-
-
-
-
-
-
Collecting More WiFi Details From WFH Employees
-
Building a Browser Extension Inventory Report (Chrome/Edge/Firefox)
-
Internet Explorer - Distinguish Standalone and Edge IE Mode Starts
-
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Collecting More WiFi Details From WFH Employees
Normally, laptop workers enjoy good quality WiFi or even a LAN network, connected through a docking station, in their company offices. Well, that changed during the Corona pandemic. The majority of employees are now working from home - connected through their personal WiFi and internet connection. That can be challenging for administrators when they have to troubleshoot a problem, as they have no insight into the quality of the employee’s network.
uberAgent supports administrators already to identify if a bad network is the cause of an issue.
One cannot have enough information when it comes to solving problems, though. Custom scripts to the rescue! This practice guide helps you with collecting even more information about WiFi connections.
The scripts listed in this guide are managed in vast limits’ public GitHub repository.
Collecting WiFi Information With PowerShell
Data Source: Netsh Command-Line Tool
Of course, using PowerShell is the standard these days when it comes to scripting. Sadly, there is no native PowerShell cmdlet for the information we’re interested in. We have to use the good old netsh command: netsh wlan show interface.
The output looks similar to the following:
There is 1 interface on the system:
Name : WLAN
Description : Intel(R) Dual Band Wireless-AC 8265
GUID : 1796b603-2174-45f7-8001-c05c4a011617
Physical address : ac:ed:5c:02:f0:30
State : connected
SSID : G12
BSSID : cc:ce:1e:2d:b0:86
Network type : Infrastructure
Radio type : 802.11n
Authentication : WPA2-Personal
Cipher : CCMP
Connection mode : Profile
Channel : 1
Receive rate (Mbps) : 144.4
Transmit rate (Mbps) : 144.4
Signal : 86%
Profile : Dominiks-WiFi
Hosted network status : Not available
<!--NeedCopy-->
The most interesting bits are the signal strength, the receive/transmit rates, the radio type, and the authentication type. With a little work, we can refactor that old-style text output to some useful PowerShell objects we can actually work with.
Converting Netsh Output to PowerShell Objects (EN)
$interface = @(netsh wlan show interface)
$hash = $null
# We only support machines with one interface for now. The following line also makes sure that the scripts only proceed if a WiFi interface is found at all.
If ($interface -match 'There is 1 interface on the system')
{
# The following builds a hash table from the netsh output
foreach($item in $interface)
{
if($item.Contains(':'))
{
$hash += @{
$item.Replace(" ","").split('{:}')[0] = $item.Replace(" ","").split('{:}')[1]
}
}
}
# Only connected interfaces are interesting
If ($hash.State -eq 'connected')
{
# Get the WiFi band by looking at the used channel
If ([int]$hash.Channel -gt 33)
{
$Band = '5'
}
Else
{
$Band = '2.4'
}
# Build the output hash
$Output = @{
'Signal' = $hash.Signal -replace '%',''
'Type' = $hash.Radiotype
'Receiverate' = $hash.'Receiverate(Mbps)'
'Transmitrate' = $hash.'Transmitrate(Mbps)'
'Band' = $Band
'SSID' = "`"$($hash.SSID)`""
'Authentication' = $hash.Authentication
'Cipher' = $hash.Cipher
}
# Finally, write the hash to stdout. The output will be picked up by uberAgent.
Write-Output $($Output.Keys.ForEach({"$_=$($Output.$_)"}) -join ' ')
}
Else
{
Throw "Interface $($hash.Name) not connected. Exiting..."
}
}
Else
{
Throw 'Zero or more than one interface on machine. Exiting...'
}
<!--NeedCopy-->
Running that script outputs the following:
Authentication=WPA2-Personal Transmitrate=144.4 Signal=86 Type=802.11n SSID="Dominiks-WiFi" Cipher=CCMP Receiverate=144.4 Band=2.4
Converting Netsh Output to PowerShell Objects (DE)
Unfortunately, the netsh output is language-specific. Hence the above script only works on English Windows operating systems. Below is a version for a German Windows, too. If you have other languages, please check the script and replace localized words according to your requirements.
$interface = @(netsh wlan show interface)
$hash = $null
# We only support machines with one interface for now. The following line also makes sure that the scripts only proceed if a WiFi interface is found at all.
If ($interface -match 'Es ist 1 Schnittstelle auf dem System vorhanden')
{
# The following builds a hash table from the netsh output
foreach($item in $interface)
{
if($item.Contains(':'))
{
$hash += @{
$item.Replace(" ","").split('{:}')[0] = $item.Replace(" ","").split('{:}')[1]
}
}
}
# Only connected interfaces are interesting
If ($hash.Status -eq 'Verbunden')
{
# Get the WiFi band by looking at the used channel
If ([int]$hash.Kanal -gt 33)
{
$Band = '5'
}
Else
{
$Band = '2.4'
}
# Build the output hash
$Output = @{
'Signal' = $hash.Signal -replace '%',''
'Type' = $hash.Funktyp
'Receiverate' = $hash.'Empfangsrate(MBit/s)'
'Transmitrate' = $hash.'Übertragungsrate(MBit/s)'
'Band' = $Band
'SSID' = "`"$($hash.SSID)`""
'Authentication' = $hash.Authentifizierung
'Cipher' = $hash.Verschlüsselung
}
# Finally, write the hash to stdout. The output will be picked up by uberAgent.
Write-Output $($Output.Keys.ForEach({"$_=$($Output.$_)"}) -join ' ')
}
Else
{
Throw "Interface $($hash.Name) not connected. Exiting..."
}
}
Else
{
Throw 'Zero or more than one interface on machine. Exiting...'
}
<!--NeedCopy-->
Start Collecting Data
Save the script to disk and create a new timer in uberAgent’s configuration. After a service restart, uberAgent starts collecting data.
[Timer]
Name = Get-WifiInfo
Interval = 60000
Script = powershell.exe -executionpolicy bypass -file "C:\Program Files\vast limits\uberAgent\Scripts\Get-WifiInfo.ps1"
ScriptContext = Session0AsSystem
<!--NeedCopy-->
The interval at which the script is run in the timer configuration above is 60 seconds; adjust it to your needs as required. Just remember that the value is specified in milliseconds.
Splunk it
Once the data is in Splunk you can use it to help you troubleshoot issues in WFH scenarios even easier.
Let’s assume you get a call by a WFH user who complains about a slow application. With the following search, you can quickly check if the user’s WiFi signal strength is low, causing the slowness of the application.
index=uberagent sourcetype="uberAgent:Script:Get-WifiInfo" host="LAPTOP-DOMINIK" | timechart latest(Signal) as "Signal quality (%)"
In the author’s case, the signal quality looks okay, but could be better:
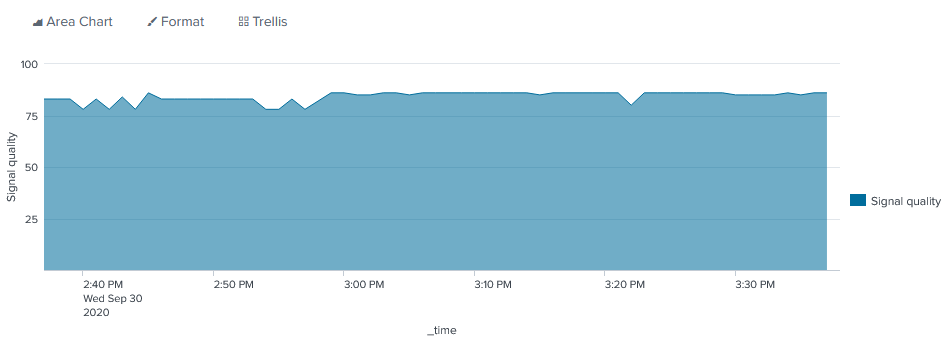
Signal quality is only one of the metrics we collected. Go and try one of the others for yourself!
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.