Deploy SD-WAN Standard Edition instances in High Availability mode in Azure - Release Version 10.2 and above
The Citrix SD-WAN Azure solution deploys Citrix SD-WAN in Edge Gateway Mode as a single instance, or a cluster pair for High Availability (HA). In an HA deployment, an Azure Load Balancer (ALB) controls the failover between the WAN interfaces of the Citrix SD-WAN appliances.
You can use the Azure load-balancer (ALB) on the LAN side to control failover on the LAN side of the SD-WAN appliances. The Citrix SD-WAN Azure solution in HA creates two separate ALBs (each one on LAN and WAN).
The following diagram illustrates the Citrix SD-WAN Azure HA deployment:
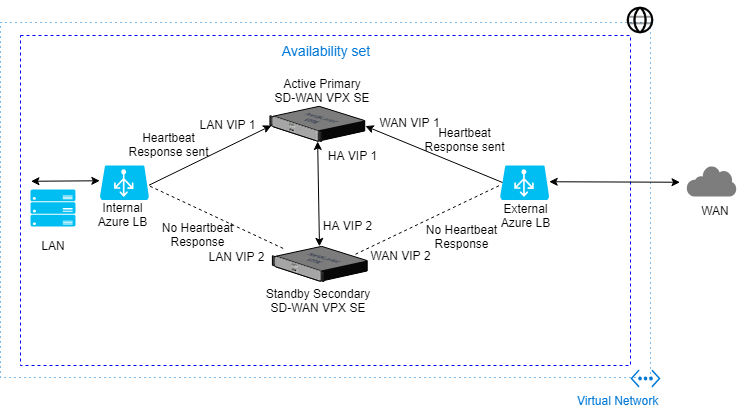
The SD-WAN Standard Edition deployment in Azure is required to be deployed in Edge or Gateway mode deployment where the SD-WAN instance acts as the gateway for the LAN environment. For more information, see Gateway mode.
How to deploy Citrix SD-WAN
To create Citrix SD-WAN Standard Edition (SE) instance:
-
Search for Citrix SD-WAN in the Azure Marketplace and select Citrix SD-WAN Standard Edition 10.2.X.
-
Click Create button to create the Citrix SD-WAN SE 10.2.X Instance.
-
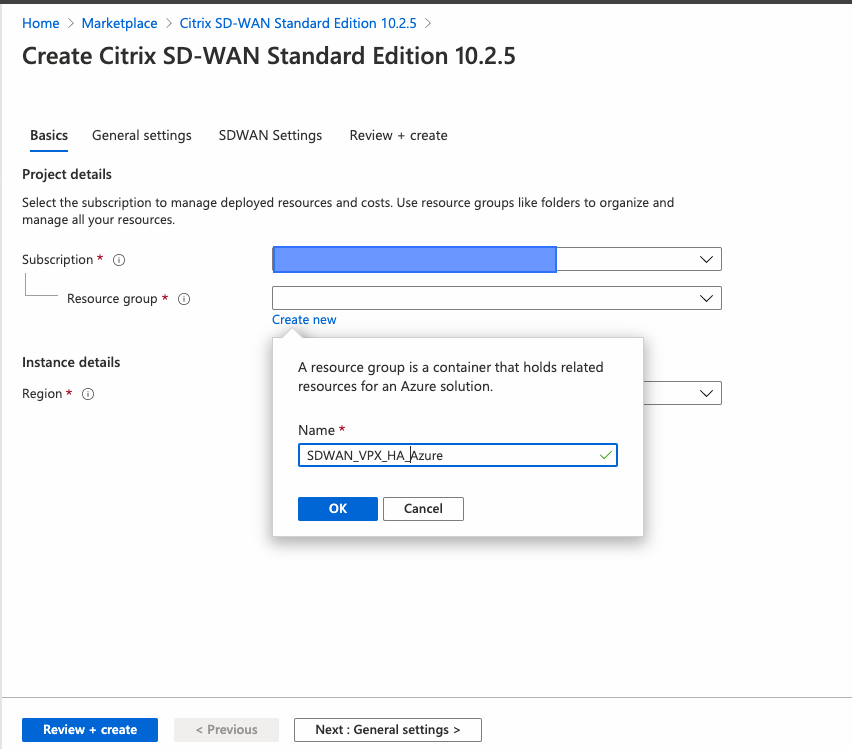
Configure Basic settings page and provide the Resource group name with the appropriate Location.
Note
To create an instance either a new resource group must be created or the resource group must be empty to be reused.
-
Name the Virtual Machine, select Enabled for HA Deployment Mode, and create a Username and Password.
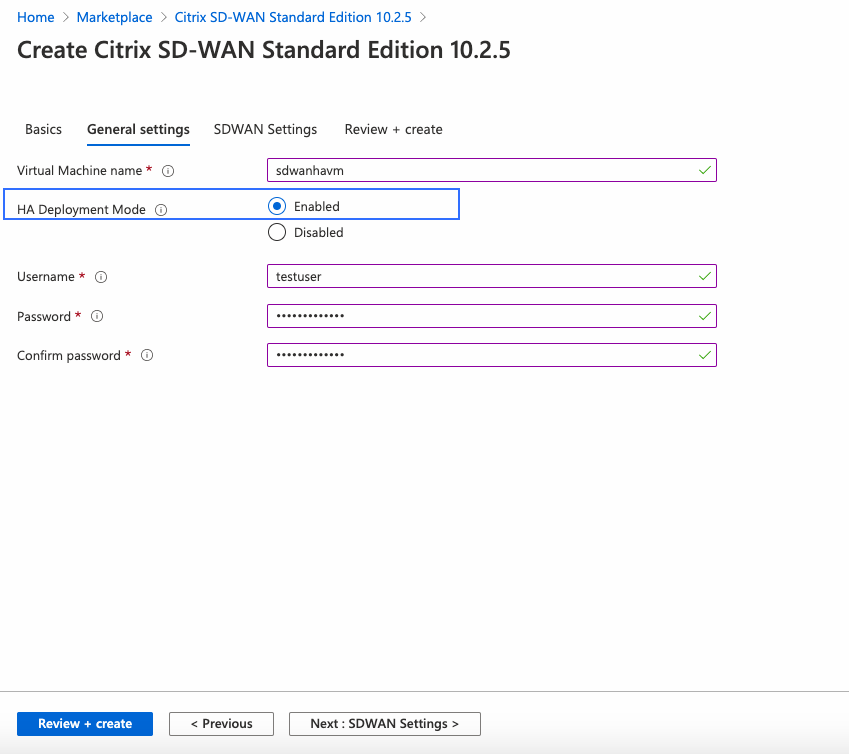
Note
Use admin as a user name for the provisioned instance with the same password that was given during provisioning to get the admin access. In the previously mentioned screenshot, the provisioned user has the guest privilege.
-
Select the Virtual Machine size based on the requirement.
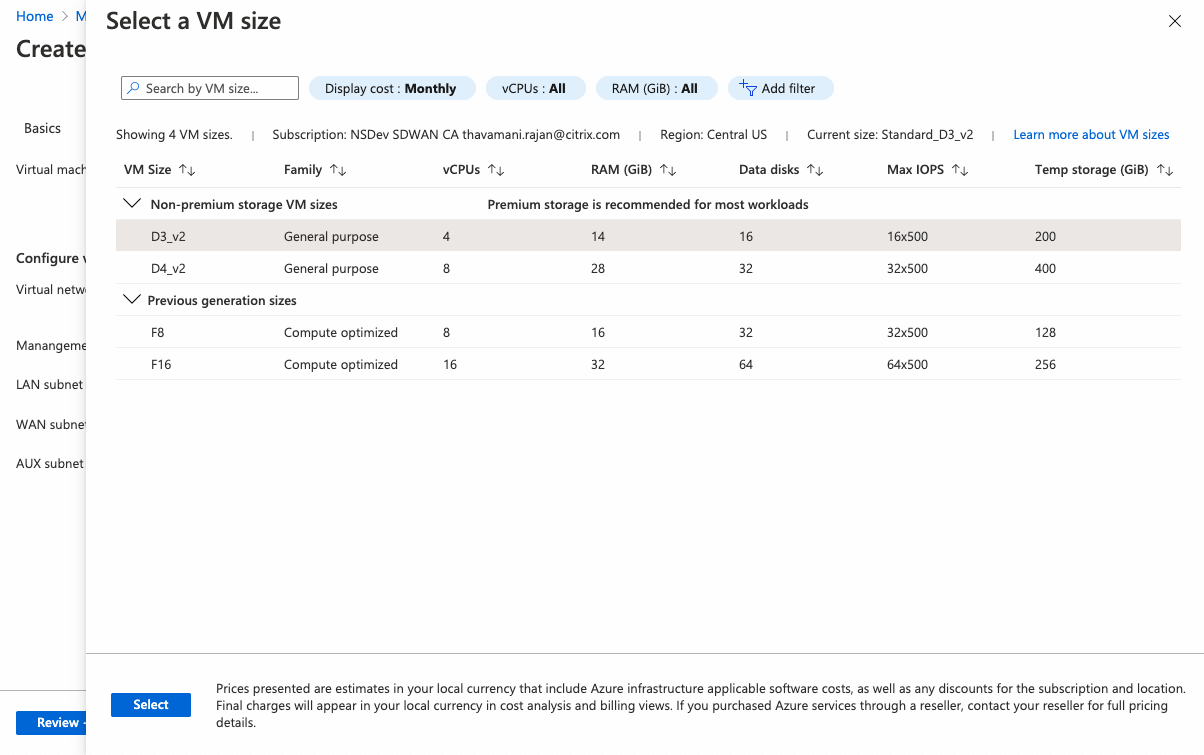
-
From Citrix SD-WAN 11.0.3 release, by default 120 GB of OS Disk Size is allocated. If necessary, you can modify the disk size to a value between 40 GB to 999 GB.
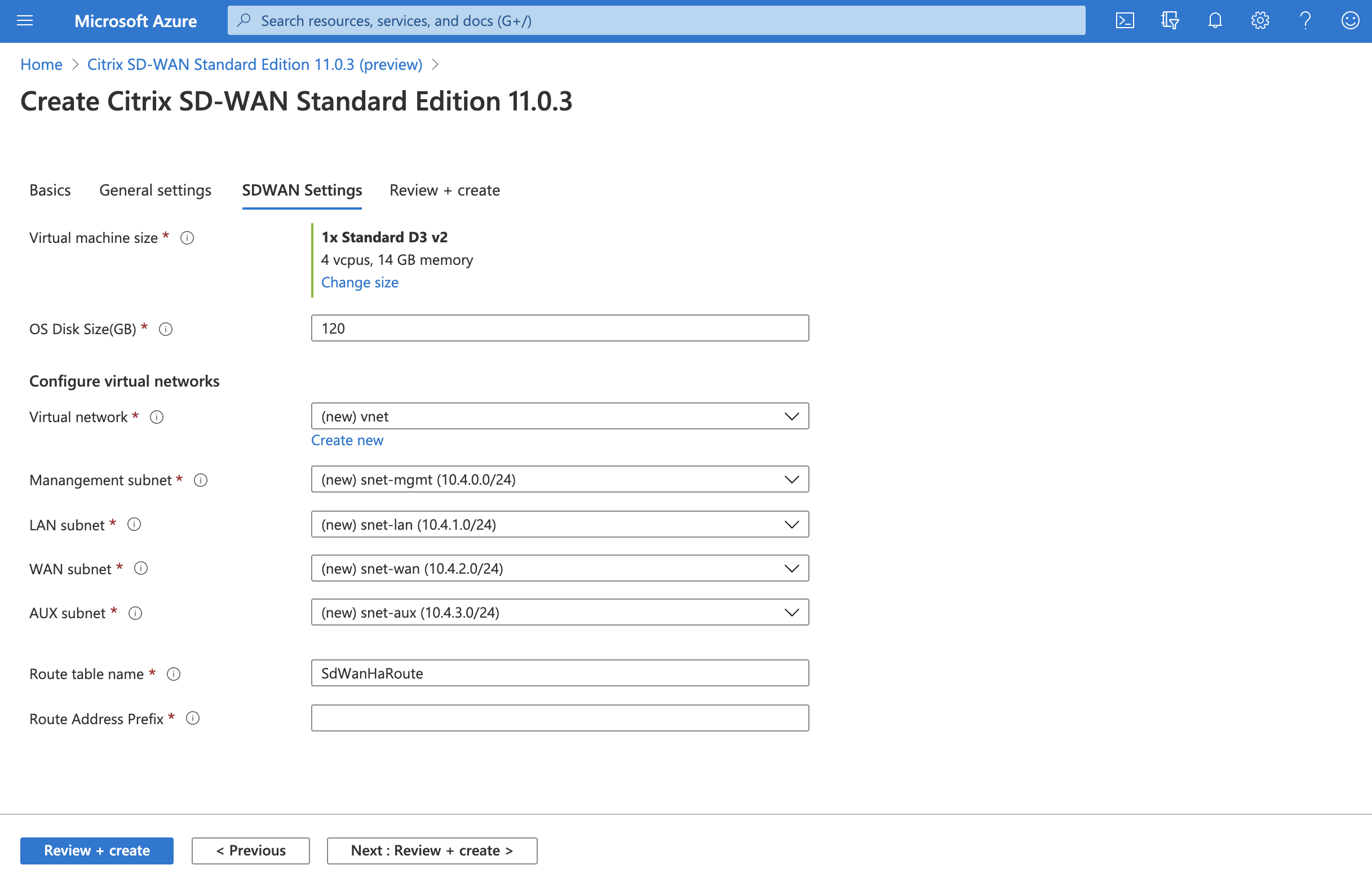
-
Use an existing VNet in the location specified or create a new.
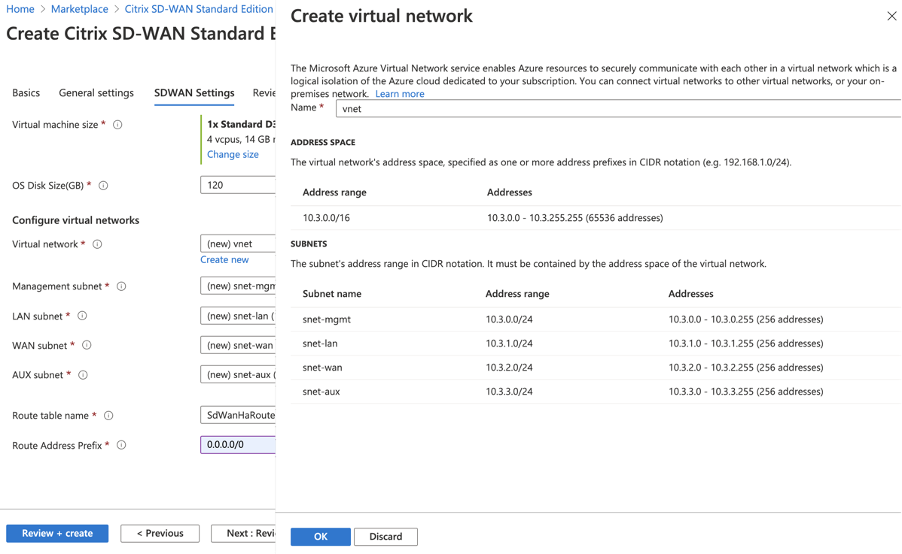
-
Once the Vnet is created, confirm the auto-populated subnets for Management, LAN, WAN, and AUX, then click OK.
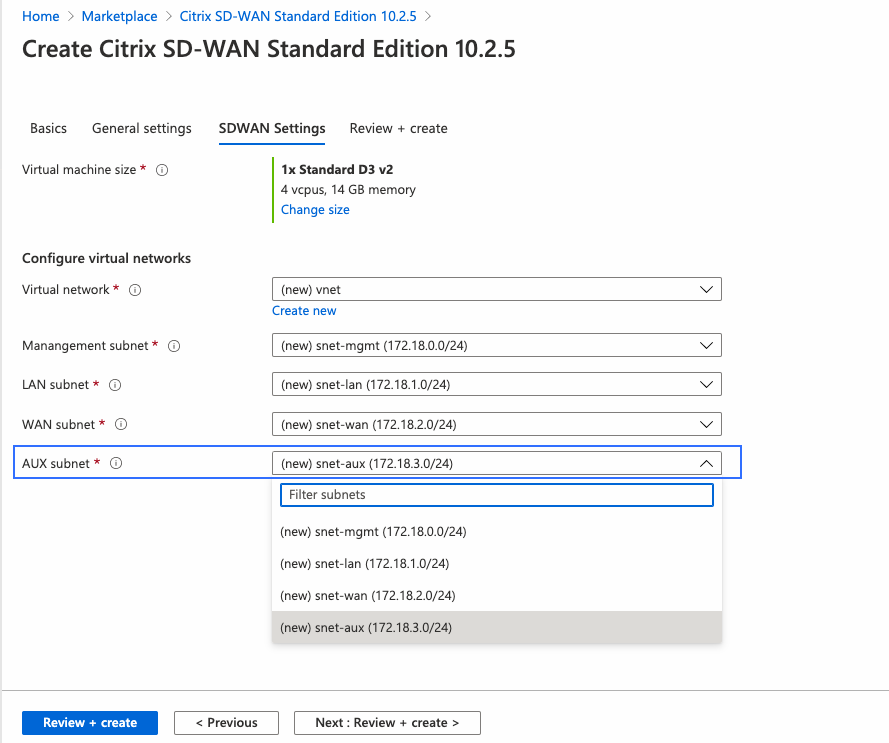
-
Validate the configuration before the Instance creation.
-
Click Create.
How to configure Citrix SD-WAN HA in Azure
-
Determine the IP addresses assigned to the SD-WAN interfaces. Navigate to Virtual Machines > SDWSEA (or as appropriate)> Networking, and examine the IP of each Azure Network Interface.
-
In this deployment, SDWSEA Interface 0 for Management is 10.100.254.4/13.67.93.144.
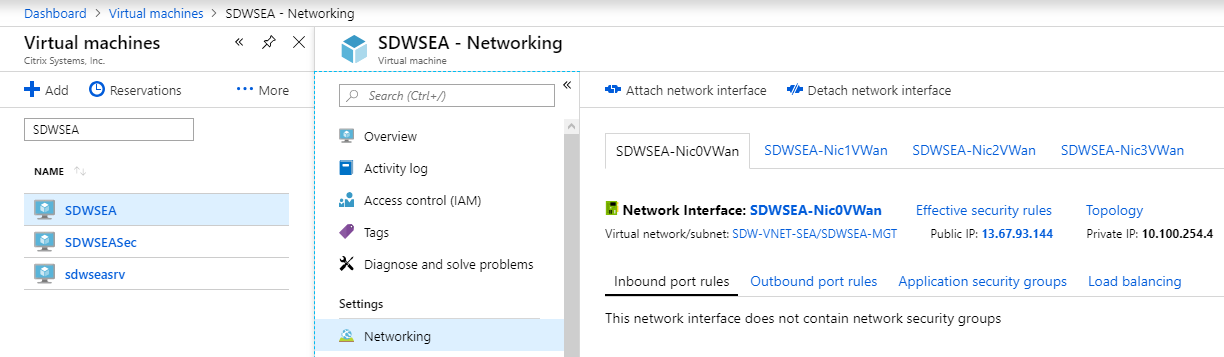
-
The SDWSEA Interface 1 LAN VIP is 10.100.1.4.
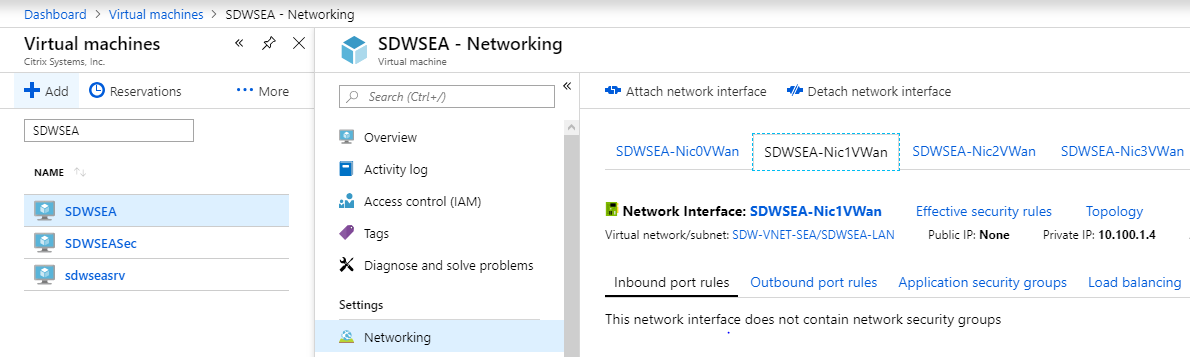
-
The SDWSEA Interface 2 WAN VIP is 10.100.0.4.
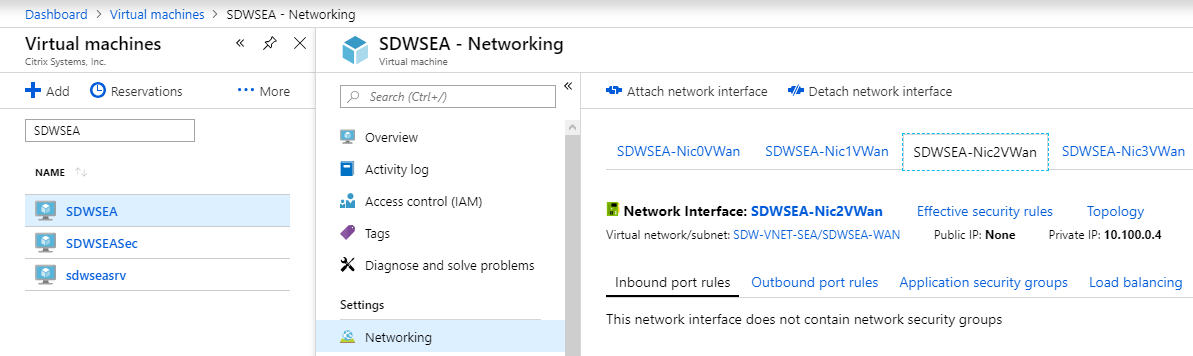
-
The SDWSEA Interface 3 HA Tracking IP (not VIP) is 10.100.253.4:
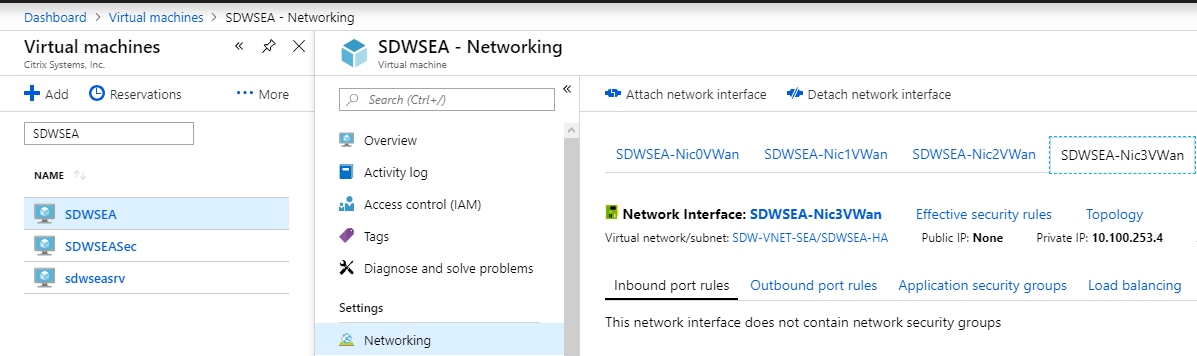
-
Repeat the procedure for the secondary Citrix SD-WAN appliance.
-
-
Determine the SD-WAN ALB Public IP. Navigate to Load Balancers > sdwanha-external. Select the correct ALB based on the Resource Group created during the deployment.
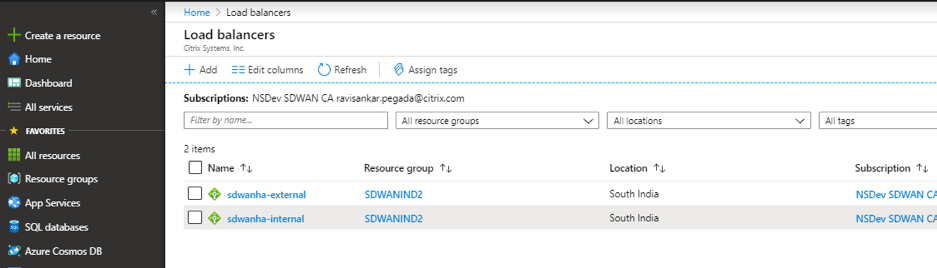
You can see 2 load balancer as following:
- External: External LB contains the public IP that you configure in the WAN link configuration.
- Internal: Internal LB contains private IP. All LAN side traffic comes to the internal LB. So you can configure the route table with Internal LB IP as a next hop.
-
Proceed to the SD-WAN MCN appliance or SD-WAN Center to configure the SD-WAN HA site. In this topic, the SDWSWEA and SDWSEASec appliances are the MCN appliances.
Note
You can configure Citrix SD-WAN HA in Azure through SD-WAN Orchestrator as well.
-
The SDWANSEA and SDWANSEASec Interface Group Configuration is provided as follows. Bypass mode is set to fail-to-block since only one Ethernet/physical interface is used per virtual interface. The WAN Interface must be set to Trusted to accept connections from the ALB.
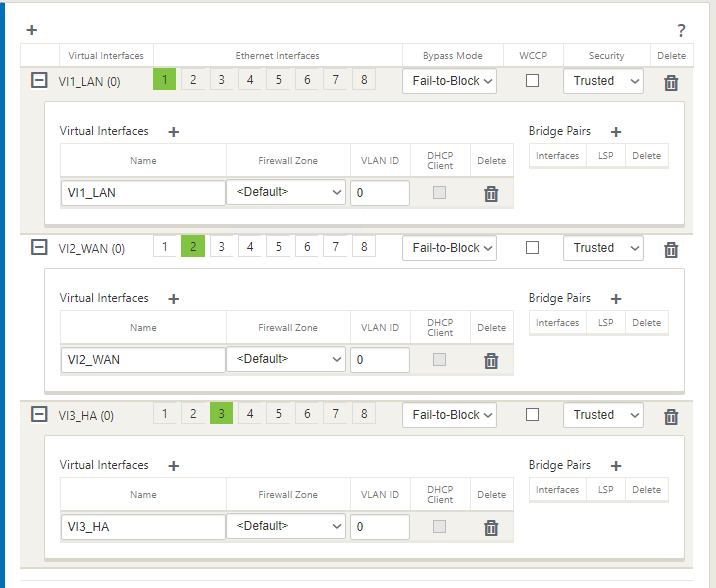
-
The Virtual IP configuration is provided as follows. Note the HA VIP is not the IP addressed assigned to Interface three. Use an available IP address in the appropriate subnet (the subnet assigned to the AUX interface) and not the IP assigned to the Citrix SD-WAN appliances. Note only one VIP in each subnet is the Identity IP.
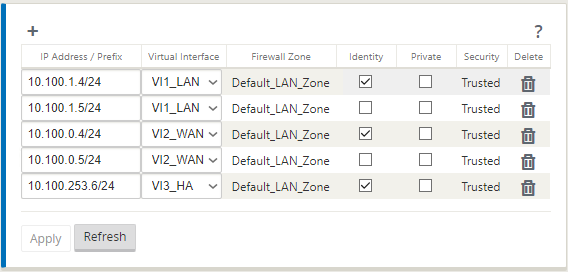
Two virtual IPs are assigned for both LAN and WAN Virtual Interfaces. One IP belongs to Primary SD-WAN Virtual Machine and the other IP belongs to Secondary SD-WAN Virtual Machine both on LAN and WAN respectively. Only the Primary IP is enabled with Identity.
-
The SDWANSEA WAN Link Settings are provided as follows. Note to configure External load balancer Public IP Address as part of WAN link Public IP Address setting. The SD-WAN license determines the bandwidth settings.
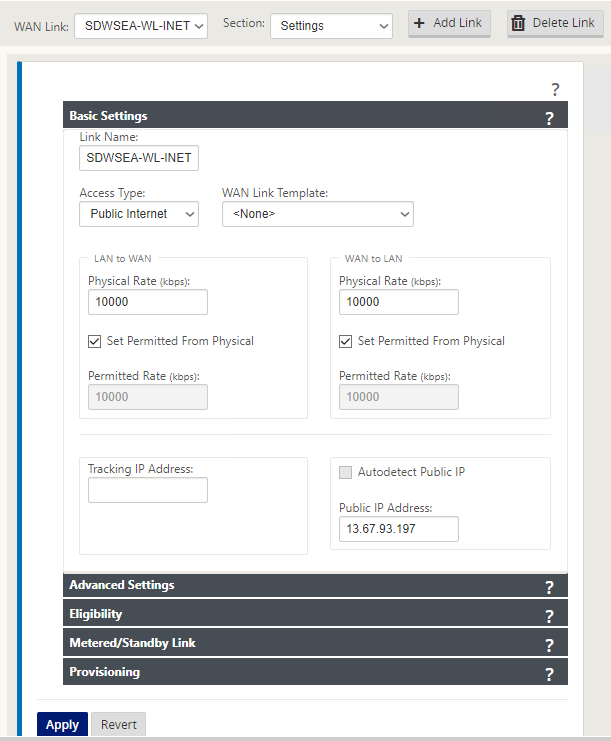
-
The Access Interface settings are as follows. The 10.100.0.1 IP is an Azure reserved IP.
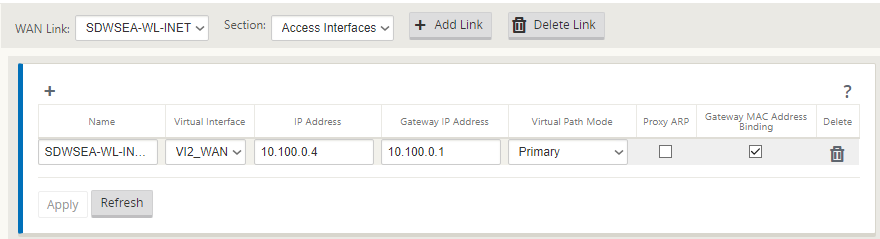
-
HA settings are as follows. The primary and secondary IP address as part of this HA setting must be configured with the AUX Interface IP address of both Primary and Secondary Virtual Machines respectively.
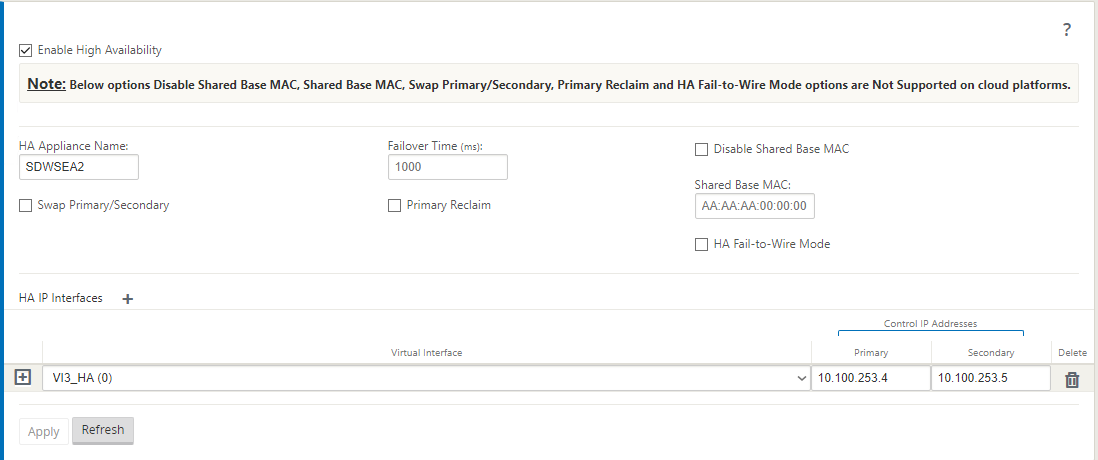
-
Click Apply.
-
To have LAN traffic go through SD-WAN, add a route table on Azure with a route whose next hop points to Azure Internal Load-balancer IP. And associate the LAN subnet to the route table created.
If at all you must route all the traffic through SD-WAN, create a default route whose next-hop is pointing to Internal Load balancer IP.
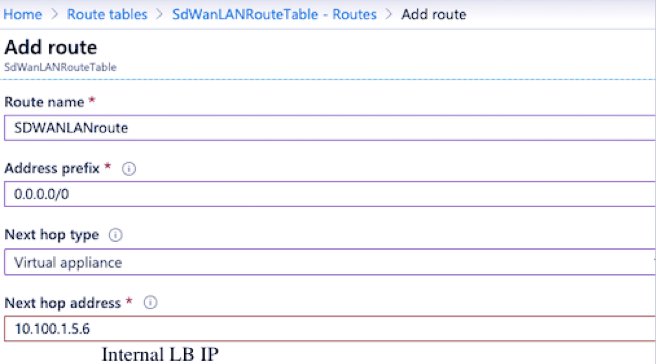
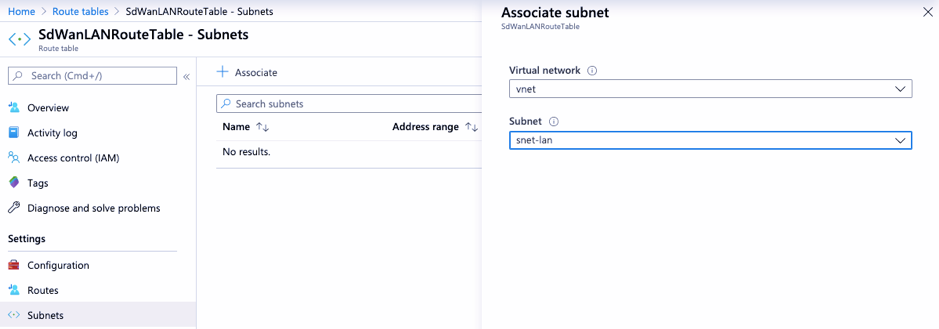
Internet breakout for Azure MCN (HA mode)
To configure Internet breakout on Azure MCNs deployed in HA mode:
- In the MCN appliance configure DHCP IP on the WAN interface with Public IP configured for the WAN link.
- Configure Internet service on the MCN.
- Add an Outbound Dynamic port restricted NAT with the inside service as Internet.
- Add a firewall policy on the MCN to allow Azure load balancer health probes on port number 500.
-
Add another load balancing rule on the Azure external load balancer for TCP on port number 80, with direct server return disabled.
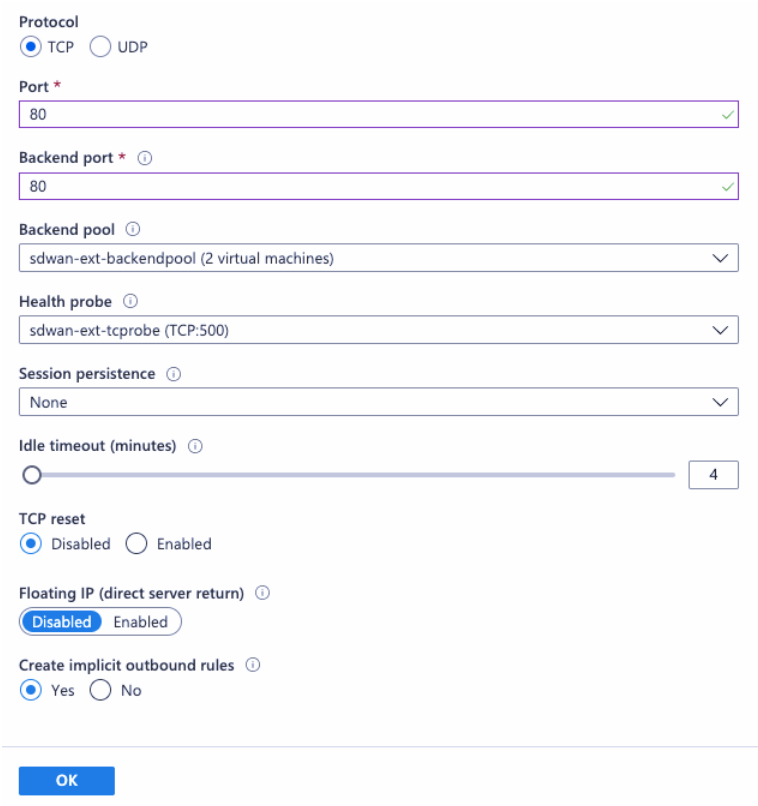
- On the end client machine that must breakout to the internet, set the route next hop IP address to the Internal Load Balancer private IP address. The load balancer IP is configured as LAN VIP in the MCN.
Note
- Azure MCNs do not support DHCP IP configuration on HA appliances running a software version prior to SD-WAN 11.2.1.
- Standalone Azure MCNs support static IP configurations.