Citrix Secure Web Gateway 12.1
Web traffic has increased exponentially in recent years, and corporations are increasingly relying on the internet for their day to day operations. That, combined with the emergence of more diverse endpoints, mobility, and BYOD, along with a growing attacker base, is making users easy targets of modern malware. They are increasingly vulnerable to identity theft and having their data compromised. Traditionally, enterprises have inspected HTTP traffic for malware and viruses. They bypassed HTTPS/TLS traffic, because it was not as prominent. It was used sparingly for content that was sensitive and trusted. But that has changed rapidly as most public internet websites now prefer to use HTTPS to protect user privacy. As a result, the inability to inspect encrypted packets allows malware or intrusions into the enterprise network. The Citrix Secure Web Gateway (SWG) solution offers tools that enterprises can use to protect against internet threats.
Citrix Secure Web Gateway as a proxy
A proxy is a server that controls all the traffic between users and the Internet or SaaS applications. Since all the traffic passes through this proxy, it performs security-related functions, such as user authentication and URL categorization.
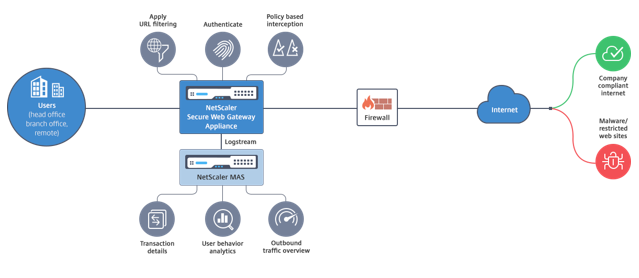
The following figure is an overview of the Citrix SWG implementation. Traffic flows through the enterprise network from the head office, branch offices, data center, and remote employees. A Citrix ADC appliance at the edge of the network acts a proxy. The appliance can operate in transparent proxy mode or explicit proxy mode and offers controls to intercept internet traffic, including HTTPS. Policies configured on the appliance determine whether it intercepts, bypasses, or blocks a particular request. Access to restricted sites can be blocked by using URL filtering. A user is authenticated before logging on to the enterprise network. All requests and responses are tagged to identify the user, and internet-site access is categorized. User activity is logged and used to generate reports. If a breach occurs, administrators can isolate the infected system, determine whether the devices of any other users who visited that website are compromised, and take appropriate action. When you integrate Citrix Application Delivery Management (ADM) with a Citrix SWG appliance, the logged user activity and the subsequent records in the appliance are exported to Citrix ADM by using logstream. Citrix ADM collates and presents information about the activities of users, from websites visited to the time spent online. It also provides information about bandwidth use and detected threats, such as malware and phishing sites. You can use these key metrics to monitor your network, and use the Citrix SWG appliance to take corrective actions.
Citrix SWG enables IT directors to do the following:
- Gain visibility into the otherwise bypassed secure traffic.
- Block access to malicious or unknown sites and avoid infecting users within the enterprise.
- Control access to some websites, such as personal mail, social networking, and job search websites, from the enterprise network.
- Apply intelligent content control policies to ensure maximum user productivity.