Internet access
The Internet Service is used for traffic between an end-user site and sites on the public internet. Internet service traffic is not encapsulated by SD-WAN and does not have the same capabilities as traffic that is delivered across the Virtual Path Service. However, it is important to classify and take account for this traffic on the SD-WAN. Traffic that is identified as Internet Service enables the added ability of SD-WAN being able to actively manage WAN link bandwidth by rate-limiting Internet traffic relative to traffic delivered across the Virtual Path and Intranet traffic per the configuration established by the administrator. In addition to bandwidth provisioning capabilities, SD-WAN has the added capability to load balance traffic delivered across the Internet Service using multiple Internet WAN links, or optionally, utilizing the Internet WAN links in a primary or secondary configuration.
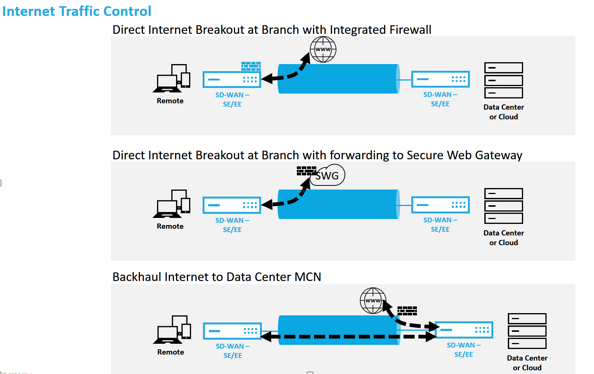
Internet traffic control using the Internet Service on SD-WAN appliances can be configured in the following deployment modes:
-
Direct Internet Breakout at Branch with Integrated Firewall
-
Direct Internet Breakout at Branch forwarding to Secure Web Gateway
-
Backhaul Internet to Data Center MCN
For information on how to configure an Internet service through Citrix SD-WAN Orchestrator service, see Internet Service.
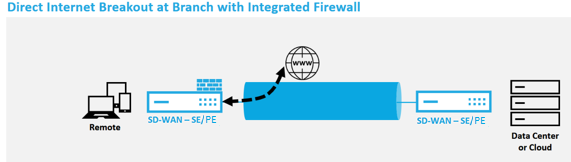
Direct Internet Breakout at Branch with Integrated Firewall
The Internet Service can be utilized in the various deployment modes supported by Citrix SD-WAN.
- Inline Deployment Mode (SD-WAN Overlay)
Citrix SD-WAN can be deployed as an overlay solution in any network. As an overlay solution, SD-WAN generally is deployed behind existing edge routers and/or firewalls. If SD-WAN is deployed behind a network firewall, the interface can be configured as trusted and Internet traffic can be delivered to the firewall as an internet gateway.
- Edge or Gateway Mode
Citrix SD-WAN can be deployed as the edge device, replacing existing edge router and/or firewall devices. Onboard firewall feature allows SD-WAN to protect the network from direct internet connectivity. In this mode, the interface connected to the public internet link is configured as untrusted, forcing encryption to be enabled, and firewall and Dynamic NAT features are enabled to secure the network.
For information on how to configure an Internet service through Citrix SD-WAN Orchestrator service, see Internet Service.
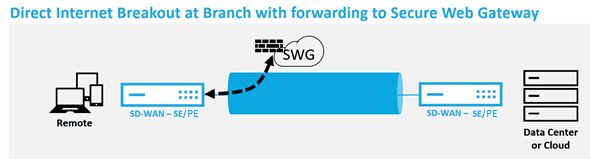
Direct Internet Access with Secure Web Gateway
To secure traffic and enforce policies, enterprises often use MPLS links to backhaul branch traffic to the corporate data center. The data center applies security policies, filters traffic through security appliances to detect malware, and routes the traffic through an ISP. Such backhauling over private MPLS links is expensive. It also results in significant latency, which creates a poor user experience at the branch site. There is also a risk that users bypass your security controls.
An alternative to backhauling is to add security appliances at the branch. However, the cost and complexity increases as you install multiple appliances to maintain consistent policies across the sites. Most significantly, if you have many branch offices, cost management becomes impractical.
One alternative is to enforce security without adding cost, complexity, or latency would be to route all branch Internet traffic using Citrix SD-WAN to the Secure Web Gateway Service. A third-party Secure Web Gateway Service enables granular and central security policy creation to be using by all connected networks. The policies are applied consistently whether the user is at the data center or a branch site. Because Secure Web Gateway solutions are cloud based, you don’t have to add more costly security appliances to the network.
For information on how to configure an Internet service through Citrix SD-WAN Orchestrator service, see Internet Service.
Citrix SD-WAN supports the following third party Secure Web Gateway solutions:
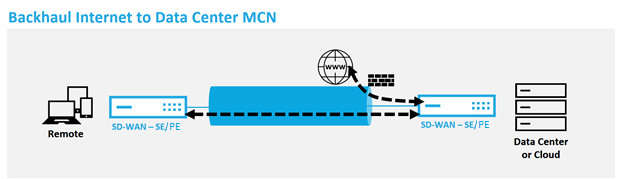
Backhaul Internet
The Citrix SD-WAN solution can backhaul Internet traffic to the MCN site or other branch sites. Backhaul indicates that the traffic destined for the Internet is sent back through another predefined site that can access the Internet. It is useful for networks that do not allow Internet access directly because of security concerns or the underlay networks topology. An example would be a remote site that lacks an external firewall where the on-board SD-WAN firewall does not meet the security requirements for that site. For some environments, backhauling all remote site internet traffic through the hardened DMZ at the Data Center might be the best approach to providing Internet access to users at remote offices. This approach does however have its limitations to be aware of following and the underlay WAN links size appropriately.
-
Backhaul of internet traffic adds latency to internet connectivity and is variable depending on the distance of the branch site for the data center.
-
Backhaul of internet traffic consumes bandwidth on the Virtual Path and is accounted for in sizing of WAN links.
-
Backhaul of internet traffic might over-subscribe the Internet WAN link at the Data Center.
All Citrix SD-WAN devices can terminate up to eight distinct Internet WAN links into a single device. Licensed throughput capabilities for the aggregated WAN links are listed per respective appliance on the Citrix SD-WAN data sheet.
Hairpin Mode
With hairpin deployment, you can implement use of a Remote Hub site for internet access through backhaul or hairpin when local internet services are unavailable or are experiencing slower traffic. You can apply high bandwidth routing between client sites by allowing backhauling from specific sites.
The purpose of a hairpin deployment from a non-WAN to a WAN forwarding site is to provide more efficient deployment process and more streamlined technical implementation. You can use a remote hub site for internet access when needs arise, and can route flows through the virtual path to the SD-WAN network.

For example, consider an administrator with multiple SD-WAN Sites, A and B. Site A has poor internet service. Site B has usable internet service, with which you want to backhaul traffic from site A to site B only. You can try to accomplish this without the complexity of strategically weighted route costs and propagation to sites that should not receive the traffic.
Also, the route table is not shared across all sites in a Hairpin deployment. For example, if traffic is hairpin’ned between Site A and Site B through Site C, then only Site C would be aware of site A’s and B’s routes. Site A and Site B do not share each other’s route table unlike in WAN-to-WAN forwarding.
When traffic is Hairpin’ned between Site A and Site B through Site C, the static routes are required to be added in Site A and Site B indicating that the next hop for both the sites is the intermediate Site C.
WAN-to-WAN Forwarding and Hairpin deployment have certain differences, namely:
-
Dynamic Virtual Paths are not configured. Always, the intermediate site sees all the traffic between the two sites.
-
Does not participate in WAN-to-WAN Forwarding groups.
WAN-to-WAN Forwarding and Hairpin deployment are mutually exclusive. Only one of them can be configured at any given point in time.
Citrix SD-WAN SE and VPX (virtual) appliances support hairpin deployment. You can now configure a 0.0.0.0/0 route to hairpin traffic between two locations without affecting any additional locations. If hairpinning used for intranet traffic, specific Intranet routes are added to the client site to forward intranet traffic through the virtual path to the hairpin site. Enabling WAN-to-WAN forwarding to accomplish hairpin functionality is no longer required.