-
-
-
-
-
-
Documenting Applied Computer GPOs
-
Building a Browser Extension Inventory Report (Chrome/Edge/Firefox)
-
Internet Explorer - Distinguish Standalone and Edge IE Mode Starts
-
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Documenting Applied Computer GPOs
Managing thousands of machines is a tough job for which many organizations are using Group Policy. If you are familiar with uberAgent you may know that it lists GPOs that are applied during user logon. Computer policies, on the other hand, are not part of uberAgent’s regular feature set. However, that can easily be remedied with the help of uberAgent’s custom script functionality. This article shows how.
The scripts listed in this guide are managed in vast limits’ public GitHub repository.
Listing Applied Machine Policies
In a nutshell, the uberAgent custom scripts feature executes any script you like and sends the output to Splunk. This works with any scripting engine, of course. In this case, we used PowerShell.
The following script lists all applied machine policies.
# We need a temporary XML file to store the data
$OutputFile = "C:\Windows\Temp\TempGPOExport.xml"
# If the file exists delete it
If (Test-Path $OutputFile)
{
Remove-Item $OutputFile -Force
}
# Run gpresult and store the result in the temporary xml file
gpresult.exe /Scope Computer /X $OutputFile /F
# Read the xml file
[xml]$XML = Get-Content $OutputFile
# Get the names of all GPOs
$GPOs = ($XML.Rsop.ComputerResults.GPO).Name | Sort-Object
# Remove the temporary file
Remove-Item $OutputFile -Force
# Join all GPOs to a long string
$GPOs = $GPOs -join ';'
# Write the output. uberAgent will pick this up.
Write-Output "MachineGPOs=`"$GPOs`""
<!--NeedCopy-->
Save the script somewhere. For this example, we save the script as C:\Program Files\vast limits\uberAgent\Scripts\Get-MachineGPOs.ps1.
Configure uberAgent to Run the Script
Create a new timer in uberAgent’s configuration. With the settings shown below, the script will be executed once per day.
[Timer]
Name = Get-MachineGPOs
Interval = 86400000
Start delay = 600000
Persist interval = true
Thread priority = background
Script = powershell.exe -executionpolicy bypass -file "C:\Program Files\vast limits\uberAgent\Scripts\Get-MachineGPOs.ps1"
ScriptContext = Session0AsSystem
<!--NeedCopy-->
Splunk it
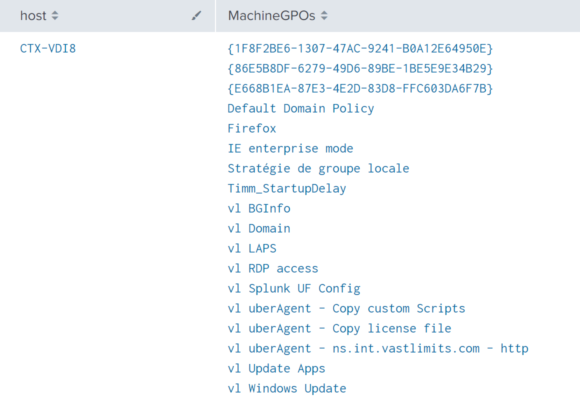
Once the data is in Splunk it can be used to document the applied computer GPOs. Run the following search to list all group policy objects per machine.
index = `uberAgent_index` sourcetype = "\"uberAgent:Script:Get-MachineGPOs\""
| stats
latest(MachineGPOs) as MachineGPOs
by host
| eval MachineGPOs = split(MachineGPOs,";")
| table
host
MachineGPOs
<!--NeedCopy-->
The results from the above search look like this:
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.