Security and network configuration
Federated Authentication Service (FAS) is tightly integrated with Microsoft Active Directory and the Microsoft certification authority. Ensure that the system is managed and secured appropriately, developing a security policy as you would for a domain controller or other critical infrastructure.
This document provides an overview of security issues to consider when deploying FAS. It also provides an overview of features available that might assist in securing your infrastructure.
Network architecture and security
The following diagram shows the main components and security boundaries used in a FAS deployment.
The FAS server is part of the security-critical infrastructure, along with the certificate authority and domain controller. In a federated environment, Citrix Gateway and Citrix StoreFront are components that perform user authentication. Other Citrix Virtual Apps and Desktops™ components are unaffected by introducing FAS.
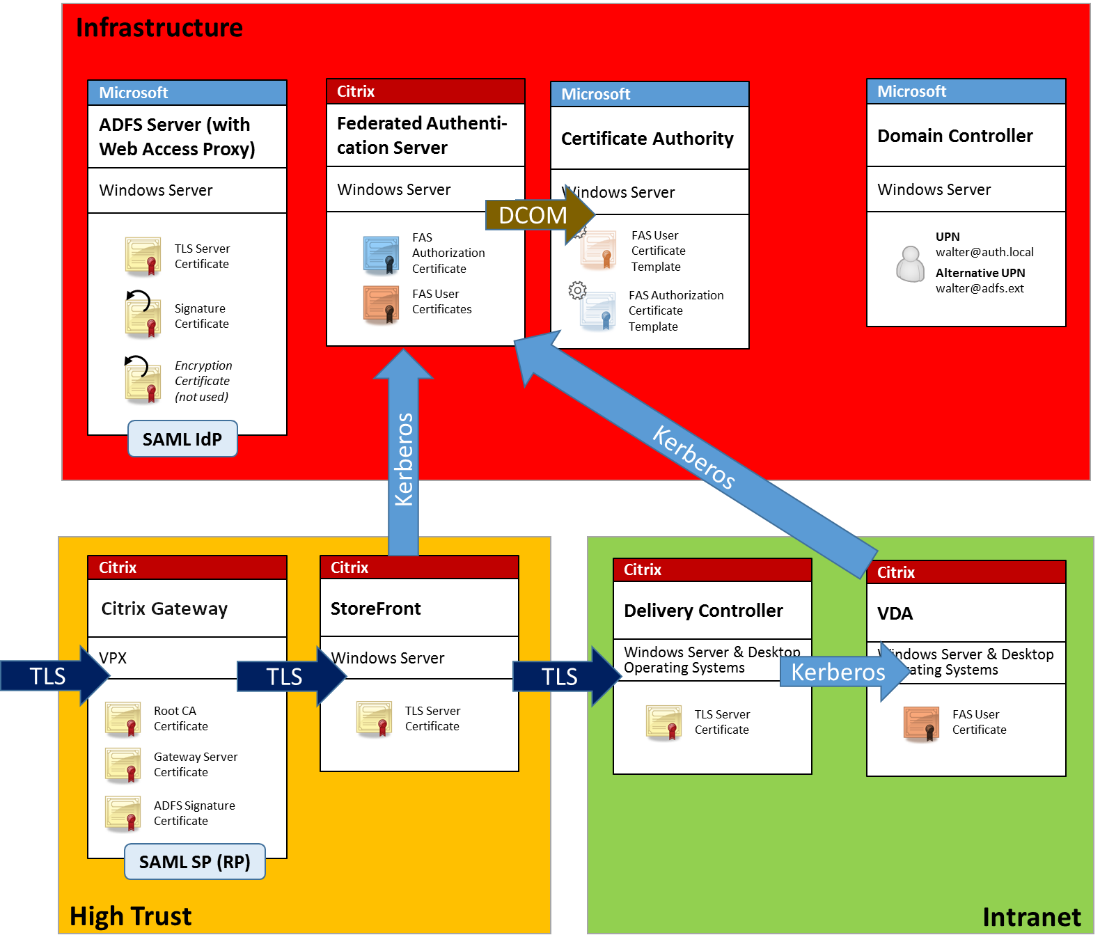
| Server | Connections |
|---|---|
| Federated Authentication Service | [in] HTTP with Kerberos security from StoreFront™ and VDAs, [out] DCOM to Microsoft certificate authority |
| Citrix Gateway | [in] HTTPS from client machines, [in/out] HTTPS to/from StoreFront server, [out] HDX to VDA |
| StoreFront | [in] HTTPS from Citrix Gateway, [out] HTTPS to Delivery Controller™, [out] HTTP with kerberos security to FAS |
| Delivery Controller | [in] HTTPS from StoreFront server, [in/out] HTTP with kerberos security from VDAs |
| VDA | [in/out] HTTP with Kerberos security from Delivery Controller, [in] HDX from Citrix Gateway, [out] HTTP with Kerberos security to FAS |
| Microsoft certificate authority | [in] DCOM from FAS |
Communication between StoreFront and FAS
-
When launching a VDA, the StoreFront server contacts the FAS server to get a single-use ticket which is needed by the Citrix Virtual Delivery Agent (VDA) to sign in the user.
-
StoreFront connects to FAS using SOAP over HTTP. By default it uses port 80.
-
It authenticates using mutual Kerberos with the Kerberos HOST/fqdn identity of the FAS server, and the Kerberos machine account identity of the StoreFront server.
-
Data is encrypted by using message level security. No additional configuration is required to enable encryption.
Communication between VDA and FAS
When an HDX™ session is connected to the VDA, the VDA contacts the FAS server to request a certificate.
-
The VDA connects to the FAS server using SOAP over HTTP. By default it uses port 80.
-
It authenticates using mutual Kerberos with the Kerberos HOST/fqdn identity of the FAS server, and the Kerberos machine identity of the VDA. Also, the VDA must supply the “credential handle” to access the certificate and private key.
-
Data is encrypted by using message level security. No additional configuration is required to enable encryption.
Communication between FAS and Microsoft certificate authority
When a user launches a VDA, if the FAS server does not already have a certificate for the user, then it communicates with the certificate authority to request a certificate. The certificate authority requires the FAS server to supply a CMC packet signed by a trusted enrollment agent certificate.
-
The FAS server communicates with the Microsoft certificate authority using DCOM. For information on required ports, see Microsoft documentation.
-
It authenticates using Kerberos.
Connections between Citrix Federated Authentication Service and Citrix Cloud™
If you are connecting FAS to Citrix Cloud, then your FAS servers must be able to access the following addresses over HTTPS port 443.
Citrix Cloud:
- FAS administration console that runs under the user’s account
*.cloud.com*.citrixworkspacesapi.net- Addresses required by a third-party identity provider, if one is used in your environment
- FAS service that runs under the Network Service account:
*.citrixworkspacesapi.net*.citrixnetworkapi.net
Citrix Cloud Japan:
- FAS administration console, under the user’s account
*.citrixcloud.jp*.citrixworkspacesapi.jp- Addresses required by a third party identity provider, if one is used in your environment
- FAS service, under the Network Service account:
*.citrixworkspacesapi.jp*.citrixnetworkapi.jp
If your environment includes proxy servers, configure the user proxy with the addresses for the FAS administration console. Also, ensure that the address for the Network Service account is configured using netsh or a similar tool.
Further information
For information on securing communication between other Citrix components, see the following articles:
- Citrix Virtual Apps and Desktops - Security considerations and best practices.
- Secure your StoreFront deployment.
Security considerations
FAS has a registration authority certificate that allows it to issue certificates autonomously for your domain users. It helps in developing and implementing a security policy to protect FAS servers, and to constrain their permissions.
Delegated enrollment agents
FAS issues user certificates by acting as an enrollment agent. The Microsoft Certification Authority allows you to restrict enrollment agents, certificate templates, and users for whom the enrollment agents can issue certificates for.
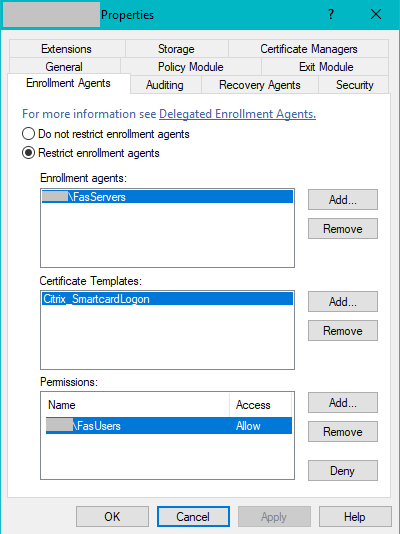
You can use the given dialog to ensure that:
- The Enrollment agents list contains only FAS servers (assuming that there are no other enrollment agents required in your Active Directory deployment).
- The Certificate Templates list contains only the FAS templates used to issue user certificates. By default this is the
Citrix_SmartcardLogontemplate. - The Permissions list contains users who are permitted to use FAS. For example, it is recommended not to issue certificates to Administrators or Protected Users group.
Note:
Any changes to the Active Directory group membership of a computer account do not take effect until the computer is rebooted.
Access Control List configuration
As described in the Configure rules section, you must configure a list of StoreFront servers. These StoreFront servers assert user identities to FAS when certificates are issued. Similarly, you can restrict which users are issued certificates, and which VDA machines they can authenticate to. This feature is in addition to any standard Active Directory or certificate authority security features you configure.
Firewall settings
The FAS server must accept incoming connections from StoreFront and VDAs, using port 80 unless otherwise configured. For more information on network communication, see Network architecture and security.
The FAS installer can optionally configure the Windows firewall. For more information, see FAS installer options.
Change FAS server port
The FAS server uses port 80 by default. You can customize the port:
Note:
You can change the FAS server port to port 443, but it doesn’t change the protocol used by FAS. FAS doesn’t use HTTPS even if configured on port 443.
-
Run the following command line on your FAS server:
"C:\Program Files\Citrix\Federated Authentication Service\Citrix.Authentication.FederatedAuthenticationService.exe" /SVCPORT [port] /CONFIGUREFIREWALL <!--NeedCopy-->Replacing
[port]with the port number you wish to use.The
/CONFIGUREFIREWALLswitch causes it to update the Windows firewall to allow incoming connections on the specified port. -
Restart the FAS service.
-
In your FAS group policy object, update the list of FAS servers to include the port (e.g.
fas.example.com:[port]). -
Propagate the change to the FAS server, StoreFront and the VDA (e.g. using
gpupdate /force)
Event log monitoring
FAS and the VDA write information to the Windows Event Log. This log can be used for monitoring and auditing information. The Event logs section lists event log entries that can be generated.
Hardware security modules
All private keys, including user certificate keys issued by FAS are stored as non-exportable private keys by the Network Service account. FAS supports the use of a cryptographic hardware security module, if your security policy requires it.
Low-level cryptographic configuration is available using the PowerShell commands. Different settings can be used for FAS authorization certificate private keys and user certificate keys. For more details, see Private key protection
Administration responsibilities
Administration of the environment can be divided into the following groups:
| Name | Responsibility |
|---|---|
| Enterprise administrator | Install and secure certificate templates in the forest |
| Domain administrator | Configure Group Policy settings |
| Certificate authority administrator | Configure the certificate authority |
| FAS administrator | Install and configure the FAS server |
| StoreFront/Citrix Gateway administrator | Configure user authentication |
| Citrix Virtual Desktops™ administrator | Configure VDAs and Controllers |
Each administrator controls different aspects of the overall security model, allowing a defense-in-depth approach to securing the system.
Group Policy settings
Note:
If all your FAS servers and VDAs are version 2511 or later, the Group Policy FQDN list on the VDA is no longer needed. See FAS V2 ticketing and the registry address list.
Trusted FAS machines are identified by a lookup table of “index number -> FQDN” configured through Group Policy. When contacting a FAS server, clients verify the FAS server’s HOST\<fqdn> Kerberos identity. All servers that access the FAS server must have identical FQDN configurations for the same index; otherwise, StoreFront and VDAs can contact different FAS servers. Additionally, if the FAS server is connected to Citrix Cloud, the Group Policy must also be applied to the FAS server itself.
Citrix recommends applying a single policy to all machines in the environment to avoid misconfiguration. Take care when modifying the list of FAS servers, especially when removing or reordering entries.
Control of this GPO must be limited to FAS administrators (and/or domain administrators) who install and decommission FAS servers. Take care to avoid reusing a machine FQDN name shortly after decommissioning a FAS server.
FAS Group Policy settings appear in the registry at HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Citrix\Authentication. The list of FAS FQDNs from the Group Policy appears at the subkey HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Citrix\Authentication\UserCredentialService\Addresses.
Certificate templates
If you do not want to use the Citrix_SmartcardLogon certificate template supplied with FAS, you can modify a copy of it. The following modifications are supported.
Rename a certificate template
If you want to rename the Citrix_SmartcardLogon to match your organizational template naming standard, you must:
- Create a copy of the certificate template and rename it to match your organizational template naming standard.
- Use FAS PowerShell commands to administer FAS, rather than the administrative user interface. (The administrative user interface is only intended for use with the Citrix default template names.)
- Either use the Microsoft MMC Certificate Templates snap-in or the Publish-FasMsTemplate command to publish your template, and
- Use the New-FasCertificateDefinition command to configure FAS with the name of your template.
Modify General properties
By default, the lifespan of a user certificate is seven days. You can modify the validity period in the certificate template.
Do not modify the Renewal period. FAS ignores this setting in the certificate template. FAS automatically renews the certificate halfway through its validity period.
Modify Request Handling properties
Do not modify these properties. FAS ignores these settings in the certificate template.
See Private key protection for the settings that FAS provides.
Modify Cryptography properties
Do not modify these properties. FAS ignores these settings in the certificate template.
Refer to Private key protection for equivalent settings that FAS provides.
Modify Key Attestation properties
Do not modify these properties. FAS does not support key attestation.
Modify Superseded Templates properties
Do not modify these properties. FAS does not support superseding templates.
Modify Extensions properties
You can modify these settings to match your organizational policy.
Note:
Inappropriate Extension settings can cause security issues, or result in unusable certificates.
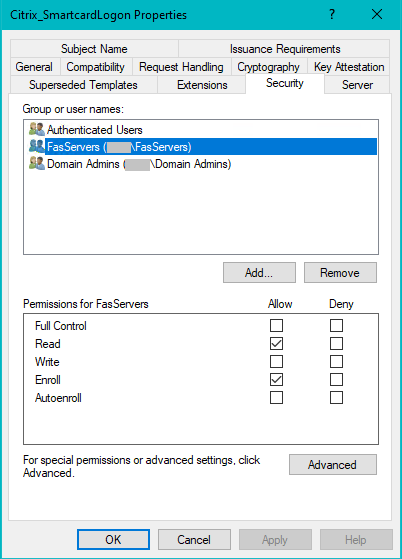
Modify Security properties
Citrix recommends that you modify these settings to allow the Read and Enroll permissions for only the machine accounts of the FAS servers. The FAS service does not require any other permissions.
Additionally:
- allow Authenticated Users to Read the template. This is necessary, because the Certificate Authorities themselves need to be able to read the template.
- allow your Certificate Authority administrators to Read and Write the template.
The recommendation applies to all three FAS templates:
Citrix_SmartcardLogonCitrix_RegistrationAuthorityCitrix_RegistrationAuthority_ManualAuthorization
Note:
Any changes to the Active Directory group membership of a computer account do not take effect until the computer is rebooted.
Modify Subject Name properties
Citrix recommends that you don’t modify these properties.
The template has Build from this Active Directory information selected, causing the certificate authority to include the user’s SID in a certificate extension, which provides a strong mapping to the user’s Active Directory account.
Modify Server properties
Although Citrix does not recommend it, you can modify these settings to match your organizational policy, if needed.
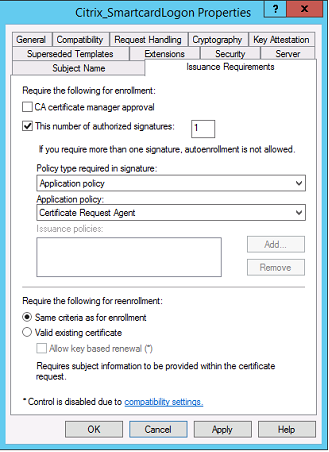
Modify Issuance requirements properties
Do not modify these settings. These settings must be as shown:
Modify Compatibility properties
You can modify these settings. The setting must be at least Windows Server 2003 CAs (schema version 2). However, FAS supports only Windows Server 2008 and later CAs. Also, as explained above, FAS ignores the additional settings available by selecting Windows Server 2008 CAs (schema version 3) or Windows Server 2012 CAs (schema version 4).
Certificate authority administration
The certificate authority administrator is responsible for the configuration of the certificate authority server and the issuing certificate private key that it uses.
Publishing templates
For a certificate authority to issue certificates based on a template supplied by the enterprise administrator, the certificate authority administrator must choose to publish that template.
A simple security practice is to publish only the registration authority certificate templates when FAS servers are being installed, or to insist on a completely offline issuance process. In either case, the certificate authority administrator must maintain complete control over authorizing registration authority certificate requests, and have a policy for authorizing FAS servers.
Firewall settings
The certificate authority administrator has the control of the network firewall settings of the certificate authority, allowing control over incoming connections. The certificate authority administrator can configure DCOM TCP and firewall rules so that only FAS servers can request certificates.
Restricted enrollment
By default any holder of a registration authority certificate can issue certificates to any user, using any certificate template that allows access. Citrix recommends that issuance of certificates is restricted to a group of non-privileged users using the Restrict enrollment agents certificate authority property. See Delegated enrollment agents.
Policy modules and auditing
For advanced deployments, custom security modules can be used to track and veto certificate issuance.
FAS administration
FAS has several security features.
Restrict StoreFront, users, and VDAs through an ACL
At the center of the FAS security model is the control for which Kerberos accounts can access functionality:
| Access Vector | Description |
|---|---|
| StoreFront [IdP] | These Kerberos accounts are trusted to declare that a user has been correctly authenticated. If one of these accounts is compromised, then certificates can be created and used for users allowed by the configuration of FAS. |
| VDAs [Relying party] | These are the machines that are allowed to access the certificates and private keys. A credential handle retrieved by the IdP is also needed, so a compromised VDA account in this group has limited scope to attack the system. |
| Users | This option controls which users can be asserted by the IdP. Note that there is overlap with the “Restricted Enrollment Agent” configuration options at the certificate authority. In general, it is advisable to include only non-privileged accounts in this list. This prevents a compromised StoreFront account from escalating privileges to a higher administrative level. In particular, domain administrator accounts must not be allowed by this ACL. |
Configure rules
Rules are useful if multiple independent Citrix Virtual Apps™ or Citrix Virtual Desktops deployments use the same FAS server infrastructure. Each rule has a separate set of configuration options; in particular, the Kerberos access control lists (ACLs) can be configured independently.
Configure the certificate authority and templates
Different certificate templates and CAs can be configured for different access rights. Advanced configurations can choose to use less or more powerful certificates, depending on the environment. For example, users identified as “external” can have a certificate with fewer privileges than “internal” users.
In-session and authentication certificates
The FAS administrator can control whether the certificate used to authenticate is available for use in the user’s session. For example, a user can have only “signing” certificates available in-session, with the more powerful “logon” certificate used only at logon.
Private key protection and key length
The FAS administrator can configure FAS to store private keys in a Hardware Security Module (HSM) or Trusted Platform Module (TPM). Citrix recommends that at least the FAS authorization certificate private key is protected by storing it in a TPM.
Similarly, user certificate private keys can be stored in a TPM or HSM. All keys must be generated as non-exportable and be at least 2048 bits in length if RSA is used.
Note:
Although FAS can generate and store user certificate keys in a TPM or HSM, the hardware may be too slow or size constained for large deployments.
For more details, see Private key protection.
Event logs
The FAS server provides detailed configuration and runtime event logs, which can be used for auditing and intrusion detection.
Administrative access and administration tools
FAS includes remote administration features (mutually authenticated Kerberos) and tools. Members of the “Local Administrators Group” have full control over FAS configuration. FAS configuration must be properly maintained.
Citrix Virtual Apps, Citrix Virtual Desktops, and VDA administrators
The use of FAS does not change the security model of the Delivery Controller and VDA administrators, as the FAS “credential handle” simply replaces the “Active Directory password.” Controller and VDA administration groups must contain only trusted users. Auditing and event logs must be maintained.
General Windows server security
All servers must be fully patched and have standard firewall and antivirus software available. Security-critical infrastructure servers must be kept in a physically secure location, with care taken over disk encryption and virtual machine maintenance options.
Auditing and event logs must be stored securely on a remote machine.
RDP access must be limited to authorized administrators. Citrix recommends smart card logon for user accounts, especially for certificate authority and domain administrator accounts.
Federal Information Processing Standard (FIPS) support
FAS uses the FIPS-validated cryptographic algorithms on FIPS-enabled Windows computers. If you configure FAS to use a TPM or HSM for key storage, consult your hardware vendor for FIPS compliance information.
Related information
- Install and configure is the primary reference for FAS installation and configuration.
- FAS architectures are introduced in the Deployment architectures article.
- Other “how-to” articles are introduced in the Advanced configuration article.
In this article
- Network architecture and security
- Security considerations
- Administration responsibilities
- Group Policy settings
- Certificate templates
- Certificate authority administration
- FAS administration
- Citrix Virtual Apps, Citrix Virtual Desktops, and VDA administrators
- General Windows server security
- Federal Information Processing Standard (FIPS) support
- Related information