Secure
To secure the communication between your server farm and Citrix Workspace app, integrate your connections to the server farm with a range of security technologies, including Citrix Gateway.
Note:
Citrix recommends using Citrix Gateway to secure communications between StoreFront servers and users’ devices.
-
A SOCKS proxy server or secure proxy server (also known as security proxy server, HTTPS proxy server).
You can use proxy servers to limit access to and from your network and to handle connections between Citrix Workspace app and servers. Citrix Workspace app supports SOCKS and secure proxy protocols.
-
Secure Web Gateway.
You can use Secure Web Gateway with Web Interface to provide a single, secure, and encrypted point of access through the Internet to servers on internal corporate networks.
You can use Secure Web Gateway with Web Interface to provide single, secure, and encrypted data. The servers on internal corporate networks can access the secured data through the Internet.
-
SSL Relay solutions with Transport Layer Security (TLS) protocols.
-
A firewall.
Network firewalls can allow or block packets based on the destination address and port.
If you’re using Citrix Workspace app through a network firewall that maps the server’s internal network IP address to an external Internet address (that is, network address translation, or NAT), configure the external address.
Support for multi-site store failover based on geo-location
Starting with version 24.12.0, the multi-store failover handling feature improves multi-store failover handling by running store address checks asynchronously and removing outdated store entries when a new failover store address is detected. When a failover occurs due to an outage, the Global Server Load Balancer (GSLB) redirects the client to a new site. This feature ensures that, when launching a previously added store, the Gateway detector checks if the store address has changed based on the user’s geo-location. If a new address is found, the client automatically removes the old store entry and adds the new one. This process runs in the background, allowing for a seamless transition to the new store without manual intervention. Note that this feature applies only to on-premises stores.
Prerequisite:
The user must log in to the store.
Limitation:
If the log-in session cookie expires, the multi-store failover does not happen automatically because the API for fetching the URL fails. In this case, the login page is prompted.
Support for WSUI on-premises using gateway
Starting with version 24.12.0, Citrix Workspace app for iOS supports Web UI for the on-premises store which is behind the gateway as well. The administrator must configure this feature, as it is not enabled by default. For more information on configuration, see New UI for on-premises stores (Technical Preview).
The following image show the current UI:
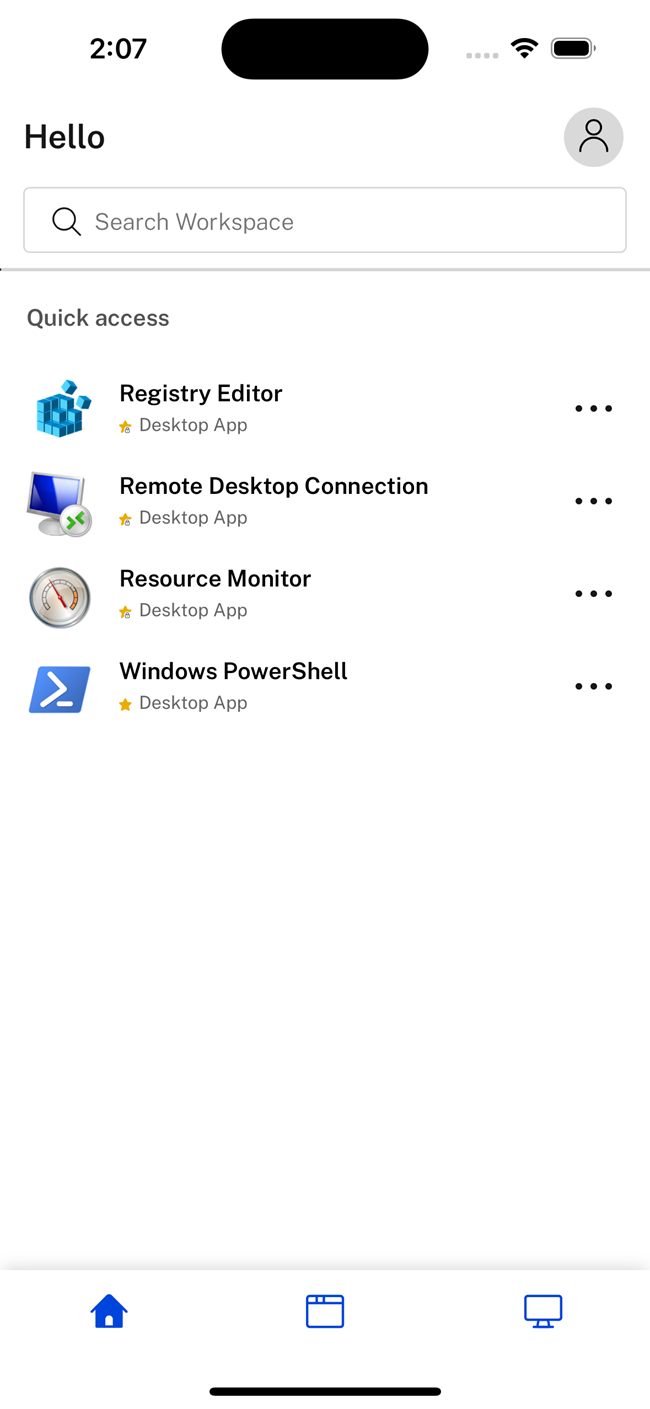
The following image show the new UI:
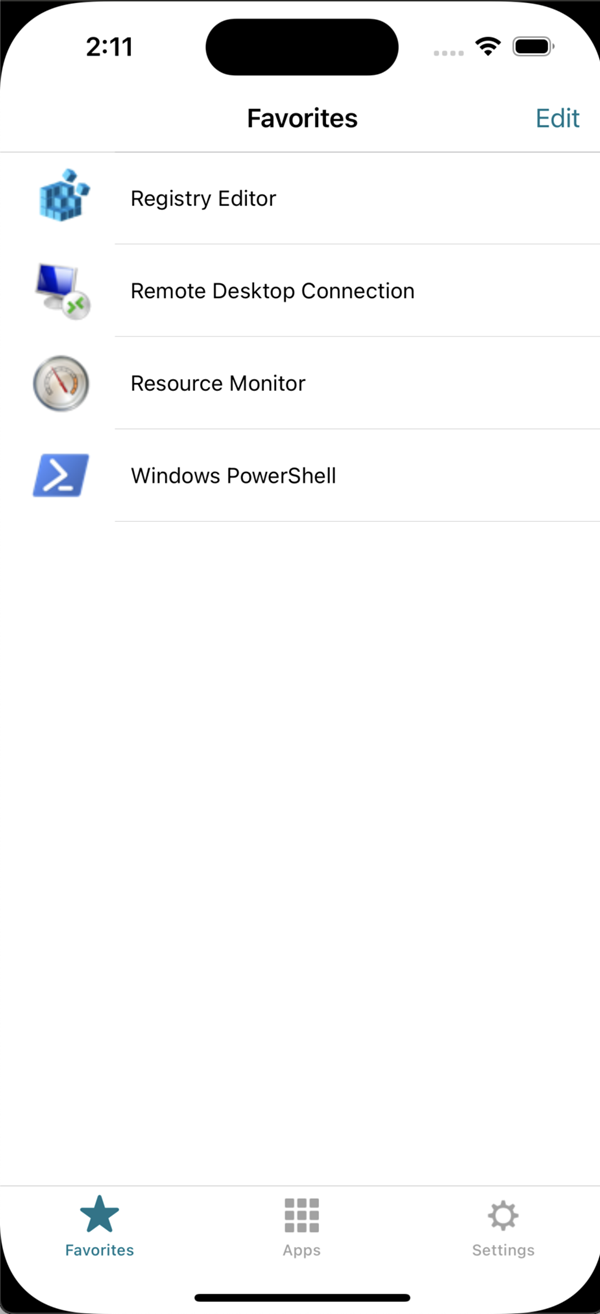
Citrix Gateway
To enable remote users to connect to your Citrix Endpoint Management deployment through Citrix Gateway, you can configure certificates to work with StoreFront. The method for enabling access depends on the edition of Citrix Endpoint Management in your deployment.
If you deploy Citrix Endpoint Management in your network, allow connections from internal or remote users to StoreFront through Citrix Gateway by integrating Citrix Gateway with StoreFront. This deployment allows users to connect to StoreFront to access published applications from XenApp and virtual desktops from XenDesktop. Users connect through Citrix Workspace app.
Secure Web Gateway
This topic applies only to deployments using the Web Interface.
You can use the Secure Web Gateway in either Normal mode or Relay mode to provide a secure channel for communication between Citrix Workspace app and the server. If you’re using the Secure Web Gateway in Normal mode, Citrix Workspace app doesn’t require any configuration. Verify that end users are connecting through the Web Interface.
Citrix Workspace app uses settings that are configured remotely on the Web Interface server to connect to servers running the Secure Web Gateway.
If the Secure Web Gateway Proxy is installed on a server in the secure network, you can use the Secure Web Gateway Proxy in Relay mode. If you’re using Relay mode, the Secure Web Gateway server functions as a proxy and you must configure Citrix Workspace app to use:
- The fully qualified domain name (FQDN) of the Secure Web Gateway server.
- The port number of the Secure Web Gateway server.
Note:
Secure Web Gateway Version 2.0 doesn’t support Relay mode.
The FQDN must list, in sequence, the following three components:
- Host name
- Intermediate domain
- Top-level domain
For example, my_computer.example.com is an FQDN, because it lists, in sequence, a host name (my_computer), an intermediate domain (example), and a top-level domain (com). The combination of intermediate and top-level domain (example. com) is referred to as the domain name.
Proxy server
Proxy servers are used to limit access to and from your network, and to handle connections between Citrix Workspace app and servers. Citrix Workspace app supports both SOCKS and secure proxy protocols.
Citrix Workspace app uses proxy server settings to communicate with the Citrix Virtual Apps and Desktops server. The proxy server settings are remotely configured on the Web Interface server.
When Citrix Workspace app communicates with the Web server, the app uses the proxy server settings. Configure the proxy server settings for the default web browser on the user device accordingly.
Firewall
Network firewalls can allow or block packets based on the destination address and port. If you’re using a firewall in your deployment, Citrix Workspace app must be able to communicate through the firewall with both the web server and Citrix server. The firewall must permit HTTP traffic for user device to Web server communication. Usually, the HTTP traffic is over the standard HTTP port 80 or 443 if a secure Web server is in use. For Citrix server communication, the firewall must permit inbound ICA traffic on ports 1494 and 2598.
If the firewall is configured for Network Address Translation (NAT), you can use the Web Interface to define mappings from internal addresses to external addresses and ports. For example, if your Citrix Virtual Apps and Desktops and Citrix DaaS (formerly Citrix Virtual Apps and Desktops service) server isn’t configured with an alternate address, you can configure Web Interface to provide an alternate address to Citrix Workspace app for iOS. Citrix Workspace app for iOS then connects to the server using the external address and port number.
TLS
Citrix Workspace app supports TLS 1.2 and 1.3 with the following cipher suites for TLS connections to XenApp and XenDesktop:
- TLS_RSA_WITH_AES_256_GCM_SHA384
- TLS_RSA_WITH_AES_128_GCM_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_RC4_128_SHA
- TLS_RSA_WITH_RC4_128_MD5
- TLS_RSA_WITH_3DES_EDE_CBC_SHA
Note:
Citrix Workspace app running on iOS 9 and later or version 21.2.0 does not support the following TLS cipher suites:
- TLS_RSA_WITH_RC4_128_SHA
- TLS_RSA_WITH_RC4_128_MD5
Transport Layer Security (TLS) is the latest, standardized version of the TLS protocol. The Internet Engineering Taskforce (IETF) renamed it TLS when it took over responsibility for the development of TLS as an open standard.
TLS secures data communications by providing server authentication, encryption of the data stream, and message integrity checks. Some organizations, including U.S. government organizations, require the use of TLS to secure data communications. These organizations might also require the use of validated cryptography, such as Federal Information Processing Standard (FIPS) 140. FIPS 140 is a standard for cryptography.
Citrix Workspace app supports RSA keys of 1024, 2048, and 3072-bit lengths. Root certificates with RSA keys of 4096-bit length are also supported.
Note:
- Citrix Workspace app uses iOS platform crypto for connections between Citrix Workspace app and StoreFront.
Configure and enable TLS
There are two main steps involved in setting up TLS:
- Set up SSL Relay on your Citrix Virtual Apps and Desktops™ server and your Web Interface server and obtain and install the necessary server certificate.
- Install the equivalent root certificate on the user device.
Install root certificates on user devices
To secure communications between TLS-enabled Citrix Workspace app and Citrix Virtual Apps and Desktops, you need a root certificate on the user device. The certificate can verify the signature of the Certificate Authority on the server certificate.
iOS comes with about 100 s of commercial root certificates that are preinstalled. If you want to use a different certificate, you can receive one from the Certificate Authority and install it on each user device.
Depending on your organization’s policies and procedures, you can install the root certificate on each user device instead of directing users to install it. The easiest and safest way is to add root certificates to the iOS keychain.
To add a root certificate to the keychain
- Send yourself an email with the certificate file.
- Open the certificate file on the device. This action automatically starts the Keychain Access application.
- Follow the prompts to add the certificate.
-
Starting with iOS 10, verify that the certificate is trusted by going to iOS Settings > About > Certificate Trust Setting.
Under Certificate Trust Settings, see the section “ENABLE FULL TRUST FOR ROOT CERTIFICATES.” Make sure that your certificate has been selected for full trust.
The root certificate is installed. The TLS-enabled clients and other applications can use the root certificate using TLS.
Support for Transport Layer Security 1.3
Starting with the 23.9.0, Citrix Workspace app for iOS now supports Transport Layer Security (TLS) 1.3 that boosts performance and efficiency. TLS 1.3 provides robust security with its strong cipher suites and one-time session keys.
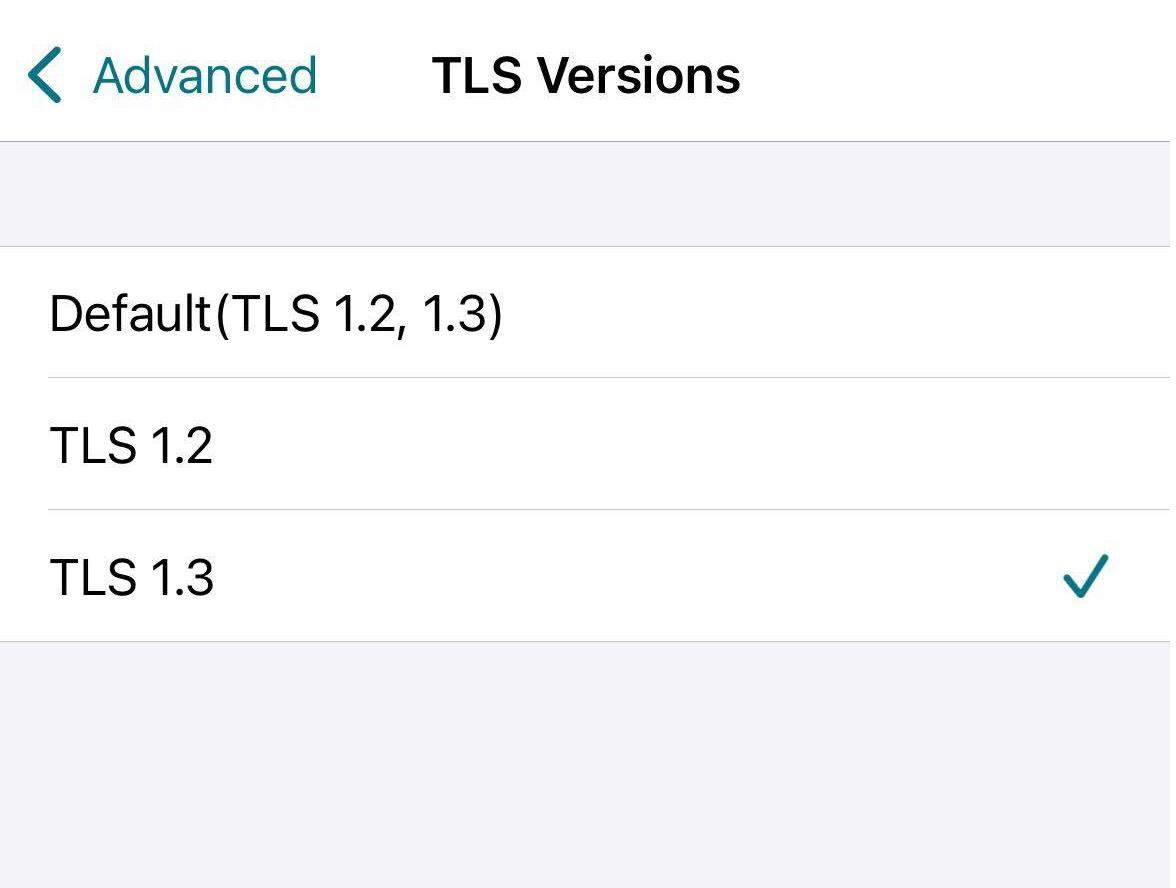
End users can enable it on Citrix Workspace app for iOS as follows.
- Go to Advanced settings > TLS Versions.
- Select TLS 1.3 version.
Support for DTLS 1.2
Starting with version 24.7.0, Citrix Workspace app for iOS supports DTLS protocol version 1.2. DTLS 1.2 provides enhancements and improvements over the previous version, which includes robust encryption algorithms, better handshake protocols, and protection against various attacks. This protocol improves overall security.
Note:
If there is any issue with DTLS protocol version 1.2, Citrix Workspace app for iOS seamlessly falls back to the previous supported versions.
Support for Citrix Device Posture service
Starting with the 2402 version, Citrix Workspace™ app for iOS supports Citrix Device Posture service. Citrix Device Posture service is a cloud-based solution that helps administrators enforce certain requirements that end devices must meet to gain access to Citrix DaaS (virtual apps and desktops) or Citrix Secure Private Access™ resources.
For Citrix Workspace app for iOS, the device posture supports only the scan of the Citrix Workspace app version and operating system version of the iOS device.
For more information, see the Device Posture documentation.
Note
This feature is supported only for cloud stores.
XenApp and XenDesktop® Site
To configure the XenApp® and XenDesktop Site:
Important:
- Citrix Workspace app uses XenApp and XenDesktop Sites, which support Citrix Secure Gateway 3.x.
- Citrix Workspace app uses Citrix Virtual Apps websites, which support Citrix Secure Gateway 3.x.
- XenApp and XenDesktop Sites supports only single-factor authentication.
- Citrix Virtual Apps™ websites support both single-factor and dual-factor authentication.
- All the built-in browsers support Web Interface 5.4.
Before beginning this configuration, install and configure Citrix Gateway to operate with Web Interface. You can adapt these instructions to fit your specific environment.
If you’re using a Citrix Secure Gateway connection, do not configure Citrix Gateway settings on Citrix Workspace app.
Citrix Workspace app uses a XenApp and XenDesktop Site to get information about the applications an end user has rights to. In the process, the information is presented to Citrix Workspace app running on your device. Similarly, you can use the Web Interface for traditional SSL-based Citrix Virtual Apps connections. For the same SSL-based connection, you can configure Citrix Gateway. XenApp and XenDesktop Sites running on the Web Interface 5.x have this configuration ability built in.
Configure the XenApp and XenDesktop Site to support connections from a Citrix Secure Gateway connection:
- In the XenApp and XenDesktop Site, select Manage secure client access > Edit secure client access settings.
- Change the Access Method to Gateway Direct.
- Enter the FQDN of the Secure Web Gateway.
- Enter the Secure Ticket Authority (STA) information.
Note:
For the Citrix Secure Gateway, Citrix recommends using the Citrix default path (//XenAppServerName/Citrix/PNAgent). The default path enables the end users to specify the FQDN of the Secure Web Gateway they’re connecting to. Don’t use the full path to the config.xml file that is on the XenApp and XenDesktop Site. For example, (//XenAppServerName/CustomPath/config.xml).
To configure the Citrix Secure Gateway
-
Use the Citrix Secure Gateway configuration wizard to configure the gateway.
The Citrix Secure Gateway supports the server in the secure network that hosts the XenApp Service site.
After selecting the Indirect option, enter the FQDN path of your Secure Web Gateway Server and continue the wizard steps.
-
Test a connection from a user device to verify that the Secure Web Gateway is configured correctly for networking and certificate allocation.
To configure the mobile device
- When adding a Citrix Secure Gateway account, enter the matching FQDN of your Citrix Secure Gateway server in the Address field:
- If you’ve created the XenApp and XenDesktop Site using the default path (/Citrix/PNAgent), enter the Secure Web Gateway FQDN: FQDNofSecureGateway.companyName.com
- If you’ve customized the path of the XenApp and XenDesktop Site, enter the full path of the config.xml file, such as: FQDNofSecureGateway.companyName.com/CustomPath/config.xml
- If you’re manually configuring the account, then clear the Citrix Gateway option New Account dialog.