Deployment modes
In a typical Citrix SD-WAN WANOP deployment, the Citrix SD-WAN WANOP appliances are paired across branch offices and datacenter. You install shared resources, such as VDA, in the datacenter. Clients from various branch offices access datacenter resources by using Citrix Receiver, as shown in the following figure.
A typical Citrix SD-WAN WANOP deployment topology
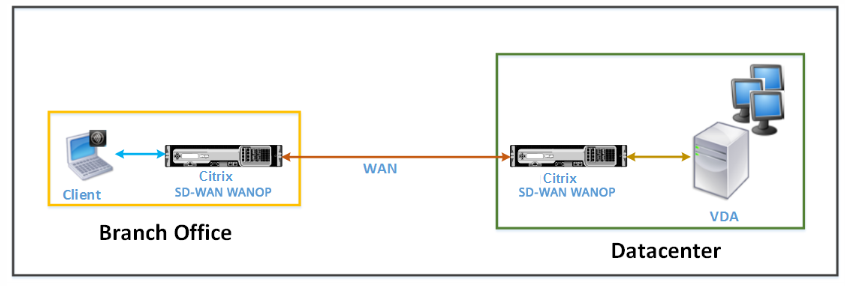
Clients install a Citrix Receiver software product, such as Citrix Receiver for HTML5, on their local computers and use it to access resources in the datacenter. Connections through the pair of Citrix SD-WAN WANOP appliances are optimized.
Understand messages exchanged between the client and the server
As with any type of network connection, a client using Citrix Receiver for HTML5 exchanges various messages with the server. The following figure shows a typical flow of messages between the client and server when a connection is established between them.
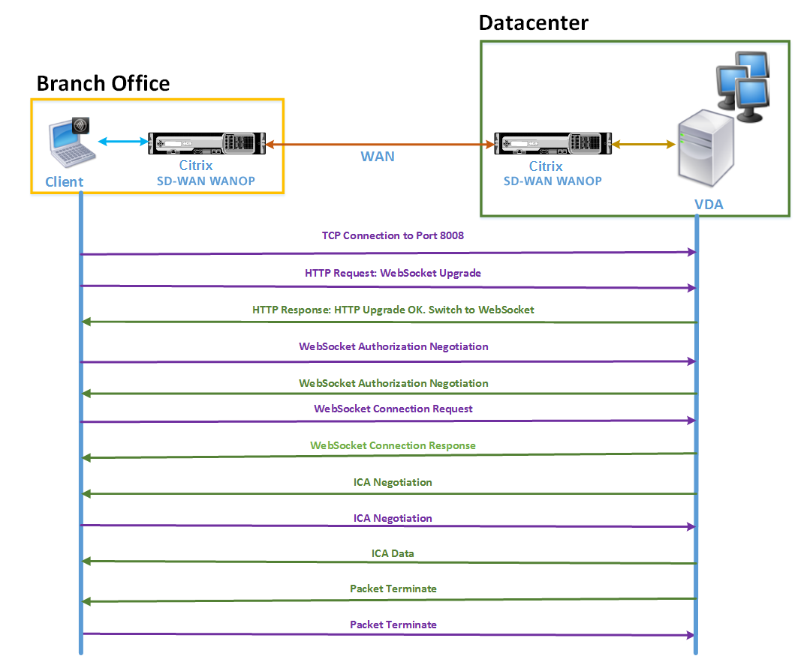
As shown in the above figure, the following sequence of messages is exchanged between the client and server when a client from a branch office wants to access datacenter server resources:
-
Client uses Citrix Receiver for HTML5 to send a TCP connection request to VDA on port 8008.
-
After establishing the TCP connection, the client sends a WebSocket upgrade request to VDA.
-
VDA responds to the upgrade request and switches to the WebSocket protocol.
-
Client and VDA negotiate WebSocket authorization.
-
Client sends a WebSocket connection request to VDA.
-
VDA responds to the WebSocket connection request.
-
VDA initiates ICA negotiation with the client.
-
After ICA negotiation, VDA starts transmitting ICA data.
-
VDA sends packet termination message.
-
Client responds with the packet termination message.
Note
The above example lists the sample messages exchanged for ICA over WebSocket. If you are using ICA over Common Gateway Protocol (CGP), the client and server negotiate CGP instead of WebSocket. However, for ICA over TCP, the client and server negotiate ICA.
Depending on the components you have deployed on the network, the connection is terminated at different points. The preceding figure represents a topology that does not have any additional components deployed on the network. As a result, the client communicates directly with VDA at port 8008. However, if you have installed a gateway, such as Citrix Gateway, at the datacenter, the connection is established with the gateway and it proxies VDA. Until the gateway negotiates the WebSocket authorization, there is no communication with VDA. After the gateway has negotiated WebSocket authorization, it opens a connection with VDA. Thereafter, the gateway acts as a middleman and passes messages from the client to VDA and vice versa.
Similarly, if a VPN tunnel is created between a Citrix gateway plugin installed on the client and Citrix Gateway installed at the datacenter, the gateway transparently forwards all client messages, immediately upon establishing a TCP connection, to VDA, and vice versa.
Note
To optimize a connection that requires end-to-end SSL encryption, a TCP connection is established at port 443 on VDA.
Supported deployment modes
When configuring a Citrix SD-WAN WANOP appliance for optimizing Citrix Receiver for HTML5, you can consider any of the following deployment modes, depending on your network requirements. To optimize Citrix Receiver for HTML5 connections, Citrix SD-WAN WANOP appliances support the following deployment modes:
-
Direct Access
-
Direct Access with End-to-End SSL Encryption
-
ICA Proxy Mode
-
ICA Proxy Mode with End-to-End SSL Encryption
-
Full Virtual Private Network (VPN) Mode
-
Full Virtual Private Network (VPN) Mode with End-to-End SSL Encryption
Direct access:
The following figure shows the deployment topology of Citrix Receiver for HTML5 installed on the client in the direct access mode.
Citrix SD-WAN WANOP appliances deployed in direct access mode
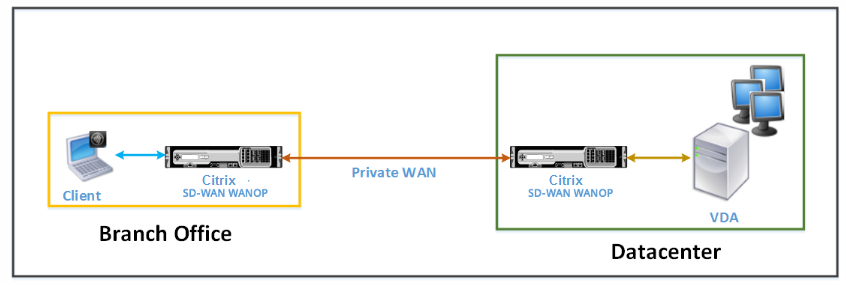
In the direct access mode, a pair of Citrix SD-WAN WANOP appliances is installed across a branch office and the datacenter in inline mode. A client accesses VDA resources through Citrix Receiver for HTML5 over the private WAN. Connections from the client to the VDA resources is secured by using encryption at the ICA level. Messages exchanged between the client and VDA are explained in Understanding Messages Exchanged Between the Client and the Server.
The Citrix SD-WAN WANOP appliances installed between the client and VDA datacenter optimize the Citrix Receiver for HTML5 connections established between them.
A direct access deployment is suitable for a corporate intranet on which clients connect without using Citrix Gateway or any other firewall. You deploy a set up with direct access when Citrix SD-WAN WANOP appliances are deployed in the inline mode and a client from a private WAN connects to the VDA resources.
Direct access with end-to-end SSL encryption:
The following figure shows the deployment topology of Citrix Receiver for HTML5 installed on the client in the direct access mode secured with end-to-end SSL encryption.
Citrix SD-WAN WANOP appliances deployed in direct access mode secured with end-to-end SSL encryption
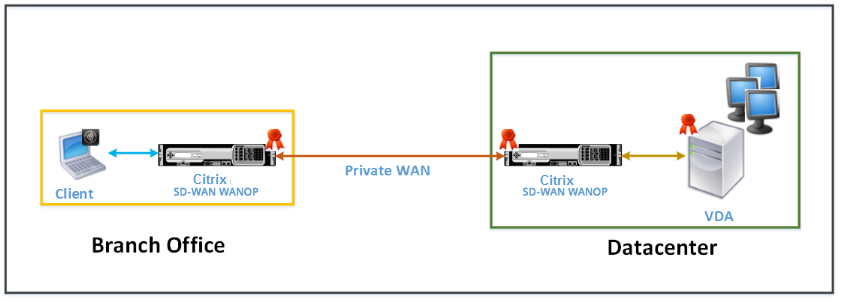
The direct access with end-to-end SSL encryption mode is similar to the Direct Access mode, with the difference that the connection between the client and VDA resources is secured by SSL encryption and uses port 443 instead of port 8008 for the connection.
In this deployment, communication between a pair of Citrix SD-WAN WANOP appliances is secured by making the two appliance secured partners. This deployment is suitable for a corporate network where connections between the client and VDA resources are secured by SSL encryption.
Note
You must configure appropriate certificates on the appliances to create secure partners. For more information about secure partnering, see Secure Peering.
ICA proxy mode:
The following figure shows the deployment topology of Citrix Receiver for HTML5 installed on the client in ICA proxy mode.
Citrix SD-WAN WANOP appliances deployed in ICA proxy mode
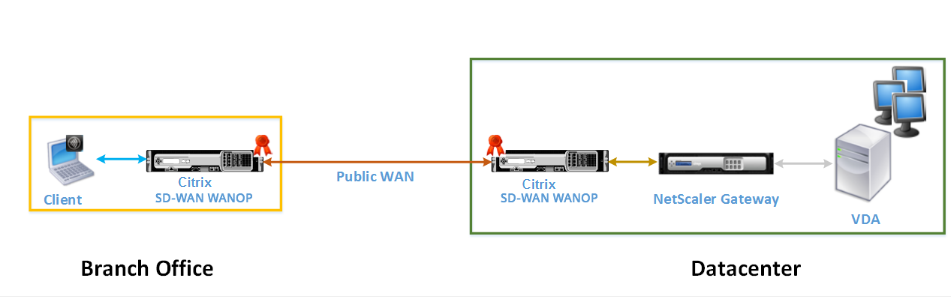
In the ICA proxy mode, a pair of Citrix SD-WAN WANOP appliances is installed across the branch office and a datacenter in inline mode. In addition, you install Citrix Gateway, which proxies VDA, at the datacenter. A client accesses VDA resources through Citrix Receiver for HTML5 over the public WAN. Because the gateway proxies the VDA, two connections are established: an SSL connection between the client and Citrix Gateway and an ICA secured connection between Citrix Gateway and VDA. The Citrix Gateway establishes a connection with VDA resources on behalf of the client. Connections from the gateway to the VDA resources is secured by encryption at the ICA level.
Messages exchanged between the client and VDA are explained in Understanding Messages Exchanged Between the Client and the Server. However, in this case the connection is terminated at Citrix Gateway. The gateway proxies VDA and opens a connection to VDA only after the gateway has negotiated WebSocket authorization. The gateway then transparently passes messages from client to VDA and vice versa.
If you expect users to access VDA resources from a public WAN, you can consider deploying the ICA Proxy mode set up.
Note
You must configure appropriate certificates on the appliances to create secure partners. For more information about secure partnering, see Secure Peering.
ICA proxy mode with end-to-end SSL encryption:
The following figure shows the deployment topology of Citrix Receiver for HTML5 installed on the client in ICA proxy mode secured with end-to-end SSL encryption.
Citrix SD-WAN WANOP appliances deployed in ICA proxy mode secured with end-to-end SSL encryption
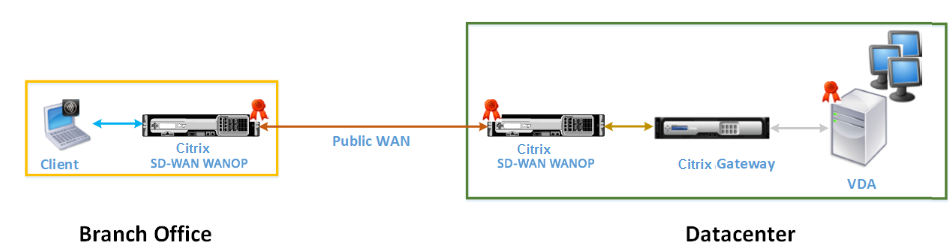
ICA Proxy mode with end-to-end SSL encryption mode is similar to ordinary ICA Proxy mode, with the difference that the connection between the Citrix Gateway and VDA is secured by SSL encryption instead of using an ICA secured connection. In this scenario, you must install appropriate certificates on the Citrix SD-WAN WANOP appliance and VDA. The connection between the Citrix Gateway and VDA uses port 443 instead of port 8008, as in case of ordinary ICA Proxy mode.
This deployment is suitable for a network where you must secure end-to-end communication between clients and VDA, including the connection between Citrix Gateway and VDA.
Full virtual private network (VPN) mode:
The following figure shows the deployment topology of Citrix Receiver for HTML5 installed on the client in the full Virtual Private Network (VPN) mode.
Citrix SD-WAN WANOP appliances deployed in VPN mode
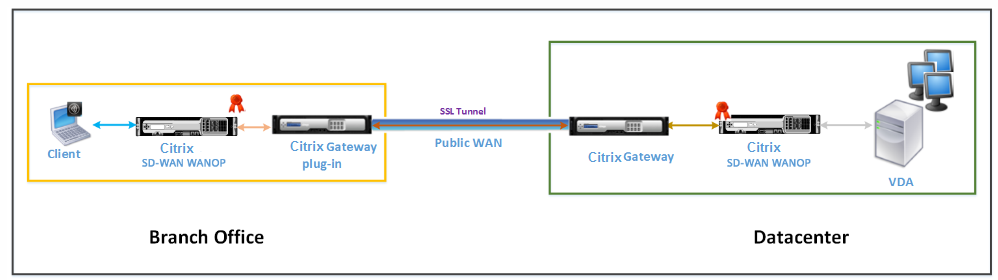
In full VPN mode, a pair of Citrix SD-WAN WANOP appliances is installed across a branch office and the datacenter in inline mode. In addition to Citrix receiver for HTML5, you install the Citrix Gateway plugin on the client and Citrix Gateway interfacing external network at the datacenter. The Citrix Gateway plugin on the client and Citrix Gateway on the datacenter create an SSL tunnel or VPN over the network when they establish a connection. As a result, the client has a direct secure access to the VDA resources, with transparent connection through the Citrix SD-WAN WANOP appliance. When the client connection is terminated at Citrix Gateway, the gateway opens a transparent connection to port 8008 on VDA.
Messages exchanged between the client and VDA are explained in the Understanding Messages Exchanged Between the Client and the Server section. However, in this case the connection is terminated at Citrix Gateway. The gateway proxies VDA and opens a transparent connection to VDA at port 8008, and transparently passes all messages from client to VDA and vice versa.
The Citrix SD-WAN WANOP plug-in enables the client to access resources regardless of the location of the client. When you expect clients to need access to the VDA resources from locations other than their desktops, you can deploy the setup in full virtual Private Network (VPN) mode.
This deployment is suitable for organizations expecting their employees to access resources when they are traveling.
Full virtual private network (VPN) mode with end-to-end SSL encryption:
The following figure shows the deployment topology of Citrix Receiver for HTML5 installed on the client in the full VPN mode secured with end-to-end SSL encryption.
Citrix SD-WAN WANOP appliances deployed in VPN mode secured with end-to-end SSL encryption
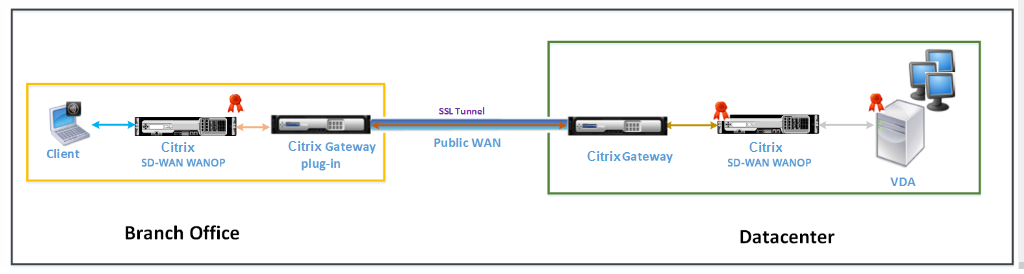
Full Virtual Private Network (VPN) mode with end to end SSL encryption deployment is similar to ordinary full VPN mode, with the difference that the communication between Citrix Gateway and VDA is secured by SSL encryption and uses port 443 instead of port 8008.
This deployment is suitable for organizations that need end-to-end SSL encryption for resources accessed by the employees who are traveling.