Configure Citrix SD-WAN WANOP appliance to optimize secure Windows traffic
You must add the Citrix SD-WAN WANOP appliance to the Windows security infrastructure before you can optimize the signed Windows file system and encrypted MAPI Outlook/Exchange traffic.
As a result of enhancements to the Windows security system in the recent Windows releases, clients and servers secure the traffic by authenticating and encrypting data. This requires the Citrix SD-WAN WANOP appliance be a trusted member of the Windows security infrastructure before it can optimize signed Windows file system and encrypted MAPI Outlook/Exchange traffic.
After you add the appliance to the Windows security infrastructure, the appliance has the following capabilities:
-
Acceleration of fileserver traffic for Microsoft Windows servers, NetApp servers, and Hitachi HNAS by using signed SMB and signed SMB2 protocol.
-
Acceleration of Microsoft Exchange server traffic when it is accessed by Outlook clients using encrypted MAPI or RPC over HTTPS.
How Citrix SD-WAN WANOP appliance works in a Windows security system
Joining the appliance to a Windows domain requires administrator credentials. When it joins the Windows domain, the appliance becomes a trusted member of the domain. This allows the appliance to be declared a member of the domain’s security infrastructure.
After the appliance has become a part of the Windows security infrastructure, users have to be authenticated before they can access resources. To avoid the difficulty of configuring a large number of users in the domain, you can delegate the authentication responsibility to a delegate user.
You create a delegate user in the active directory. This user is similar to a normal user, but with special privileges. After creating the delegate user, you must configure this user on the Citrix SD-WAN WANOP appliance. The appliance uses the delegate user to authenticate on behalf of users when they access authenticated and encrypted data streams using Windows protocols, such as CIFS and MAPI.
For accelerating CIFS and MAPI traffic, the standard Windows delegation mechanism allows you to limit security delegation to the relevant services. This constrained delegation has been available since the release of Windows Server 2003.
After becoming a part of the domain, the appliance accelerates the secure Windows traffic. A datacenter appliance that joins a Windows domain must have a secure peer relationship with the remote appliance or Citrix SD-WAN WANOP Plug-in, but only the datacenter appliance joins the Windows domain. For purposes of CIFS or MAPI acceleration, the remote appliance acts as a slave to the datacenter appliance, being controlled over the secure SSL tunnel between the two. Therefore, the delegate user credentials do not leave the datacenter.
The following figure shows a sample topology diagram for this setup.
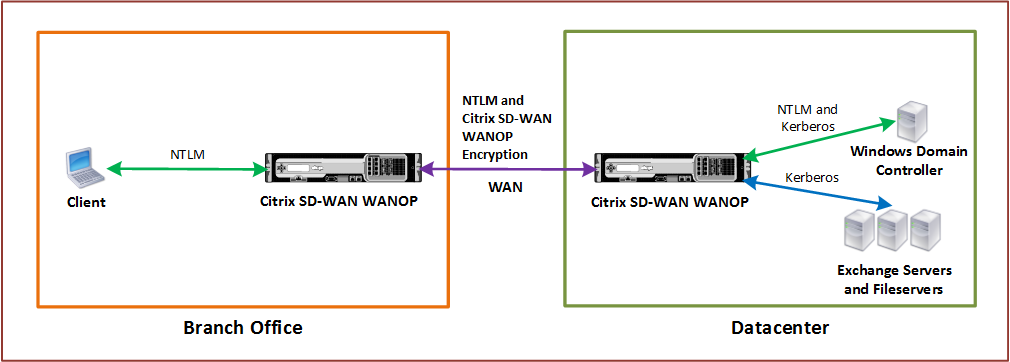
In the above figure, a branch office client accesses resources of the datacenter. The branch office client, being in another domain, uses NTLM authentication as a part of the Windows security system. As with all accelerated connections between two Citrix SD-WAN WANOP appliances in a secure peer relationship, the CIFS or MAPI connections and NTLM authentications over the WAN are encrypted. Depending on the Windows domain controller version, the user request from the datacenter Citrix SD-WAN WANOP appliance is authenticated using NTLM or Kerberos authentication protocol. After the domain authenticates the user, subsequent access requests to the Exchange server and file servers use Kerberos authentication protocol. The Citrix SD-WAN WANOP appliance then optimizes the connections established between the client and the server.
If the appliances do not have a secure peer relationship, or if the datacenter appliance has not successfully joined the domain, the connections use TCP flow-control acceleration, which performs no security operations, compression, or data transformations. The connections between the client and server are established as if the Citrix SD-WAN WANOP appliances were not there.
You can configure different client authentication modes on Windows operating systems. The types of connections that the Citrix SD-WAN WANOP appliance optimizes depend on the client authentication mode that you configure.
The following table list the Windows client-authentication modes on Windows, and the corresponding Citrix SD-WAN WANOP optimizations.
Authentication and Optimization Supported for Windows Operating System
| Client Operating System | Client Authentication Mode | Optimization | Comments |
|---|---|---|---|
| Windows XP/Windows Vista/Windows7/Windows 8 | Negotiate Authentication (SPNEGO) | TCP flow-control acceleration, Compression, CIFS protocol acceleration | Default setting used for all Windows releases. |
| Windows XP/Windows Vista/Windows 7/Windows 8 | NTLM only or Kerberos only | TCP flow-control acceleration only | Non-default authentication modes |
Note: If you use the NTLM only or Kerberos only client authentication modes, the traffic is not accelerated if it is encrypted.
Requirements to add a Citrix SD-WAN WANOP appliance to the Windows security system
To optimize traffic for secured Windows signed SMB and encrypted MAPI traffic, your Citrix SD-WAN WANOP deployment must meet the following requirements before you add the appliance to the Windows security infrastructure:
-
Both the client-side and server-side acceleration appliances must have established a secure peer relationship.
-
The appliances must use an NTP server that is closely synchronized to the time on the Windows domain server. Ideally, the appliances and the Windows domain server are all clients of the same NTP server.
-
Outlook must not be configured for the (non-default) Kerberos only or NTLM only option. The default (negotiated) option is required for acceleration.
-
The client and server can be members of any domain that has two-way trust with the server-side appliance’s domain. One-way trust is not supported.
-
A Kerberos delegate user must be set up on the domain controller, to be used by the appliance participating in the domain’s security infrastructure.
-
The DNS server IP addresses for the domain must be configured and reachable on the server-side appliance.
-
The domain servers must be fully reachable, with both forward and reverse lookups for all the IP addresses of the domain controllers configured on the DNS servers.
-
The server-side Citrix SD-WAN WANOP appliance’s host name must be unique. Using the default host name of “hostname” is likely to cause problems.
Note
The Macintosh Outlook client does not use the MAPI (Outlook/Exchange) standard and is not accelerated by this feature.
Add a Citrix SD-WAN WANOP appliance to the Windows security infrastructure
To optimize secure Windows traffic, the Citrix SD-WAN WANOP appliance must be a part of the Windows security system and must authenticate itself with the security system or domain. As shown in the below figure, to make the appliance a part of the Windows security system, you must make the appliance join a domain (using administrative credentials). Additionally, you need to configure a new or existing user as a delegate user by associating CIFS and Exchange services with that user. You then have to configure this delegate user on the Citrix SD-WAN WANOP appliance.
You can use the Pre Domain Check utility to find out if there are any issues with joining the appliance to a domain.
Note
The Windows security system uses the Exchange service to manage MAPI connections. Configuring the setup to optimize secure Windows traffic
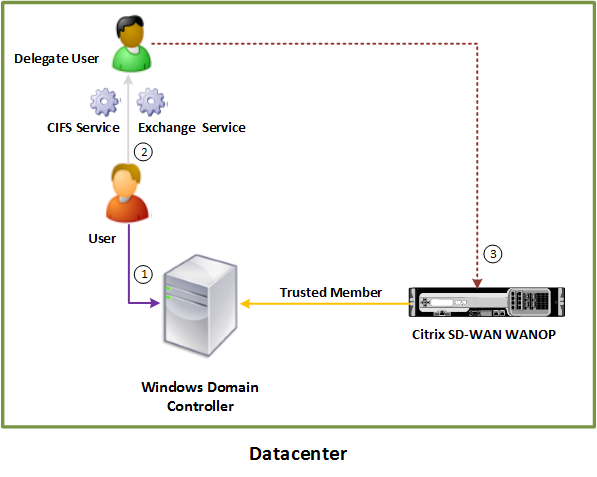
Join a Citrix SD-WAN WANOP appliance to the Windows domain:
When the appliance joins the domain, it exchanges a shared secret with the domain controller, allowing the appliance to remain part of the domain indefinitely. When joining an appliance to a domain, make sure that you have administrator credentials for the domain controller.
To make sure that the Citrix SD-WAN WANOP appliance optimizes the CIFS and MAPI traffic (including traffic encapsulated as RPC over HTTPS), you must make the appliance part of the domain that the Windows fileserver and Exchange server are a part of. You need to join the server-side appliance to the domain.
Note: The domain administration credentials are not saved on the appliance.
To join a Citrix SD-WAN WANOP appliance to a Windows domain:
-
Navigate to the Configuration > Secure Acceleration > Windows Domain tab.
-
Click Join Windows Domain.
-
Enter the Windows domain name in the Domain Name field.
-
In the User Name field, enter the user name of the domain controller administrator.
-
In the Password field, specify the domain controller administrator password.
-
If necessary, edit the DNS servers for consistency with the Windows domain.
-
Click OK.
-
In the Delegate Users section, add a delegate user, as described in the procedures below.

Configure a delegate user:
After you join the appliance to a Windows domain, you must create a user that the appliance can use to authenticate users with the domain. This user is known as the delegate user.
Note: To create a delegate user account, you need administrator access to the Windows domain controller and the appliance. If you do not have administrator access to the Windows domain controller, make sure that an authorized administrator performs the required tasks on the domain controller.
Setting up user authentication by using Kerberos delegation involves two tasks——configuring a delegate user on the domain controller and then adding this user to the Citrix SD-WAN WANOP appliance.
Configure a delegate user on a domain controller:
Before you configure a delegate user on a Citrix SD-WAN WANOP appliance, you must configure a delegate user with the required properties on the domain controller. You can either create a delegate user account or use an existing user account as a delegate user account.
After creating an account or selecting an existing account, enable delegation for this user. You then associate the delegate user with the CIFS and Exchange services, so that the traffic for these services can be accelerated. After you add this user to the Citrix SD-WAN WANOP appliance, the appliance presents delegated credentials for the services associated with this account.
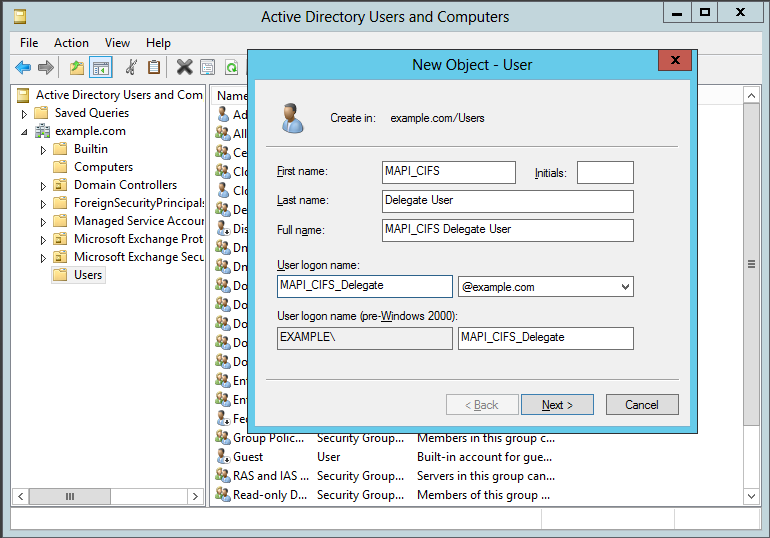
Create a delegate user account:
Create a delegate user account on the Windows domain controller so that the Citrix SD-WAN WANOP appliance can use this account on behalf of the users to authenticate them with the domain controller.
Note: If you want to configure an existing user as a delegate user, skip this procedure.
To create a delegate user account:
-
Log on to the Windows domain controller as an administrator. Make sure that the file server or Exchange server is a member of this domain.
-
From the Start menu, open the Active Directory Users and Computers Window.
-
Create a delegate user, as shown in the following screen shot:
Enable delegation for a user:
So far, the user you have created is similar to any user you create on the Active Directory server. To enable delegation for the user, you must set the Service Principal Name attribute of the user to delegate and associate the delegate user with the required services. This makes the user to have special privileges attached to it and make it a delegate user.
To enable delegation for the user:
-
From the Start menu, open the Active Directory Users and Computers Window.
-
From the View menu, select Advanced Features.
-
Select the User node.
-
Right-click the user that you want to make a delegate user.
-
From the shortcut menu, select Properties and navigate to the Attribute Editor tab, as shown in the following screen shot:
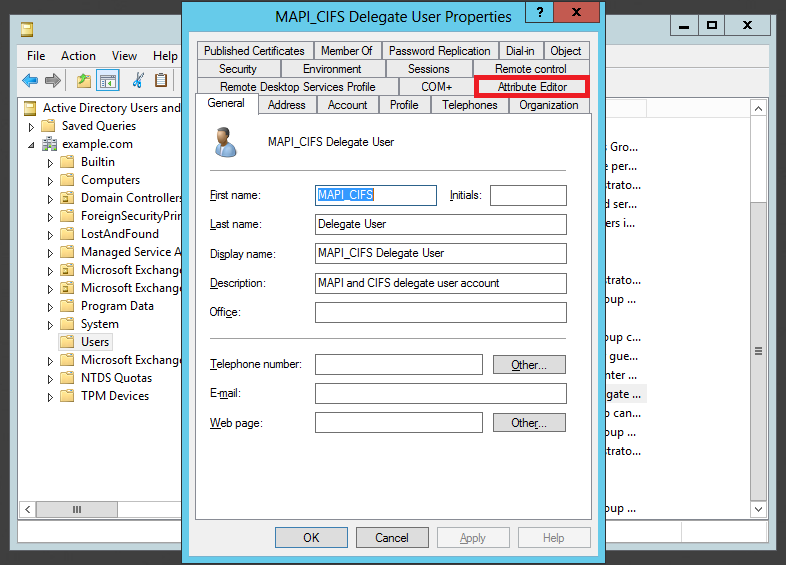
-
From the Attributes list, select servicePrincipalName, as shown in the following screen shot:
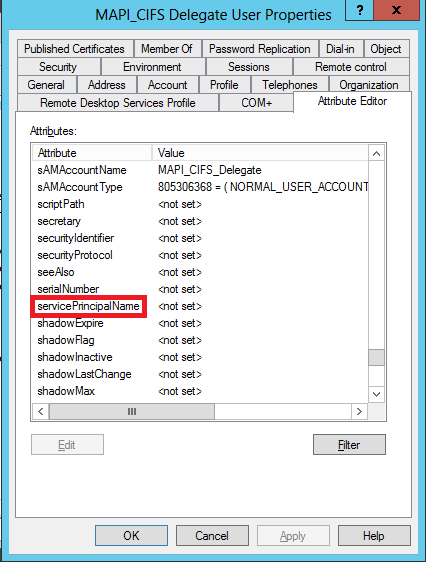
-
Click Edit.
-
In the Multi-valued String Editor dialog box, in the Value to add field, specify delegate/<User_Name>, as shown in the following screen shot:
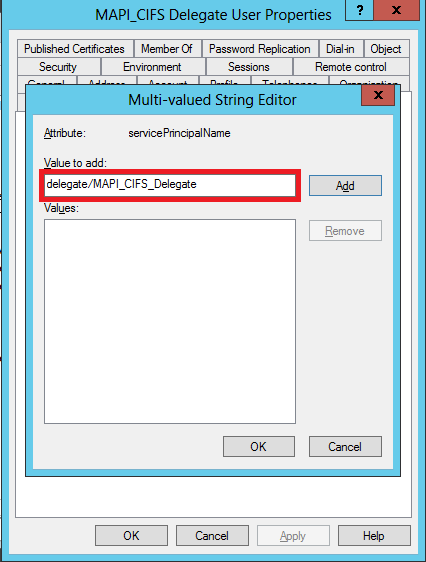
-
Click Add.
-
Click OK.
-
Click Apply.
-
Click OK.
-
Open the user’s MAPI-CIFS Delegate User Properties dialog box and verify that the Delegation tab has been added to the dialog box, as shown in the following screen shot:
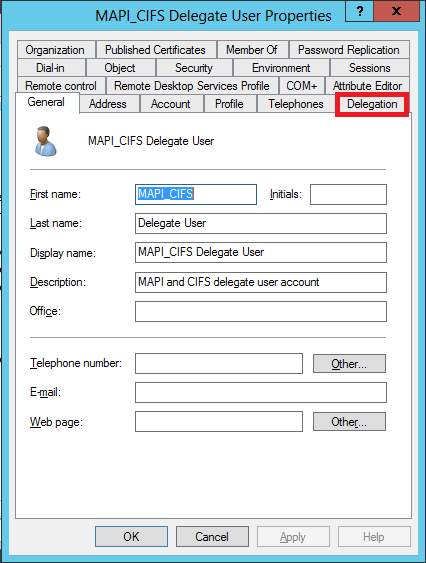
Associate the delegate user with CIFS and Exchange Services:
After enabling the Delegation tab for the user, you can associate the user with services for which the user can present delegated credentials. When you add this user to the Citrix SD-WAN WANOP appliance, the appliance presents delegated credentials for the services associated with this account. Note: Windows security infrastructure uses the Exchange service to manage MAPI traffic.
To associate the delegate user with CIFS and Exchange services:
-
In the Delegation tab, select the Trust this user for delegation to specific services only option.
-
Select the Use any authentication protocol option.
-
Click Add, as shown in the following screen shot:
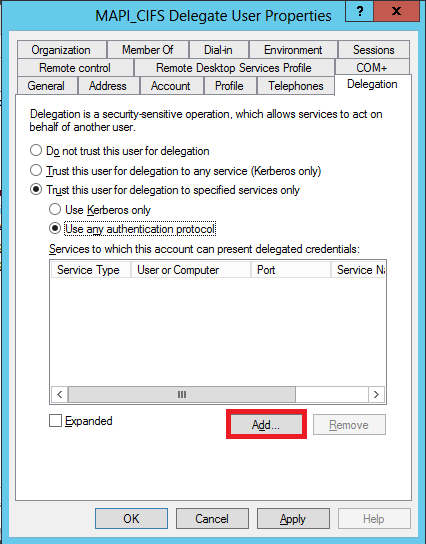
-
In the Add Service dialog box, click Users and Computers.
-
In the Select Users or Computers dialog box, add the local computer to be selected, as shown in the following screen shot:
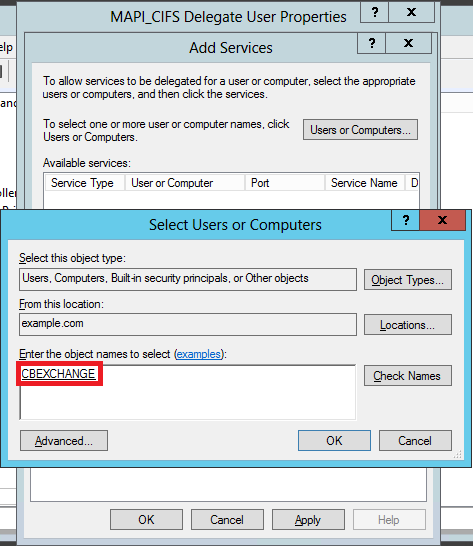
-
Click OK.
-
In the Add Services dialog box, from the Available services list, select cifs, as shown in the following screen shot:
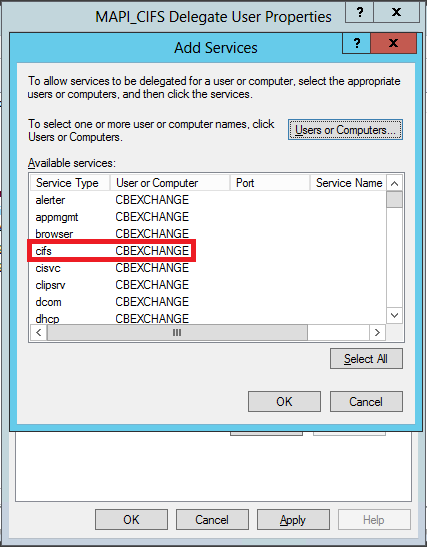
-
If you have to set up MAPI acceleration on the Citrix SD-WAN WANOP appliance, press and hold the Ctrl key, and select the exchangeMDB service.
-
Click OK. The services you have selected are added to the Services to which this account can present delegated credentials list, as shown in the following screen shot:
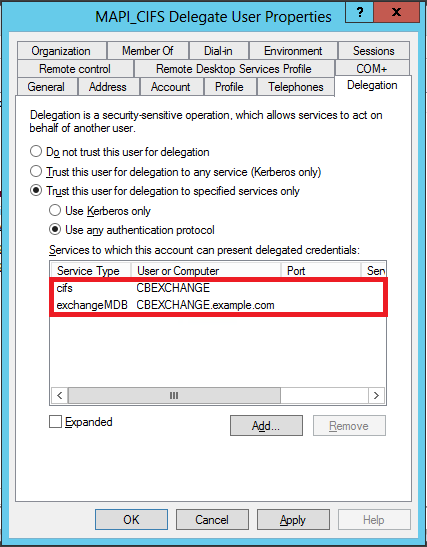
-
Click OK.
-
Close the Active Directory Users and Computers Window.
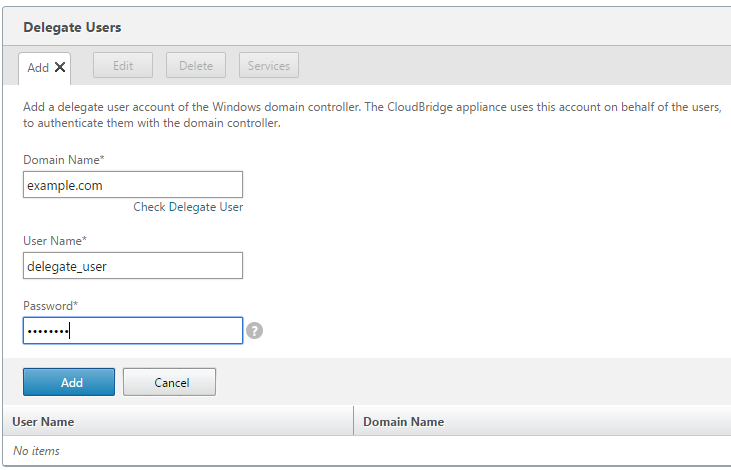
Configure a delegate user on a Citrix SD-WAN WANOP appliance:
After configuring the delegate user on the Active Directory server, you must configure this user on the Citrix SD-WAN WANOP appliance, so that the appliance can present this user’s delegated credentials to the domain. This enables the appliance to actively optimize the network traffic for the advanced CIFS and MAPI acceleration features.
To add the delegate user to the server-side appliance:
-
Navigate to the Configuration > Secure Acceleration > Windows Domain tab.
-
Click the Join Windows Domain button, if present.
-
Under Delegate Users, click Add.
-
In the Domain Name field, specify the domain name. This is typically the domain that you specified under the Windows Domain section.
-
In the User Name field, enter the user name of the delegate user.
-
In the Password field, specify the password of the delegate user.
-
Click Add.
Verify that the appliance has joined the domain
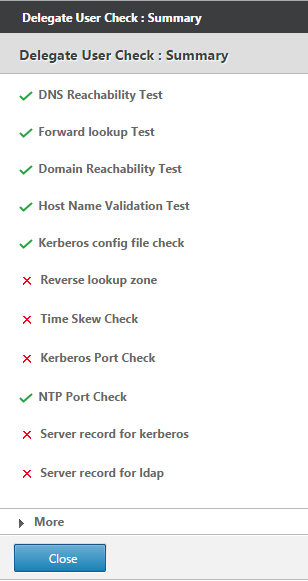
If, after adding the appliance to the domain, you notice that the appliance is not optimizing secure Windows traffic, some error might have prevented the appliance from joining the domain. You can use the Pre Domain Check utility to find out if there are any issues with the appliance joining the domain. You can even run this utility to identify possible issues before you attempt to join the appliance to a domain.
To check the delegate user:
-
Log on to the server-side Citrix SD-WAN WANOP appliance.
-
Navigate to Configuration > Secure Acceleration > Windows tab.
-
Click the Join Windows Domain button, if present.
-
Select a delegate user and click Edit.
-
Click Check Delegate User.
-
Wait for the Delegate User Domain Check to complete and examine the results.