解决了 Windows 登录问题
本文介绍了用户使用证书和/或智能卡登录时 Windows 提供的日志和错误消息。 可以使用这些日志提供的信息对身份验证失败问题进行故障排除。
证书和公钥基础结构
Windows Active Directory 维护负责管理用户登录时使用的证书的多个证书存储。
- NTAuth 证书存储:要针对 Windows 进行身份验证,必须将即时颁发用户证书(即,不支持任何证书链)的证书颁发机构放置在 NTAuth 存储中。 要查看这些证书,请在 certutil 程序中输入以下命令:certutil –viewstore –enterprise NTAuth。
- 根证书和中间证书存储:一般而言,证书登录系统只能提供单个证书,因此,如果正在使用证书链,所有计算机上的中间证书存储都必须包括这些证书。 根证书必须位于可信证书存储中,而倒数第二个证书必须位于 NTAuth 存储中。
- 登录证书扩展名和组策略:可以将 Windows 配置为强制验证 EKU 以及其他证书策略。请参阅 Microsoft 文档:https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/ff404287(v=ws.10)。
| 注册表策略 | 说明 |
|---|---|
| AllowCertificatesWithNoEKU | 禁用时,证书必须包括智能卡登录扩展密钥用法 (EKU)。 |
| AllowSignatureOnlyKeys | 默认情况下,Windows 会过滤掉不允许进行 RSA 解密的证书私钥。此选项将覆盖该过滤器。 |
| AllowTimeInvalidCertificates | 默认情况下,Windows 会过滤掉过期的证书。此选项将覆盖该过滤器。 |
| EnumerateECCCerts | 启用椭圆曲线身份验证。 |
| X509HintsNeeded | 如果某个证书不包含唯一的用户主体名称 (UPN),或者可以不确定,此选项将允许用户手动指定其 Windows 登录帐户。 |
| UseCachedCRLOnlyAnd、IgnoreRevocationUnknownErrors | 禁用吊销检查(通常在域控制器上设置)。 |
- 域控制器证书: 所有服务器必须具有恰当的“域控制器”证书,才能对 Kerberos 连接进行身份验证。 可以使用“本地计算机证书个人存储”MMC 管理单元菜单申请这些证书。
UPN 名称和证书映射
建议用户证书在使用者替代名称扩展名中包括一个唯一的用户主体名称 (UPN)。
Active Directory 中的 UPN 名称
默认情况下,Active Directory 中的每个用户都具有建立在模式 <samUsername>@<domainNetBios> 和 <samUsername>@<domainFQDN> 的基础之上的隐式 UPN。 可用域和 FQDN 都包括在林的 RootDSE 条目中。 请注意,单个域可以具有多个在 RootDSE 中注册的 FQDN 地址。
此外,Active Directory 中的每个用户都具有显式 UPN 和 altUserPrincipalNames。 这些是用于指定该用户的 UPN 的 LDAP 条目。
按 UPN 搜索用户时,Windows 首先在当前域(取决于对查找 UPN 的过程的识别)中查找显式 UPN,然后查找替代 UPN。 如果没有匹配项,则将查找隐式 UPN,这样可以解析到林中的其他域。
证书映射服务
如果某个证书不包括显式 UPN,Active Directory 将具有用于存储完全匹配的公用证书以供在 x509certificate 属性中使用的选项。 计算机可以直接查询此属性(默认情况下,在单个域中查询),以便为用户解析此类证书。
系统将向用户提供一个选项以指定可加快此搜索速度并且还允许在跨域环境中使用此功能的用户帐户。
如果林中存在多个域,并且用户未明确指定域,Active Directory rootDSE 将指定证书映射服务的位置。 该服务通常位于全局目录计算机上,并且在林中具有所有 x509certificate 属性的缓存视图。 可以使用此计算机仅基于证书来有效地查找任意域中的用户帐户。
控制登录域控制器选择
当环境中包含多个域控制器时,查看并显示用于身份验证的域控制器将非常有用,这样可以启用并检索日志。
控制域控制器选择
要强制 Windows 使用特定的 Windows 域控制器进行登录,可以通过配置 lmhosts 文件(\Windows\System32\drivers\etc\lmhosts)来显式设置 Windows 计算机使用的域控制器列表。
该位置通常存在一个名为 lmhosts.sam 的示例文件。其内容只有一行:
1.2.3.4 dcnetbiosname #PRE #DOM:mydomai
其中,1.2.3.4 为 mydomain 域中名为 dcnetbiosname 的域控制器的 IP 地址。
重新启动后,Windows 计算机将使用该信息登录 mydomain。 请注意,完成调试后,必须还原此配置。
识别正在使用的域控制器
登录时,Windows 将使用让该用户登录的域控制器设置一个 MSDOS 环境变量。 要查看该变量,请启动命令提示窗口并输入以下命令:echo %LOGONSERVER%。
与身份验证有关的日志存储在此命令返回的计算机中。
启用帐户审核事件
默认情况下,Windows 域控制器不启用完全帐户审核日志。 可以在组策略编辑器中通过安全设置中的审核策略对其进行控制。启用后,域控制器将在安全日志文件中生成额外的事件日志信息。
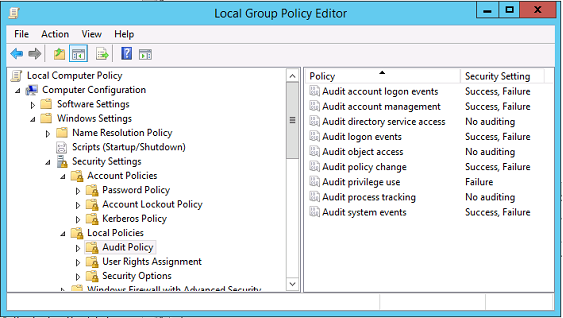
证书验证日志
检查证书有效性
如果将智能卡证书导出为 DER 证书(不需要任何私钥),则可以通过以下命令验证其有效性:certutil –verify user.cer
启用 CAPI 日志记录
在域控制器和用户计算机上,打开事件查看器并启用 Microsoft/Windows/CAPI2/Operational Logs 的日志记录功能。
可以通过 CurrentControlSet\Services\crypt32 下的注册表项控制 CAPI 日志记录功能。
| 值 | 说明 |
|---|---|
| DiagLevel (DWORD) | 详细级别(0 到 5) |
| DiagMatchAnyMask (QUADWORD) | 事件过滤器(对所有事件使用 0xffffff) |
| DiagProcessName (MULTI_SZ) | 按进程名称过滤(例如,LSASS.exe) |
CAPI 日志
| 消息 | 说明 |
|---|---|
| 构建链 | 名为 CertGetCertificateChain 的 LSA(包括结果) |
| 验证吊销 | 名为 CertVerifyRevocation 的 LSA(包括结果) |
| X509 对象 | 在详细模式下,证书和证书吊销列表 (CRL) 转储到 AppData\LocalLow\Microsoft\X509Objects |
| 验证证书链策略 | 名为 CertVerifyChainPolicy 的 LSA(包括参数) |
错误消息
| 错误代码: | 说明 |
|---|---|
| 证书不可信 | 无法使用计算机的中间证书存储和可信根证书存储中的证书构建智能卡证书。 |
| 证书吊销检查错误 | 无法从证书 CRL 分发点指定的地址下载智能卡的 CRL。如果强制执行吊销检查,则会阻止成功登录。请参阅证书和公钥基础结构部分。 |
| 证书用途错误 | 证书不适用于登录。例如,证书可能是服务器证书或签名证书。 |
Kerberos 日志
要启用 Kerberos 日志记录,请在域控制器和最终用户计算机上创建以下注册表值:
| 配置单元 | Value name(值名称) | 值 [DWORD] |
|---|---|---|
| CurrentControlSet\Control\Lsa\Kerberos\Parameters | 日志级别 | 0x1 |
| CurrentControlSet\Control\Lsa\Kerberos\Parameters | KerbDebuglevel | 0xffffffff |
| CurrentControlSet\Services\Kdc | KdcDebugLevel | 0x1 |
| CurrentControlSet\Services\Kdc | KdcExtraLogLevel | 0x1f |
Kerberos 日志记录输出到系统事件日志中。
- “不可信证书”等消息应能够轻松诊断。
- 下面两个错误代码为信息性代码,可以安全地忽略:
- KDC_ERR_PREAUTH_REQUIRED(用于向后兼容域控制器较旧的域控制器)
- 未知错误 0x4b
事件日志消息
本节介绍了用户使用证书登录时域控制器和工作站上的预期日志条目。
- 域控制器 CAPI2 日志
- 域控制器安全日志
- Virtual Delivery Agent (VDA) 安全日志
- VDA CAPI 日志
- VDA 系统日志
域控制器 CAPI2 日志
登录过程中,域控制器将验证调用者的证书,从而生成以下格式的一系列日志条目。
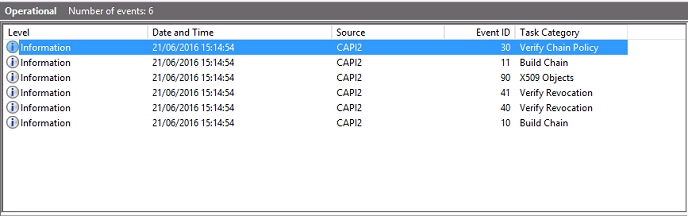
最终事件日志消息在域控制器上显示 lsass.exe,从而根据 VDA 提供的证书构建一个链,并验证其有效性(包括吊销)。结果返回为“ERROR_SUCCESS”。
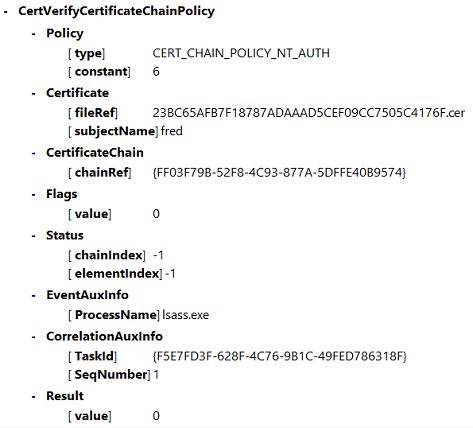
域控制器安全日志
域控制器显示一系列登录事件,关键事件为 4768,其中,证书用于发出 Kerberos Ticket Granting Ticket (krbtgt)。
在此消息之前显示的消息将显示用于进行身份验证以登录域控制器的服务器的计算机帐户。 在此消息之后显示的消息将显示属于正在用于针对域控制器进行身份验证的新 krbtgt 的用户帐户。
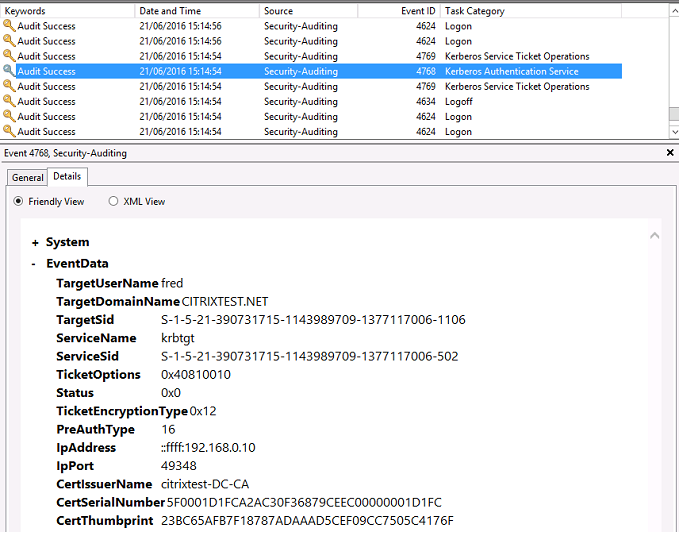
VDA 安全日志
与登录事件相对应的 VDA 安全审核日志是指 winlogon.exe 中事件 ID 为 4648 的条目。
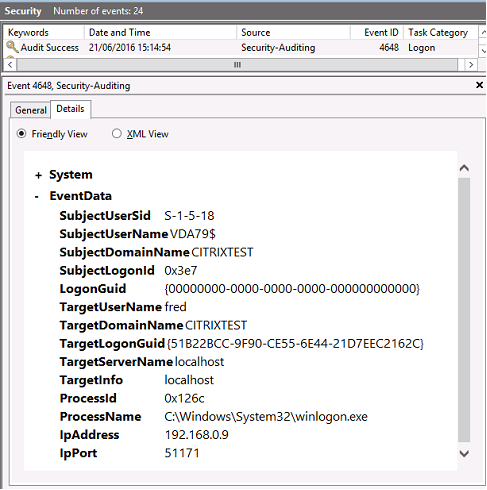
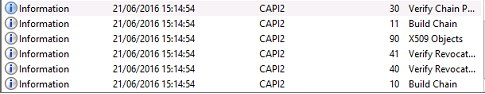
VDA CAPI 日志
此示例 VDA CAPI 日志显示 lsass.exe 中的单个链构建和验证顺序,用于验证域控制器证书 (dc.citrixtest.net)。
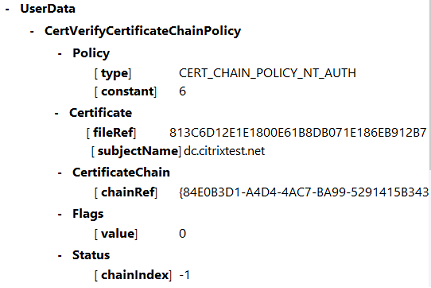
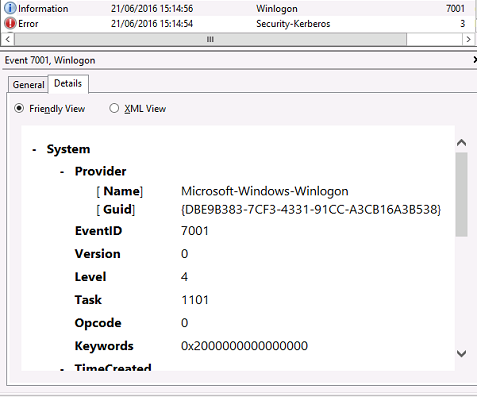
VDA 系统日志
启用了 Kerberos 日志记录时,系统日志将显示错误 KDC_ERR_PREAUTH_REQUIRED(可以忽略)以及 Winlogon 中显示 Kerberos 登录成功的条目。
事件日志
以下各表列出了由 FAS 生成的事件日志条目。
管理事件[联合身份验证服务]
[事件来源:Citrix.Authentication.FederatedAuthenticationService]
将记录这些事件,以响应 FAS 服务器的配置变化。
| 日志代码 |
|---|
| [S001] ACCESS DENIED: User [{0}] is not a member of Administrators group |
| [S002] ACCESS DENIED: User [{0}] is not an Administrator of Role [{1}] |
| [S003] Administrator [{0}] setting Maintenance Mode to [{1}] |
| [S004] Administrator [{0}] enrolling with CA [{1}] templates [{2} and {3}] |
| [S005] Administrator [{0}] de-authorizing CA [{1}] |
| [S006] Administrator [{0}] creating new Certificate Definition [{1}] |
| [S007] Administrator [{0}] updating Certificate Definition [{1}] |
| [S008] Administrator [{0}] deleting Certificate Definition [{1}] |
| [S009] Administrator [{0}] creating new Role [{1}] |
| [S010] Administrator [{0}] updating Role [{1}] |
| [S011] Administrator [{0}] deleting Role [{1}] |
| [S012] Administrator [{0}] creating certificate [upn: {1} sid: {2} role: {3}][Certificate Definition: {4}][Security Context: {5}] |
| [S013] Administrator [{0}] deleting certificates [upn: {1} role: {2} Certificate Definition: {3} Security Context: {4}] |
| [S015] Administrator [{0}] creating certificate request [TPM: {1}] |
| [S016] Administrator [{0}] importing Authorization certificate [Reference: {1}] |
| [S050] Administrator [{0}] creating new cloud configuration: [{1}] |
| [S051] Administrator [{0}] updating cloud configuration: [{1}] |
| [S052] Administrator [{0}] removing cloud configuration |
| 日志代码 |
|---|
| [S401] Performing configuration upgrade – [From version {0}][to version {1}] |
| [S402] ERROR: The Citrix Federated Authentication Service must be run as Network Service [currently running as: {0}] |
| [S404] Forcefully erasing the Citrix Federated Authentication Service database |
| [S405] An error occured while migrating data from the registry to the database: [{0}] |
| [S406] Migration of data from registry to database is complete (note: user certificates are not migrated) |
| [S407] Registry-based data was not migrated to a database since a database already existed |
| [S408] Cannot downgrade the configuration – [From version {0}][to version {1}] |
| [S409] ThreadPool MinThreads adjusted from [workers: {0} completion: {1}] to: [workers: {2} completion: {3}] |
| [S410] Failed to adjust ThreadPool MinThreads from [workers: {0} completion: {1}] to: [workers: {2} completion: {3}] |
| [S411] Error starting the FAS service: [{0}] |
创建身份声明 [联合身份验证服务]
[事件来源:Citrix.Authentication.FederatedAuthenticationService]
在运行期间,当可信服务器声明用户登录时,将在 FAS 服务器上记录这些事件。
| 日志代码 |
|---|
| [S101] Server [{0}] is not authorized to assert identities in role [{1}] |
| [S102] Server [{0}] failed to assert UPN [{1}] (Exception: {2}{3}) |
| [S103] Server [{0}] requested UPN [{1}] SID {2}, but lookup returned SID {3} |
| [S104] Server [{0}] failed to assert UPN [{1}] (UPN not allowed by role [{2}]) |
| [S105] Server [{0}] issued identity assertion [upn: {1}, role {2}, Security Context: [{3}]] |
| [S120] Issuing certificate to [upn: {0} role: {1} Security Context: [{2}]] |
| [S121] Certificate issued to [upn: {0} role: {1}] by [certifcate authority: {2}] |
| [S122] Warning: Server is overloaded [upn: {0} role: {1}][Requests per minute {2}]. |
| [S123] Failed to issue a certificate for [upn: {0} role: {1}] [exception: {2}] |
| [S124] Failed to issue a certificate for [upn: {0} role: {1}] at [certifcate authority: {2}] [exception: {3}] |
Acting as a relying party [联合身份验证服务]
[事件来源:Citrix.Authentication.FederatedAuthenticationService]
VDA 将用户登录时,这些事件将在运行时记录在 FAS 服务器上。
| 日志代码 |
|---|
| [S201] Relying party [{0}] does not have access to a password. |
| [S202] Relying party [{0}] does not have access to a certificate. |
| [S203] Relying party [{0}] does not have access to the Logon CSP |
| [S204] Relying party [{0}] accessing the Logon CSP for [upn: {1}] in role: [{2}] [Operation: {3}] as authorized by [{4}] |
| [S205] Calling account [{0}] is not a relying party in role [{1}] |
| [S206] Calling account [{0}] is not a relying party |
| [S208] Private Key operation failed [Operation: {0}][upn: {1} role: {2} certificateDefinition {3}][Error {4} {5}]. |
In-session certificate server [联合身份验证服务]
[事件来源:Citrix.Authentication.FederatedAuthenticationService]
当用户使用会话中证书时,会在 FAS 服务器上记录这些事件。
| 日志代码 |
|---|
| [S301] Access Denied: User [{0}] does not have access to a Virtual Smart Card |
| [S302] User [{0}] requested unknown Virtual Smart Card [thumbprint: {1}] |
| [S303] Access Denied: User [{0}] does not match Virtual Smart Card [upn: {1}] |
| [S304] User [{0}] running program [{1}] on computer [{2}] using Virtual Smart Card [upn: {3} role: {4} thumbprint: {5}] for private key operation [{6}] |
| [S305] Private Key operation failed [Operation: {0}][upn: {1} role: {2} containerName {3}][Error {4} {5}]. |
FAS assertion plugin [联合身份验证服务]
[事件来源:Citrix.Authentication.FederatedAuthenticationService]
这些事件由 FAS 断言插件记录。
| 日志代码 |
|---|
| [S500] No FAS assertion plugin is configured |
| [S501] The configured FAS assertion plugin could not be loaded [exception:{0}] |
| [S502] FAS assertion plugin loaded [pluginId={0}] [assembly={1}] [location={2}] |
| [S503] Server [{0}] failed to assert UPN [{1}] (logon evidence was supplied but the plugin [{2}] does not support it) |
| [S504] Server [{0}] failed to assert UPN [{1}] (logon evidence was supplied but there is no configured FAS plugin) |
| [S505] Server [{0}] failed to assert UPN [{1}] (the plugin [{2}] rejected the logon evidence with status [{3}] and message [{4}]) |
| [S506] The plugin [{0}] accepted logon evidence from server [{1}] for UPN [{2}] with message [{3}] |
| [S507] Server [{0}] failed to assert UPN [{1}] (the plugin [{2}] threw exception [{3}]) |
| [S507] Server [{0}] failed to assert UPN [{1}] (the plugin [{2}] threw exception [{3}]) |
| [S508] Server [{0}] failed to assert UPN [{1}] (access disposition was supplied but the plugin [{2}] does not support it) |
| [S509] Server [{0}] failed to assert UPN [{1}] (access disposition was supplied but there is no configured FAS plugin) |
| [S510] Server [{0}] failed to assert UPN [{1}] (the access disposition was deemed invalid by plugin [{2}] |
启用了 Workspace 的 FAS [联合身份验证服务]
[事件来源:Citrix.Fas.Cloud]
将 FAS 与 Workspace 结合使用时会记录这些事件。
| 日志代码 |
|---|
| [S001] Rotating Citrix Cloud service keys [fas id={0}] |
| [S002] The FAS cloud service is starting. FasHub cloud service URL: {0} |
| [S003] FAS registered with the cloud [fas id: {0}] [transaction id: {1}] |
| [S004] FAS failed to register with the cloud [fas id: {0}] [transaction id: {1}] [exception: {2}] |
| [S005] FAS sent its current configuration to the cloud [fas id: {0}] [transaction id: {1}] |
| [S006] FAS failed to send its current configuration to the cloud [fas id: {0}] [transaction id: {1}] [exception: {2}] |
| [S007] FAS unregisted from the cloud [fas id: {0}] [transaction id: {1}] |
| [S009] FAS failed to unregister from the cloud [fas id: {0}] [transaction id: {1}] [exception: {2}] |
| [S010] The FAS service is connected to the cloud messaging URL: {0} |
| [S011] The FAS service is not connected to the cloud |
| [S012] The FAS service is available for single-sign on from Citrix Cloud |
| [S013] The FAS service is not available for single-sign on from Citrix Cloud.[{0}] Further details can be found in the admin console |
[S014] A call to the cloud service <service name> failed [fas id: {0}] [transaction id: {1}] [exception: {2}] |
| [S015] A message from Citrix Cloud was blocked because the caller is not permitted [message ID {0}] [transaction ID {1}] [caller {2}] |
[S016] A call to the cloud service <service name> succeeded [fas id: {0}] [transaction id: {1}] |
| [S019] FAS downloaded its configuration from the cloud [fas id: {0}] [transaction id: {1}] |
| [S020] FAS failed to download its configuration from the cloud [fas id: {0}] [transaction id: {1}] [exception: {2}] |
| [S021] The FAS cloud service failed to start. Exception: {0} |
| [S022] The FAS cloud service is stopping |
Log on [VDA]
[事件来源:Citrix.Authentication.IdentityAssertion]
在登录阶段会在 VDA 上记录这些事件。
| 日志代码 |
|---|
| [S101] Identity Assertion Logon failed. Unrecognised Federated Authentication Service [id: {0}] |
| [S102] Identity Assertion Logon failed. Could not lookup SID for {0} [Exception: {1}{2}] |
| [S103] Identity Assertion Logon failed. User {0} has SID {1}, expected SID {2} |
| [S104] Identity Assertion Logon failed. Failed to connect to Federated Authentication Service: {0} [Error: {1} {2}] |
| [S105] Identity Assertion Logon. Logging in [Username: {0}][Domain: {1}] |
| [S106] Identity Assertion Logon. Logging in [Certificate: {0}] |
| [S107] Identity Assertion Logon failed. [Exception: {0}{1}] |
| [S108] Identity Assertion Subsystem. ACCESS_DENIED [Caller: {0}] |
In-session certificates [VDA]
[事件来源:Citrix.Authentication.IdentityAssertion]
当用户尝试使用会话中证书时,会在 VDA 上记录这些事件。
| 日志代码 |
|---|
| [S201] Virtual smart card access authorized by [{0}] for [PID: {1} Program Name: {2}][Certificate thumbprint: {3}] |
| [S203] Virtual Smart Card Subsystem. Access Denied [caller: {0}, session {1}] |
| [S204] Virtual Smart Card Subsystem. Smart card support disabled |
证书请求和密钥对生成 [联合身份验证服务]
[事件来源:Citrix.Fas.PkiCore]
当 FAS 服务器执行日志级别的加密操作时,会记录这些事件。
| 日志代码 |
|---|
| [S001] TrustArea::TrustArea: Installed certificate [TrustArea: {0}] [Certificate {1}][TrustAreaJoinParameters{2} |
| [S014] Pkcs10Request::Create: Created PKCS10 request [Distinguished Name {0}] |
| [S016] PrivateKey::Create [Identifier {0}][MachineWide: {1}][Provider: {2}][ProviderType: {3}][EllipticCurve: {4}][KeyLength: {5}][isExportable: {6}] |
| [S017] PrivateKey::Delete [CspName: {0}, Identifier {1}] |
| 日志代码 |
|---|
| [S104] MicrosoftCertificateAuthority::GetCredentials: Authorized to use {0} |
| [S105] MicrosoftCertificateAuthority::SubmitCertificateRequest Error submit response [{0}] |
| [S106] MicrosoftCertificateAuthority::SubmitCertificateRequest Issued certificate [{0}] |
| [S112] MicrosoftCertificateAuthority::SubmitCertificateRequest - Waiting for approval [CR_DISP_UNDER_SUBMISSION] [Reference: {0}] |
最终用户错误消息
本节列出了在 Windows 登录页面上向用户显示的常见错误消息。
| 显示的错误消息 | 说明和参考 |
|---|---|
| 无效用户名或密码 | 计算机相信您拥有有效的证书和私钥,但 Kerberos 域控制器拒绝了连接。参阅本文的 Kerberos 登录部分。 |
| 系统无法让您登录。无法验证您的凭据。/不支持该请求 | 无法联系域控制器,或者域控制器未配置证书,无法支持智能卡身份验证。为“Kerberos 身份验证”、“域控制器身份验证”或“域控制器”证书注册域控制器。此操作通常值得一试,即使在现有证书可能有效时也是如此。 |
| 系统无法让您登录。用于身份验证的智能卡证书不可信。 | 未在本地计算机上安装中间证书和根证书。请参阅证书和公钥基础结构。 |
| 请求错误 | 这通常指示未正确设置证书上的扩展名,或者 RSA 密钥太短(小于 2048 位)。 |
相关信息
- 为智能卡登录配置域:http://support.citrix.com/article/CTX206156
- 智能卡登录策略:https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/ff404287(v=ws.10)
- 启用 CAPI 日志记录:http://social.technet.microsoft.com/wiki/contents/articles/242.troubleshooting-pki-problems-on-windows.aspx
- 启用 Kerberos 日志记录:https://support.microsoft.com/en-us/kb/262177
- 有关通过第三方证书颁发机构启用智能卡登录的指导原则:https://support.microsoft.com/en-us/kb/281245