This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Rule Editor: uAQL Studio
uAQL Studio is a free online tool to learn, build and test uberAgent ESA Threat Detection rules.
Quickstart
Follow these steps to get started with uAQL Studio quickly:
- Open uAQL Studio in a new browser tab
- Select an event type
- Add events to test the uAQL query your going to write
- Work on your uAQL query until it matches your test events correctly
- Fill out the fields
Rule name,Tag,Risk score - Copy the rule definition from the preview pane to the clipboard and paste it into your uberAgent ESA configuration
Walkthrough
In this walkthrough, we’re building a Threat Detection rule that detects script child processes of Microsoft Office applications.
Launch uAQL Studio
Click the following link to launch uAQL Studio in a new browser tab: https://uberagent.com/uaql-studio/.
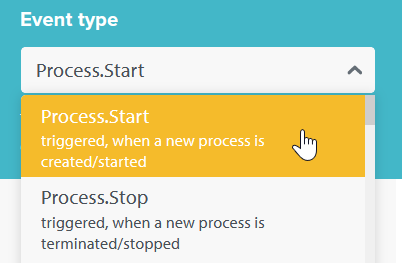
Select an Event Type
uberAgent ESA Threat Detection supports many different types of events, including process, network, registry, and DNS events. Select the Process.Start event type:
Add a Test Event
Click Add event and specify the properties of an event you want uAQL Studio to match against the uAQL query you’re going to write. Since we’re creating a rule to detect script child processes of MS Office apps we’re adding the properties of just such an event:
-
Parent.Name:
excel.exe -
Parent.Company:
Microsoft -
Process.Name:
powershell.exe
It should look similar to this:
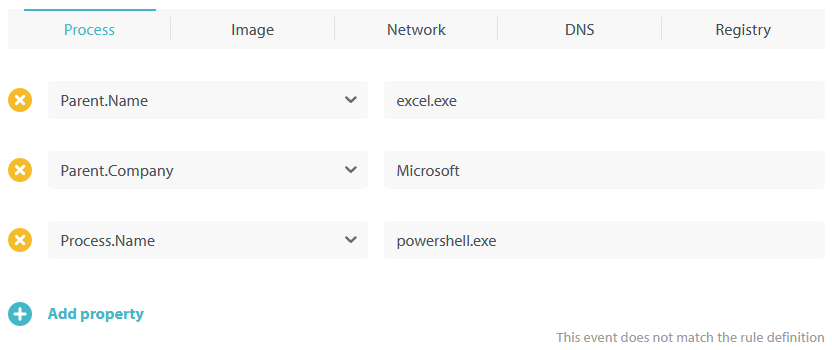
As you can see in the lower right corner of the above screenshot, at this point the test event is not matched by the rule definition (aka, the query). That is correct, of course. After all, the query is still empty!
Define the uAQL Query
Detecting Child Processes of MS Office Apps
Let’s start to work on our detection query by first creating a snippet that identifies child processes of MS Office apps. Please see the documentation for details. The following properties should work:
- the company name of the parent process needs to start with
Microsoft(which also covers "Microsoft Corporation" and variants like "Microsoft Corp.", all of which can be found in the wild) - the parent process name must be one of the following:
excel.exe,msaccess.exe,onenote.exe,outlook.exe,powerpnt.exe,winword.exe
In uAQL code the above looks as follows:
istartswith(Parent.Company, "Microsoft") and Parent.Name in ["excel.exe", "msaccess.exe", "onenote.exe", "outlook.exe", "powerpnt.exe", "winword.exe"]
<!--NeedCopy-->
Detecting Script Processes
We define the following executables as script runtimes:
-
PowerShell:
powershell.exe,pwsh.exe -
Batch, VBS, miscellaneous:
cmd.exe,cscript.exe,wscript.exe,ftp.exe
In uAQL code the above looks as follows:
Process.Name in ["cmd.exe", "cscript.exe", "wscript.exe", "ftp.exe"] or Process.Name in ["powershell.exe", "pwsh.exe"]
<!--NeedCopy-->
Putting the Query Together
We can now combine the two snippets into the complete uAQL query:
istartswith(Parent.Company, "Microsoft") and Parent.Name in ["excel.exe", "msaccess.exe", "onenote.exe", "outlook.exe", "powerpnt.exe", "winword.exe"] and (Process.Name in ["cmd.exe", "cscript.exe", "wscript.exe", "ftp.exe"] or Process.Name in ["powershell.exe", "pwsh.exe"])
<!--NeedCopy-->
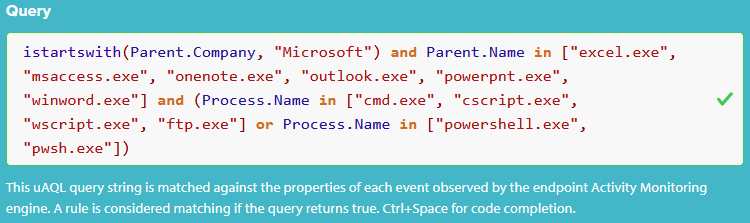
Paste the Query Into uAQL Studio
Copy the completed query from above and paste it into the Query field in uAQL Studio. The built-in syntax checking mechanism should show a green checkmark similar to the following:
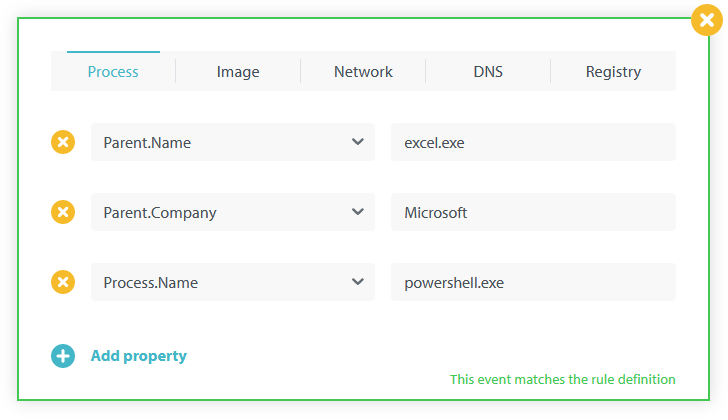
Verify the Test Event Matches
Take a look at the test event we created earlier. The green border indicates that it matches the query. The text in the lower right corner has changed to This event matches the rule definition:
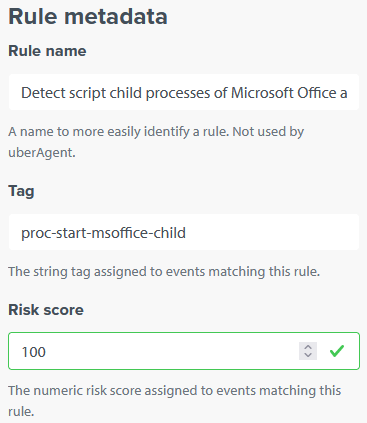
Add Rule Metadata
The rule definition is now complete but we need to add some metadata to make it usable with uberAgent and Splunk. Please see the documentation for details. The following values work well:
-
Rule name:
Detect script child processes of Microsoft Office applications -
Tag:
proc-start-msoffice-child -
Risk score:
100
The UI should now look similar to the following:
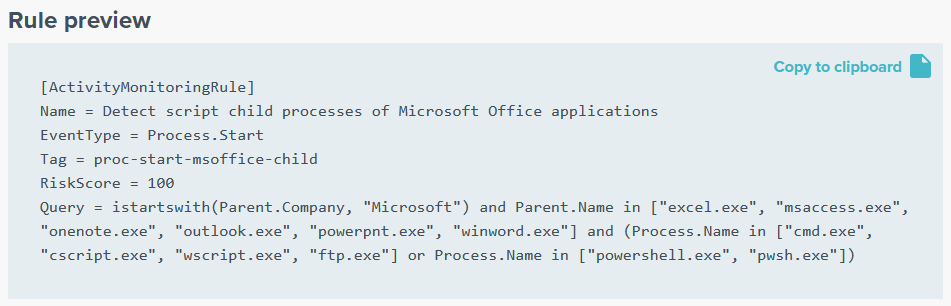
Copy the Rule Definition
With this, the rule definition is complete. We can copy it from the preview pane and use it with uberAgent ESA!
Share
Share
In this article
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.