Unsanctioned websites
Applications (intranet or internet) that are not configured within Secure Private Access are regarded as “Unsanctioned Websites”. By default, Secure Private Access denies access to all intranet web applications if there are no applications and access policies configured for those applications.
For all other internet URLs or SaaS applications that do not have an app configured, admins can use the Settings > Unsanctioned Websites tab from the admin console to allow or deny access via Citrix Enterprise Browser. Admins can also redirect access to a Remote Browser Isolated (RBI) environment to prevent browser-based attacks. If an admin has configured redirection of URLs to RBI, the following actions occur.
- Secure Private Access converts the domains.
- Citrix Enterprise Browser then sends these URLs back to Secure Private Access.
- Secure Private Access redirects those URLs to the Remote Browser Isolation service.
You can use wildcards, such as *.example.com, to control access to all the domains in that website and all the pages within that domain.
Note:
By default, settings are configured to ALLOW access to all internet URLs or SaaS apps via Citrix Enterprise Browser.
How unsanctioned websites work
- URL analysis check is done to determine if the URL is a Citrix service URL.
- The URL is then checked to determine if it is an Enterprise web or SaaS app URL.
- The URL is then checked to determine if it is identified as a blocked URL, or if it must be redirected to a secure browser session or if the URL can be allowed to be accessed.
The following illustration explains the end user traffic flow.
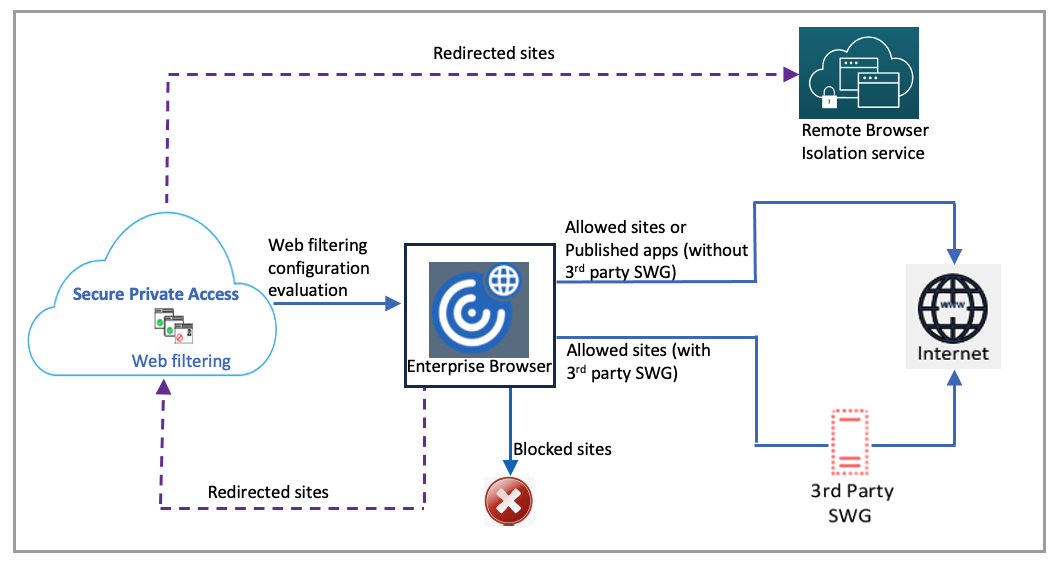
When a request arrives, the following checks are performed, and corresponding actions are taken:
-
Does the request match the global allow list?
-
If it matches, the user can access the requested website.
-
If it does not match, website lists are checked.
-
-
Does the request match the configured website list?
-
If it matches, the following sequence determines the action.
-
Block
-
Redirect
-
Allow
-
-
If it does not match, the default action (ALLOW) is applied. The default action cannot be changed.
-
Configure rules for unsanctioned websites
-
In the Secure Private Access console, click Settings > Unsanctioned Websites.
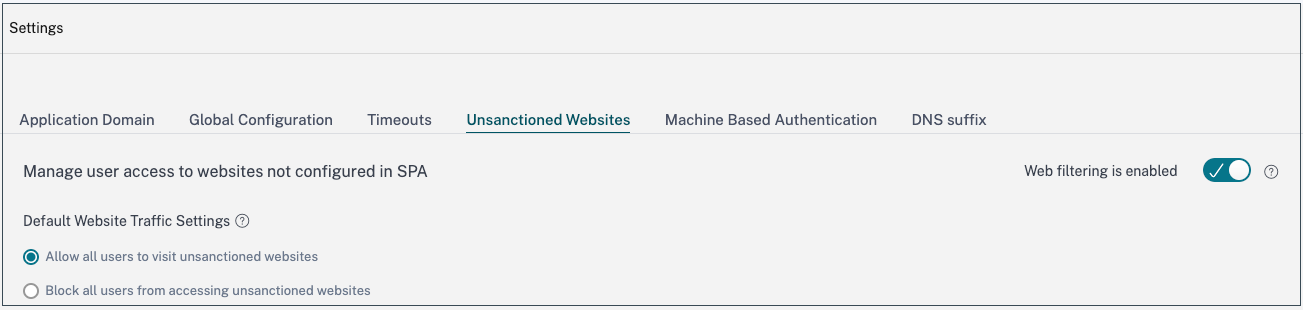
Note:
- The web filtering feature is enabled by default and access to all unsanctioned internet URLs is allowed.
- You can change the setting to Block all users from accessing unsanctioned websites to block access to any internet URL via Citrix Enterprise Browser for all users.
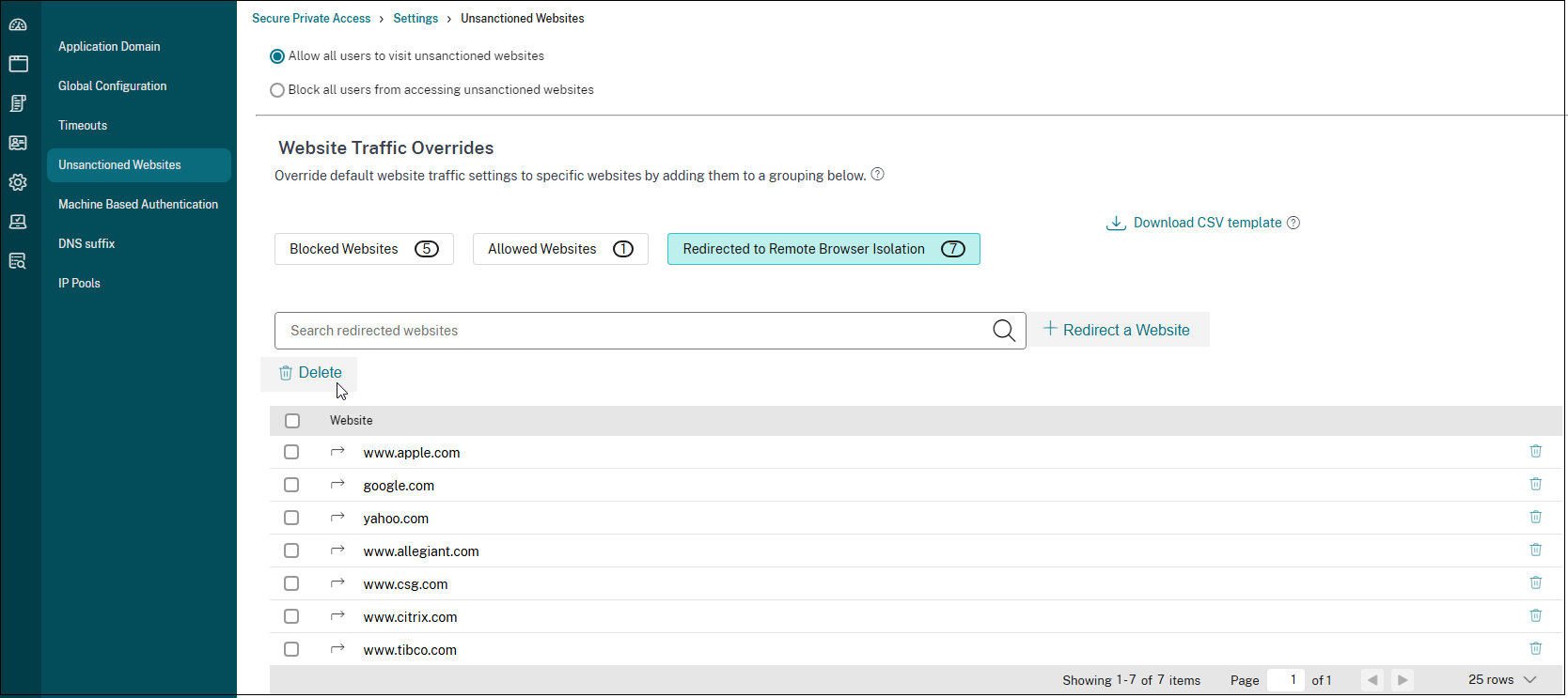
You can also change settings for specific URLs by adding them to blocked websites, allowed websites, or redirected to the Remote Browser Isolation list.
For example, if you have blocked access to all unsanctioned URLs by default and you want to allow access to only a few specific internet URLs, then you can do so by performing the following steps:
- Click the Allowed Websites tab, and then click Allow a Website.
- Add the website address that must be allowed access. You can either manually add the website address or drag and drop a CSV file containing the website address.
-
Click Add a URL and then click Save.
The URL is added to the list of allowed websites.
Note:
A paid Remote Browser Isolation Standard service customer (organization) gets 5,000 hours of use per year by default. For more hours, they must buy the secure browser add-on packs. You can track the usage of the Remote Browser Isolation service. For more information, see the following topics: