Citrix Analytics for Security™ (Security Analytics)
With the advantage of work from anywhere, anytime, any device on any network, sensitive corporate data is exposed more than when users only worked from an isolated corporate office. Malicious users have a large attack surface to target. IT teams are charged with delivering a great user experience without compromising security. Citrix Analytics for Security can help bridge that gap with a focus on user security.
What is Security Analytics?
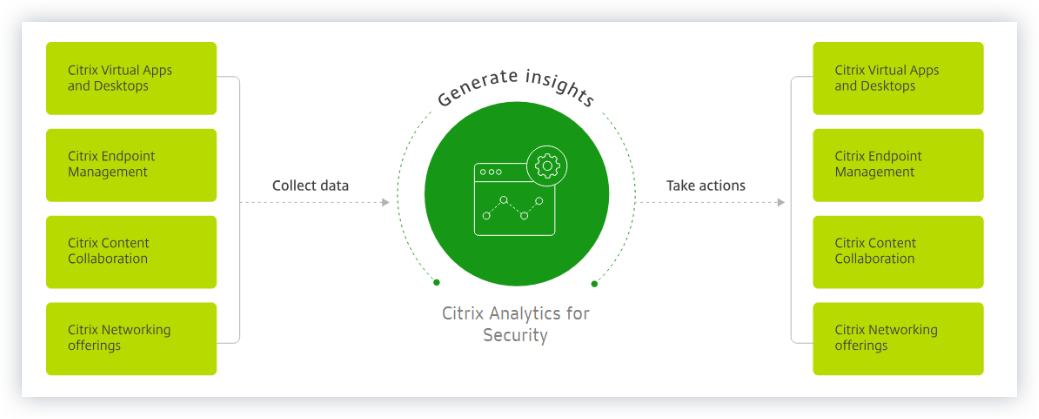
Citrix Analytics for Security continuously assesses the behavior of Citrix Virtual Apps and Desktops™ users, Citrix DaaS (formerly Citrix Virtual Apps and Desktops service) users, and Citrix Workspace™ users. It applies actions to protect sensitive corporate information. The aggregation and correlation of data across networks, virtualized applications and desktops tools enables the generation of valuable insights and more focused actions to address user security threats. Also, machine learning supports highly predictive approaches to identifying malicious user behavior.
Features
-
Streamlined insights from across Citrix products and partner integrations. For more information, see Self-service search.
-
Easy-to-consume dashboards provide a complete view of user behavior. For more information, see Users dashboard.
-
Detect and mitigate malicious user behavior using machine learning and customized policies with automated actions. For more information, see Policies and actions.
-
Continuous monitoring of user behavior after initial authentication to corporate networks balances thorough security and great user experience. For more information, see Continuous risk assessment.
Dashboards
You can view details about user or entity behavior on the following security dashboards:
-
Users: Provides visibility into user-behavior patterns across an organization.
-
User access: Summarizes the number of risky domains accessed and the volume of data uploaded and downloaded by the users in your network.
-
App Access: Summarizes the details of the domains, URLs, and apps accessed by users in your network.
-
Access Assurance Location: Summarizes the access details and the logon details of the Citrix Virtual Apps and Desktops users and Citrix DaaS users.
-
Reports: Create custom reports based on the dimensions and metrics available from the onboarded data sources.
What’s next
-
System requirements: Minimum requirements that must be met before getting started.
-
Data sources: Know about the products that Analytics supports.
-
Data governance: Know about the collection, storage, and retention of logs by Analytics.
-
Get started: How to start using Analytics in your organization.