Secure user sessions using TLS
As of Version 7.16, the Linux VDA supports TLS encryption for secure user sessions. TLS encryption is disabled by default.
Enable TLS encryption
To enable TLS encryption for secure user sessions, obtain certificates and enable TLS encryption on both the Linux VDA and the Delivery Controller™ (the Controller).
Obtain certificates
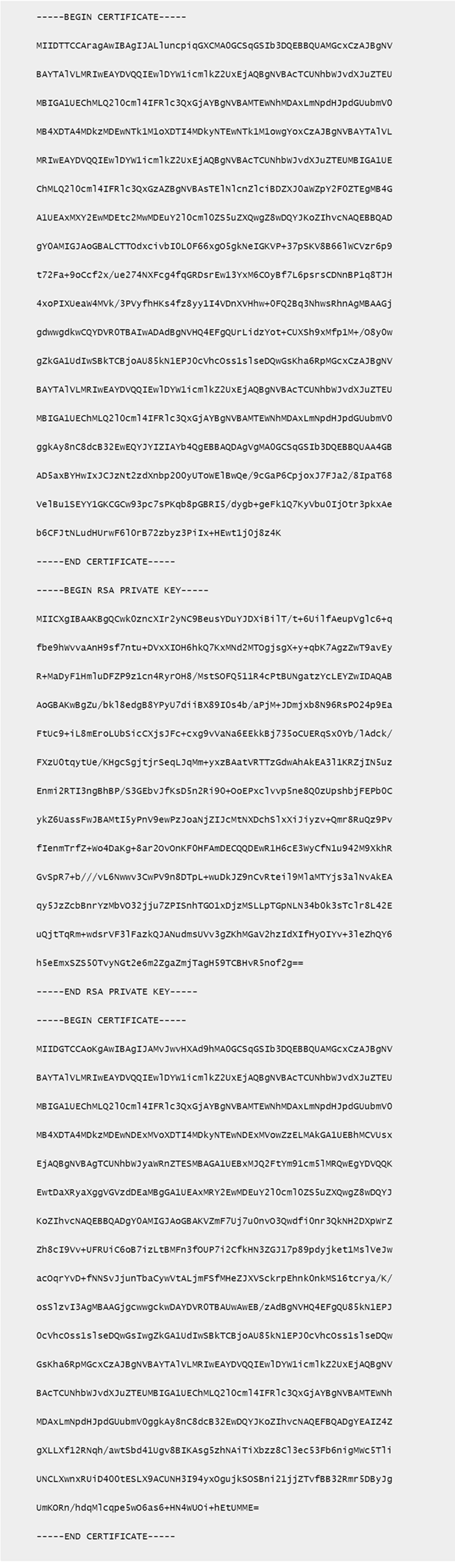
Obtain server certificates in PEM format and root certificates in CRT format from a trusted Certificate Authority (CA). A server certificate contains the following sections:
- Certificate
- Unencrypted private key
- Intermediate certificates (optional)
An example of a server certificate:
Enable TLS encryption
Enable TLS encryption on the Linux VDA
On the Linux VDA, use the enable_vdassl.sh tool to enable (or disable) TLS encryption. The tool is located in the /opt/Citrix/VDA/sbin directory. For information about the options available in the tool, run the /opt/Citrix/VDA/sbin/enable_vdassl.sh -help command.
Tip: A server certificate must be installed on each Linux VDA server and root certificates must be installed on each Linux VDA server and client.
Enable TLS encryption on the Controller
Note:
You can enable TLS encryption only for entire delivery groups. You cannot enable TLS encryption for specific applications.
In a PowerShell window on the Controller, run the following commands in sequence to enable TLS encryption for the target delivery group.
Add-PSSnapin citrix.*Get-BrokerAccessPolicyRule –DesktopGroupName 'GROUPNAME' | Set-BrokerAccessPolicyRule –HdxSslEnabled $true
Note:
To ensure that only VDA FQDNs are contained in an ICA® session file, you can also run the Set-BrokerSite –DnsResolutionEnabled $true command. The command enables DNS resolution. If you disable DNS resolution, an ICA session file discloses VDA IP addresses and provides FQDNs only for the TLS-related items such as SSLProxyHost and UDPDTLSPort.
To disable TLS encryption on the Controller, run the following commands in sequence:
Add-PSSnapin citrix.*Get-BrokerAccessPolicyRule –DesktopGroupName 'GROUPNAME' | Set-BrokerAccessPolicyRule –HdxSslEnabled $falseSet-BrokerSite –DnsResolutionEnabled $false
Troubleshooting
The following “Can’t assign requested address” error might occur in Citrix Workspace™ app for Windows when you try to access a published desktop session:
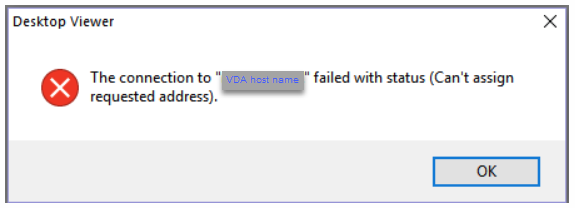
As a workaround, add an entry to the hosts file, which is similar to:
<IP address of the Linux VDA> <FQDN of the Linux VDA>
On Windows machines, the hosts file typically locates at C:\Windows\System32\drivers\etc\hosts.
The official version of this content is in English. Some of the Cloud Software Group documentation content is machine translated for your convenience only. Cloud Software Group has no control over machine-translated content, which may contain errors, inaccuracies or unsuitable language. No warranty of any kind, either expressed or implied, is made as to the accuracy, reliability, suitability, or correctness of any translations made from the English original into any other language, or that your Cloud Software Group product or service conforms to any machine translated content, and any warranty provided under the applicable end user license agreement or terms of service, or any other agreement with Cloud Software Group, that the product or service conforms with any documentation shall not apply to the extent that such documentation has been machine translated. Cloud Software Group will not be held responsible for any damage or issues that may arise from using machine-translated content.
DIESER DIENST KANN ÜBERSETZUNGEN ENTHALTEN, DIE VON GOOGLE BEREITGESTELLT WERDEN. GOOGLE LEHNT JEDE AUSDRÜCKLICHE ODER STILLSCHWEIGENDE GEWÄHRLEISTUNG IN BEZUG AUF DIE ÜBERSETZUNGEN AB, EINSCHLIESSLICH JEGLICHER GEWÄHRLEISTUNG DER GENAUIGKEIT, ZUVERLÄSSIGKEIT UND JEGLICHER STILLSCHWEIGENDEN GEWÄHRLEISTUNG DER MARKTGÄNGIGKEIT, DER EIGNUNG FÜR EINEN BESTIMMTEN ZWECK UND DER NICHTVERLETZUNG VON RECHTEN DRITTER.
CE SERVICE PEUT CONTENIR DES TRADUCTIONS FOURNIES PAR GOOGLE. GOOGLE EXCLUT TOUTE GARANTIE RELATIVE AUX TRADUCTIONS, EXPRESSE OU IMPLICITE, Y COMPRIS TOUTE GARANTIE D'EXACTITUDE, DE FIABILITÉ ET TOUTE GARANTIE IMPLICITE DE QUALITÉ MARCHANDE, D'ADÉQUATION À UN USAGE PARTICULIER ET D'ABSENCE DE CONTREFAÇON.
ESTE SERVICIO PUEDE CONTENER TRADUCCIONES CON TECNOLOGÍA DE GOOGLE. GOOGLE RENUNCIA A TODAS LAS GARANTÍAS RELACIONADAS CON LAS TRADUCCIONES, TANTO IMPLÍCITAS COMO EXPLÍCITAS, INCLUIDAS LAS GARANTÍAS DE EXACTITUD, FIABILIDAD Y OTRAS GARANTÍAS IMPLÍCITAS DE COMERCIABILIDAD, IDONEIDAD PARA UN FIN EN PARTICULAR Y AUSENCIA DE INFRACCIÓN DE DERECHOS.
本服务可能包含由 Google 提供技术支持的翻译。Google 对这些翻译内容不做任何明示或暗示的保证,包括对准确性、可靠性的任何保证以及对适销性、特定用途的适用性和非侵权性的任何暗示保证。
このサービスには、Google が提供する翻訳が含まれている可能性があります。Google は翻訳について、明示的か黙示的かを問わず、精度と信頼性に関するあらゆる保証、および商品性、特定目的への適合性、第三者の権利を侵害しないことに関するあらゆる黙示的保証を含め、一切保証しません。
ESTE SERVIÇO PODE CONTER TRADUÇÕES FORNECIDAS PELO GOOGLE. O GOOGLE SE EXIME DE TODAS AS GARANTIAS RELACIONADAS COM AS TRADUÇÕES, EXPRESSAS OU IMPLÍCITAS, INCLUINDO QUALQUER GARANTIA DE PRECISÃO, CONFIABILIDADE E QUALQUER GARANTIA IMPLÍCITA DE COMERCIALIZAÇÃO, ADEQUAÇÃO A UM PROPÓSITO ESPECÍFICO E NÃO INFRAÇÃO.

