Reporting, the tabular export report does not include details such as service, service group, virtual server, and interface name.
[ NSHELP-37224 ]
-
Flexed license dashboard displays NetScaler details only after at least one NetScaler is checked out from the Premium bandwidth license pool.
[ NSADM-106497 ]
February 06, 2024
Analytics
App dashboard - Support to view application metrics details from NetScaler admin partition
In App Dashboard, you can now view metric details for applications that are created from the NetScaler admin partitions. Earlier, you were able to only view applications from the admin partitions without any metrics.
[ NSADM-105343 ]
Infrastructure
NetScaler ADM rebranding in Citrix Cloud
Starting from 14.1 16.x build, NetScaler ADM service was rebranded to NetScaler Console service. In continuation, Application Delivery Management is now rebranded to NetScaler Console in the following places:
-
The tile under My Services in Citrix Cloud home page.
-
The service name in Citrix Cloud menu > My Services.
-
The product name in the Add administrator workflow in Set access > Custom Access from Citrix Cloud menu > Identity and Access Management > Administrators > Add administrator/group.
Run default validation scripts in upgrade jobs
NetScaler Console now includes an option for default validation scripts in the upgrade job workflow. These default scripts are run both before and after an upgrade job, generating a diff report. You still have the option to run custom default scripts.
For more information, see Upgrade NetScaler instances.
[ NSADM-100803 ]
Automate radar object deployment for NetScaler Console Sites
NetScaler supports automating radar object deployment for NetScaler Console sites, eliminating the need for manual deployment on the NetScaler instances.
This enhancement is available only when you edit a NetScaler instance and it is applicable only for site type Data Center (with type Private) or Branch.
When you select Deploy to NetScaler from the Real User Measurements list, the NetScaler Instance list is automatically populated, allowing you to choose the specific instance to deploy the radar object (r20.gif).
For more information, see Automate radar object deployment.
[ NSADM-104691 ]
Fixed Issues
The issues that are addressed in Build Feb 06, 2024.
Analytics
-
The XML SQL attack is not reported in both security dashboard (Security > Security Dashboard) and security violations dashboard (Security > Security Violations).
[ NSHELP-37159 ]
Licensing
-
Flexed license dashboard displays NetScaler details only after at least one NetScaler is checked out from the Premium bandwidth license pool.
[ NSADM-106497 ]
Management and Monitoring
-
When a configuration job is created, the status in Infrastructure > Configuration > Jobs shows Completed but Details > Execution Summary displays 0% complete.
[ NSHELP-37176 ]
-
A two-stage upgrade job status for a NetScaler HA displays ‘Scheduled’ even though the NetScaler HA upgrade is completed. The primary node displays completed (Status Stage 1: Completed) but the secondary node displays scheduled (Stage 2: Scheduled).
[ NSHELP-36943 ]
-
When a configuration audit template is created with special characters in its name under Infrastructure > Configuration > Configuration Audit > Audit Templates > Add, the template is successfully generated. However, a differential report fails to generate for the template in the Configuration Audit dashboard during polling.
This issue is observed when special characters other than - (dash) and ‘_’ (underscore) are used.
[ NSHELP-36438 ]
January 24, 2024
Analytics
View Upgrade Advisory details in Tasks
In Tasks, you can now view the Upgrade Advisory actionable task. Based on your current utilization, if your NetScaler instances have already reached or about to reach End-of-Life (EOL) or End-of-Maintenance (EOM) within 90 days, the Upgrade Advisory task displays the details of those instances. You can click Take Action and upgrade those instances to a recommended build.
[ NSADM-104715 ]
Infrastructure
Enhanced permissions for read-only users
Users with read-only permissions for the following features can now poll NetScaler instances:
- SSL certificates (Infrastructure > SSL Dashboard > Poll Now)
- Network functions (Infrastructure > Network Functions > Poll Now)
- Configuration audits (Infrastructure > Configuration > Configuration Audit > Poll Now)
[ NSADM-104710 ]
Fixed Issues
The issues that are addressed in Build Jan 24, 2024.
-
The built-in agent registration in NetScaler SDX displays a success message but the SDX instance does not appear in Infrastructure > Instances Dashboard.
[ NSHELP-37137, NSHELP-37128 ]
-
In Infrastructure > Network Functions > Load Balancing, the Servers tab indicates the number of servers but does not display any table entries for non-default users.
[ NSHELP-36964 ]
January 16, 2024
Support for identification and remediation of CVE-2023-6548 and CVE-2023-6549
NetScaler Console service Security Advisory now supports the identification and remediation of CVE-2023-6548 and CVE-2023-6549.
-
Identification for CVE-2023-6548 requires a version scan.
-
Identification for CVE-2023-6549 requires a combination of version and configuration scan.
Remediation requires an upgrade of the vulnerable NetScaler instances to a recommended build that has the fix.
Note:
Security Advisory does not support NetScaler builds that have reached End of Life (EOL). We recommend you upgrade to the NetScaler supported builds or versions.
For more information on how to use NetScaler ADM to upgrade NetScaler instances, see Use jobs to upgrade NetScaler instances.
For more information, see Security Bulletin.
Note:
It might take a couple of hours for the security advisory system scan to conclude and reflect on the impact of CVE-2023-6548 and CVE-2023-6549 in the security advisory module. To see the impact sooner, you may start an on-demand scan by clicking Scan Now.
[ NSADM-104763 ]
January 09, 2024
Analytics
Support to share custom dashboard to other users
As an administrator, you can now share the custom dashboard with other users. In Overview > Custom Dashboard, select a dashboard and click Share. Type the username and click Invite to share the dashboard. The assigned users can view the dashboard in read-only mode.
[ NSADM-100879 ]
Infrastructure
Configure ITM Radar in NetScaler Console Sites
The ITM Radar enhances network monitoring capabilities. The sites deployed in data centers, virtual machines, or cloud providers can now host the radar object (r20.gif), providing insights into performance metrics. The ITM Radar object actively collects valuable end-user application statistics, providing the sites with robust ITM radar telemetry for more effective network monitoring and informed traffic management decisions.
For more information, see Configure ITM Radar.
[ NSADM-91686 ]
View gateway insights data in Splunk and New Relic
When you create a new subscription in Settings > Ecosystem Integration for the integration of NetScaler Console service with Splunk and New Relic, you can now select the Gateway Insights option. After you configure the subscription with the Gateway Insights option, you can view the gateway insights data in Splunk and New Relic.
For more information, see For more information, see Integration with Splunk and Integration with New Relic.
[ NSADM-101036 ]
Export SSL data to Splunk and New Relic immediately
The SSL data is now exported to Splunk and New Relic immediately after an admin creates a subscription by selecting SSL Certificate Insight in Splunk and New Relic. Earlier, the admins had to click Poll Now (Infrastructure > SSL Dashboard) to export the data for the first time.
[ NSADM-101035 ]
View Upgrade Advisory details in Tasks
In Tasks, you can now view the Upgrade Advisory actionable task. Based on your current utilization, if your NetScaler instances have already reached or about to reach End-of-Life (EOL) or End-of-Maintenance (EOM) within 90 days, the Upgrade Advisory task displays the details of those instances. You can click Take Action and upgrade those instances to a recommended build.
[ NSADM-104715 ]
Action policy - Configure notifications for Requests, Bandwidth, and Response Time
In Action Policies (Settings > Actions > Action Policies), when you configure an action policy in Application Performance, you can now select Requests, Bandwidth, and Response Time options. These options enable you to configure and receive notifications for total requests, total bandwidth, average response time, and response time anomalies. For more information, see Configure an action policy to receive application event notifications.
In addition, you can also now configure an action policy from graph trend in Web Insight for these metrics. As an administrator, when you notice any unusual traffic pattern or a sudden spike in these metrics for any application, this enhancement enables you to create a relative action policy by clicking Create Action Policy after placing it on a specific point in the graph.
[ NSADM-101273 ]
Fixed Issues
The issues that are addressed in Build Jan 09, 2024.
Licensing
-
After the Flexed or Pooled license is applied, the Analytics Configuration page (Settings > Analytics Configuration) is not updated with the correct details.
[ NSADM-106665 ]
-
The Flexed license dashboard in NetScaler Licensing > Flexed Licensing > Dashboard appears blank.
[ NSADM-106561 ]
-
In NetScaler Licensing > License Management, the configuration for the threshold breach through email notification is not working as expected.
[ NSHELP-36895 ]
December 13, 2023
Infrastructure
NetScaler ADM service rebranding
NetScaler Application Delivery Management service (ADM Service) is now rebranded to NetScaler Console service.
Other terminologies that have been rebranded are as follows:
- ADM agent is now rebranded to NetScaler agent
- ADM Service Connect is now rebranded to Console Advisory Connect
Note:
Our NetScaler Console service product UI and documentation are currently undergoing updates to reflect these changes. During this time, you may come across the earlier and rebranded names being referenced interchangeably. We thank you for your understanding during this transition.
[ NSADM-105125 ]
Licensing
NetScaler Flexed licensing
NetScaler Flexed licensing is the new licensing framework aimed at simplifying the license management process. Your Flexed license includes software instance licenses (VPX/CPX/BLX, SDX, MPX, and VPX FIPS) and bandwidth capacity licenses. You must apply the Flexed licenses on NetScaler Console service or NetScaler ADM on-prem. You must also apply the MPX Z-Cap and SDX Z-Cap license on NetScaler MPX hardware and NetScaler SDX hardware, respectively. You can then allocate them across all NetScaler form factors deployed in cloud or on-prem.
Note:
Ensure that your NetScaler agents are running version 16.x or later.
For more information, see Flexed license.
[ NSADM-98483 ]
Analytics
Flexed license - Metrics Collector disabled by default for the new NetScaler instances added in NetScaler Console
If you are using the Flexed license, the Metrics Collector is now disabled by default for the new NetScaler instances added in NetScaler Console. You must manually enable this option to push the NetScaler metrics and counters data to the Console. The metrics collector configuration for the existing managed instances remain unchanged.
Note:
The Metrics Collector must be enabled for the data to appear in the Application Dashboard and its related tabs such as Performance, SSL, and Key Metrics for all the licensed virtual servers on that instance.
For more information, see Configure Intelligent App Analytics.
[ NSADM-106193 ]
Deprecation of Video and TCP insight features
With the latest release, Video Insight and TCP Insight reporting data are no longer available for visualization in the NetScaler Console.
[ NSADM-106597 ]
Infrastructure
Download files for batch configuration jobs
The configuration jobs now allow you to download files from a directory on a NetScaler instance to a directory on your local machine using the NetScaler ADM GUI.
To use this feature, navigate to Infrastructure > Configuration > Configuration Jobs, select a job and click Download Result Files.
The Download Result Files button is available only if the following conditions are met:
- The configuration job that is created is a batch configuration job. To create a batch configuration job, go to Create Job > Select Configuration and in the Configuration Editor, select Configuration Source > Batch Configuration
- A
scp getcommand is used in the Configuration Editor
For multiple NetScaler instances, the downloaded result files are available in separate folders, each corresponding to an individual instance.

[ NSADM-105442 ]
Pause and resume a scheduled upgrade job
NetScaler ADM now offers the option to pause your scheduled upgrade job. To use this feature, navigate to Infrastructure > Upgrade Jobs, select an existing scheduled upgrade job, and click Stop to pause the job. To resume the scheduled upgrade job, click Resume.
Note:
If the scheduled time for the upgrade job has passed after you decided to resume it, you need to create the upgrade job again.
For more information, see Upgrade Jobs
[ NSADM-100807, NSADM-97280 ]
Fixed Issues
The issues that are addressed in Build December 13, 2023.
Analytics
-
In Applications > Dashboard, the export of transaction log data to the tabular or CSV format does not display any data. This issue is noticed when NetScaler ADM is configured with non UTC time zones.
[ NSHELP-36817 ]
-
In Security > Security Violations > Violation Details, the search filter does not recognise the “Client-IP !=” query.
[ NSHELP-36675 ]
-
Scheduled snapshot reports exported from Security > Security Violations > Export Reports > Schedule Export with the file format selected as JPEG display the following error:
“Please provide query parameters in the report context or csv_export_arr.”
[ NSHELP-36657 ]
Infrastructure
-
Certain users see “For development purposes only” watermark on the maps in the Infrastructure > Instances page.
[ NSHELP-36863 ]
Management and Monitoring
-
NetScaler ADM agent generates “netScalerLoginFailure” SNMP traps. This issue occurs because the credentials that the ADM agent uses to log into NetScaler gets truncated due to a newline character.
[ NSHELP-36804 ]
Security
-
After configuring protections in the Unified security dashboard (Security > Security Dashboard > Manage Application), the protections are not getting deployed in the content switching virtual server.
[ NSADM-105544 ]
November 29, 2023
Infrastructure
Use tags to authorize instances for user groups
As an administrator, you can now authorize users to specific instances based on associated tags. When creating user groups, navigate to Settings > Users & Roles > Add > Authorization Settings > Select Tags and then authorize users to instances by tags.
For more information, see Configuring role-based access control.
[ NSADM-104798 ]
Fixed Issues
The issues that are addressed in Build November 29, 2023.
-
When you provision a VPX instance on SDX in Infrastructure > Instances > NetScaler > SDX > Select Action > Provision VPX, the Manage through network option does not appear.
[ NSHELP-36328 ]
November 09, 2023
Analytics
Configure Gateway session timeout
In Settings > Analytics Settings > Configure ICA/Gateway Session Timeout, you can now configure timeout session for Gateway Insight. By default, the value is 30 minutes. With this configuration, if NetScaler ADM does not receive session terminate record within the configured duration, then the session is recorded as terminated.
[ NSADM-101271 ]
Update in NetScaler backup process and firewall access
NetScaler instance backups are now uploaded from the NetScaler agent to NetScaler ADM Service directly and then to Amazon S3. So, you no longer need to allow access to S3 URLs in your firewall for the NetScaler backup service.
[ NSADM-98267 ]
Support for Intelligent Traffic Management
NetScaler ADM service now supports intelligent traffic management that helps you enhance the user experience by analyzing the internet traffic in real-time and automatically steering your traffic to the optimal locations.
Intelligent traffic management enables you to:
- Deliver applications in multiple locations to reduce application response time and maximize application availability, based on real-time service data.
- Configure the authoritative DNS to manage your zones.
- View insights into the customer data centers or delivery platforms and applications.
- Identify the best platforms and locations.
Click Intelligent Traffic Management in the left navigation pane to get started. For more information, see Intelligent Traffic Management.
[ NSADM-91677 ]
Unified Security dashboard
In NetScaler ADM, you can now use a single-pane dashboard to configure protections, enable analytics, and deploy them on your applications. Navigate to Security > Security Dashboard and then click Manage Application to:
-
View all secured and unsecured applications.
-
Select a unsecured application, configure protections from various template options, enable analytics for the protections, and deploy them on your application to secure the application.
Earlier, you had to configure all protections in the NetScaler instances and you were able to view only analytics for the configured protections in NetScaler ADM. As an administrator, this single-pane dashboard enables you to configure protections for the application in a single workflow.
For more information, see Unified Security dashboard.
[ NSADM-92678 ]
Fixed Issues
The issues that are addressed in Build Nov 09, 2023.
Infrastructure
-
When setting up the NetScaler built-in agent to manage instances, the configuration gets stuck at the Add Instances page, even though the registration is successful, and the agent can be viewed in the Instance Dashboard page.
[ NSHELP-36614 ]
StyleBooks
-
When config packs with special characters in their parameters are updated or deleted, NetScaler ADM displays a success message despite incomplete update or delete operations on NetScaler. With this fix, NetScaler ADM now accurately displays errors for any incomplete configurations resulting because of special characters in the configpack definition.
[ NSADM-104423 ]
October 25, 2023
Analytics
Create custom dashboards to view instance key metric details
Similar to the unified dashboard (Overview > Dashboard), you can now view instance metric details based on your choice by creating custom dashboards. For example, if you want to monitor the key metrics for applications and application security, you can create a custom dashboard by selecting only those two categories. You can create up to 20 dashboards by using a unique name for each dashboard. As an administrator, this enhancement enables you to create multiple dashboards and monitor only the required instance insights.
To get started, navigate to Overview > Custom Dashboard.
For more information, see Create custom dashboards to view instance key metric details.
[ NSADM-91875 ]
Actionable tasks and recommendations
The following enhancements are now added to the Tasks feature:
-
A new Tasks tab is introduced where you can view actionable tasks that need your immediate attention. These tasks are displayed based on your current utilization. As an administrator, completion of these actionable tasks ensure that your NetScaler deployment is secured, compliant, and efficient. You can also view these actionable tasks based on the severity of the issues (Critical and Medium).
-
The To Do tab is renamed as Recommendations. In Recommendations, you can continue to review the existing tasks and click Guide Me to complete the task.
-
The Archive tab is no longer available. Instead, you can choose to Dismiss a recommendation from the list.
For more information, see Actionable tasks and recommendations.
Infrastructure
Use certificate store to update SSL certificates
When you update an SSL certificate in Infrastructure > SSL Dashboard > Update, you can now select the certificate from the certificate store. Earlier, you had to upload the certificate file and key file to update an SSL certificate.
[ NSADM-101303 ]
Updated list of SNMP traps
The list of SNMP traps is now updated with new traps as well as some previously missing traps. To view the complete list, navigate to Infrastructure > Events > Event Settings > NetScaler.
[ NSADM-99798 ]
Fixed issues
The issues that are addressed in Build Oct 25, 2023.
-
When you provision a VPX instance on SDX in Infrastructure > Instances > NetScaler > SDX > Select Action > Provision VPX, the Manage through network option does not appear.
[ NSHELP-36328 ]
October 10, 2023
Management and Monitoring
Support for identification and remediation of CVE-2023-4966 and CVE-2023-4967
NetScaler Console Security Advisory now supports the identification and remediation of CVE-2023-4966 and CVE-2023-4967.
-
Identification requires a combination of version and configuration scan.
-
Remediation requires an upgrade of the vulnerable NetScaler instances to a recommended build that has the fix.
Note:
Security Advisory does not support NetScaler builds that have reached End of Life (EOL). We recommend you upgrade to the NetScaler supported builds or versions.
For more information on how to use NetScaler ADM to upgrade NetScaler instances, see Use jobs to upgrade NetScaler instances.
For more information, see Security Bulletin.
[NSADM-101092]
September 26, 2023
Analytics
Export data to Splunk and New Relic only from selected instances
When you create a subscription to export data to Splunk and New Relic, you can now select the NetScaler instances. If you create a subscription with specific instances, the data is exported to Splunk and New Relic only from the selected NetScaler instances.
For more information, see Integration with Splunk and Integration with New Relic.
[NSADM-94371]
Infrastructure
ADM on-prem instances connected with ADM Service using Cloud Connector
In Settings, you can now view a new option called ADM On-Prem. In this page, you can view details of the ADM on-prem instances that are connected with the ADM service tenant through ADM On-Prem Cloud Connector.
For more information, see ADM on-prem instances connected with ADM Service using Cloud Connector.
[NSADM-94576]
Fixed Issues
The issues that are addressed in Build Sep 26, 2023.
Analytics
-
The periodic pruning of the App Dashboard data did not function as expected. As a result, NetScaler Console consumed more disk space.
[ NSHELP-36184 ]
September 13, 2023
Infrastructure
Authentication token to upload technical support bundle
You now need an authentication token to upload the technical support bundle generated on your NetScaler to the Citrix technical support server. Previously, you uploaded the technical support bundle using Citrix user name and password. For more information, see How to generate a technical support bundle for a NetScaler instance.
[ NSADM-93351 ]
Fixed Issues
The issues that are addressed in Build Sep 13, 2023.
Analytics
-
When NetScaler Console loses the virtual server licenses, the analytics status for the virtual servers using those licenses is expected to be disabled. This scenario was not working as expected for the VPN virtual servers.
[ NSHELP-36183 ]
Infrastructure
-
In Gateway > HDX Insight and Gateway > Gateway Insight, the X-axis of the graph displays dates instead of time.
[ NSHELP-36043 ]
Management and Monitoring
-
Reports exported from Infrastructure > Network Reporting > Export appear truncated or incomplete.
[ NSHELP-36252 ]
-
Azure Active Directory (AD) users who belong to many Azure groups cannot access NetScaler Console even if the AD groups are mapped to ADM groups.
[ NSHELP-35456 ]
August 31, 2023
Infrastructure
View the Certificate Store page under SSL Dashboard
You can now navigate to Infrastructure > SSL Dashboard > Certificate Store to view the Certificate Store page.
[ NSADM-97858 ]
Support for SNMP functionality for the agents
In Infrastructure > Agents > Actions > Manage SNMP, you can now create SNMP managers, SNMP users and SNMP views for agents.
For more information on SNMP managers and users, see Create SNMP managers and users for NetScaler ADM agent.
[ NSADM-94923 ]
User experience and functionality improvements for the Data Storage Management dashboard
To improve the user experience and make the data storage management more efficient, the following improvements are now available for the Data Storage Management dashboard:
-
New UI design for the dashboard:
-
Added Data Ingestion, Storage Consumption, Data Pruning, and Actions tiles
-
Actions tile provides options to add more storage, review data retention policy, perform data pruning, and review your system notifications
-
-
Search functionality in Storage Consumption Trends section:
In addition to viewing the storage trends, you can now search for specific features and trends.
-
Perform data pruning:
-
You can now select one or more features and prune their data to free up your storage
-
You are entitled to 10 data prunes each month
-
For more information on the Data Storage Management dashboard, see Data Storage Management.
[ NSADM-93202 ]
Security
API Gateway renamed to API Security
API Gateway is now renamed to API Security. You can view the changes in the following pages:
- Security > API Security
- Security > API Security > API Analytics > Get help > API Security docs
- Settings > Users & Roles > Groups > Authorization Settings > API Security
- Settings > Users & Roles > Access Policies > Permissions > Security > API Security
[ NSADM-102384 ]
Fixed Issues
The issues that are addressed in Build August 31, 2023.
Management and Monitoring
- In Infrastructure > Network Reporting, the Network Reporting dashboard does not display any historical data in the virtual server reports. This issue is seen when you select a NetScaler HA pair in Select Entities while creating the dashboard.
[ NSHELP-36228 ]
August 11, 2023
Management and Monitoring
Security Advisory - File integrity monitoring
The NetScaler Console Security Advisory now enables you to scan the NetScaler build files and view results of any alterations or additions to the original NetScaler build files.
In Security Advisory (Infrastructure > Instance Advisory > Security Advisory), the Scan Now option enables you to select Scan CVEs, Scan Files, or Scan Both. After you select Scan Files or Scan both, NetScaler Console compares the binary hash for managed NetScaler build files with the original binary hash values and highlights if there are any file alterations or file additions under the File Integrity Monitoring tab.
The scan results showcase the NetScaler instances that have any potential changes to the original files and/or any other file additions. For further investigations on the scan results, you can contact your organization’s digital forensics.
For more information, see Security Advisory.
[NSADM-91856]
August 09, 2023
Infrastructure
View virtualization platform details for NetScaler VPX
In Infrastructure > Instances > NetScaler > VPX, you can now view the platform on which NetScaler VPX is hosted by selecting Settings > Cloud Platform.
[NSADM-97319]
Retry failed upgrade jobs
In Infrastructure > Upgrade Jobs, you can now select the failed upgrade job and do either of the following actions:
-
Click Retry next to the failed upgrade job
-
Go to Select Action > Retry Upgrade Job
For more information, see Retry failed upgrade jobs.
[NSADM-93439]
Security
Update an existing API definition
In Security > API Gateway > API Discovery, you can now update an existing API definition with selected API resources.
For more information, see Update an existing API definition with discovered API endpoints.
[NSADM-97433]
Fixed Issues
The issues that are addressed in Build August 09, 2023.
Provisioning
-
The NetScaler VPX provision on VMware vCenter (Infrastructure > Instance > Citrix ADC > VPX > Provision) fails because of the same name that was used in the previously deleted VPX instance.
[NSHELP-35983]
StyleBooks
-
When you try to migrate an ADC configuration from a source ADC instance to a target instance in Applications > Configuration > Config Packs > Migrate ADC > Get Started > Specify Configuration, and click Next, the following error message is displayed intermittently:
No Job found.
[NSADM-97948]
-
If you create a configpack from a StyleBook definition that has an authentication virtual server and built-in cache policy bindings, and then you delete the configpack, the deletion is successful. However, if you try to create the configpack again with the same parameters, the following error message appears:
Resource already exists.
[NSHELP-35646]
July 26, 2023
Analytics
Support to configure the export of metrics from NetScaler to Prometheus through StyleBook
To export metrics from NetScaler to Prometheus, you must create an analytics profile in NetScaler and specify the schema file. For more information, see Monitoring NetScaler Console, applications, and application security using Prometheus.
In Applications > Configuration > Stylebooks > Default Stylebook, you can now use the Prometheus TimeSeries Analytics Configuration StyleBook and run the configuration to all managed instances.
For more information, see Prometheus analytics StyleBook.
[NSADM-97698]
Assign a Net Profile for the managed NetScaler instances from NetScaler Console
When you enable analytics for the virtual servers in NetScaler Console, the AppFlow data from the NetScaler is exported to NetScaler Console through the NetScaler subnet IP address (SNIP). In some scenarios, the SNIP might be blocked because of the firewall in the network. In such scenarios, you might have to use a different IP address than the SNIP. For more information about net profile, see Use a specified source IP for back-end communication.
You can now assign net profiles to a NetScaler instance through NetScaler Console. Navigate to Infrastructure > Instances > Citrix ADC, select the instance, and from the Select Action list, click Configure Net Profiles to assign a net profile for the instance.
Note:
Ensure that you have disabled analytics in all virtual servers before you assign a net profile for the instance.
With this enhancement, you can assign a net profile for exporting AppFlow data from NetScaler to NetScaler Console.
[NSADM-91836]
Infrastructure
Improved user experience when using CLI to configure NetScaler agent as a proxy
When you try to register a NetScaler agent to the NetScaler Console service, the CLI now prompts you with (y/n) questions regarding the proxy usage.
You also have an option to configure the proxy in the same script, if needed.
[NSADM-96921]
CLI support to view endpoint URLs while registering a NetScaler agent
After you enter a service URL in CLI while registering a NetScaler agent with the NetScaler Console service, you can view the list of all the endpoint URLs that must be allowed access.
[NSADM-96920]
StyleBooks
Support for additional attributes in StyleBooks analytics
The StyleBooks analytics section is now enhanced to:
-
Accept parameters to configure Transport Mode (
transport-mode) -
Configure HDX Insight for different types of traffic(
enable-hdxinsight-for)-
Enable HTTP X-Forwarded-For option (
http-x-forwarded-for) -
Enable Client side Measurements (
client-side-measurements)
-
For more information, see StyleBooks Analytics.
[NSADM-97839]
July 18, 2023
Management and Monitoring
Support for identification and remediation of CVE-2023-3519, CVE-2023-3466, and CVE-2023-3467
NetScaler Console Security Advisory now supports the identification and remediation of CVE-2023-3519, CVE-2023-3466, and CVE-2023-3467.
Identification of:
-
CVE-2023-3519 requires a combination of version and config scan.
-
CVE-2023-3466 and CVE-2023-3467 requires a version scan.
The remediation for CVE-2023-3519, CVE-2023-3466, and CVE-2023-3467 requires an upgrade of the vulnerable NetScaler instance to a release and build that has the fix.
Note:
Security Advisory does not support NetScaler builds that have reached End of Life (EOL). We recommend you upgrade to the NetScaler supported builds or versions.
For more information on how to use NetScaler Console to upgrade NetScaler instances, see Use jobs to upgrade NetScaler instances.
For more information on how to remediate CVE-2023-3519, CVE-2023-3466, and CVE-2023-3467, see Security Bulletin.
Note:
It might take a couple of hours for the security advisory system scan to conclude and reflect the impact of CVE-2023-3519, CVE-2023-3466, and CVE-2023-3467 in the security advisory module. To see the impact sooner, you can start an on-demand scan by clicking Scan Now.
[ NSADM-100103 ]
July 12, 2023
Fixed issues
The issues that are addressed in Build July 12, 2023.
-
When you back up or restore a NetScaler instance, the
/var/metrics_confdirectory is not backed up.[ NSHELP-35724 ]
-
The deployment of config packs might fail when the StyleBook definition includes the
operationssection.[ NSHELP-35588 ]
July 03, 2023
Analytics
Configuration Job - Support to create a job for configuring export of metrics from NetScaler to Prometheus
To export metrics from NetScaler to Prometheus, you must create an analytics profile in NetScaler and specify the schema file. For more information, see Monitoring NetScaler, applications, and application security using Prometheus.
In Configuration Job, you can now create a job using the NSConfigurePrometheusAnalyticsProfile template from the Inbuilt Template, specify the required parameters, and run the job to all managed instances.
For more information, see Schedule a job for configuring export of metrics from NetScaler to Prometheus.
[NSADM-97251]
Infrastructure
NetScaler agent caches NetScaler images
The time taken for the NetScaler upgrade is now considerably reduced as the NetScaler images are cached in the NetScaler agent after they are downloaded. Hence, the images are not required to be downloaded for subsequent upgrade jobs.
Note:
This is applicable only for NetScalers that are added using the NetScaler agent.
For more information, see Create an ADC upgrade job.
[NSADM-76343]
Fixed issues
-
In Web Insight, when you drill down any metric to view details and then further drill down any metric, the graph remains in the previous view, but all other details appear as expected.
As a result, this creates an assumption that the further drill down is not working as expected.
[NSADM-98995]
-
When you try to migrate an ADC configuration from a source ADC instance to a target instance in Applications > Configuration > Config Packs > Migrate ADC > Get Started > Specify Configuration, and click Next, the following error message is displayed intermittently:
“No Job found”.
[NSADM-97948, NSADM-97727]
-
In the App dashboard, when you select an application and navigate to the SSL tab to bind a certificate, an error message “Certificate not found in database” is displayed.
[NSHELP-35654]
June 14, 2023
Security
Support to create API definition without selecting endpoints
In the Security > API Gateway > API Discovery > Vserver page, you can now create an API definition without selecting an endpoint. When you click Create API Definition, a pop-up window appears for you to confirm if an API definition must be created for all the discovered endpoints. Click Yes to create the API definition with all the endpoints, else click No.
For more information, see Discover API endpoints.
[ NSADM-94318 ]
StyleBooks
Support for additional argument types in replace() function
The replace() built-in function can also accept a list of the following built-in types:
stringipaddresstcp-portnumberboolean
For more information, see replace().
[ NSADM-96802 ]
Fixed Issues
The issues that are addressed in Build June 14, 2023.
-
In Upgrade Jobs (Infrastructure > Upgrade Jobs), when you select the pre-upgrade validation failed instance and click Revalidate, an error message is displayed.
[ NSADM-98329 ]
-
MPX instances are missing from the Infrastructure > Citrix ADC Inventory > Citrix ADC (MPX/VPX/CPX/BLX) page.
[ NSHELP-35593 ]
-
When you export the SSL expiry reports for weekly, 30 days or 90 days from Infrastructure > SSL Dashboard > SSL Certificates > Export Reports and select Tabular, the resulting report displays an empty Domain column.
[ NSHELP-35592 ]
-
In Infrastructure > SSL Dashboard > SSL Certificates, the NetScaler high-availability pair does not display the superscript of ‘P’ and ‘S’ for the primary and the secondary devices.
[ NSHELP-35523 ]
-
In NetScaler release 13.1 and above, the ISSU commands do not get executed during the NetScaler upgrade.
[ NSHELP-35391 ]
-
For multiple Cluster IP addresses (CLIPs) in a cluster, when you add a CLIP in brackets in Infrastructure > Instances > Citrix ADC > Add, the configuration fails and the CLIP does not get added to NetScaler Console.
[ NSHELP-35323 ]
May 31, 2023
Analytics
Pooled licensing recommendations in the Tasks feature
In Tasks, you can now view recommendations and Guide Me workflows for pooled licensing entitlements. As an administrator, these pooled licensing recommendations ensure that you are making use of all capabilities of NetScaler Console.
For more information, see View recommendations and manage your ADCs and applications efficiently.
[ NSADM-93988 ]
Export SSL insights data to Splunk and New Relic
When you create a new subscription in Settings > Ecosystem Integration for the integration of Citrix ADM with Splunk and New Relic, you can now select the SSL Certificate Insights option. After you configure the subscription with the SSL Certificate Insights option, you can view the SSL data (SSL vserver and SSL certificate related data) in the Splunk and New Relic dashboard.
For more information, see Integration with Splunk and Integration with New Relic.
[ NSADM-92047 ]
Fixed Issues
The issues that are addressed in Build May 31, 2023.
-
In Gateway > HDX Insight > Instances, when you select an instance and export the data, the user name information for Desktop Users was not available. With this fix, the user name information is also available in the report.
[ NSADM-96024 ]
-
When you select Configure SNMP for an SDX instance in Infrastructure > Instances> Citrix ADC > SDX, an error message is displayed. This issue occurs if the SDX profile is configured with SNMP v3 and NoAuthNoPriv as the security level.
[ NSHELP-35324 ]
-
In Infrastructure > Configuration > Configuration Jobs > Create Job > Select Configuration, when you enter a password variable ($password$) and retain the Type as Text Field instead of Password Field, and click Next, the page does not load.
[ NSHELP-35266 ]
-
In Web Insight, when you export data using the snapshot option, the graphs in the report appear blank.
[ NSHELP-35147 ]
-
Analytics is not visible in HDX Insight. Even if Citrix ADM is rebooted, the analytics is visible only for a short duration and becomes invisible later.
[ NSHELP-35128 ]
-
For an SDX instance in Infrastructure > Instances > Citrix ADC > SDX > Dasboard, when the used and free values for a resource are zero, the System Resource Utilization chart displays a blank space and blank value fields.
With this fix, the number zero is displayed next to the resource name if the used and free values are zero.
[ NSHELP-35069 ]
May 18, 2023
Analytics
Support to export from each widget in Web Insight
In Web Insight, the export option is now introduced in all widgets and it enables you to export data in tabular format. Using this enhancement, you can:
-
Export the required data individually from any widget.
-
Drill down any metric and also export the required data from any widget.
Earlier, the export data provided only the consolidated report.
Note
You can also continue to use the existing Export option to generate the consolidated report.
[NSADM-94140]
Infrastructure
View the complete certificate chain
You can now view the complete chain of links for a certificate including the intermediate certificates up to the root CA certificate.
To view the certificate chain, navigate to Infrastructure > SSL Dashboard, choose an SSL certificate and click Details.
[NSADM-52467]
Support to log events irrespective of event age
NetScaler Console now allows you to record all events irrespective of the event age you set in the event rules.
To set this option, navigate to Infrastructure > Rules > Add > Configure Event Age and select the Log events instantly irrespective of event age duration checkbox.
[NSHELP-19914]
Fixed Issues
The issues that are addressed in Build May 18, 2023.
-
In Infrastructure > Upgrade Jobs> Add > Schedule Task, if you select Perform two stage upgrade for nodes in HA and select the same time in the two Start Time fields, the following error message appears when you proceed:
“common.date_diff_error:There should be atleast 1 hour difference between upgrade time”
Even if you change the start time in the fields, the Create Job tab displays an empty page.
[NSHELP-35016]
-
In Infrastructure > Instance Advisory > Upgrade Advisory, the End of Maintenance (EOM) and End of Life (EOL) details for Release 13.0 is incorrect.
[NSHELP-34953]
-
The email alert for any event was showing the region incorrectly. With this fix, the region is not shown in the email alerts for events.
[NSHELP-34913]
May 09, 2023
Management and Monitoring
Support for identification and remediation of CVE-2023-24488 and CVE-2023-24487
NetScaler Console Security Advisory now supports the identification and remediation of CVE-2023-24488 and CVE-2023-24487.
Identification of:
-
CVE-2023-24488 requires a combination of version and config scan.
-
CVE-2023-24487 requires a version scan.
The remediation for CVE-2023-24487 and CVE-2023-24488 requires an upgrade of the vulnerable ADC instance to a release and build that has the fix.
For more information on the fixed build version details for CVE-2023-24487 and CVE-2023-24488, see Security Bulletin.
Note:
ADC build 13.1–45.63 replaces build 13.1–45.61.
For more information on how to use NetScaler Console to upgrade ADC instances, see Create an ADC upgrade job.
Note:
It might take a couple of hours for the security advisory system scan to conclude and reflect the impact of CVE-2023-24488 and CVE-2023-24487 in the security advisory module. To see the impact sooner, you can start an on-demand scan by clicking Scan Now.
[NSADM-93570]
April 25, 2023
The enhancements and changes that are available in Build April 25, 2023.
Analytics
Web Insight - Support to view nil values in graphs
In Web Insight, when you drill down any metric under Applications, Clients, URLs, or Instances, the analytics view now provides the visibility of nil values (for example, 0 ms and 0 request) in the graph for the selected duration.
Earlier, if there is no traffic or transactions received for the selected duration, Web Insight displayed the graphs by skipping those nil values. As an administrator, you can now view the complete graph with these nil values.
[ NSADM-88686]
StyleBooks
Specify user group access to config packs
As an administrator, you can now restrict user groups from accessing config packs created by other user groups. To select this option, navigate to Settings > Users & Roles > Groups > Authorization Settings > Config Packs > All Configurations created by the user group.
[ NSADM-92374 ]
Fixed Issues
The issues that are addressed in Build April 25, 2023.
-
In Applications > Configuration > Config Packs, when you enter a search query using the search criteria of Properties > Display Key, the search result is displayed but the search bar displays the index number of the result.
With this fix, the search bar displays the search query in text instead of a number.
[ NSADM-96859 ]
Analytics
-
The bandwidth data in HDX Insight and Gateway Insight is displayed incorrectly in bytes per second instead of bits per second.
[ NSHELP-34836 ]
April 13, 2023
The enhancements and changes that are available in Build April 13, 2023.
Analytics
Integrated Cache notification in Web Insight
After you enable Integrated Cache in the NetScaler instance, the eligible requests are processed without requiring a round trip to an origin server. In Web Insight, these Integrated Cache requests are currently visible under Servers with virtual server IP address instead of the actual server IP address.
For a better visibility of these Integrated Cache requests, you can now view an IC notification next to the ADC virtual server IP address under Servers.
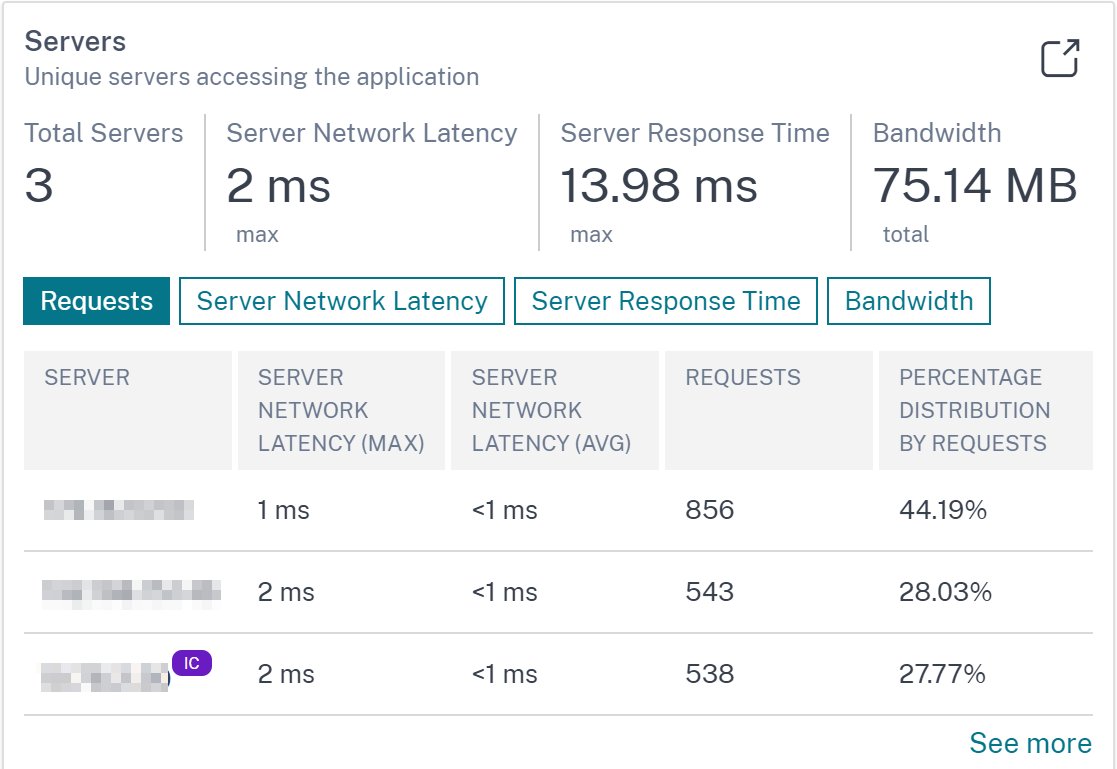
For the requests that are not processed with Integrated Cache, the actual origin server IP address is visible.
As an administrator, this notification enables you to quickly identify that the ADC instance has processed the Integrated Cache requests.
[NSADM-91864]
Integrated Cache hits and misses graph in Web Insight
In Web Insight, when you drill down a server, the Server Metrics now display Integrated Cache Hits and Integrated Cache Misses tabs.
As an administrator, the graph view in:
-
The Integrated Cache Hits tab enables you to view the total responses that the NetScaler appliance serves from the cache.
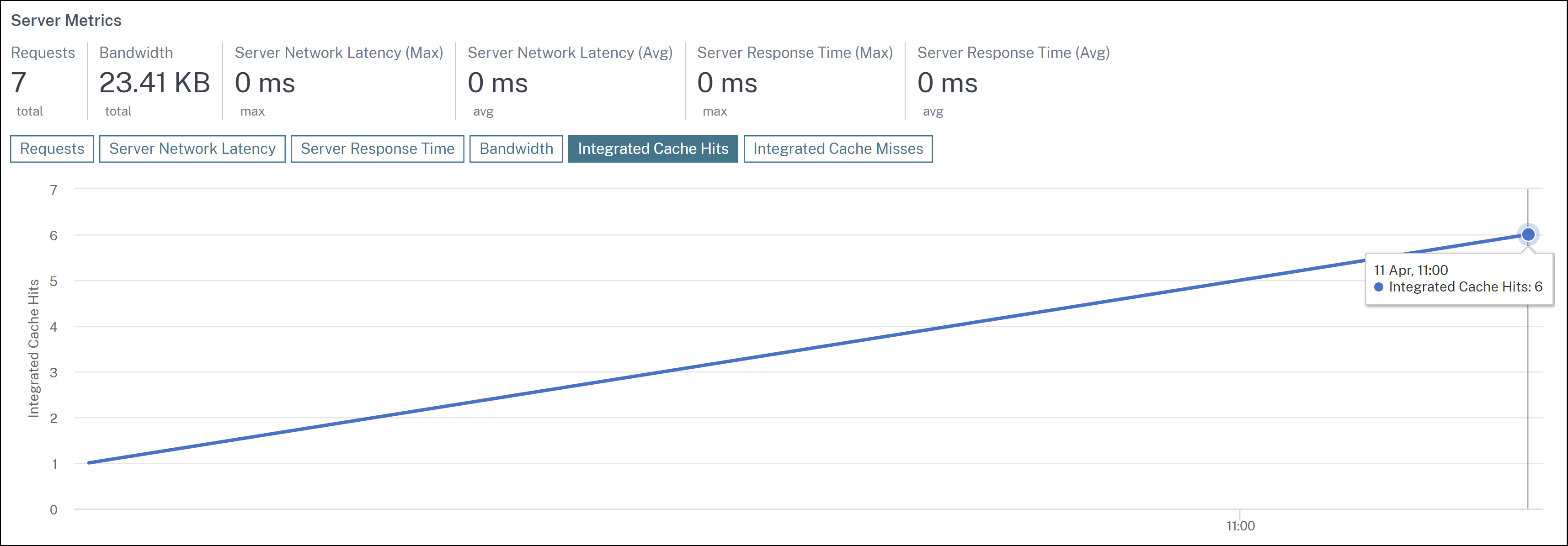
-
The Integrated Cache Misses tab enables you to view the total responses that the NetScaler appliance serves from the origin server.
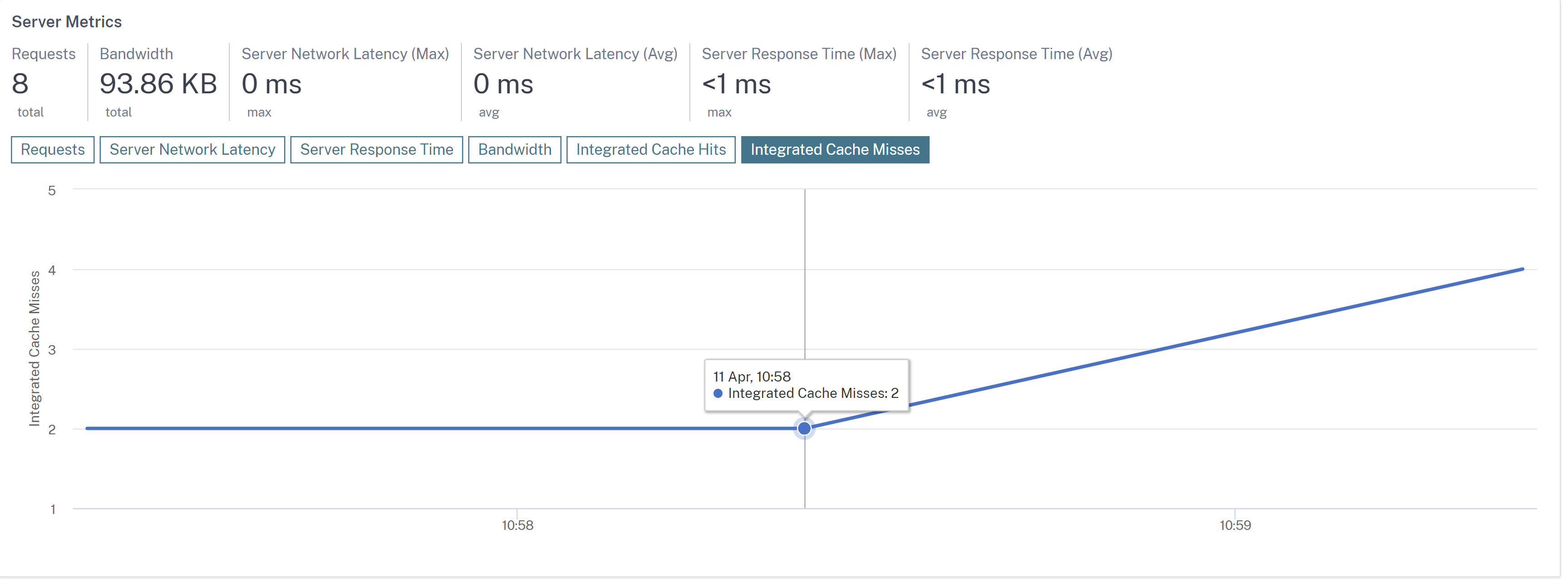
[NSADM-93952]
Web Insight - View both average and maximum values in graphs
Starting from 13.1 45.47 or later versions, the Web Insight in NetScaler Console is supported with the visibility of maximum latency values under Servers and Clients.
In addition to this support, when you drill down a server or a client, you can now view both average and maximum values in the summary panel, and also by hovering the mouse pointer on the time series analytics graph in Server Network Latency, Server Response Time, and Client Network Latency.
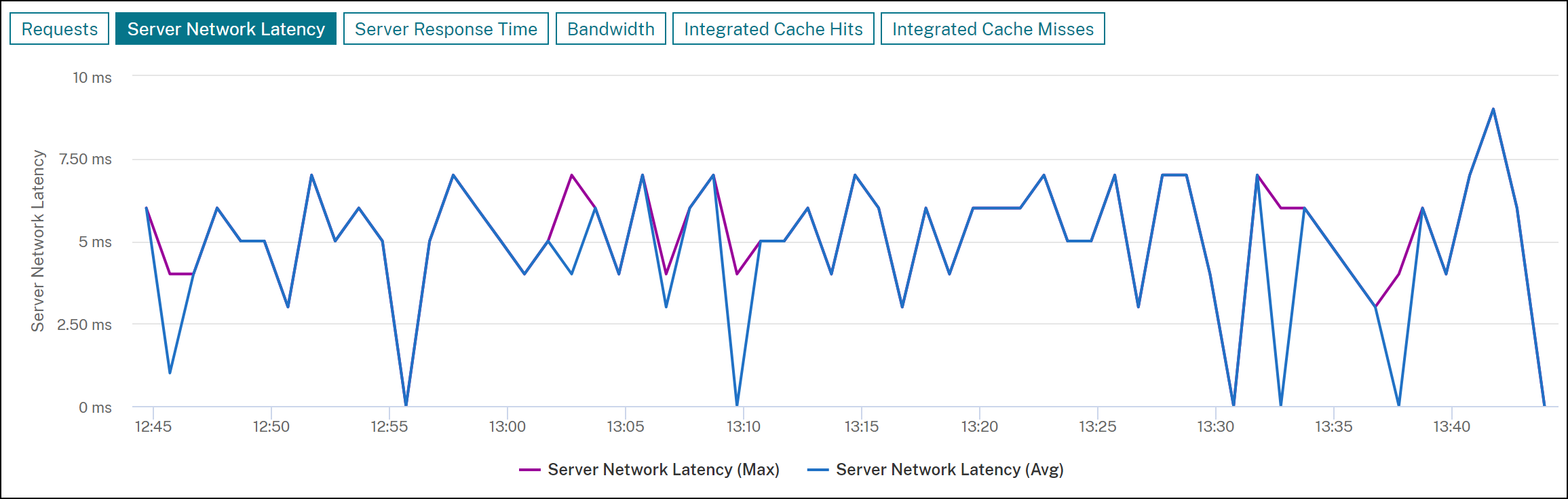
As an administrator, this enhancement enables you to visualize the maximum latency in graphs for the selected duration.
[NSADM-93816]
Infrastructure
View data storage trends in NetScaler Console GUI
In Settings > Data Storage Management, you can now view the data storage information across the different features in your current deployment. The Data Storage Management dashboard helps you visualize how the data is stored and if the features are operating within their storage entitlement.
Note
The data storage policies are expected to change in the upcoming releases. With these changes, you will not be able to store historical data after it exceeds the storage limit.
For more information, see Manage data storage.
[NSADM-94623]
Fixed Issues
The issues that are addressed in Build April 12, 2023.
Infrastructure
-
In high-availability deployments, there is no option to upload build image files only to the secondary node.
As part of the fix, you can now upload build image files to the secondary node from Infrastructure > Upgrade Jobs > Create Job tab > Upload to secondary node only.
[NSADM-96079]
-
The reports exported from Infrastructure > Instances > NetScaler do not display the serial number of secondary nodes.
The reports now display the serial numbers of both primary and secondary nodes of the NetScaler instances. You can also view the reports from Infrastructure > NetScaler Inventory.
[NSHELP-18816]
April 05, 2023
The enhancements and changes that are available in Build April 05, 2023.
Security
Create API definitions from discovered API endpoints in NetScaler Console GUI
You can now create API definitions from discovered API endpoints in Security > API Gateway > API Discovery.
[NSADM-85957]
Unified dashboard - View API analytics key metrics
In the unified dashboard (Overview > Dashboard), you now view key metrics for the API endpoints configured through NetScaler Console.
For more information, see A unified dashboard to view instance key metric details.
[NSADM-85954]
Fixed Issues
The issues that are addressed in Build April 05, 2023.
-
The Choose Appliance option for Certificate File and Key File fields appears for the following pages:
-
Infrastructure > SSL Dashboard > Manage Certificate Store > Add
-
Infrastructure > SSL Dashboard > SSL Certificates > Update
As a fix, the Choose Appliance option is now removed.
[NSHELP-34566]
-
-
If NetScaler has an on-premises NetScaler Console as a licensing server and an agent is modified in Infrastructure > Instances > Agents, the following issue occurs:
The IP address of the license server on NetScaler changes from the IP address of the on-premises NetScaler Console to the IP address of one of the NetScaler agents.[NSHELP-34483]
-
When you edit the password for an SDX admin profile configured with SNMPv3 from Infrastructure > Instances> NetScaler > SDX tab > Profile, the following error message appears:
Please provide valid authentication protocol. The possible values are MD5, SHA.[NSHELP-34372]
March 14, 2023
Fixed issues
The following issue is addressed in Build March 14, 2023:
In Infrastructure > SSL Dashboard > Install Certificates, when you upload a certificate chain that has the same root certificate as an existing certificate chain, the certificate installation fails. The following text is displayed in Infrastructure > SSL Dashboard > SSL Audit Logs > Device Log > Command Log:
Resource Already Exists
[NSHELP-34233]
When you delete an email distribution list from Settings > Notifications > Email, the following error is seen:
Error: Bad Gateway
This issue occurs because the name of the email distribution list has a white space.
As part of the fix, NetScaler Console now allows you to delete email distribution lists with white spaces.
[NSHELP-34545]
March 02, 2023
Analytics
Improvements to Web Insight
In Web Insight, you can now view the following enhancements under Application Metrics:
-
A new Summary tab is introduced that enables you to visualize an overview of the application performance such as Response Time, Requests, and Bandwidth. As an administrator, this enables you to get an insight of the application performance for the selected duration. You can use the toggle option and customize the view.
-
In the Requests tab, apart from the existing total requests, you can also view requests from the top 5 clients based on the total requests. As an administrator, this enables you to get an insight on the clients accessing the application for the selected duration.
-
In the Bandwidth tab, you can view the bandwidth consumption from the top 5 servers based on the total bandwidth consumption. As an administrator, this enables you to get an insight on the servers consuming more bandwidth for the selected duration.
-
In the Response Time tab, you can also view Client Network Latency, Server Network Latency, and Server Processing Time on the same graph. As an administrator, this enables you to get an insight on the latency that occurs from client, server, and application for the selected duration. You can use the toggle option and customize the view.
[NSADM-87792]
Infrastructure
Deletion of inactive NetScaler Console Express accounts
If your NetScaler Console Express account remains inactive for 45 days, the account will be deleted. Citrix sends a reminder after 30 days of inactivity.
[NSADM-93203]
Management and Monitoring
Change in execution summary for NetScaler high availability upgrade
In NetScaler Console GUI, the execution summary in Infrastructure > Upgrade Jobs > Execution Summary no longer displays the high availability synchronization related commands.
This is because, during the NetScaler high availability upgrade, if the NetScaler primary and secondary nodes are in different versions, NetScaler performs the disabling of the high availability synchronization between the nodes. NetScaler Console does not perform this operation.
[NSADM-93441]
Set threshold for individual entities in Network Reports
In Infrastructure > Network Reporting > Thresholds, you can now set the threshold value for specific entities while configuring the threshold.
For more information, see Network Reporting.
[NSADM-91727]
Support for scheduling individual agent upgrade
In Infrastructure > Instances > Agents > Settings, you can now schedule the upgrade of each NetScaler agent. You can choose to either automatically upgrade an agent to the next build or specify a time and time zone to schedule an upgrade.
For more information, see Agent upgrade settings.
[NSADM-91719]
Improvements in NetScaler instance upgrade
The following changes are now available in the Pre-upgrade validation tab:
-
Instances blocked from upgrade section - This new section lists the instances that are blocked from upgrade because of pre-upgrade validation errors.
-
Quick Cleanup button - This button is available in the Disk Space Details pane and allows you to quickly free up the disk space from multiple folders.
For more information, see How to upgrade an ADC instance.
[NSADM-91505]
NetScaler BLX images now available in the image library
While upgrading NetScaler BLX from Infrastructure > Upgrade jobs > Upgrade NetScaler BLX > Select Image, you can now select the NetScaler BLX images from the image library.
[NSADM-86864]
Security
View the versions of NetScaler Web App Firewall and bot signatures for a NetScaler instance
You can now view the versions of NetScaler Web App Firewall and bot signatures for a NetScaler instance. The latest signature versions protect your instance from the CVEs. For more information, see Signature Alert Articles and Bot signature alert articles.
[NSADM-92378]
Application Performance Analytics
Improvements to Web Insight
In Web Insight, you can now view the maximum network latency values in both Server and Client. As an administrator, this enhancement enables you to identify the exact server or client that is performing with maximum latency.
Earlier, Web Insight provided the maximum value only based on the average latency values across all servers and clients.
[NSADM-91834]
Miscellaneous
Create and apply filters in the unified dashboard
In the unified dashboard (Overview > Dashboard), you can now create and apply filters in:
-
Applications
-
ADC Infrastructure
-
Application Security
As an administrator, you can apply filters and view insights only for the selected instances or applications.
For more information, see A unified dashboard to view instance key metric details.
[NSADM-91873]
Fixed Issues
The issues that are addressed in Build Mar 02, 2023.
- In Infrastructure > Upgrade Jobs, when you select a completed job that has the pre-upgrade or post-upgrade script file name with special characters and then download the output scripts from the Select Action list, the File not found error message is displayed.
[NSHELP-33854]
February 07, 2023
Analytics
Security violations display OWASP tags
In the NetScaler Console GUI, the security violations now display OWASP tags. It supports the OWASP 2017 and OWASP 2021 lists. These tags help you determine whether the violation belongs to the OWASP top 10 list.
Select a violation to view more details. The details now include the OWASP 2017 and OWASP 2021 columns. These columns display the OWASP codes and you can use them to learn more about the violation from the OWASP website.
[NSADM-92999]
Management and Monitoring
Support for changing agent password without current password
As a super administrator, you can now allow agent passwords to be changed without their current passwords.
Navigate to Settings > Global Settings > System Configurations > Agent and Time Zone > Agent and select the Remove current password prerequisite for agent password change checkbox. The Change Agent Password page will no longer have the Current password field.
To display the Current password field again, clear the Remove current password prerequisite for agent password change checkbox.
[NSADM-91826]
Time series data visualization interval for NetScaler Console Express accounts is revised
For virtual servers managed with the Express account, the time series data visualization in analytics graphs and Network Reporting graphs for the Last 1 Hour duration is now revised.
| Feature | Existing data visualization interval | New data visualization interval |
|---|---|---|
| Application dashboard | 1 minute | 5 minutes |
| Network Reporting | 5 minutes | 10 minutes |
| Web Insight, HDX Insight, Gateway Insight, Security Insights, BOT Insights, Detailed Transactions | 1 minute | 5 minutes |
[NSADM-93200]
Fixed issues
The following issues are addressed in Build February 07, 2023.
When you enable or disable syslog settings for the ADC instance, ADM does not save configuration in the ADC instance. As a result, configuration changes events are not saved in NetScaler Console.
[NSHELP-33264]
In Infrastructure > Instances > Agent, after you install the SSL certificate with a password encrypted key, the connection to agent on Port 443 fails.
[NSHELP-33614]
January 24, 2023
Fixed issues
The following issues are addressed in Build January 24, 2023.
An error message appears when you enable SNMP v3 on a NetScaler SDX instance from the NetScaler Console GUI by navigating to Infrastructure > Instances > NetScaler > SDX > Select Action > Configure SNMP.
[NSHELP-33852]
January 10, 2023
Management and Monitoring
View recommendations and manage your ADCs and apps efficiently as actionable Tasks with Guide Me workflows
In the NetScaler Console GUI, a new Task option is introduced, where you can now view recommendations based on your subscription and current utilization. As an administrator, you can:
-
View To-Do tasks as actionable recommendations for licensing, analytics, events, SSL certificates, and many more
-
Complete the task using the Guide Me option that provides guidance tool tips to successfully complete the task
-
Acknowledge the tasks and move them to archive
-
Go to Archived tasks and use the guided tool tips for recurring needs
These recommendations ensure that you are utilizing all the capabilities of NetScaler Console, enable product discovery and functionalities recommended by the product for efficient administration of the deployment.
For more information, see View recommendations and manage your ADCs and applications efficiently.
[NSADM-68719]
StyleBooks
Enable or disable netmask length in StyleBook configuration GUI
When you create a configuration pack from StyleBooks with thetype: ipnetwork attribute, the StyleBook configuration GUI now displays the Netmask Length button next to the IP address field.
You can do one of the following actions:
-
Enable to input netmask length
-
Disable to input netmask IP address
[NSADM-80696]
December 13, 2022
Management and Monitoring
Support for identification and remediation of CVE-2022-27518
NetScaler Console security advisory now supports the identification and remediation of CVE-2022-27518.
Identification of CVE-2022-27518 requires a combination of a version scan and config scan, and remediation requires an upgrade of the vulnerable ADC instances to a release and build that has the fix.
For more information about how to remediate CVE-2022-27518, see Security Advisory.
NOTE
It might take a couple of hours for the security advisory system scan to conclude and reflect the impact of CVE-2022-27518 in the security advisory module. To see the impact sooner, you can start an on-demand scan by clicking Scan Now.
December 09, 2022
Analytics
Discontinuation of Advanced Security Analytics for the premium licensed ADC instances
NetScaler Console no longer supports Advanced Security Analytics for the premium licensed ADC instances. With this upgrade, in the NetScaler Console GUI:
-
The existing configurations in Advanced Security Analytics and the associated behavior-based violations are now not visible.
-
The visibility of the other Bot and WAF violations remain unchanged. For more information, see the Violation Categories.
-
The Splunk and New Relic export are supported only with WAF and Bot violations.
[NSADM-92342]
Configure an action policy from Web Insight
In Web Insight, you can now configure an action policy from graph trend for the following metrics:
-
Client Network Latency
-
Server Network Latency
-
Server Processing Time
As an administrator, when you notice any unusual traffic pattern or a sudden spike in these metrics for any application, this enhancement enables you to create a relative action policy by clicking Create Action Policy after placing it on a specific point in the graph.
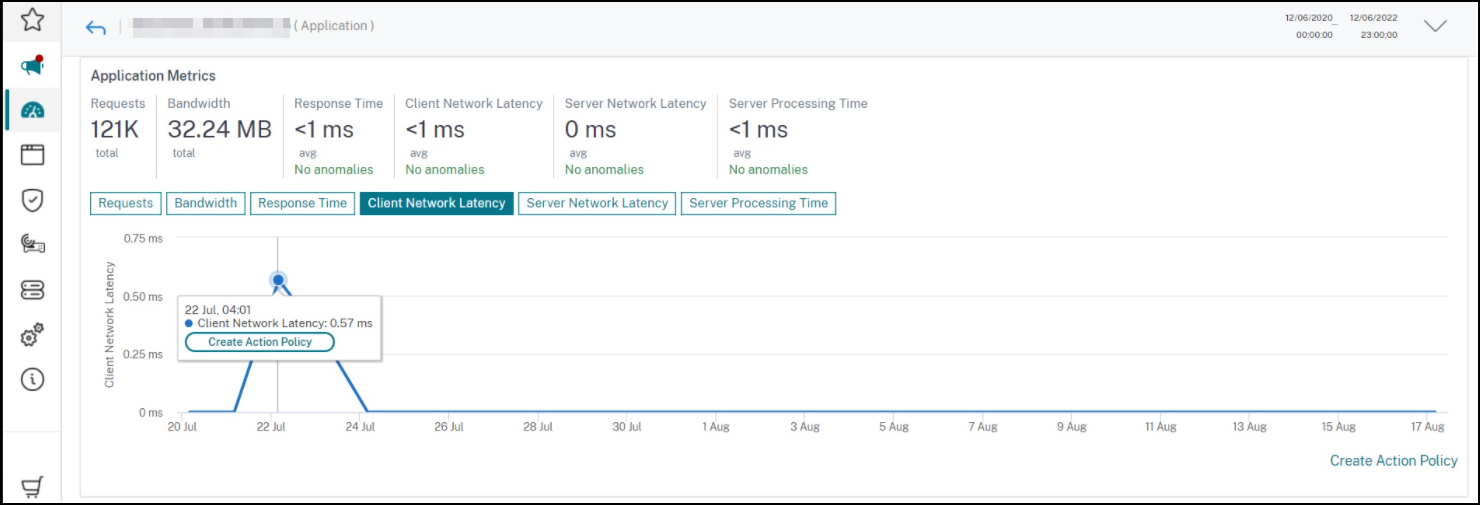
[NSADM-88682]
Action policy - Add multiple applications
When you configure an action policy for Client Network Latency, Server Network Latency, and Server Processing Time, you can now select multiple applications using the IN operator and apply them in a single policy.
For more information, see Action policies.
[NSADM-88680]
November 29, 2022
Infrastructure
Z License expiry information shown in NetScaler Console
You can now view Z License expiry information of MPX and SDX instances in NetScaler Console by navigating to Infrastructure > Pooled Licensing > Pooled Capacity > Z licenses.
[NSADM-80202]
Management and Monitoring
Discontinued SD-WAN and HAProxy features in NetScaler Console
NetScaler Console no longer supports SD-WAN and HAProxy features. As a result, the associated features applicable for SD-WAN and HAProxy are now not available in the NetScaler Console GUI.
[NSADM-90549]
SDX Upgrade improvements - Support for selection of SDX image from the resource library
When you schedule a maintenance job to upgrade an SDX instance in NetScaler Console, you now have the option to select from the image library required for an upgrade. Navigate to Infrastructure > Upgrade Jobs > Create Job, select Upgrade NetScaler SDX, and click Proceed to upgrade an SDX instance.
[NSADM-88832]
Fixed issues
The issues that are addressed in Build November 29, 2022.
-
Users from Azure AD cannot log in to ADM if an administrator added them to DaaS or other NetScaler products before ADM.
[NSHELP-32556]
-
In Infrastructure > Network Functions > Load balancing > Services, the total configured services show only 5000 counts, even when the total configured services count on the ADC instances is greater than 5000.
[NSHELP-32299]
November 16, 2022
Analytics
Integration with New Relic
You can now integrate NetScaler Console with New Relic to view analytics for WAF, Bot, and behavior-based violations in your New Relic dashboard. With this integration, you can:
- Combine all other external data sources in your New Relic dashboard
- Get visibility of analytics in a centralized place
NetScaler Console collects Bot, WAF, and behavior-based events and sends them to New Relic either in real time or periodically, based on your choice. As an administrator, you can also view the Bot, WAF, and other behavior-based events in your New Relic dashboard.
For more information, see Integration with New Relic.
[NSADM-83119]
Infrastructure
Automated upgrade of Autoscale groups
The upgrade operation of Autoscale groups is now automated. Navigate to Infrastructure > Public Cloud > AutoScale Groups and select the Autoscale group you want to upgrade. NetScaler Console performs the required checks and upgrades the Autoscale group.
For more information, see Modify Autoscale Groups.
[ NSADM-84955 ]
Management and Monitoring
Crypto Utilization metrics available on the ADM Service Network Reporting dashboard
You can now add and view the Crypto Utilization metrics in the Network reporting dashboard. Navigate to Infrastructure > Network Reporting > Create Dashboard. Select SSL Crypto Utilization as the entity and create a dashboard for Network Reporting.
[NSADM-88416]
Fixed Issues
The issues that are addressed in Build November 16, 2022.
Asymmetric Crypto Units and Symmetric Crypto Units are now editable fields in the NetScaler Console GUI. You can enter the number of ASUs and SCUs while provisioning a NetScaler VPX instance on the NetScaler SDX appliance with Intel Coleto (COL) chips.
Navigate to Infrastructure > Instances > NetScaler, and on the SDX tab, select an SDX instance where you want to provision a NetScaler VPX instance. In Select Action, select Provision VPX and in the page that displays, enter the crypto capacity under Crypto Allocation
[NSHELP-33297]
November 8, 2022
Management and Monitoring
Support for identification and remediation of CVE-2022-27510, CVE-2022-27513, and CVE-2022-27516
NetScaler Console security advisory now supports the identification and remediation of three new CVEs: CVE-2022-27510, CVE-2022-27513, and CVE-2022-27516.
-
Identification of CVE-2022-27510 requires a combination of config scan and version scan, and remediation requires an upgrade of the vulnerable ADC instances to a release and build that has the fix.
-
Identification of CVE-2022-27513 requires a combination of a config scan and version scan, and remediation requires an upgrade of the vulnerable ADC instances to a release and build that has the fix.
-
Identification of CVE-2022-27516 requires a combination of a config scan and version scan, and remediation requires an upgrade of the vulnerable ADC instances to a release and build that has the fix.
For more information about how to remediate CVE-2022-27510, CVE-2022-27513 and CVE-2022-27516, see Security Advisory.
Note
It might take a couple of hours for the security advisory system scan to conclude and reflect the impact of CVE-2022-27510, CVE-2022-27513, and CVE-2022-27516 in the security advisory module. To see the impact sooner, you can start an on-demand scan by clicking Scan Now.
A security article for HTTP request smuggling attacks is also released along with the bulletin. For information on HTTP request smuggling attacks, see CTX472830.
Note
NetScaler Console security advisory only supports the identification and remediation of the CVEs. It does not support the security concerns that are highlighted in the Security article. Hence, we do not support the identification and remediation of HTTP request smuggling attacks.
[NSADM-88525]
October 28, 2022
Infrastructure
Specify time zone for agent upgrade
In Infrastructure > Instances > Agents > Settings > Upgrade, the start time uses the time zone that you chose in Global Settings > System Configuration.
For more information about setting time zone, see Set the NetScaler Console time zone.
[NSADM-88417]
Fixed Issues
The issues that are addressed in Build October 28, 2022.
In Settings > Licensing & Analytics Config > Configure Analytics, the results on the All Virtual Servers page disappear when you apply the following filters:
- Name
- State
- Type
[NSHELP-32807]
When you configure a second NIC to isolate management access to NetScaler Console, the second NIC IP address is incorrectly assigned the same IP address of the primary NIC.
[NSHELP-32567]
October 12, 2022
Analytics
WAF security violations - View analytics for Command Injection Grammar
In Security > Security Violations, under WAF, you can now view logs and analytics for Command Injection Grammar violation. For more information, see:
[NSADM-85792]
Infrastructure
Validate your Cloud Access Profile with additional permissions
The existing Cloud Access Profile of the Autoscale group that connects to AWS needs additional IAM permissions. Currently, the NetScaler Console service invalidated the Cloud Access Profiles due to missing permissions. To validate IAM permissions, do the following:
- Copy the latest IAM permissions mentioned in Create IAM roles.
- Go to AWS console and validate the Cloud Access Profile’s role with the latest IAM permissions.
[NSADM-90096]
September 27, 2022
Analytics
WAF security violations - View analytics for Block Keyword
In Security > Security Violations, under WAF, you can now view logs and analytics for Block Keyword and JSON Block Keyword violations.
For more information, see:
[NSADM-86225]
Configure bot management on the platinum ADC instances
In NetScaler Console, you can now:
-
Configure bot detection techniques and deploy them on the ADC instances build 13.0 36.27 or later with premium license.
-
View bot analytics by enabling the Bot Security Violations option for the existing virtual servers configured with bot detection techniques either through StyleBook or directly from the ADC instance.
Along with the existing StyleBook configuration, this enhancement further simplifies the process to configure the bot detection techniques and deploy on the ADC instances.
For more information, see Configure bot detection techniques in NetScaler Console.
[NSADM-80413]
Infrastructure
New option to create a configuration job for Autoscale applications
In Autoscale Groups > Configurations, you can now navigate to configuration jobs by selecting an Autoscale application. In the Create Job page, sample commands appear based on the configuration details of the selected application. You can edit values or commands. Also, add or remove commands.
Note
You can use configuration jobs only for the applications created using the ADC CLI Commands mode.
For more information, see Deploy an Autoscale application using configuration jobs.
[NSADM-85939]
NetScaler Console reschedules the jobs when unforeseen events occur
Sometimes, while running a configuration or an upgrade job, you might face the events like:
-
Upgrade of NetScaler Console service is in progress.
-
An ADM agent goes down. It can happen if the agent upgrade is in progress.
In such events, NetScaler Console reschedules the jobs to the following hour.
Earlier, NetScaler Console was not able to identify the ADM service upgrade or the agent state. As a result, jobs were failing after the time-out.
[NSADM-85554]
View usage and license information for unmanaged CICO ADC instances
You can now navigate to Infrastructure > Pooled Licensing > Bandwidth Licenses > CICO to view the usage and license information for unmanaged CICO ADC instances on ADM Service.
[NSADM-85452]
Management and Monitoring
Generate a tech-support bundle for the secondary ADC instance
In an ADC high-availability pair, you can now generate a tech-support bundle for the secondary node as well, from the ADM GUI. Earlier, you were able to generate a tech-support bundle only for the primary node.
[NSADM-88905]
View network reporting data points for each day of the month
In Infrastructure > Network Reporting, when you select one month duration in the dashboard, it shows the data points for each day. Earlier, it was showing the data points for each week.
[NSADM-88875]
StyleBooks
StyleBooks support NetScaler BLX instances
While creating a configuration pack, you can now choose NetScaler BLX instances as the target instances. Earlier, StyleBooks supported NetScaler MPX, SDX, VPX, and CPX instances.
[NSADM-86253]
September 13, 2022
StyleBooks
Improved default StyleBooks to configure a load-balancing virtual server
With the improved default StyleBooks, you can now configure all supported options in ADC for a load-balancing virtual server. For example, you can now set IP pattern, IP mask, IP range, and more. Earlier, you were able to configure only fewer options from StyleBooks. We added the following StyleBooks in NetScaler Console with their improved versions:
| Name | Version |
|---|---|
| lb | 2.0 |
| lb-mon | 2.0 |
[NSADM-80663]
Fixed Issues
The issues that are addressed in Build September 13, 2022.
-
While inviting an IAM group by selecting Azure AD as the identity provider, the ADM roles do not appear under Custom Access if they have whitespaces.
[NSHELP-32557]
-
Users from Azure AD cannot log in to ADM if an administrator added them to DaaS or other NetScaler products before ADM.
[NSHELP-32556]
August 29, 2022
Auto-enabling Gateway Insight and Account Takeover for NetScaler Gateway
All the licensed NetScaler Gateway virtual servers are now automatically enabled with Account Takeover for NetScaler Gateway and Gateway Insight. In NetScaler Console, this enables you to view insights for:
-
Account takeover attacks for NetScaler Gateway in Security > Security Violations. NetScaler Gateway login page availability becomes an easy target for malicious bots to steal user credentials and perform cyberattacks such as credential stuffing and password spraying. As an administrator, you might want to analyze if malicious bots have attempted to take over the NetScaler Gateway account. For more information, see Account Takeover for NetScaler Gateway.
-
Issues related to NetScaler Gateway virtual servers in Gateway > Gateway Insight. As an administrator, you might want to monitor the gateway instances for insights such as user logon activity, logon failure reasons, active users, available users, bot attacks, and so on. For more information, see Gateway Insight.
Note
The auto-enablement for Gateway Insight and Account Takeover for NetScaler Gateway functionality will be released to customers in phases.
Your NetScaler Console must have one or more external NetScaler agents configured and have one or more Premium or Advanced Gateway devices.
After this functionality is released in your NetScaler Console, all the existing licensed NetScaler Gateway virtual servers and the subsequent licensed NetScaler Gateway virtual servers will be automatically enabled with Gateway Insight and Account Takeover for NetScaler Gateway.
For all NetScaler Gateway virtual servers that are manually disabled with Gateway Insight option, the Gateway Insight will not be auto-enabled to those virtual servers.
To disable the Gateway Insight option:
- Navigate to Settings > Licensing & Analytics Configuration.
- Under Virtual Server Analytics Summary, click Configure Analytics.
- In the All Virtual Servers page, select the NetScaler Gateway virtual server and click Edit Analytics.
- Deselect the Gateway Insight option and click Save.
The Account Takeover for NetScaler Gateway is automatically disabled, after the Gateway Insight option is disabled.
[NSADM-82732]
Improvements to the unified dashboard
The Unified Dashboard in Overview > Dashboard is now added with smaller widgets for all key metrics under each category. When you click Edit dashboard, you can:
-
Remove the whole widget (Applications, ADC Infrastructure, Gateway, or Application Security).
-
Remove the smaller widgets present under each widget.
-
Click Add widget and select the required key metrics that you want to view under each widget.
This enhancement enables you to customize the dashboard view by adding or removing the required widgets under each category.
[NSADM-86337]
Choose a country from the selected region
When you’re logging in to the NetScaler Console service for the first time, you can now choose a country that suits your business need. The countries appear based on your selected region. Earlier, you were able to select only regions.
For example, if you select the EMEA region, the GUI lists the following countries:
- France
- United Kingdom
- Germany
Similarly, you can choose a suitable country from other regions.
[NSADM-83643]
Web Insight - View details for cipher related issues
In Applications > Web Insight, under SSL Errors, you can now drill down the Cipher Mismatch to view details such as the SSL cipher name, the recommended actions, and the details of the affected applications and clients.
For more information, see Web Insight.
SNMP version 3 support for SDX configuration on ADM
You can now create an SNMP v3 profile for the NetScaler SDX instance from the ADM GUI. Navigate to Infrastructure > Instances > NetScaler > SDX tab and then click Profiles. You can add all the profile parameters, select v3 as SNMP profile type, and then click Create to create a NetScaler SDX Profile.
[NSADM-84828]
August 16, 2022
Analytics
App Dashboard - View detailed insights to troubleshoot the application issues
In App Dashboard, when you drill down an application, you can now view the Recommended Actions for the following application issues that enable you to view detailed insights to troubleshoot the issues:
-
Response Time
-
Active Services
-
Unstable Server
-
Service Flaps
For more information, see Performance indicators (issues).
[NSADM-84811]
Infrastructure
Dual NIC support for ADM agent
You can configure a second NIC on ADM agent to manage access to NetScaler Console. Using the Dual NIC architecture, ADM agent will now be able to:
-
Establish communication between ADM agent and ADC instances
-
Establish communication between ADM agent and ADM service
For more information, see Dual NIC support on NetScaler Console.
[NSADM-85781]
Recreate a cluster that is part of Google Cloud Autoscale group
To view and troubleshoot the ADC clusters that are part of a Google Cloud (GCP) Autoscale group, you can now navigate to Infrastructure > Public Cloud > Autoscale Group, and click View Clusters.
You can select the GCP cluster and click Recreate to delete the existing cluster and replace it with a new cluster. All the application configurations are transferred to the new ADC cluster.
For more information, see View and troubleshoot ADC clusters.
[NSADM-75731]
Management and Monitoring
View ADM agent details in the unified dashboard
In the unified dashboard, you can now visualize an overview of ADM agent details. In Overview > Dashboard, next to the ADM Agent Status, you can view the agents that are available/unavailable.
Click View Details to visualize an overview of ADM agent details such as total in-built agents, total external agents, agent IP, status, system usage, diagnostic checks, and so on.
For more information, see Unified dashboard overview.
[NSADM-83096]
Fixed Issues
-
After you enable analytics or when you edit analytics for NetScaler Gateway virtual servers configured from the HA pair, the Instance level options under Advanced Settings (optional) appear disabled, even after these options are enabled.
[NSHELP-32188]
-
In Gateway > HDX Insight > Users, when you select a user, instead of showing details for the selected user, ADM shows details for all the users.
[NSHELP-32181]
-
In Gateway > HDX Insight > Instances, when you click a country to drill down for further details, the data under Current Sessions are not displayed.
[NSHELP-32125]
July 13, 2022
Management and Monitoring
Support for identification and remediation of CVE-2022-27509
NetScaler Console security advisory now supports the identification and remediation of CVE-2022-27509.
Identification of CVE-2022-27509 requires a combination of version scan and custom scan, and remediation requires an upgrade of the vulnerable ADC instances to a release and build that has the fix. If your vulnerable ADC instances have the /etc/httpd.conf file copied to the /nsconfig directory, see [Upgrade considerations for customized ADC configurations before planning ADC upgrade.
You can also opt out of these Security Advisory custom scans. For more information on Custom Scan Settings and opting out of custom scans, see the Configure Custom Scan settings section on the Security Advisory page.
For more information about how ADM identifies ADCs vulnerable to CVE-2022-27509 and steps to remediation, see Identify and remediate vulnerabilities for CVE-2022-27509.
Note
It might take a couple of hours for the security advisory system scan to conclude and reflect on the impact of CVE-2022-27509 in the security advisory module. To see the impact sooner, you may start an on-demand scan by clicking Scan Now.
[NSADM-85549]
Configure an access policy for Upgrade Jobs
As a super administrator, you can now configure an access policy, set the permissions (View/Edit) for the Upgrade Jobs, and apply the policy to your NetScaler Console users. In Settings > Users & Roles > Access Policies, click Add to configure an access policy by selecting Infrastructure > Upgrade Jobs under Permissions.
For more information, see Configure access policies on NetScaler Console.
[NSADM-82494]
Support for configuration audit in NetScaler BLX instances in shared mode
You can now create Configuration Audit templates with certain configurations and monitor the configuration changes in NetScaler BLX instances in shared mode. For more information, see Create audit templates.
[NSADM-82323]
Support for CSV format and schedule export in Web transaction analytics
In Web transaction analytics, you can now view the following enhancements when you click the Export icon:
-
In Export Now, you can export data in CSV format.
-
The Schedule Export option is introduced that enables you to schedule and export the data in CSV format through email and Slack.
For more information, see Web transaction analytics.
Fixed Issue
In NetScaler Console service, when you navigate to Infrastructure > Instances > Agents, and click Settings to change the agent upgrade settings, a confirmation message Modified Agent Upgrade Settings is displayed once the settings are changed.
[NSHELP-32099]
June 29, 2022
Applications
Configure and associate an application to multiple custom applications
In Application Dashboard, you can now configure an application and associate it to multiple custom applications. Using this feature, you can reuse the same application for multiple custom applications, rather than creating a separate application for each custom app.
For more information, see Configure and associate an application to multiple custom applications.
[NSADM-82040]
Management and Monitoring
Supported browsers to access NetScaler Console GUI
NetScaler Console GUI is now accessible only from the following compatible browser versions:
| Web browser | Version |
|---|---|
| Microsoft Edge | 79 and later |
| Google Chrome | 51 and later |
| Safari | 10 and later |
| Mozilla Firefox | 52 and later |
[NSADM-83943]
June 15, 2022
Infrastructure
Monitor the NetScaler agent system parameters usage and remediate issues using the self-heal daemon
The NetScaler agent now monitors its system resources (CPU, Memory, and disk) by automatically running the self-heal daemon in the background. The self-heal daemon checks for thresholds and applies actions automatically during the following scenarios:
-
If the disk usage exceeds 80% or more for a specific duration, clean-up space (logs, backup logs, core files, crash files, and so on) action is applied to reclaim the disk space.
-
If the memory and CPU usage exceeds 90% or more for a specific duration, ADM processes are restarted to reclaim the CPU and memory.
Note
The self-heal daemon does not monitor the thresholds configured in Infrastructure > Instances > Agents > Settings > Notification.
[NSADM-82558]
June 07, 2022
Analytics
View Bot and WAF analytics for custom apps
In Security > Security Violations, under WAF and Bot, you can now select a custom app and view the consolidated applications details that are applicable for a custom app. You can also select an application from the list and view details for a particular application of the custom app.
For more information, see Security violations.
[NSADM-77375]
Management and Monitoring
Import and install the SSL certificate bundle (with certificate chain) through the Certificate Store
In Infrastructure > SSL Dashboard, when you select Manage Certificate Store from the list available next to Settings, you can:
-
Click Import ADC Certificates > Start Polling and the SSL certificate bundle along with the certificate chain that links the server certificate to its issuer (the intermediate CA) is imported from the ADC instance to the Certificate Store.
-
View the certificates in the Certificate Store, select a certificate, and click Install to install the certificate along with the certificate chain on the selected ADC instances.
[NSADM-82727]
Upgrade support for NetScaler BLX instances
In Infrastructure > Upgrade Jobs, you can now create a job to upgrade NetScaler BLX instances. You must select the appropriate build image (applicable for Ubuntu or Red Hat) for a successful upgrade. For more information, see Maintenance jobs.
[NSADM-82324]
Fixed Issue
In Infrastructure > Event Summary > Syslog Messages, the data was displayed only for the last 30 days. With this fix, the data is displayed for up to 180 days.
[NSHELP-30961]
May 10, 2022
Analytics
Export realtime data to Splunk
The integration of NetScaler Console with Splunk now enables you to export realtime data to Splunk. In the ADM GUI, when you select the Realtime Export option and configure, the selected violations in NetScaler Console are pushed to Splunk immediately.
For more information, see Integration with Splunk.
[NSADM-84529]
Improvements to WAF learning engine
In NetScaler Console, you can now configure a learning profile and deploy or skip the relaxation rules for the following additional security checks:
-
JSON SQL
-
JSON Command Injection
-
JSON XSS
Note
To configure a learning profile using these security checks, the NetScaler instance must be 13.1–14.10 or later.
For more information, see WAF learning engine.
[NSADM-80921]
Applications
Improvements to the unified dashboard
The unified dashboard in Overview > Dashboard now enables you to customize it based on your choice. Using the Edit dashboard option, you can:
-
Drag widgets
-
Remove widgets
-
Add widgets
-
Reset to default
After making changes, click Save.
Note
By default, all widgets are displayed. If you have customized the dashboard, saved the changes, and use the Reset to default option, the last saved customized dashboard is restored.
[NSADM-52144]
Infrastructure
Improvements to ADM GUI
You can now expand or collapse the ADM GUI navigation menu individually. This improvement enables you to view all options in each section.
[NSADM-85480]
Support for identification and remediation of CVE-2022-27507 and CVE-2022-22508
NetScaler Console security advisory now supports the identification and remediation of two new CVEs: CVE-2022-27507 and CVE-2022-22508.
-
Identification of CVE-2022-27507 requires a combination of a version scan and config scan, and remediation requires an upgrade of the vulnerable ADC instances to a release and build that has the fix.
ADM Security Advisory does not support mitigation. If you have applied mitigation (temporary workaround) to the ADC instance, ADM will still identify the ADC as vulnerable until you have completed remediation.
For CVE-2022-27507, even if you have applied mitigation and temporarily disabled HDX Insight for EDT traffic, (see Security Bulletin), ADM Security Advisory will still identify the ADC as vulnerable until you have completed remediation (upgrade to a release and the build that has the fix).
-
Identification of CVE-2022-27508 requires a combination of a version scan and config scan, and remediation requires an upgrade of the vulnerable ADC instances to a release and build that has the fix.
For more information about how to remediate CVE-2022-27507 and CVE-2022-22508, see Security Advisory.
Note
It might take a couple of hours for the security advisory system scan to conclude and reflect the impact of CVE-2022-27507 and CVE-2022-27508 in the security advisory module. To see the impact sooner, you may start an on-demand scan by clicking Scan Now.
[NSADM-85673]
Fixed Issue
In Infrastructure > Instances > NetScaler, when you change an admin profile password and include % in the password, an error message is displayed.
[NSHELP-31392]
April 27, 2022
Management and Monitoring
ADC downgrade through ADM GUI with the correct ns.conf file
In Infrastructure > Upgrade Jobs, when you create an upgrade job to upgrade the ADC instance to a lower version, ADM now selects the compatible ns.conf file from which the configuration is applied to the ADC instance. The selected ns.conf file must be of the same version or lower than the version selected by the user. If there is no suitable ns.conf file present in the ADC instance, downgrade is not allowed and the appropriate error message is displayed.
[NSADM-81421]
Fixed Issues
-
When you enable Advanced Security Analytics, apply profile with one or more behavior-based violations, and click Save, the details in the table are not displayed in Settings > Licensing & Analytics Configuration > All Virtual Servers.
Note: The behavior-based violations are Excessive Client Connections, Unusually Large Upload Transactions, Unusually Large Download Transactions, and Unusually High Request Rate.
[NSADM-85020]
-
In Infrastructure > Event Summary > Syslog Messages, the data was displayed only for the last 30 days. With this fix, the data is displayed for up to 180 days.
[NSHELP-30961]
April 12, 2022
Analytics
New violations added for rate limiting bot violations
The rate limiting rule detects multiple requests coming from the same client. In Security > Security Violations > Application Overview, under Bot, you can now view the following violation details:
-
URL
-
Source IP
-
Geo Location
-
Session
Click Logs to view details such as time, client IP, bot type, bot detection, and so on. For more information, see View bot violation details.
[NSADM-80925]
Headless Browser violation support in bot violation
In Security > Security Violations > Application Overview, under Bot, you can now view Headless Browser violation details. Click Logs to view details such as time, client IP, bot type, bot detection, and so on.
For more information, see View bot violation details.
[NSADM-89027]
Management and Monitoring
CVE-2022-21827 not in scope of NetScaler Console Security Advisory
The CVE-2022-21827 impacts the NetScaler Gateway plug-in for Windows supported versions prior to 21.9.1.2.
The detection and remediation of vulnerabilities impacting the NetScaler Gateway plug-in for Windows is not supported by the NetScaler Console. Also, NetScaler Gateway plug-in vulnerabilities cannot be assessed by performing any checks on ADC side, verifying the ADC version, or by checking the ADC configuration. The detection and remediation for this CVE can only be assessed based on the version of the NetScaler Gateway plug-in for Windows deployed on the client.
As a result, the detection and remediation of this vulnerability is out of NetScaler Console Security Advisory scope.
For more information, see Unsupported CVEs in Security Advisory.
Unsubscribe option available in product emails sent to customer
Customers (New customers and Inactive) now have the option to unsubscribe to all the email notifications within the product emails sent by NetScaler Console. For more information to subscribe or unsubscribe, see Email subscriptions.
[NSADM-83272]
Retain filters in app dashboard
In Applications > Dashboard, when you apply filters through the search bar and key metrics, the filters are now retained. You can view the same filters even if:
-
You return to Applications > Dashboard from a different navigation within the ADM GUI.
-
You close the browser and open a new session from the same browser.
Note
The filters are not retained if you open a new session from a different browser or in an incognito mode.
[NSADM-82038]
StyleBooks
Auto-update of config packs
When an SSL certificate is updated in the NetScaler Console certificate store, the config packs associated with the SSL certificate are automatically updated.
[NSADM-80694]
March 31, 2022
Analytics
Improvements to Advanced Security Analytics in Security Violations
As an improvement to the Advanced Security Analytics feature, the process to first enable Advanced Security Analytics and then create a profile by using the Settings icon is now simplified. You can now enable Advanced Security Analytics, create a profile, and assign the profile to the virtual servers in a single workflow.
For more information, see Enable Advanced security analytics.
[NSADM-81383]
Improvements to the unified dashboard
In Overview > Dashboard, you can now view the following improvements:
-
You can click the key metric counts under all categories to view details of the affected ADC instance/application/Gateway.
-
Under Applications, minor GUI changes made in SSL key metrics to visualize more information.
-
Under Gateway, the Users Geo Distribution displays the top 3 countries based on the user counts.
[NSADM-82758]
Management and Monitoring
Support for ECDSA algorithm in SSL dashboard
When you configure an enterprise policy in SSL dashboard > Settings > Enterprise Policy, you can now select ECDSA in the Recommended Signature Algorithm.
For more information on ECDSA, see ECDSA cipher suites support.
For more information on enterprise policy configuration, see Configure an enterprise policy.
[NSADM-71321]
Onboarding
ADM support for Kubernetes version 1.23
NetScaler Console now supports adding and managing clusters with Kubernetes version 1.23.
[NSADM-83683]
March 16, 2022
Onboarding
Test Onboarding Readiness of ADC instances
When you want to onboard an ADC instance on to NetScaler Console using the default built-agent option, you can perform a test run to ensure that the ADC instance is ready to onboard. For more information, see Test onboarding readiness of ADC instances.
[NSADM-80502]
March 01, 2022
Management and Monitoring
Invite users or groups to ADM from the Azure AD
As a super administrator, you can now invite users or groups to NetScaler Console from the connected Azure AD to NetScaler Console. Before doing so, ensure that the Azure AD is connected to Citrix Cloud, see Connect Azure Active Directory to Citrix Cloud. Earlier, you were only able to invite users with Citrix Identity.
When you select Azure AD as the identity provider, you can specify only Custom Access for the selected user or group. The users can log in to NetScaler Console using their Azure AD credentials. With this feature, you don’t require to create a Citrix Identity for the users who are part of the selected Azure AD. If a user is added to the invited group, you don’t require to send an invite for the newly added user. This user can access NetScaler Console using the Azure AD credentials.
[NSADM-81039]
Certificates and Key files uploaded to ADC are saved by ADM and the information is stored in the ADM database
When you upload certificates and Key files to Cert Store using the SSL Dashboard in the ADM Service GUI, only the metadata and the encrypted contents of the certificate file are saved in ADM Database. The key and password used to decrypt the content are saved in Cloud Wallet.
[NSADM-72475]
New network reports in ADM
The following new network reports are added as the total counters:
-
Authentication Success vs Failures
-
HTTP Authentication Success vs Failures
-
Non-HTTP Authentication Success vs Failures
-
AAA Sessions
-
Current AAA Sessions
-
Current ICAOnly Sessions
-
Current ICAOnly Connections
-
Current ICA(Smart Access) Connections
You can use these counters to add thresholds and receive notifications. For more information see Network reporting.
[NSADM-62239]
Action policy - Configure Bot and WAF notifications with transaction details
In Action Policies, when you configure an action policy, you can now select Bot Violation per Client and WAF Violation per Client options. These options enable you to configure and receive notifications with transaction details such as client IP, total attacks, violation type, and so on.
For more information, see Configure an action policy to receive application event notifications.
[NSADM-80630]
Opt out of Security Advisory Custom Scans
NetScaler Application Delivery Management Service UI now allows you to opt out of security advisory custom scans. When you opt out of these Security Advisory Custom scans, the impact of the CVEs that need a custom scan will not be evaluated for your ADC instances in the Security Advisory.
To opt out of Security Advisory Custom Scans, see Custom Scan settings.
[NSADM-80288]
StyleBooks
Use HTML formatting tags in the StyleBook description and header
In the StyleBook definition, you can now include a header field and use HTML formatting tags for the text. You can also include images as part of the header and it will be rendered at the top of the configuration form. This feature allows you to add infographics for the StyleBook users that help in understanding the StyleBook configuration. If you use images in the header, ensure to use base64 encoded image format in the image tag.
name: app-stylebook-with-HTML-tags
namespace: com.examples.stylebooks
version: `1.0`
display-name: `Example App StyleBook`
header: 'This <b> StyleBook </b> defines all the app configuration for <i>Load Balanced Application </i>. The following image describes the target deployment for the app <img id=`b64img` src=`data:image/png;base64,` />'
<!--NeedCopy-->
[NSADM-80699]
Deliver Autoscale applications that are outside of ADC instances’ virtual network or VPC
When application servers and ADC instances are situated on different Virtual networks, VPC Networks, and Subnets, provide the CIDR block of a subnet or VPC where you have application servers. Specify the CIDR block in the Origin Server field while configuring the provision parameters. This way you can deliver apps from the application servers that are situated outside of the ADC instances’ virtual network or VPC network.
Earlier, this feature was available only for the Autoscale groups in AWS, now you can use this feature in Azure and Google Cloud also.
For more information, see:
-
[NSADM-78617]
February 10, 2022
Management and Monitoring
Support for the ShowConfiguration template
In the Configuration Editor, when you select Batch Configuration, you can now use the ShowConfiguration template. Drag the ShowConfiguration template to the right pane and enter the show commands to run on NetScaler instances.
For example, you can enter commands such as sh ns info, sh node, sh ns stats, and sh interface, shell ls /var/tmp and view the output.
You can download the output of the commands as a text file.
[NSADM-66132]
Configure an action policy to receive application event notifications
Apart from the existing analytics view of application events, you can configure an action policy to get application event notifications through Slack, Email, PagerDuty, or ServiceNow. The application events include performance issues, bot and WAF violations, and service graph violations. As an administrator, using the action policy, you can get event notifications in real time.
Using the action policy, you can:
-
Predefine certain conditions for the application events.
-
Get notified for the following events through Slack, Email, PagerDuty, and ServiceNow:
-
WAF SQL Violation
-
WAF XSS Violation
-
WAF Infer XML Violation
Note
To receive the WAF violation notification, the minimum violation transactions must be 20%. For example, out of 100 transactions, minimum 20 must be violation transactions.
-
Top 3 WAF violations
(Total violations contributed by SQL, XSS, XML together must be 30%. For example, out of 100 transactions, 30 or more transactions must be a combination of SQL, XSS, Infer XML violations.)
-
Bot violations
(For more information on the list of bot violation, see violation categories.)
-
App score violation
-
Client network latency
-
Server network latency
-
Server processing time
-
Service graph violation
-
For more information, see Configure an action policy to receive application event notifications.
[NSADM-70968], [NSADM-76588], [NSADM-72799]
Applications
Improvements to service graph
In global service graph and microservices service graph, you can now view the legend that provides the description for symbols available in service graph.
[NSADM-82077]
Onboarding
Configure settings for low-touch onboarding workflow emails
As a part of ADM Service Connect based low-touch onboarding workflow, you receive product initiated emails from NetScaler Console service. You can configure and manage the emails that you receive as part of this workflow in the following ways:
-
Enable emails for all admins
-
Enable / disable emails for selected admins
-
Disable emails for all admins
For more information to configure and manage emails, see Email Settings.
[NSADM-80289]
View NetScaler agent diagnostics and receive alerts for endpoint verification
NetScaler Console now performs a periodic (every one hour) diagnostic check for NetScaler agent and provides the following information:
-
Endpoint reachability
-
Health check probe
-
Agent proxy
If the agent endpoint reachability status changes (from OK to Needs Review), the super administrator receives an email notification comprising the issue details.
For more information, see View agent diagnostics and receive alerts for endpoint verification.
[NSADM-69407]
StyleBooks
Updates of the StyleBook configuration pack are automatically reconciled
Sometimes, updating a StyleBook configuration pack that is deployed on an ADC instance can have differences from its deployed state. In such cases, the configuration pack update fails. The StyleBook engine now automatically reconciles these differences and updates the configuration pack. Earlier, a message appeared on the GUI that needed your confirmation to reconcile the changes before updating the configuration pack.
[NSADM-80660]
Manage data sources in ADM
Defining a data source in NetScaler Console helps you to use data from external sources as an input while creating or updating StyleBook configurations. Otherwise, you have to explicitly supply each input required by the StyleBook. In NetScaler Console, you can use any managed ADC instance as a data source for the input to a StyleBook configuration. In NetScaler Console, you can use the managed ADC instances as data sources. You can also define custom data sources which can serve as input when creating or updating configurations. To view custom data sources, go to Applications > Configuration > Data Sources.
Use the datum built-in type in the StyleBook definition to define a data source.
Example:
parameters:
-
name: selected-lb
label: Select an existing ADC
type: datum
required: true
data-source:
type: managed-adc
<!--NeedCopy-->
In this example, the datum parameter is used to define the managed-adc data source. This data source allows you to retrieve data from the ADC instances managed by NetScaler Console.
[NSADM-80659]
Check the StyleBook compatibility for a configuration pack
When you are changing the StyleBook for a configuration pack in the ADM GUI, you can now determine the changes from the newly selected StyleBook definition. And, how these changes affect the configuration pack. With this information, you can make necessary updates to the StyleBook definition before changing it. Or, you can decide to continue with the existing StyleBook.
For example, if you change the StyleBook for a configuration pack, the existing StyleBook can have an allowed port HTTPS whereas the newly selected StyleBook can have SSL. In this case, you may need to edit the same HTTPS values for SSL port as well.
[NSADM-80664]
January 25, 2022
ADC low touch onboarding to ADM – View automated diagnostics
The following information is applicable only for the ADC instances that are connected to ADM Service through ADM service connect feature.
Earlier there was a manual process to use the diagnostic tool to troubleshoot the low touch onboarding issues. Now, you can also view diagnostic information about the ADC instances that have issues in low touch onboarding on the ADM GUI.
When you are in the ADM Service Connect based low touch onboarding workflow, in the Asset Inventory page you can see the newly added Onboarding Readiness option that provides the ADC instance onboarding readiness status such as Needs Review or OK.
You can also see this view by navigating to Infrastructure > Instances > NetScaler and clicking the Asset Inventory option.
You can then use this information to understand and resolve the issues.
For more information, see Troubleshoot issues using the diagnostic tool or the ADM GUI.
[NSADM-77245]
Support for low touch onboarding of customers not yet on Citrix cloud
As a part of the Low-touch onboarding of NetScaler instances using ADM Service Connect workflow, customers who are not yet on Citrix Cloud will now be able to sign-up to Citrix cloud and onboard their ADC instances onto ADM Service easily. These customers will receive an email from NetScaler Console service guiding them to Onboard to ADM Service. By clicking on this button, they can then sign up to Citrix Cloud and onboard their ADC instances on to ADM Service using the low touch onboarding workflow. For more information, see Low-touch onboarding of NetScaler instances using service connect.
[NSADM-76466]
Infrastructure Analytics - Configure notifications for specific issues
In Infrastructure Analytics, you can now select the required issues, enable notifications for issues that breach the configured thresholds, and receive notifications only for the selected issues. Earlier, notifications were received for all issues. This enhancement enables you to receive notifications only for the selected issues that you want to monitor.
For more information, see Configure notifications.
[NSADM-76361]
January 17, 2022
ADM support for BLX cluster
You can now add the BLX cluster in ADM. In the ADM GUI, the Cluster IP address (CLIP) is added and the count of the cluster nodes is now visible in the dashboard.
[NSADM-78588]
A unified dashboard to view instance key metric details
As an administrator, you can now visualize a dashboard that provides an overview of key metric details based on:
-
Applications
-
ADC Infrastructure
-
Application Security
-
Gateway
This single-pane dashboard enables you to view details for a better monitoring experience of the instance usage and performance. For more information, see A unified dashboard to view instance key metric details.
[NSADM-74075]
Security violation - JSON SQL Injection Grammar
In Security > Security Violations, under WAF, you can now view the JSON SQL Injection Grammar violation for the selected application. For more information, see Violation details.
[NSADM-62909]
Use the StyleBook’s reserved keywords for parameters and expressions
You can now use the reserved keywords when you define parameters and expressions in a StyleBook definition. The reserved keywords are as follows:
"and", "false", "in", "not", "true", "or"
<!--NeedCopy-->
For example, a parameter named not is now a valid parameter ($parameters.not).
[NSADM-80657]
StyleBooks support nested parameter-conditions
In a StyleBook definition, you can now specify a parameter condition within a parameter condition. These conditions are called nested parameter conditions and use a repeat construct to define these conditions. The nested parameter conditions are useful when you want to apply an action to each item of a list parameter.
Example:
parameters-conditions:
-
repeat: $parameters.lbvservers
repeat-item: lbvserver
parameters-conditions:
-
target: $lbvserver.port
action: set-allowed-values
condition: $lbvserver.protocol == "HTTPS"
value: $parameters.ssl-ports
<!--NeedCopy-->
In this example, when the user selects the HTTPS protocol for a load balancing virtual server, the port values are dynamically populated. And, it applies for each load balancing virtual servers in the list.
For more information, see Nested parameter conditions.
[NSADM-62747]
Fixed Issue
In a GSLB setup, when you have the same domain name for multiple ADC instances, the entity polling incorrectly updates the database.
[NSHELP-29885]
In this article
- Notice about Syslog feature deprecation
- April 10, 2024
- Fixed Issues
- March 26, 2024
- March 12, 2024
- February 28, 2024
- February 06, 2024
- January 24, 2024
- January 16, 2024
- January 09, 2024
- December 13, 2023
- November 29, 2023
- November 09, 2023
- October 25, 2023
- October 10, 2023
- September 26, 2023
- September 13, 2023
- August 31, 2023
- August 11, 2023
- August 09, 2023
- July 26, 2023
- July 18, 2023
- July 12, 2023
- July 03, 2023
- June 14, 2023
- May 31, 2023
- May 18, 2023
- May 09, 2023
- April 25, 2023
- April 13, 2023
- April 05, 2023
- March 14, 2023
- March 02, 2023
- February 07, 2023
- January 24, 2023
- January 10, 2023
- December 13, 2022
- December 09, 2022
- November 29, 2022
- November 16, 2022
- November 8, 2022
- October 28, 2022
- October 12, 2022
- September 27, 2022
- September 13, 2022
- August 29, 2022
- August 16, 2022
- July 13, 2022
- June 29, 2022
- June 15, 2022
- June 07, 2022
- May 10, 2022
- April 27, 2022
- April 12, 2022
- March 31, 2022
- March 16, 2022
- March 01, 2022
- February 10, 2022
- January 25, 2022
- January 17, 2022