Citrix SD-WAN integration with AWS Transit Gateway Connect
Citrix SD-WAN supports integration with AWS Transit Gateway Connect to deliver a consistent, high performing, and secure overlay network for the branch and home office users to access cloud applications.
AWS Transit Gateway allows you to create and manage gateways to connect your Amazon Virtual Private Cloud (Amazon VPC) deployments and on-premises networks.
AWS Transit Gateway Connect integrates Citrix SD-WAN and AWS Transit Gateway and simplifies the ability to build and manage global private networks.
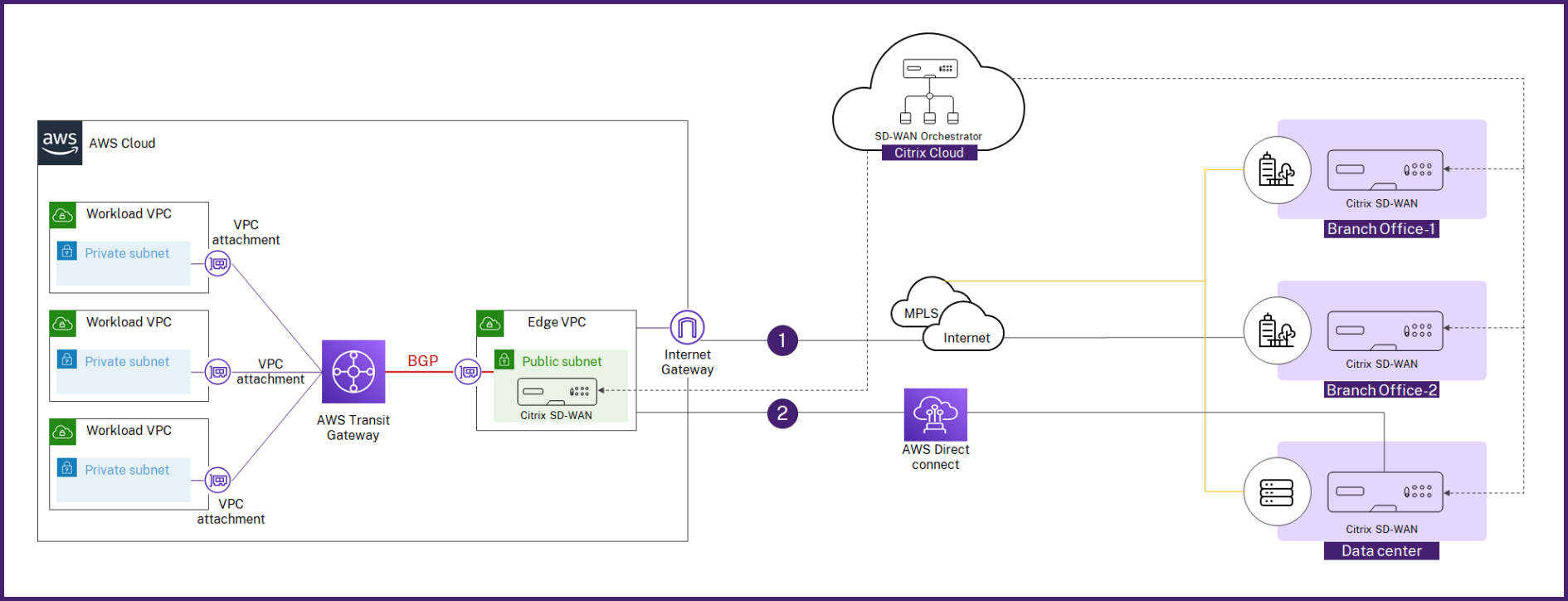
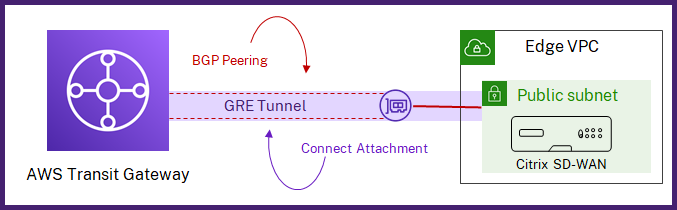
With AWS Transit Gateway Connect, you can create a Connect attachment that establishes Connect peer (GRE tunnel) between Citrix SD-WAN VPX and AWS Transit Gateway. The Connect attachment supports the Generic Routing Encapsulation (GRE) tunnel protocol for high performance, and Border Gateway Protocol (BGP) for dynamic routing.
Each Connect peer on the Connect attachment supports a maximum bandwidth of 5 Gbps. To achieve higher throughput, you can add more Connect peers and scale up to 20 Gbps per Connect attachment (maximum 4 GRE tunnels per Connect attachment). If more than 20 Gbps aggregated bandwidth is needed, you can scale horizontally by creating more Connect attachments.
You can set up connectivity between Citrix SD-WAN and Transit Gateway connect by using the integrated workflow in Citrix SD-WAN Orchestrator.
Prerequisites
- AWS account (AWS Subscription ID, Secret Access Key, and Access Key ID) with required permissions to create the following resources:
- VPC attachment and Transit Gateway Connect attachment
- Transit Gateway CIDR Block
- Connect Peer on the Connect Attachment
- Route in the site’s LAN subnet associated route table.
- A Citrix SD-WAN VPX site configured in Citrix SD-WAN Orchestrator service. Make sure to configure the same AWS Subnet CIDR associated with LAN interface as the IPv4 address on the virtual interface of LAN interface.
- Deployed Transit Gateway. If not already deployed, you can create a Transit Gateway from the AWS Management Console.
- Do not use AWS reserved BGP CIDR Blocks anywhere in the AWS site configuration as these CIDR blocks are used as tunnel IP/Prefix for creating LAN GRE tunnel. For AWS reserved blocks, see Connected Peers.
- AWS region selected must have AWS Transit Gateway Connect support. AWS Transit Gateway Connect support is available only in the AWS regions listed under Requirements and considerations.
- GRE protocol must be allowed in the security group associated with the AWS LAN subnet of the site.
Configuration
At the customer level, navigate to Configuration > Delivery Channels > Delivery Services. In the SaaS and Cloud On-Ramp Services section, select the AWS Transit Gateway tile. The AWS Transit Gateway page is displayed.
You can also navigate to AWS Transit Gateway page from Configuration > SaaS & Cloud On Ramp > AWS Transit Gateway.

On the top right corner of the page, click the Authentication link.
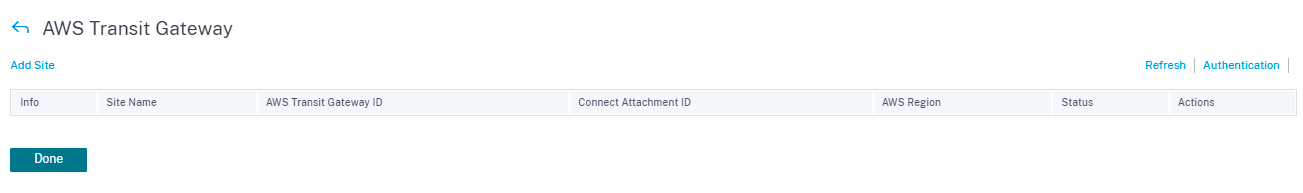
Enter the AWS Subscription ID, AWS Secret Access Key, and AWS Access Key ID.
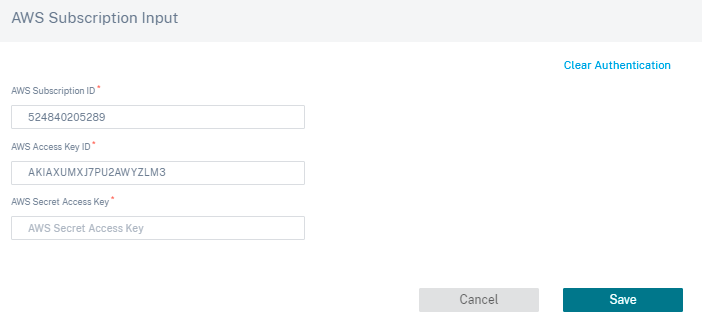
Select a site that is deployed in VPC in which you want to deploy Transit Gateway Connect attachment.
Note
Only the sites that are deployed in AWS are listed.
Based on the site selected, the AWS Region and VPC ID are auto populated.
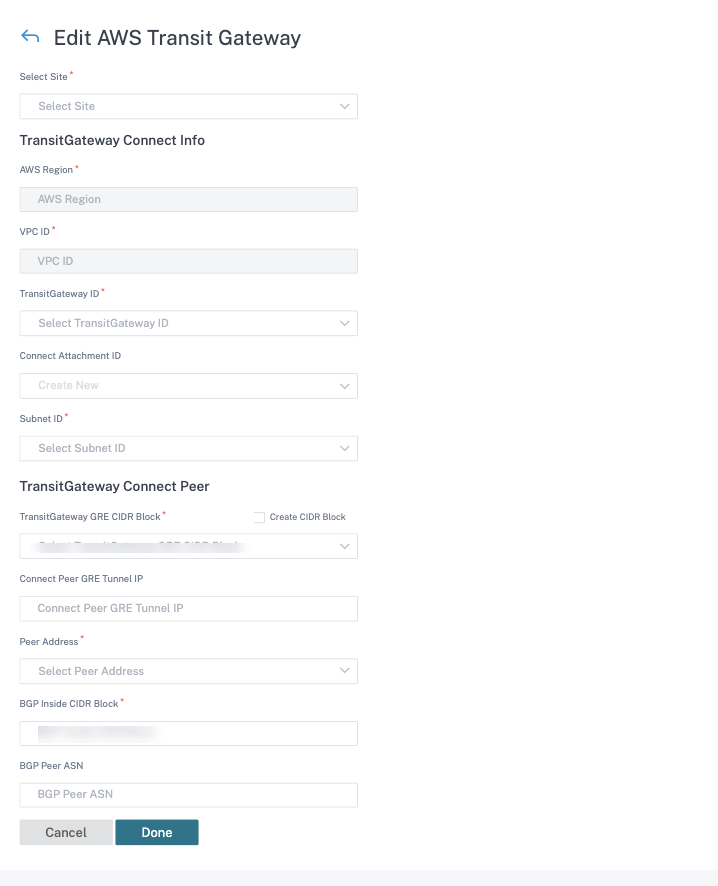
- Transit Gateway ID: A network transit hub that interconnects attachments (VPCs and VPNs).
- Connect Attachment ID: A unique identifier for the Transit Gateway Connect Attachment. A Connect Attachment allows you to establish connectivity between a Transit Gateway and third party appliances using GRE and BGP. You can either select an existing Connect Attachment ID or create an ID as needed.
- Subnet ID: The AWS Subnet CIDR where the SD-WAN VPX LAN Interface is present.
Click + Connect Peer to create Transit Gateway Connect Peer. A Transit Gateway Connect Peer creates a GRE tunnel between the Citrix SD-WAN VPX in an AWS region and the Transit Gateway. The GRE tunnel is created by picking the IP addresses of the Transit Gateway CIDR block and SD-WAN VPX’s LAN IP address.
- Transit Gateway GRE CIDR Block: The IP addresses that are used for establishing GRE tunnel. You can either select an existing CIDR block or create a new one by selecting the Create Transit Gateway GRE CIDR Block check box.
- Connect Peer GRE Tunnel IP: The GRE tunnel Peer IP address on Transit Gateway side.
- Peer Address: The LAN IP address of Citrix SD-WAN VPX.
- BGP Inside CIDR Block: The range of inside IPv4 addresses that are used for BGP peering. Specify a /29 CIDR block from the 169.254.0.0/16 range.
- BGP Peer ASN: The Border Gateway Protocol (BGP) Autonomous System Number (ASN) of the Citrix SD-WAN VPX. You can use an existing ASN assigned to your network. If you do not have one, you can use a private ASN in the 64512–65534 range.
Note
- AWS imposes certain restrictions on Transit Gateway CIDR Block and BGP Inside CIDR. For more details on the restrictions, see Transit Gateway CIDR Block and BGP Inside CIDR.
- If Connect Peer GRE tunnel IP is not specified, then AWS auto-assigns the IP address by picking one of the IP addresses from the configured Transit Gateway CIDR block. If you want to specify a particular IP address, ensure that it is in Transit Gateway CIDR block range.
Click Done and then Save.
Click Deploy from the Action column. The deployment process takes approximately 5 minutes and you can view the status by clicking the Refresh button.
Note
- The name of the auto-created LAN GRE tunnel is in the following format:
AWS_TGW_Connect-Tunnel-<number>
<number> is the number of GRE tunnels auto-created for the site, incremented by one.
- Identity is disabled on all the existing Virtual IP addresses of the LAN virtual interface which is configured in the Connect Peer and is enabled only on the newly added Virtual IP address (BGP Peer IP assigned to the site by AWS).
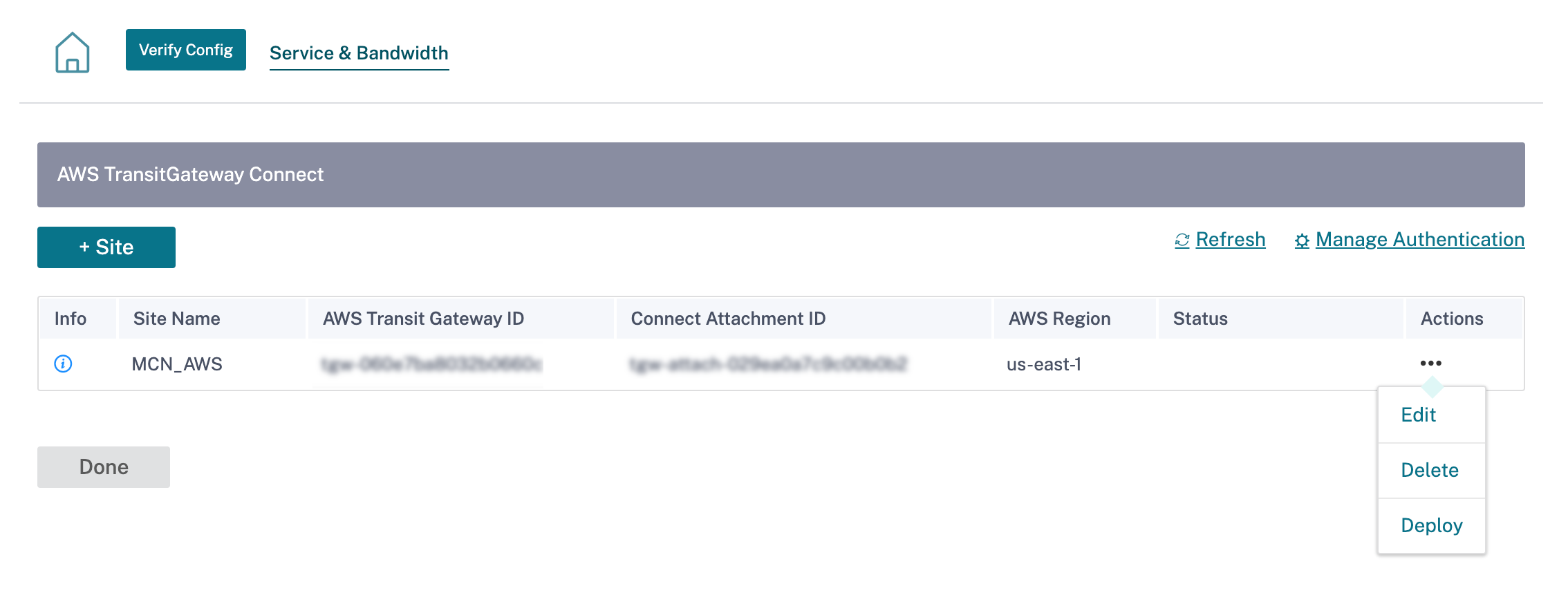
You can activate the configuration changes across the network using Deployment Tracker. After successful activation, the GRE tunnels are established between the Citrix SD-WAN VPX and AWS Transit Gateway. The following configurations are auto-created for the site when you click verify config and proceeds with staging and activation:
- LAN GRE tunnel
- BGP and BGP ASN
- BGP Neighbors
- Import Filter
- Export Filters
- Additional Virtual IP on LAN Virtual Interface
Monitoring and troubleshooting
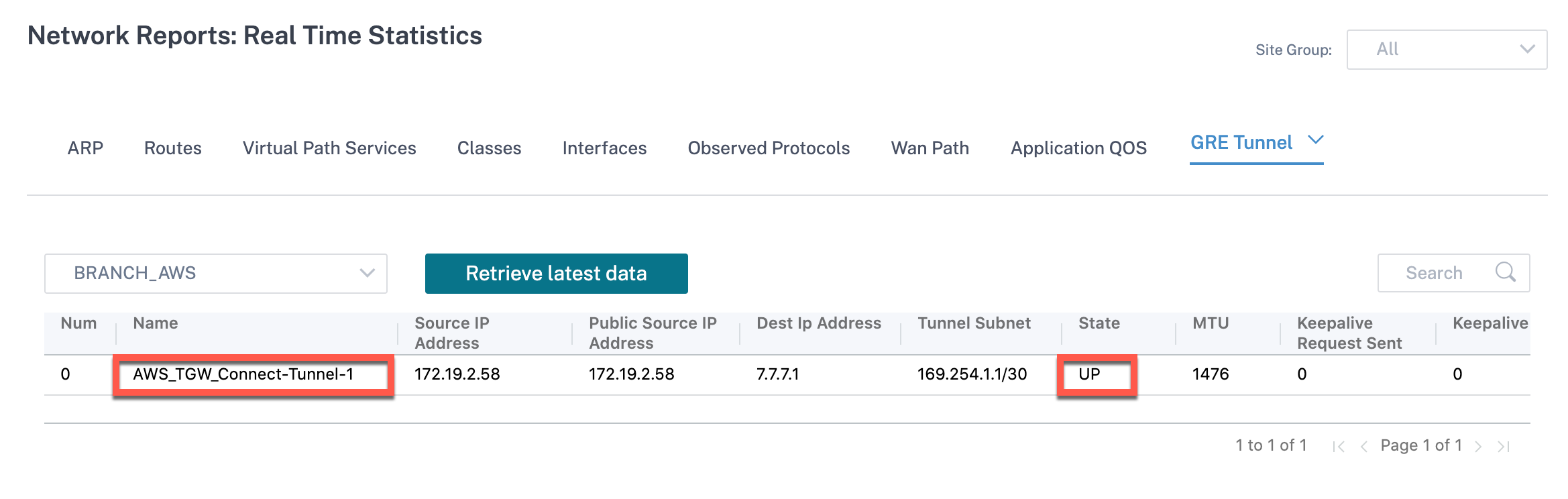
To verify the GRE tunnel establishment status, navigate to Reports > Real Time > Statistics > Other Stats > GRE Tunnel. In the following screenshot, you can see that the GRE tunnel is established from SD-WAN towards AWS Transit Gateway and the state is UP.
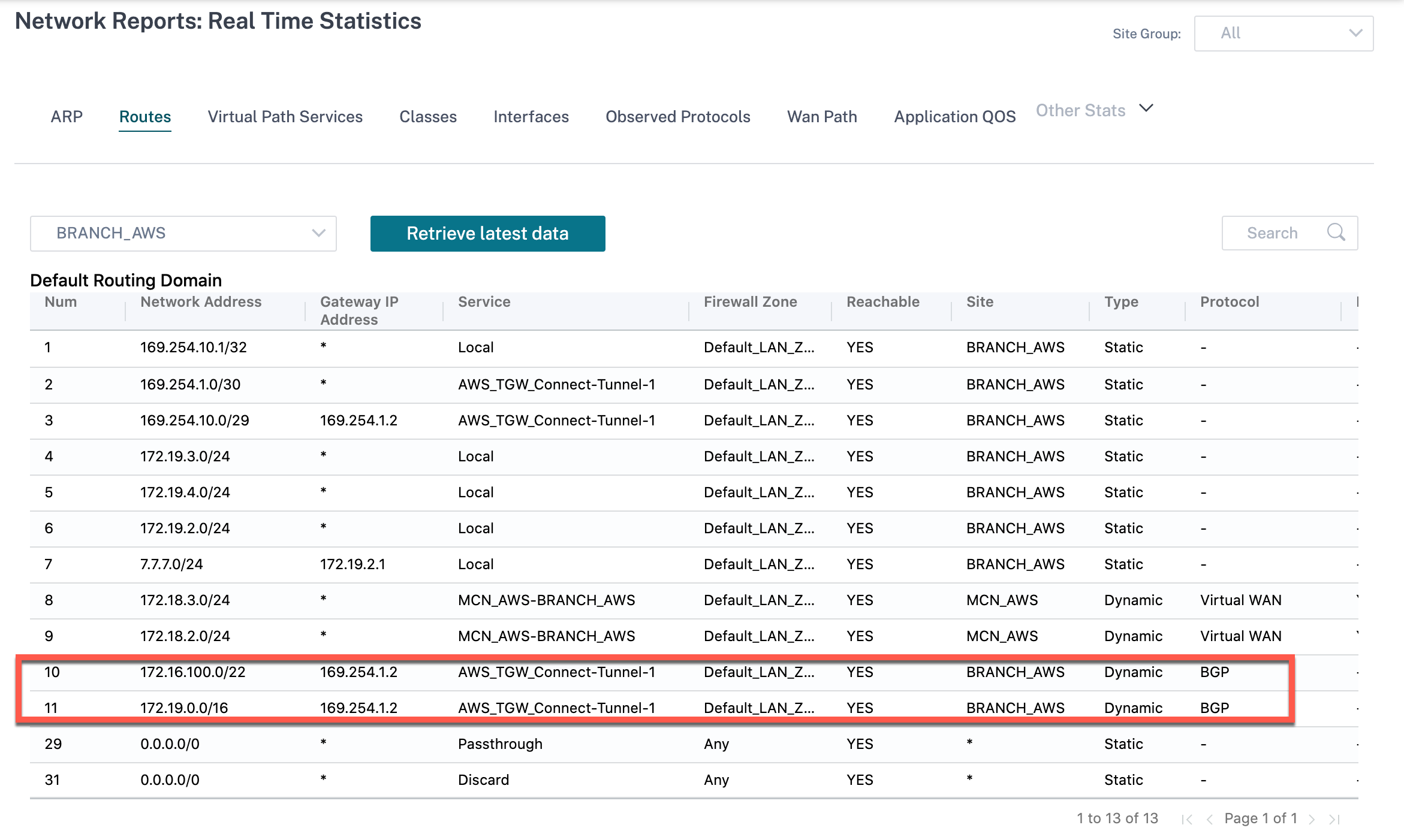
To verify the BGP route installation, navigate to Reports > Real Time > Routes and check if the site has BGP route. It means you can learn the networks attached to AWS Transit Gateway Connect and can communicate to those networks through GRE tunnel.
FAQ
-
What to do when AWS Transit Gateway Connect status shows as Failed after deploying?
The status might transition to Failed in one of the following cases:
- When VPC Attachment creation failed
- Connect Attachment creation failed
- Connect Peer deployment failed
In case of Connect Peer deployment failed, click the Info icon to view detailed information. To proceed further, delete and redeploy the site.
-
What to do when there is a VPC attachment already created?
We recommend you to create Transit Gateway Connect Attachment from AWS console and deploy Connect Peer using the existing Connect Attachment for the site from Citrix SD-WAN Orchestrator service.
-
What to do when the Connect Peer deployment fails at LAN Route creation while deploying AWS Transit Gateway Connect?
As part of the deployment, Citrix SD-WAN Orchestrator service tries to add LAN Route in the routing table of the SD-WAN LAN interface in AWS. The route creation might fail if you have not created a Secondary route table for LAN subnet. To avoid any security issue, do not add LAN route in the main VPC route table.
-
What to do when the Connect Peer deployment fails at Connect Peer creation while deploying AWS Transit Gateway Connect?
On multiple occasions, it is observed that sometimes AWS Transit Gateway Connect Peer remains in Pending state for hours (can be an interim AWS Transit Gateway Connect behavior). Citrix SD-WAN Orchestrator service proceeds with deployment only when each resource has transitioned to Available state in AWS.
-
When you click Delete from the Actions column, the site gets immediately removed from AWS Transit Gateway. But, the resources are still seen on AWS console. Why?
When you click Delete, Citrix SD-WAN Orchestrator service starts a delete job to remove all the resources from AWS. However if you have manually intervened and deleted a few of the resources, the Citrix SD-WAN Orchestrator delete job cleans up the database entries only. You have to manually clean up the rest of the resources.
-
How much time does it take for Citrix SD-WAN Orchestrator service to delete AWS resources?
Once you click Delete from the Actions column, it takes a maximum of 10 minutes to delete AWS resources. Wait for this interval to ensure that all the resources are successfully deleted.
-
What is the preferred way to create multiple Transit Gateway sites present in the same VPC having subnet in the same availability zone?
The preferred method is to create Connect Attachment only once and use the same Connect Attachment for the remaining sites.