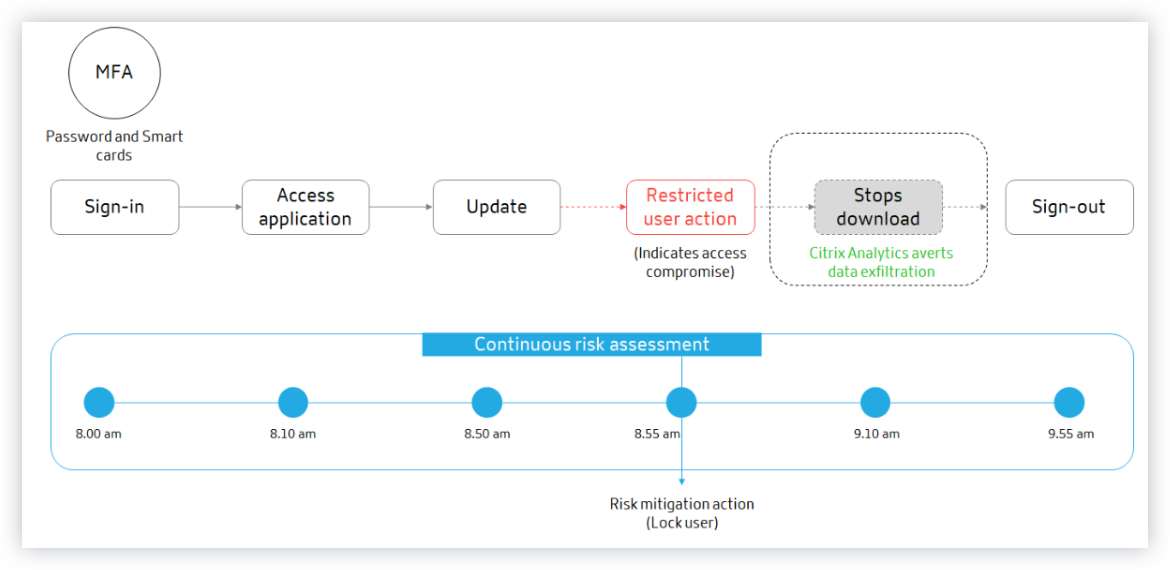
Continuous risk assessment
An increased use of portable computing devices and the internet allows Citrix Workspace™ users to work from almost any location and on any device. The challenge with this flexibility is that, remote access exposes sensitive data to security risks through cyber-criminal activities like data exfiltration, theft, vandalism, and service disruptions. Employees within organizations are also likely to contribute to this damage.
Some conventional ways of addressing such risks are to implement multifactor authentication, short sign-in sessions, and so on. Although these risk assessment methods ensure a higher level of security, they do not provide complete security after the initial validation of users. If a malicious user is successful in gaining access to the network, they misuse sensitive data that is harmful to an organization.
To enhance the security aspect and to ensure a better user experience, Citrix Analytics introduces the solution of continuous risk assessment. This solution protects your data from both external cyber criminals and malicious insiders by ensuring that the risk exposure of the users who are using Citrix Virtual Apps and Desktops or Citrix DaaS (formerly Citrix Virtual Apps and Desktops service) remains the same as it was when verified during the initial stage, without requiring the user to prove it every time. This solution is achieved by continuously assessing a risky event during a session and by automatically applying actions to prevent the organization’s resources from further misuse.
Use cases
Consider a user Adam Maxwell, who was able to access a network for the first time after multiple failed sign-in attempts from an unusual location that is contrary to their usual behavior. Also, the location has a track record of cyber attacks. In this scenario, you are required to take immediate action to avoid Adam’s account from further misuse. You can lock Adam’s account and notify him about the action taken. This action might temporarily create service disruptions to the user’s account. The user can contact the administrator for assistance to restore the account.
Consider another scenario where Adam has accessed a network from a new device and from a new IP for the first time. You can contact Adam asking to confirm if he identifies this activity. If so, it might be that Adam has changed his working device and is working from his home network. This activity does not cause any harm to your organization’s security, and can be ignored. However, if the user did not perform this activity, it is likely that the account has been compromised. In this scenario, you can lock the user’s account to prevent any further damage.
Key features
Continuous risk assessment automates some of the functionalities associated with policies and visibility dashboards:
Support multiple conditions
When you create or modify a policy, you can add up to four conditions. The conditions can contain combinations of default risk indicators and custom risk indicators, user risk scores, or both.
For more information, see What are policies.
Notify users before applying actions
Before applying an appropriate action on a user’s account, you can notify the user and assess the nature of an unusual activity that has been detected.
For more information, see Request end user response.
Notify users after applying actions
For some activities, awaiting user response before applying an action can put the user’s account and your organization’s security at risk. In such scenarios, you can apply a disruptive action when you detect an unusual activity, and notify the user about the same.
For more information, see Notify user after applying disruptive action.
Enforcement and monitor modes
You can set policies to enforcement or monitor modes based on your requirements. Policies in enforcement mode have a direct impact on users’ accounts. However, if you want to assess the impact or the outcome of your policies before implementing them, you can set your policies to monitor mode.
For more information, see Supported modes.
Visibility into access and policy dashboards
Using the Access Summary dashboard, you can gain insights into the number of access attempts made by users. For more information, see Access Summary.
Using the Policies and Actions dashboard, you can gain insights into the policies and actions applied on user accounts. For more information, see Policies and Actions.
Default policies
Citrix Analytics introduces pre-defined policies that are enabled on the Policies dashboard by default. These policies are created by using risk indicators and user risk scores as the pre-defined conditions. A global action is assigned to every default policy.
Note
The policies listed in your environment might vary depending on when you first started using Citrix Analytics, and whether you have made any local changes.
For more information, see What are policies.
You can use the following default policies or modify them based on your requirements:
| Policy name | Condition | Data source | Action |
|---|---|---|---|
| Successful credential exploit | When the Excessive authentication failures and Suspicious logon risk indicators are triggered | Citrix Gateway | Lock user |
| Potential data exfiltration | When the Potential data exfiltration risk indicator is triggered | Citrix Virtual Apps and Desktops and Citrix DaaS | Log off user |
| Unusual access from a suspicious IP | When the Suspicious logon and Logon from suspicious IP risk indicators are triggered | Citrix Gateway | Lock user |
| First time access from device | When the CVAD- First time access from new device risk indicator is triggered | Citrix Virtual Apps and Desktops and Citrix DaaS | Request end user response |
| Impossible travel on access | When the Impossible Travel risk indicator is triggered. | Citrix Virtual Apps and Desktops and Citrix DaaS | Request end user response |
| Impossible travel on authentication | When the Impossible Travel risk indicator is triggered. | Citrix Gateway | Request end user response |