Microsoft Sentinel integration
Notes
Contact CAS-PM-Ext@cloud.com to request assistance for the Microsoft Sentinel integration, exporting data to Microsoft Sentinel, or provide feedback.
Data export to Microsoft Sentinel by using the Logstash engine is in preview. This feature is provided without a service level agreement and it’s not recommended for production workloads. For more information, see the Microsoft Sentinel documentation.
Integrate Citrix Analytics for Security™ with your Microsoft Sentinel by using the Logstash engine.
This integration enables you to export and correlate the users’ data from your Citrix IT environment to Microsoft Sentinel and get deeper insights into your organization’s security posture. View the insightful dashboards that are unique to Citrix Analytics for Security in your Splunk environment. You can also create custom views based on your security requirements.
For more information about the benefits of the integration and the type of processed data that is sent to your SIEM, see Security Information and Event Management integration.
Prerequisites
-
Turn on data processing for at least one data source. It helps Citrix Analytics for Security to begin the Microsoft Sentinel integration process.
-
Ensure that the following endpoint is in the allow list in your network.
Endpoint United States region European Union region Asia Pacific South region Kafka brokers casnb-0.citrix.com:9094casnb-eu-0.citrix.com:9094casnb-aps-0.citrix.com:9094casnb-1.citrix.com:9094casnb-eu-1.citrix.com:9094casnb-aps-1.citrix.com:9094casnb-2.citrix.com:9094casnb-eu-2.citrix.com:9094casnb-aps-2.citrix.com:9094casnb-3.citrix.com:9094 -
Ensure that you use logstash versions 7.17.7 or later (tested versions for compatibility with Citrix Analytics for Security: v7.17.7 and v8.5.3) with the Microsoft Sentinel output plug-in for Logstash.
Integrate with Microsoft Sentinel
-
Go to Settings > Data Exports.
-
On the Account set up section, create an account by specifying the user name and a password. This account is used to prepare a configuration file, which is required for the integration.
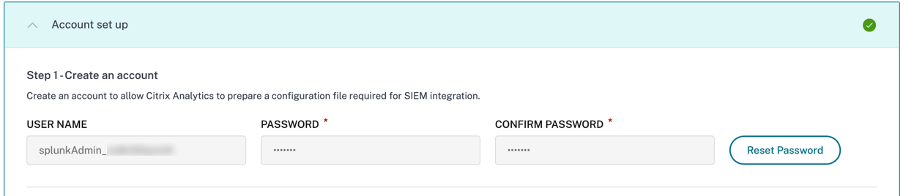
-
Ensure that the password meets the following conditions:

-
Click Configure to generate the Logstash configuration file.
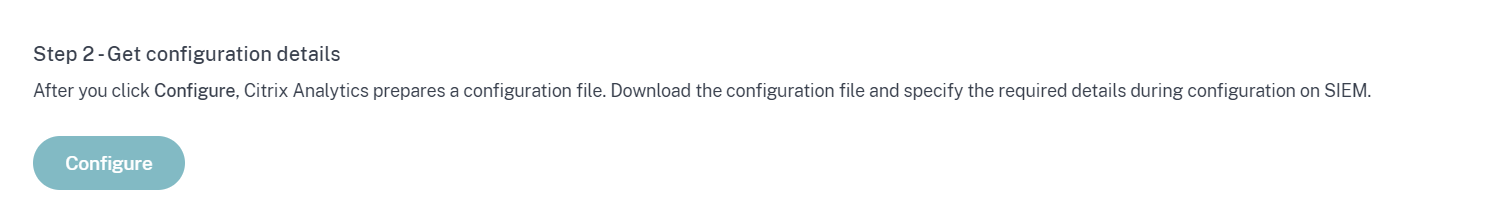
-
Select the Azure Sentinel (Preview) tab to download the configuration files:
-
Logstash config file: Contains the configuration data (input, filter, and output sections) for sending events from Citrix Analytics for Security to Microsoft Sentinel using the Logstash data collection engine.
For information on Logstash config file structure, see the Logstash documentation.
-
JKS file: Contains the certificates required for SSL connection.
Note
These files contain sensitive information. Keep them in a safe and secure location.
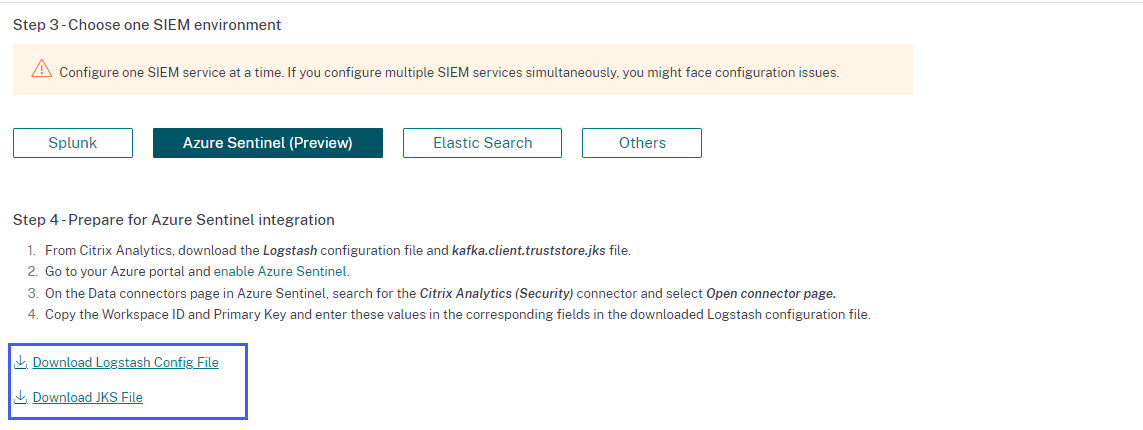
-
-
Prepare your Azure Sentinel integration:
-
On your Azure portal, enable Microsoft Sentinel. You can create a workspace or use your existing workspace to run Microsoft Sentinel.
-
From the main menu, select Data connectors to open the data connectors gallery.
-
Search for Citrix Analytics (Security).
-
Select Citrix Analytics (Security) and select Open connector page.
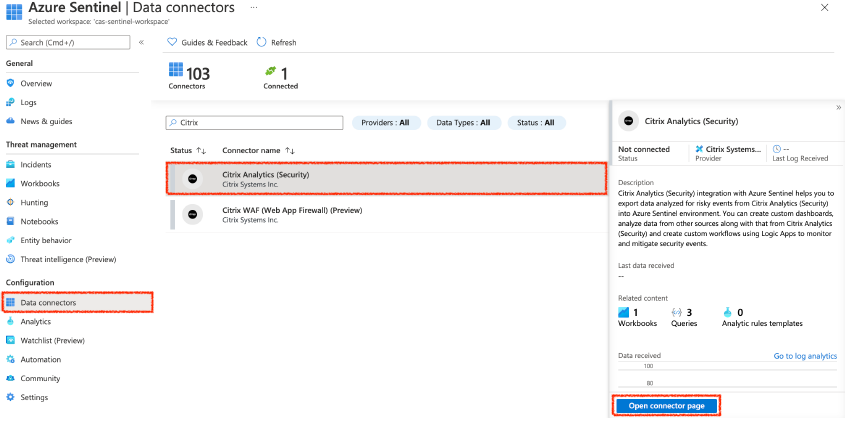
-
From the Citrix Analytics (Security) page, copy the Workspace ID and Primary Key. You must enter this information in the Logstash config file in subsequent steps.
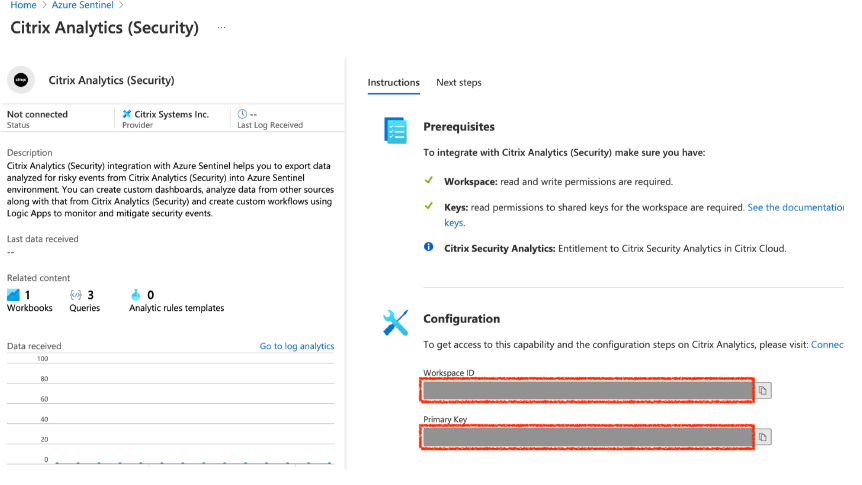
-
Configure Logstash on your host machine:
-
On your Linux or Windows host machine, install Logstash and Microsoft Sentinel output plug-in for Logstash.
-
On the host machine where you have installed Logstash, place the following files in the specified directory:
Host machine type File name Directory path Linux CAS_AzureSentinel_LogStash_Config.config For Debian and RPM packages: /etc/logstash/conf.d/For .zip and .tar.gz archives: {extract.path}/configkafka.client.truststore.jks For Debian and RPM packages: /etc/logstash/ssl/For .zip and .tar.gz archives: {extract.path}/sslWindows CAS_AzureSentinel_LogStash_Config.config C:\logstash-7.xx.x\configkafka.client.truststore.jks For information on the default directory structure of Logstash installation packages, see Logstash documentation.
-
Open the Logstash config file and do the following:
-
In the input section of the file, enter the following:
-
Password: The password of the account that you have created in Citrix Analytics for Security to prepare the configuration file.
-
SSL truststore location: The location of your SSL client certificate. This is the location of the kafka.client.truststore.jks file in your host machine.
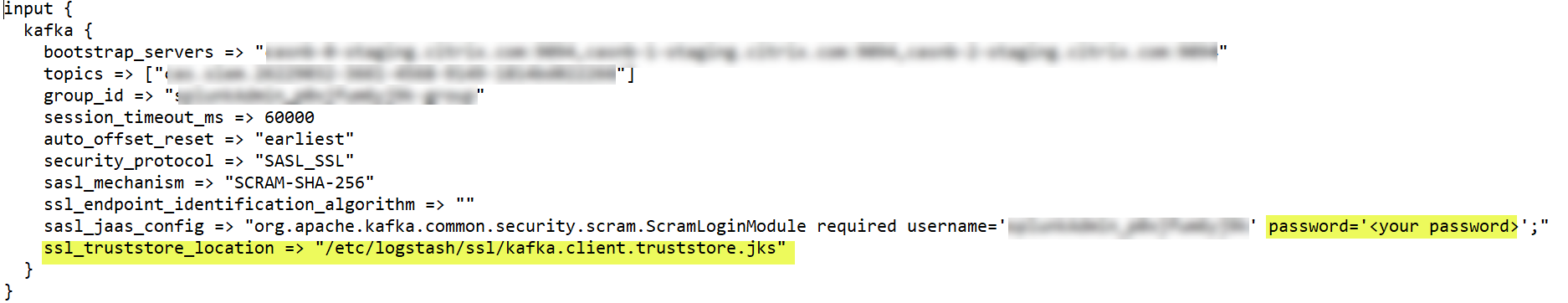
-
-
In the output section of the file, enter the Workspace ID and Primary key (that you have copied from Microsoft Sentinel) in the output section of the file.
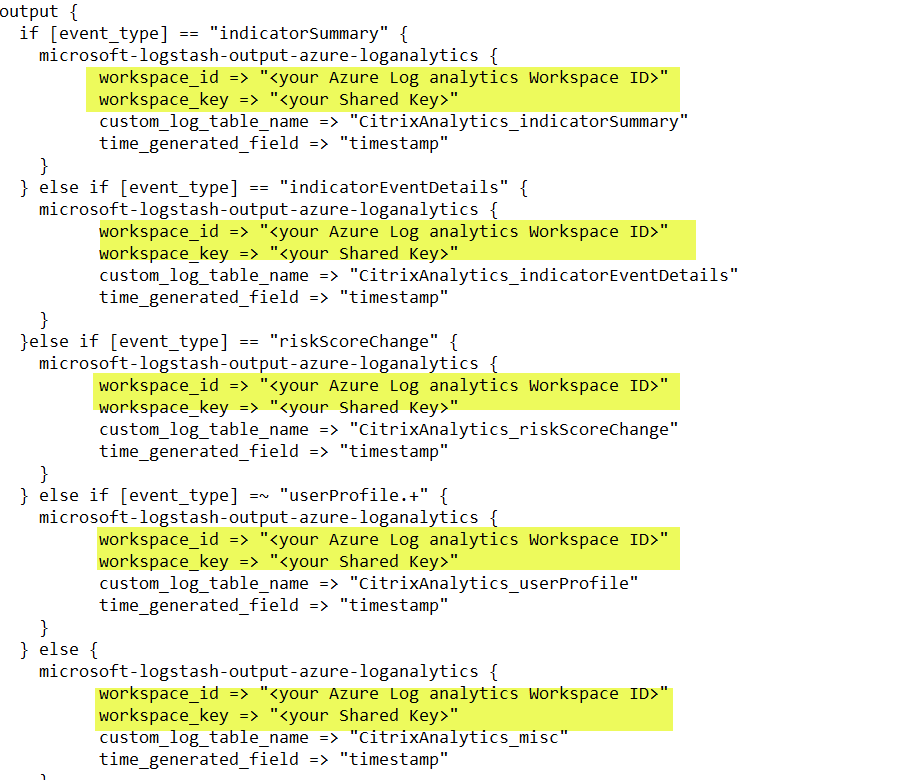
-
-
Restart the Logstash host machine to send the processed data from Citrix Analytics for Security to Microsoft Sentinel.
-
-
Go to your Microsoft Sentinel Workspace and view the data in the Citrix Analytics workbook.
-
Turn on or off data transmission
After Citrix Analytics for Security prepares the configuration file, data transmission is turned on for Microsoft Sentinel.
To stop transmitting data from Citrix Analytics for Security:
-
Go to Settings > Data Exports.
-
Turn off the toggle button to disable the data transmission. By default the data transmission always enabled..
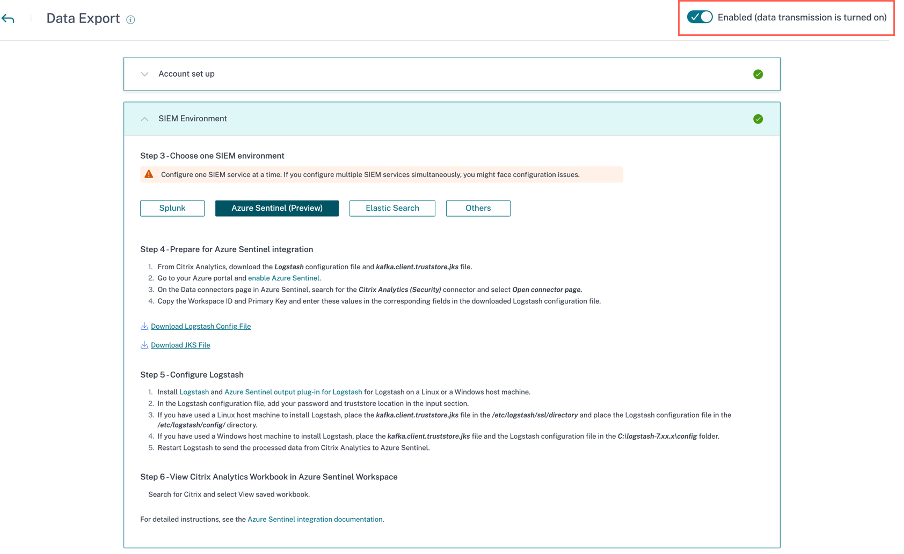
A warning window appears for your confirmation. Click Turn off data transmission button to stop the transmission activity.
To enable data transmission again, turn on the toggle button.
For learn more about Microsoft Sentinel integration, refer the following links: