Citrix Secure Private Access™ risk indicators
Risky website access
Note The following capabilities on Citrix Analytics for Security™ are impacted due to the deprecation of Category-based web filtering by Secure Private Access:
- Data fields such as Category-Group, Category and Reputation of URLs are not available anymore on the Citrix Analytics for security dashboard.
- The Risky website access indicator which relies on the same data is also deprecated and is not triggered for customers.
- Any existing custom risk indicators using the data fields (Category-Group, Category and Reputation of URLs) and its associated policies are not triggered anymore.
For details on the deprecation from Secure Private Access, refer to Feature deprecations.
Attempt to access blacklisted URL
Citrix Analytics detects data access threats based on the blacklisted URLs accessed by the user and triggers the corresponding risk indicator.
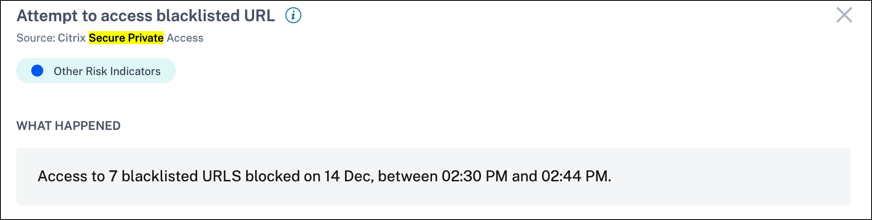
The Attempt to access blacklisted URL risk indicator is reported in Citrix Analytics when a user attempts to access a blacklisted URL configured in Secure Private Access.
The risk factor associated with the Attempt to access blacklisted URL risk indicator is the Other risk indicators. For more information about the risk factors, see Citrix user risk indicators.
When is the Attempt to access blacklisted URL risk indicator is triggered?
Secure Private Access includes a URL categorization feature that provides policy-based control to restrict access to blacklisted URLs. When a user attempts to access a blacklisted URL, Secure Private Access reports this event to Citrix Analytics. Citrix Analytics updates the user’s risk score and adds an Attempt to access blacklisted URL risk indicator entry to the user’s risk timeline.
How to analyze the Attempt to access blacklisted URL risk indicator?
Consider a user Georgina Kalou, accessed a blacklisted URL configured in Secure Private Access. Secure Private Access reports this event to Citrix Analytics, which assigns an updated risk score to Georgina Kalou. The Attempt to access blacklisted URL risk indicator is added to Georgina Kalou’s risk timeline.
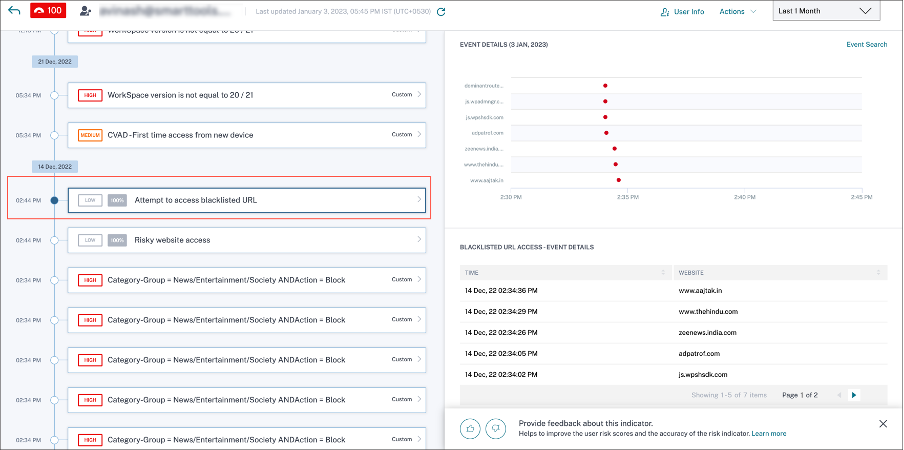
From Georgina Kalou’s risk timeline, you can select the reported Attempt to access blacklisted URL risk indicator. The reason for the event is displayed along with the details about the events, such as, time of the event, website details.
To view the Attempt to access blacklisted URL entry for a user, navigate to Security > Users, and select the user.
When you select the Attempt to access blacklisted URL risk indicator entry from the timeline, a corresponding detailed information panel appears in the right pane.
-
The WHAT HAPPENED section provides a brief summary of the risk indicator. It includes the details of the blacklisted URL accessed by the user during the selected period.
-
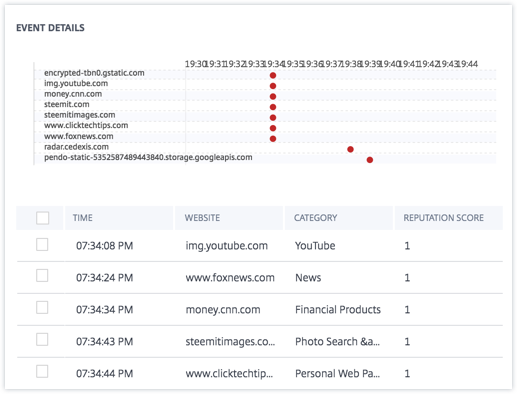
The EVENT DETAILS section, includes a timeline visualization of the individual events that occurred during the selected time period. Also, you can view the following key information about each event:
-
Time. The time the event occurred.
-
Website. The risky website accessed by the user.
-
Category. The category specified by Secure Private Access for the blacklisted URL.
-
Reputation rating. The reputation rating returned by Secure Private Access for the blacklisted URL. For more information, see URL reputation score.
-
What actions you can apply to the user?
You can perform the following actions on the user’s account:
-
Add to watchlist. When you want to monitor a user for future potential threats, you can add them to a watchlist.
-
Notify administrator(s). When there is any unusual or suspicious activity on the user’s account, an email notification is sent to all or selected administrators.
To learn more about actions and how to configure them manually, see Policies and Actions.
To apply the actions to the user manually, navigate to the user’s profile and select the appropriate risk indicator. From the Actions menu, select an action and click Apply.
Note
Irrespective of the data source that triggers a risk indicator, actions pertaining to other data sources can be applied.
Unusual upload volume
Citrix Analytics detects data access threats based on Unusual upload volume activity and triggers the corresponding risk indicator.
The Unusual upload volume risk indicator is reported when a user uploads excess volume of data to an application or website.
The risk factor associated with the Unusual upload volume risk indicator is the Other risk indicators. For more information about the risk factors, see Citrix user risk indicators.
When is the Unusual upload volume risk indicator triggered?
You can configure Secure Private Access to monitor user activities, such as malicious, dangerous, or unknown websites visited and the bandwidth consumed, and risky downloads and uploads. When a user in your organization uploads data to an application or website, Secure Private Access reports these events to Citrix Analytics.
Citrix Analytics monitors all these events and if it determines that this user activity is contrary to the user’s usual behavior, it updates the user’s risk score. The Unusual upload volume risk indicator is added to the user’s risk timeline.
How to analyze the unusual upload volume risk indicator?
Consider a user Adam Maxwell, who uploaded excess volume of data to an application or website. Secure Private Access reports these events to Citrix Analytics, which assigns an updated risk score to Adam Maxwell. The Unusual upload volume risk indicator is added to the Adam Maxwell’s risk timeline.
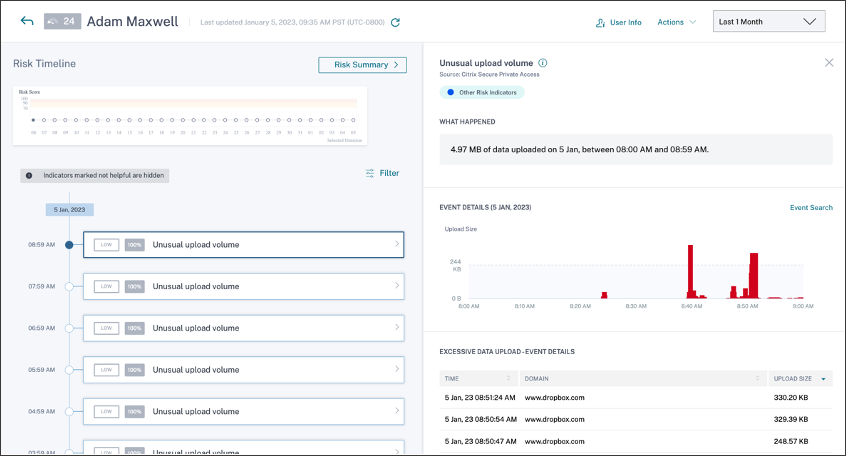
From Adam Maxwell’s risk timeline, you can select the reported Unusual upload volume risk indicator. The reason for the event is displayed along with the details about the events, such as, time of the event and domain.
To view the Unusual upload volume risk indicator, navigate to Security > Users, and select the user.
When you select an Unusual upload volume risk indicator entry from the timeline, a corresponding detailed information panel appears in the right pane.
-
The WHAT HAPPENED section provides a brief summary of the risk indicator, including the volume of data uploaded during the selected period.
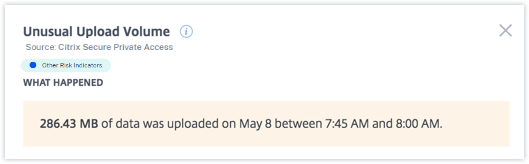
-
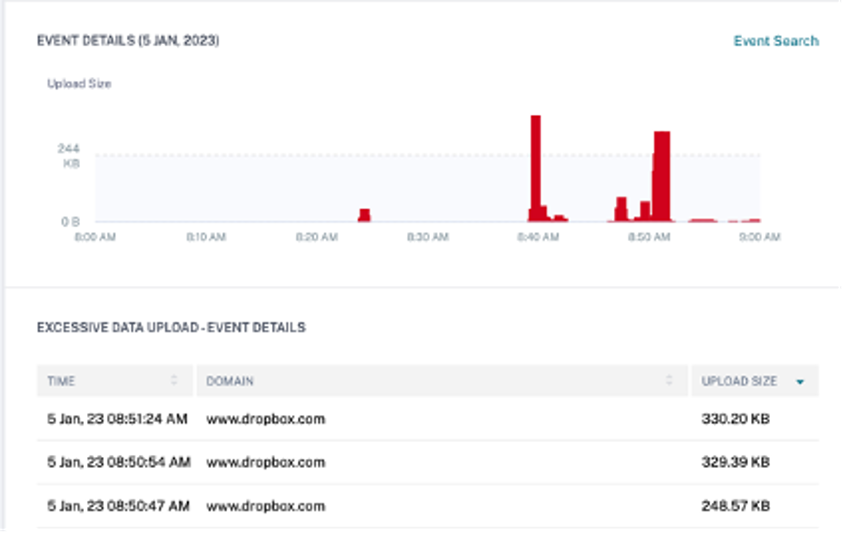
The EVENT DETAILS section, includes a timeline visualization of the individual data upload events that occurred during the selected time period. Also, you can view the following key information about each event:
-
Time. The time the excessive data was uploaded to an application or a website.
-
Domain. The domain to which the user uploaded the data.
-
Upload size. Volume of data uploaded to the domain.
-
What actions you can apply to the user?
You can do the following actions on the user’s account:
-
Add to watchlist. When you want to monitor a user for future potential threats, you can add them to a watchlist.
-
Notify administrator(s). When there is any unusual or suspicious activity on the user’s account, an email notification is sent to all or selected administrators.
To learn more about actions and how to configure them manually, see Policies and Actions.
To apply the actions to the user manually, navigate to the user’s profile and select the appropriate risk indicator. From the Actions menu, select an action and click Apply.
Note
Irrespective of the data source that triggers a risk indicator, actions pertaining to other data sources can be applied.
Excessive data download
Citrix Analytics detects data access threats based on the excessive data downloaded by users in your network and triggers the corresponding risk indicator.
The risk indicator is reported when a user in your organization downloads excess volume of data from an application or website.
When is the Excessive data download risk indicator triggered?
You can configure Secure Private Access to monitor user activities, such as malicious, dangerous, or unknown websites visited and the bandwidth consumed, and risky downloads and uploads. When a user in your organization downloads data from an application or website, Secure Private Access reports these events to Citrix Analytics.
Citrix Analytics monitors all these events and if it determines that the user activity is contrary to the user’s usual behavior, it updates the user’s risk score. The Excessive data download risk indicator is added to the user’s risk timeline.
The risk factor associated with the Excessive data download risk indicator is the Other risk indicators. For more information about the risk factors, see Citrix user risk indicators.
How to analyze the Excessive data download risk indicator?
Consider a user Georgina Kalou, downloaded excess volume of data from an application or website. Secure Private Access reports these events to Citrix Analytics, which assigns an updated risk score to Georgina Kalou and adds the Excessive data download risk indicator entry to the user’s risk timeline.
From Georgina Kalou’s risk timeline, you can select the reported Excessive data download risk indicator. The reason for the event is displayed along with the details about the events, such as, time and domain details.
To view the Excessive data download risk indicator, navigate to Security > Users, and select the user.
When you select the Excessive data download risk indicator entry from the timeline, a corresponding detailed information panel appears in the right pane.
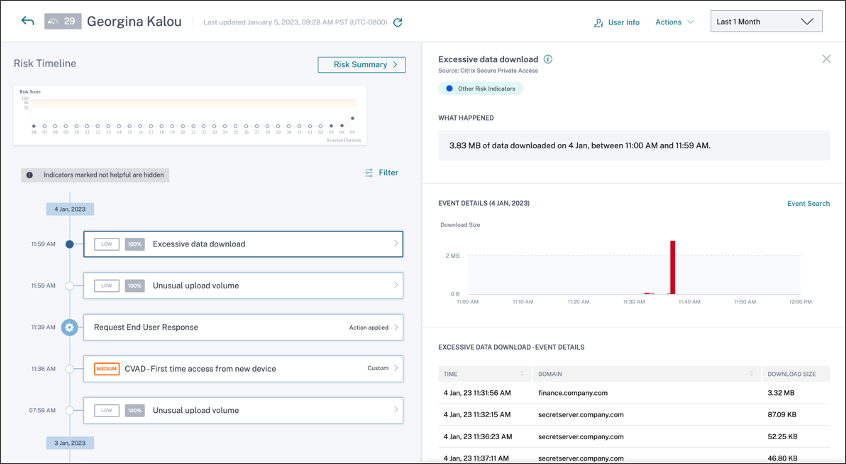
-
The WHAT HAPPENED section provides a brief summary of the risk indicator, including the volume of data uploaded downloaded during the selected period.
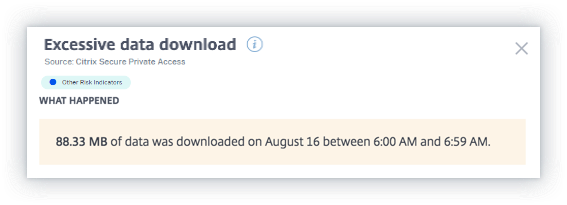
-
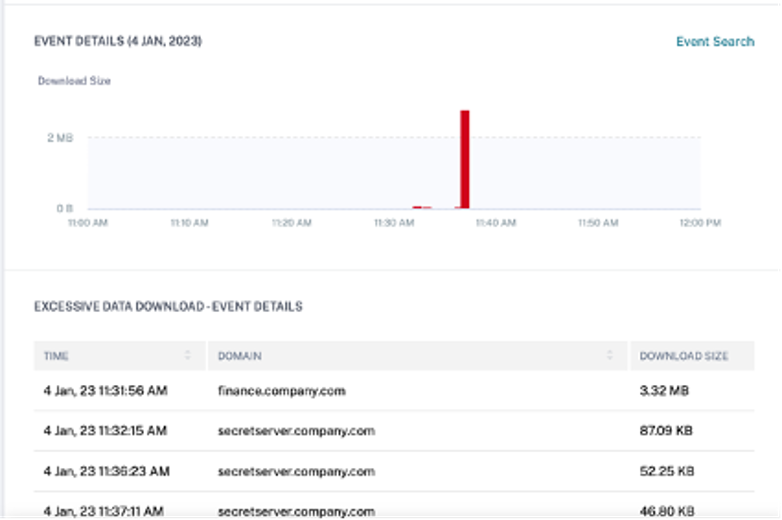
The EVENT DETAILS section, includes a timeline visualization of the individual data download events that occurred during the selected time period. Also, you can view the following key information about each event:
-
Time. The time the excessive data was downloaded to an application or a website.
-
Domain. The domain to which the user downloaded data.
-
Download size. Volume of data downloaded to the domain.
-
What actions you can apply to the user?
You can perform the following actions on the user’s account:
-
Add to watchlist. When you want to monitor a user for future potential threats, you can add them to a watchlist.
-
Notify administrator(s). When there is any unusual or suspicious activity on the user’s account, an email notification is sent to all or selected administrators.
To learn more about actions and how to configure them manually, see Policies and Actions.
To apply the actions to the user manually, navigate to the user’s profile and select the appropriate risk indicator. From the Actions menu, select an action and click Apply.
Note
Irrespective of the data source that triggers a risk indicator, actions pertaining to other data sources can be applied.