Pass-through from Citrix Gateway
Users authenticate to Citrix Gateway and are automatically logged on when they access their stores. Pass-through from Citrix Gateway authentication is enabled by default when you first configure remote access to a store. Users can connect through Citrix Gateway to stores using Citrix Workspace app or a web browser. For more information about configuring StoreFront for Citrix Gateway, see Configure a Citrix Gateway.
StoreFront supports pass-through with the following Citrix Gateway authentication methods.
- Domain Users log on using their Active Directory username and password.
- RSA Users log on to Citrix Gateway using passcodes that are derived from tokencodes generated by security tokens combined, sometimes, with personal identification numbers. If you enable pass-through authentication by security token only, ensure that the resources you make available do not require extra or alternative forms of authentication, such as users’ Microsoft Active Directory domain credentials.
- Smart card Users log on using smart cards
- RSA + Domain Users logging on to Citrix Gateway are required to enter both their domain credentials and security token passcodes.
If on the Citrix Gateway you have disabled authentication or you have disabled single-sign-on then pass-through is not used and you must configure one of the other authentication methods.
If you configure double-source authentication to Citrix Gateway for remote users accessing stores from within Citrix Workspace app, you must create two authentication policies on Citrix Gateway. Configure RADIUS (Remote Authentication Dial-In User Service) as the primary authentication method and LDAP (Lightweight Directory Access Protocol) as the secondary method. Modify the credential index to use the secondary authentication method in the session profile so that LDAP credentials are passed to StoreFront. When you add the Citrix Gateway appliance to your StoreFront configuration, set the Logon type to Domain and security token. For more information, see http://support.citrix.com/article/CTX125364
To enable multi domain authentication through Citrix Gateway to StoreFront, set SSO Name Attribute to userPrincipalName in the Citrix Gateway LDAP authentication policy for each domain. You can require users to specify a domain on the Citrix Gateway logon page so that the appropriate LDAP policy to use can be determined. When you configure the Citrix Gateway session profiles for connections to StoreFront, do not specify a single sign-on domain. You must configure trust relationships between each of the domains. Ensure that you allow users to log on to StoreFront from any domain by not restricting access to explicitly trusted domains only.
Where supported by your Citrix Gateway deployment, you can use SmartAccess to control user access to Citrix Virtual Apps and Desktops resources based on Citrix Gateway session policies.
Enable Gateway pass-through
To enable or disable gateway pass-through authentication for a store when connecting through Workspace apps, in the Authentication Methods window tick or untick Pass-through from Citrix Gateway.
Enabling Citrix Gateway pass-through authentication for a store by default also enables it for all websites for that store. You can disable username and password authentication for a specific website on the Authentication methods tab.
Configure trusted user domains
If your Citrix Gateway is configured to use LDAP authentication, you can restrict access to specific domains.
-
In the “Manage Authentication methods” window, from the Pass-through from Citrix Gateway > Settings drop-down menu, select Configure Trusted Domains.
-
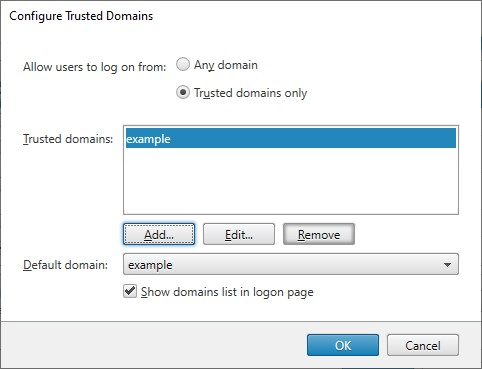
Select Trusted Domains only and click Add to enter the name of a trusted domain. Users with accounts in that domain are able to log on to all stores that use the authentication service. To modify a domain name, select the entry in the Trusted domains list and click Edit. To discontinue access to stores for user accounts in a domain, select the domain in the list and click Remove.
The way in which you specify the domain name determines the format in which users must enter their credentials. If you want users to enter their credentials in domain user name format, add the NetBIOS name to the list. To require that users to enter their credentials in user principal name format, add the fully qualified domain name to the list. If you want to enable users to enter their credentials in both domain user name format and user principal name format, you must add both the NetBIOS name and the fully qualified domain name to the list.
-
If you configure multiple trusted domains, select from the Default domain list the domain that is selected by default when users log on.
-
If you want to list the trusted domains on the logon page, select the Show domains list in the logon page check box.
Delegate credential validation to Citrix Gateway
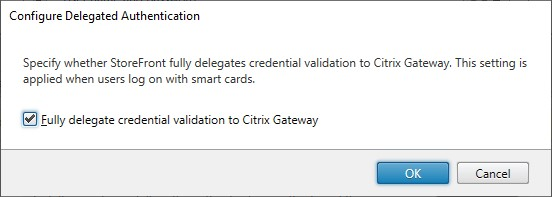
By default StoreFront validates the username and password it receives from the Gateway. If your Citrix Gateway is configured to use passwordless authentication methods such as smart card you must configure StoreFront so that it does not validate the credentials and so is reliant on the Gateway’s authentication. In this case, it is recommended that you enter a callback URL when configuring the gateway so StoreFront can verify the request came from the gateway, see Manage Citrix Gateways.
-
In the Manage Authentication Methods window, from the Pass-through from Citrix Gateway > Settings drop-down menu, select Configure Delegated Authentication.
-
Select Fully delegate credential validation to citrix gateway.
 .
.
PowerShell SDK
To configure the store to delegate authentication to the gateway using the PowerShell SDK, use cmdlet Set-STFCitrixAGBasicOptions to set CredentialValidationMode to Auto. To configure StoreFront to validate the credentials, set CredentialValidationMode to Password.
Allow users to change expired passwords at logon
If your Citrix Gateway is configured to use LDAP (username and password) authentication then you can configure NetScaler to allow changing expired passwords on log-in.
- Log into the NetScaler administration website
- On the side menu go to Authentication > Dashboard.
- Click the authentication server.
- Under Other Settings tick Allow Password Change.
Allow users to change passwords after logon
With Pass-through from Citrix Gateway, the Citrix Gateway is responsible for handling authentication. You can configure StoreFront to allow users to change their passwords after logging on. This functionality is only available when accessing StoreFront stores through Citrix Workspace app for HTML5, not locally installed Citrix Workspace apps.
The default StoreFront configuration prevents users from changing their passwords, even if the passwords have expired. If you decide to enable this feature, ensure that the policies for the domains containing your servers do not prevent users from changing their passwords. Enabling users to change their passwords exposes sensitive security functions to anyone who can access any of the stores that use the authentication service. If your organization has a security policy that reserves user password change functions for internal use only, ensure that none of the stores are accessible from outside your corporate network.
-
In the Manage Authentication Methods window, from the Pass-through from Citrix Gateway > Settings drop-down menu, select Manage Password Options
-
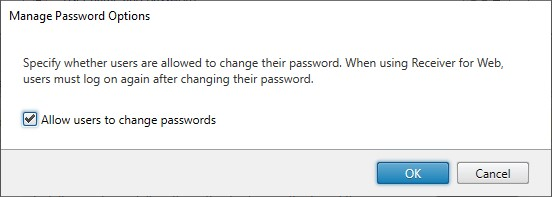
To allow users to change passwords, select Allow users to change passwords check box.
Note:
If you select or clear Allow users to change passwords, this also affects settings under Manage Password Options for Username and password authentication.
PowerShell SDK
To modify change password options using the PowerShell SDK, use cmdlet Set-STFExplicitCommonOptions.
Configure Delivery Controller to trust StoreFront
When the Citrix Gateway is configured with LDAP authentication, it passes the credentials through to StoreFront. For other authentication methods, StoreFront does not have access to the credentials so is unable to authenticate to Citrix Virtual Apps and Desktops. You must therefore configure the Delivery Controller to trust requests from StoreFront, see Citrix Virtual Apps and Desktops Security considerations and best practices.
Single sign-on to VDAs using Federated Authentication Service
When the gateway is configured with LDAP authentication, it passes the credentials through to StoreFront so that it can single sign-on to VDAs. For other authentication methods, StoreFront does not have access to the credentials so single sign-on is not available by default. You can use Federated Authentication Service to provide single sign on.
In this article
- Enable Gateway pass-through
- Configure trusted user domains
- Delegate credential validation to Citrix Gateway
- Allow users to change expired passwords at logon
- Allow users to change passwords after logon
- Configure Delivery Controller to trust StoreFront
- Single sign-on to VDAs using Federated Authentication Service