This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Configuring Alerts
Splunk has a powerful alerting system that can be used to send emails or run arbitrary commands whenever a specific condition is met, as defined in a Splunk search.
In this walkthrough, we demonstrate how to alert when the duration of user logons exceeds a certain threshold.
Defining the Condition
An easy way to find the right Splunk search for defining the alert condition is to use an element already present on one of uberAgent’s dashboards. In this example, we are interested in logon duration which is displayed on the User Logon Duration dashboard.
Navigate to the table near the bottom and click the button with the little lens symbol on it:
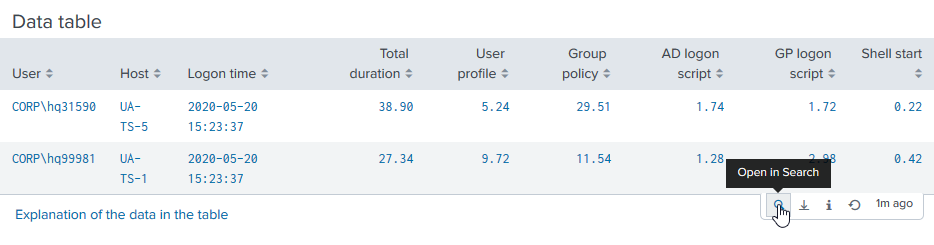
This opens the search in another window. At this stage you can add a condition (highlighted below) to filter for specific events:
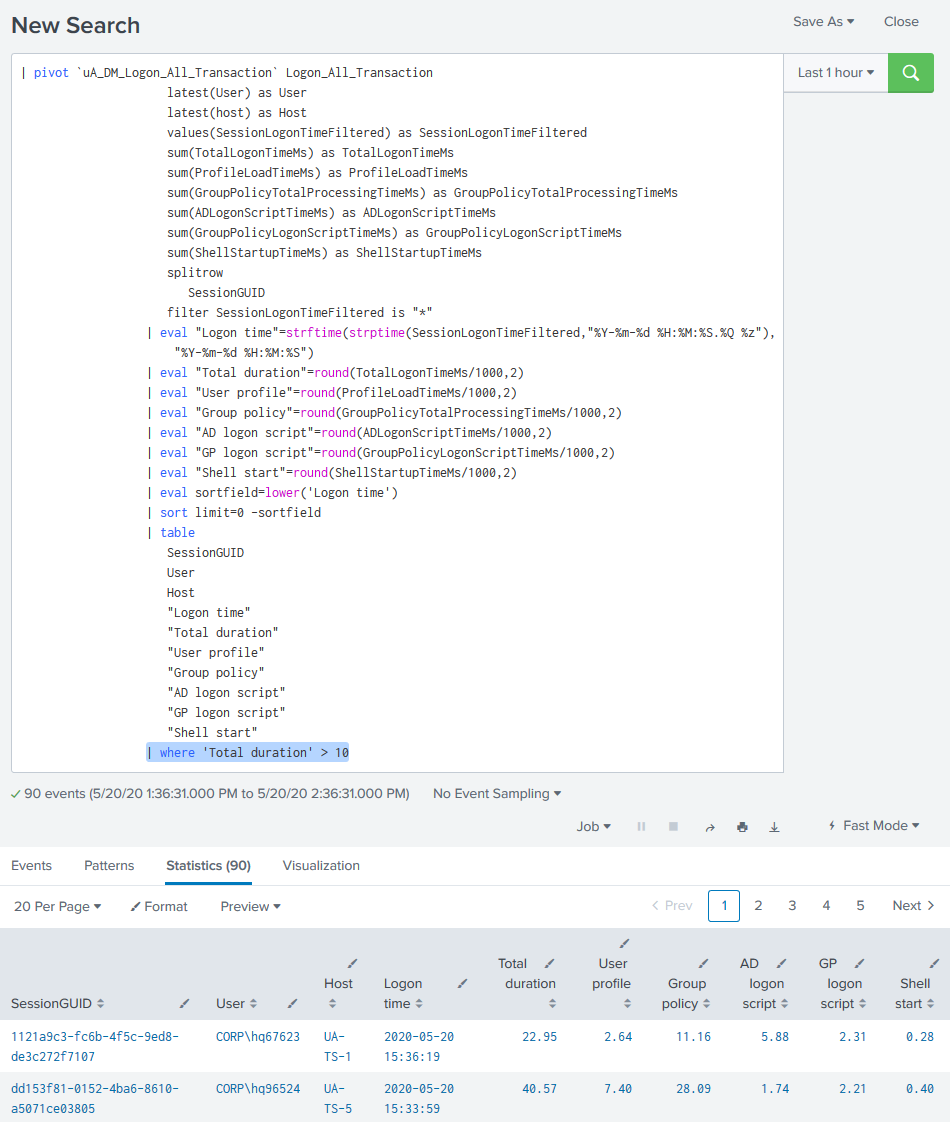
Setting up the Alert
Once you are happy with the results returned from your conditional search, copy the search string.
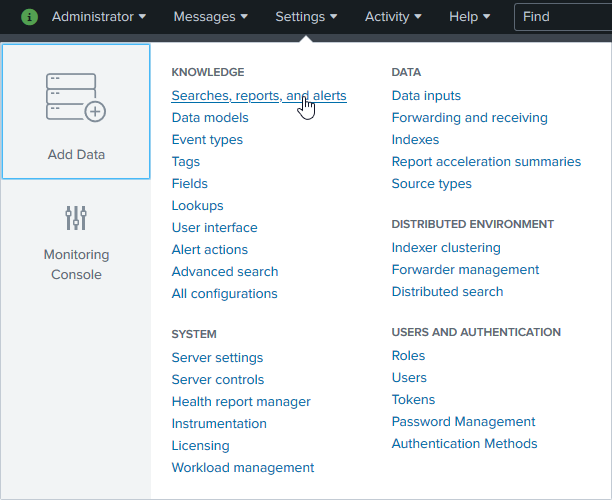
Click Settings > Searches, reports and alerts:
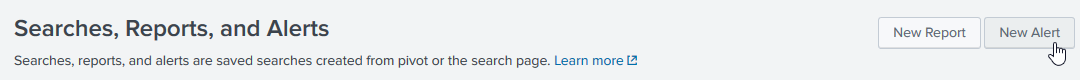
Click New Alert:
Configure the alert as shown in the following very large screenshot:
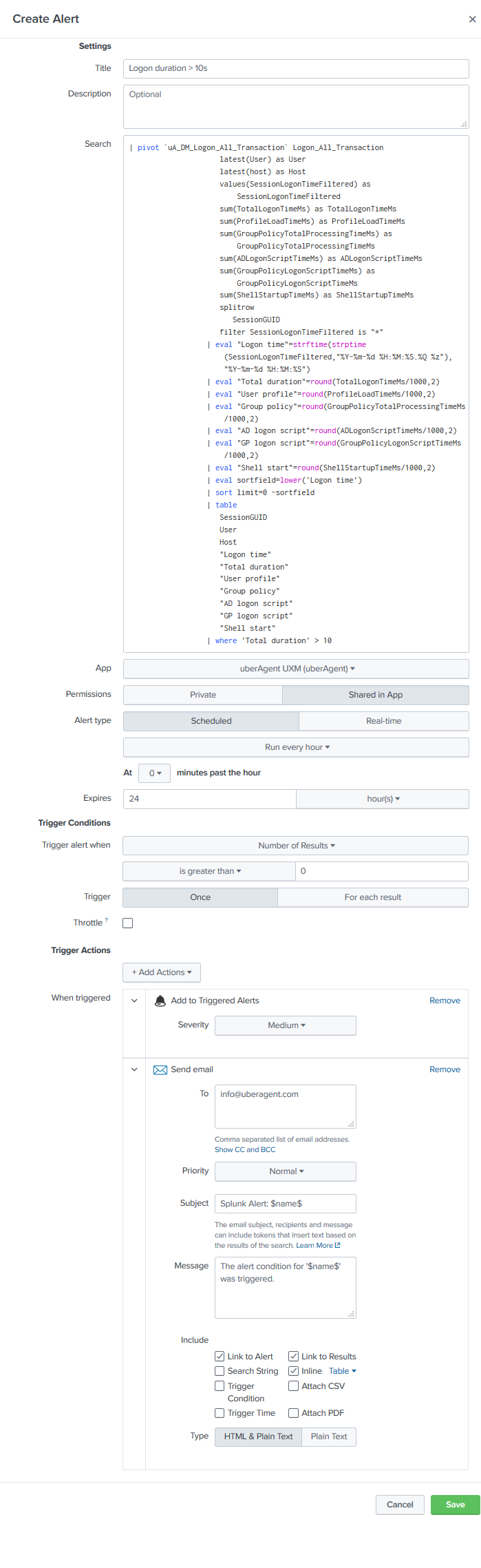
Specify email addresses for the email trigger action. It might also be a good idea to check Inline so that you get the actual data causing the alert right in the email.
Configure Email Alerting
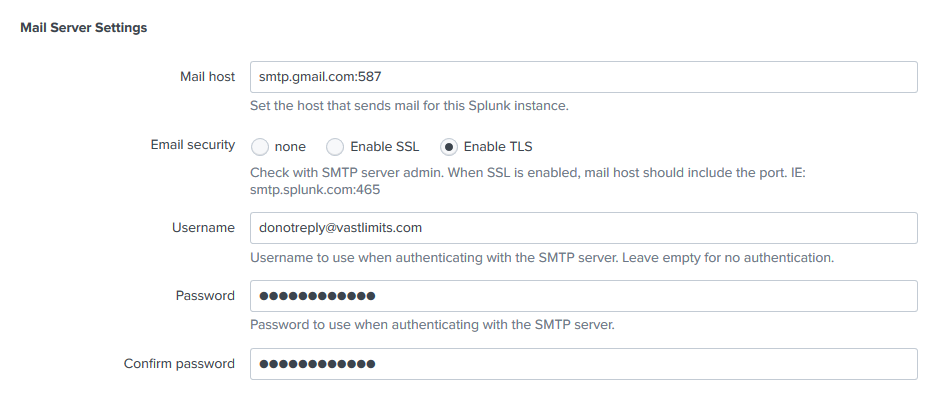
To configure alerting via Email go to Settings > Server settings > Email settings.
The following mail server settings apply to Google Apps:
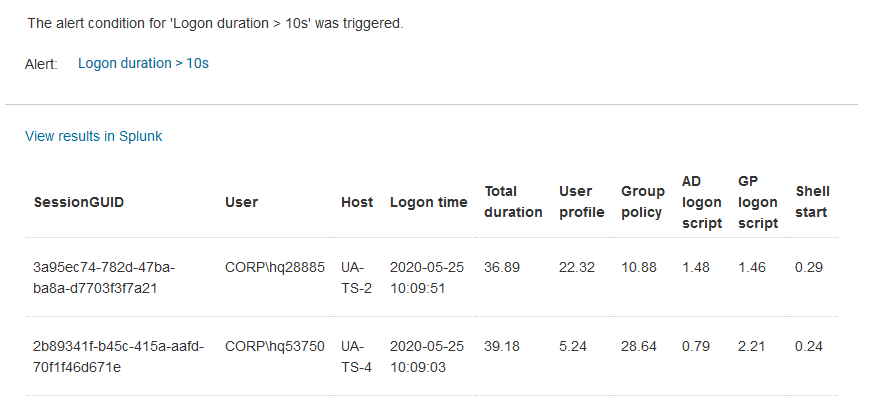
The Resulting Alerts
With that, you are all done. With the sample configuration you will receive an email like the following whenever a user logon takes more than 10 seconds:
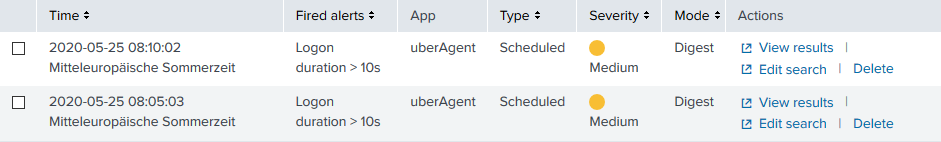
You can also see all alerts in Activity > Triggered Alerts:
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.