Digital signatures
Aug 14, 2017
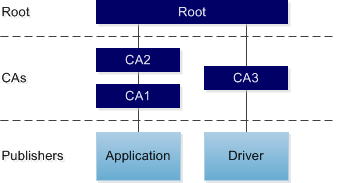
A digital signature is a mechanism that provides users with assurance that a digital file comes from an identifiable source and has not been tampered with. Digital signatures often include a chain of certificates. The publisher of the digital file generates the digital signature using a certificate issued by a certification authority (CA). The CA is responsible for verifying the publisher’s identity. That CA’s certificate may in turn have been issued by another CA, and so on back to the root CA. (There can be more than one root.) In this way the certificates form a chain, as the following diagram illustrates.
The Windows operating system (OS) stores certificates and lists of trusted and untrusted publishers and CAs on a per-machine and per-user basis. You can use the Certificates snap-in to the Microsoft Management Console to view and manage the certificates that are stored on the OS.
Capture of digital signature DNA
When you import applications into AppDNA, the import process captures information about any digital signatures that are found in the application files. When present, digital signatures are typically in the application’s portable executable (PE) files (such as executables and DLLs). However, for drivers, the digital signature can be in an associated catalog file.
The import process extracts and stores the signature’s basic details and information about each certificate in the certificate chain. The import process attempts to determine whether the signature is valid within the context of the certificate chain on the AppDNA import machine. However, the results may differ on another machine or OS, or for a different user, if the stored certificate information differs. For this reason, some of the algorithms do additional checks against the selected OS image(s).
The import process does not check certificate revocation lists, because this would slow down the import to an unacceptable degree.
Untrusted signatures on Windows 8 and Windows Server 2012
Both Windows 8 and Windows Server 2012 block files signed by an untrusted publisher from running. The practical impact of this depends on which file is affected. If it is the main application executable, the application will not run – Windows presents the user with a message that explains that the application does not meet the signing requirement. However, if the affected file is a minor DLL, the application may run but will fail when functionality that relies on the DLL is invoked. If the affected file is a kernel-mode driver, it may not be possible to install or run the driver.
Kernel-mode drivers are device drivers that run in “supervisor mode”, which provides privileged access to low-level capabilities and performance advantages compared to drivers that run in standard “user mode”. If a program that is running in supervisor mode fails, it can cause the entire system to fail. Windows Server 2012 and 64-bit editions of Windows 8 therefore block the installation and running of kernel-mode drivers that are signed by an untrusted publisher.
Note: Sometimes an application may contain multiple digital signatures from more than one publisher – for example, if the application includes third-party components that are also signed.
Windows 8 and Windows Server 2012 algorithms
The following algorithms detect files that contain an untrusted digital signature. Untrusted means that either the publisher or one of the CAs in the chain appears in the list of untrusted publishers and CAs stored in the target OS image. The results for these algorithms therefore depend on the target OS image that is selected.
- For Windows 8 and Windows 8.1: WIN8_UNTRUSTED_001
- For Windows Server 2012 and Windows Server 2012 R2: W2K12_UNTRUSTED_001
The remediation report views provide information about which file within the application is affected, whether this is a driver, and details of the untrusted certificate.
Remediation
For external applications, contact the manufacturer to obtain an updated version of the application or driver that is signed by a trusted publisher.
If this is not possible, investigate why the publisher or CA is on the untrusted list. You can use the Certificates snap-in to the Microsoft Management Console to remove a publisher from the untrusted list in the OS image. However, this should not be done without first establishing that it is indeed trustworthy and that the application is safe and conforms to security policies.
For instructions for opening the Certificates snap-in, see View or manage your certificates on the Microsoft web site. After you have opened the Certificates snap-in, use the Help to view detailed documentation about viewing and managing certificates.
 View PDF
View PDF

