User risk timeline and profile
Note
Attention: Citrix Content Collaboration™ and ShareFile has reached its end of life and is no longer available to users.
The User risk timeline on a user’s profile enables you, as a Citrix Analytics administrator to gain deeper insights into a user’s risky behavior. By default, the user risk timeline is displayed for the last one month. You can also see the corresponding actions taken on their account for a selected time period. From the User risk timeline, you can delve deeper into a user’s profile to understand the following:
- Application Usage
- Data Usage
- Devices Usage
- Locations Usage
Also, you can view the risk score and risk indicator trends for the user and determine if the user is a high-risk user or not.
You can view the latest risk score of the user in the upper left corner of the User risk timeline page. The Risk Summary view reports show both the latest and historical maximum scores.
When you go to a user’s risk timeline, you can select either a risk indicator or an action that has been applied to their account. If you choose one of the above, the right pane displays the risk indicator section or the action section.
Risk timeline
The Risk Timeline displays the following information:
-
Risk indicators. Risk Indicators are user activities that are suspicious or can pose a security threat to your organization. The indicators are triggered when the user’s behavior deviates from their normal behavior. The risk indicators can be for the following data sources:
-
Citrix Content Collaboration
-
Citrix Gateway
-
Citrix Endpoint Management™
-
Citrix Virtual Apps and Desktops or Citrix DaaS (formerly Citrix Virtual Apps and Desktops service)
-
Citrix Secure Private Access
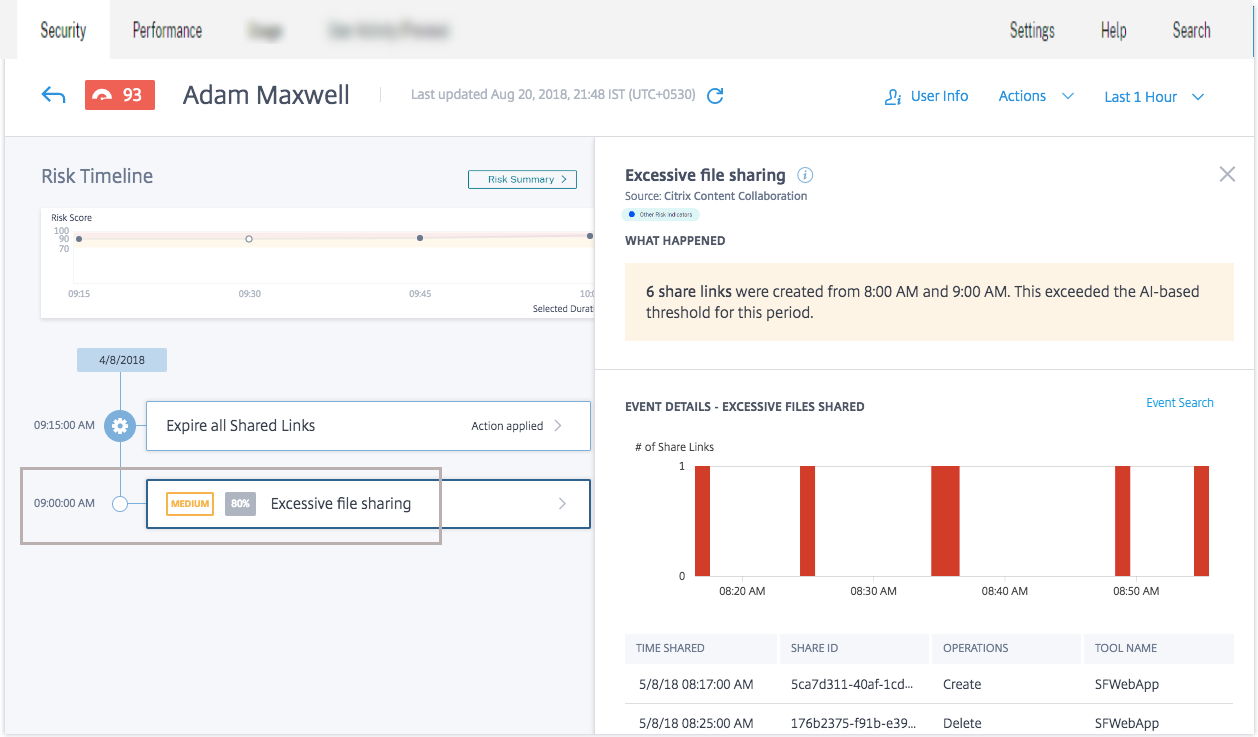
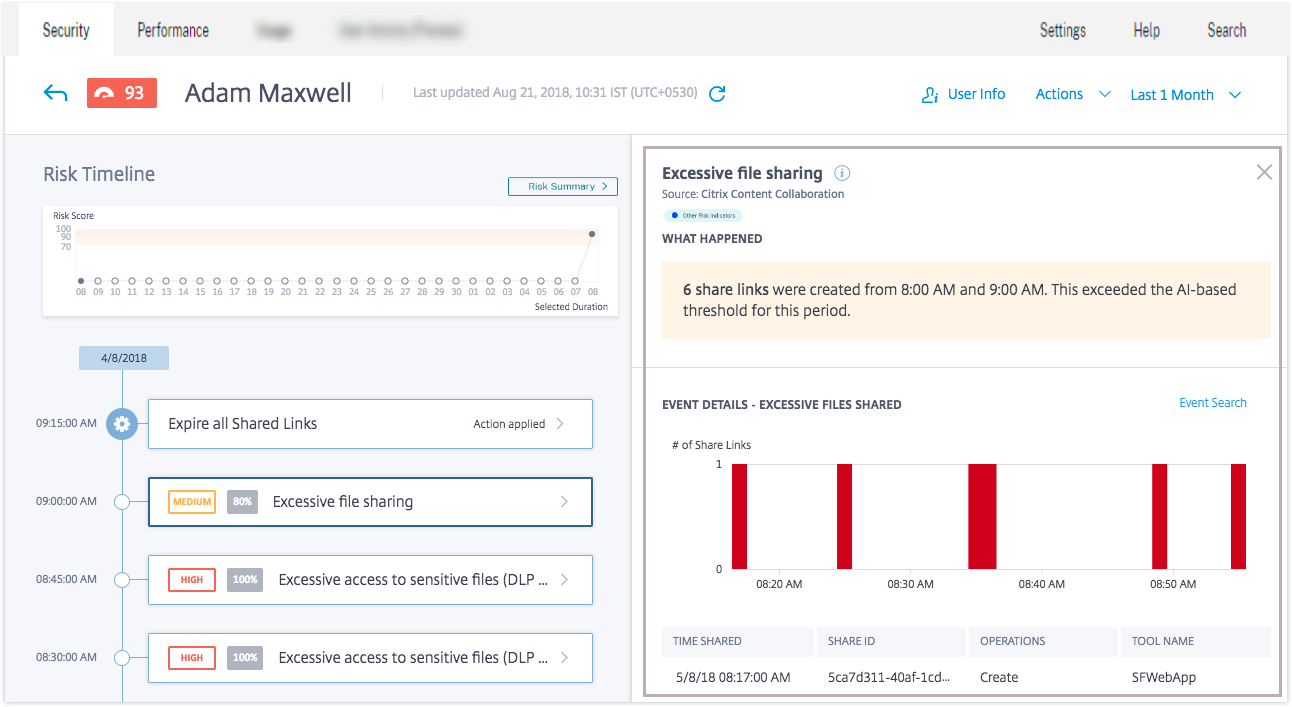
When you select a risk indicator from the user’s timeline, the risk indicator information section is displayed in the right pane. You can view the reason for the risk indicator along with details of the event. They are broadly categorized into the following sections:
-
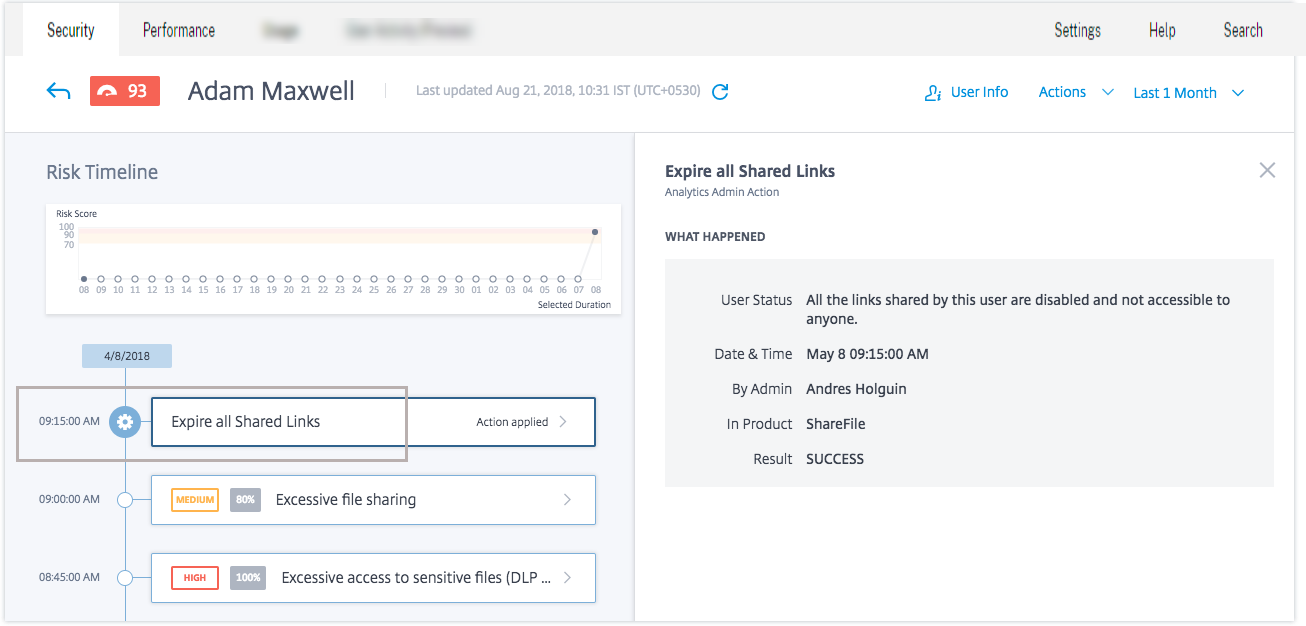
What happened. You can view a summary of the risk indicator here. For example, if you have selected the Excessive file sharing risk indicator. In the What happened section, you can view the number of share links sent to recipients and when the sharing event occurred.
-
Event details. You can view individual event entries in graphical and tabular format along with details of the event. Click Event Search to access the self-service search page and view the events corresponding to the user’s risk indicator. For more information, see Self-service search.
-
Additional contextual information. You can view data shared, if any, during an event’s occurrence in this section.
You can manually mark risk indicators as helpful or not helpful. For more information, see Provide feedback for User Risk indicators.
Learn more: Risk indicators
-
-
Actions. Actions help you respond to suspicious events and prevent future anomalous events from occurring. Actions that have been applied to a user’s profile are displayed on the risk timeline. These actions are either automatically applied to a user’s account through configured policies or you can apply a specific action manually.
Learn more: Policies and actions.
-
Privileged user events. Privileged user events are triggered every time there is a change in the Admin or Executive privilege status of a user. When a risk indicator is triggered for a user, you can co-relate it with the specified privilege status change event. If necessary, you can apply the appropriate action on the user profile. The Admin or Executive privilege events displayed on the user risk timeline are as follows:
-
Added to Executive group
-
Removed from Executive group
-
Privilege elevated to Admin
-
Admin privilege removed
Consider the user Adam Maxwell who was added to the Executive privileged group CitrixAnalytics. The Added to Executive group event is added to the user’s risk timeline. Now, Adam starts excessively deleting files and folders and triggers the machine learning algorithm that detects unusual behavior. The Excessive file or folder deletion risk indicator is added to the user’s risk timeline. You can compare the event and the risk indicator on the risk timeline. After the comparison, you can determine if the risk indicator was triggered as a consequence of the event. If so, you can apply appropriate actions to Adam’s profile. For more information on privileged users, see Privileged users.
-
When you select an event from the user’s timeline, the event information section is displayed in the right pane.
For an Executive, the right pane displays information such as User status, Date and time, and Active Directory group.
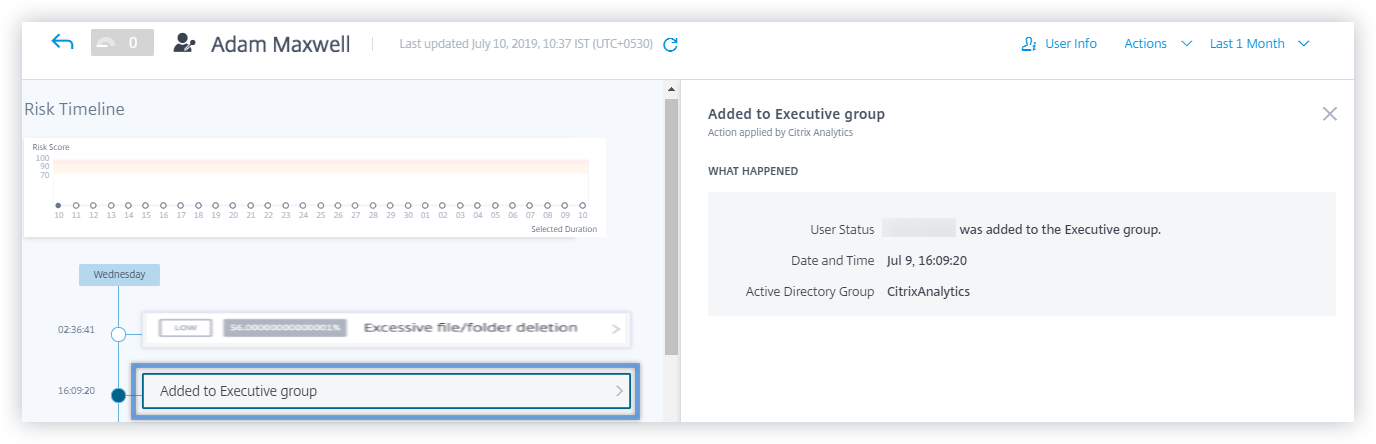
For an Admin privilege event, the right pane displays information such as User status, Date and time, and In product.
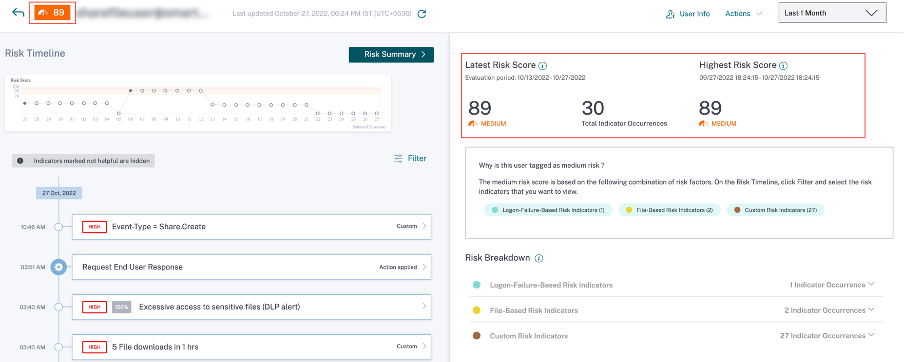
Risk summary
View the risk factors associated with the user that contributed to their risk score. You can see the risk score details taken as the maximum over the selected time period, along with the latest score and corresponding risk indicator count. Upon navigation to the User Timeline from either the main landing page or the Risky Users page, the time selection is preserved from the source page. For more information about the risk factors, see Citrix user risk indicators.
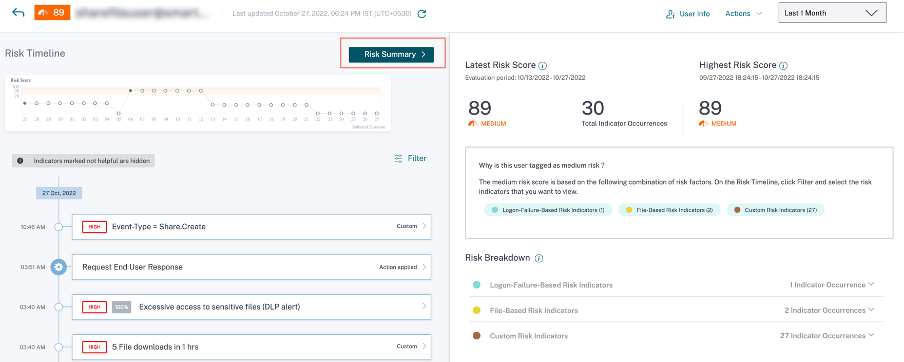
Click Risk Summary to view the following information:
-
Latest risk score: The latest risk score indicates the current risk of the user based on recent behavior. The risk score determines the level of risk a user poses to an organization over a trailing 2-week period. The risk score value is dynamic and varies based on user behavior analytics. Based on the score, a user can fall under one of the following categories: high-risk user, medium-risk user, low-risk user, and user with zero risk score. For more information about the user categories, see Users dashboard.
- Total indicator occurrences: Indicates the total number of risk indicators triggered by the user in the last two weeks. These triggered risk indicators determine the user’s risk score.
-
Highest Risk score: The highest risk score indicates the maximum value of the risk scores calculated for this user within the selected time duration. It is representative of the aggregate risk for the user and may not always be equal to the latest risk score.
-
Risk factors: Indicates one or more combinations of the risk factors associated with the user activities that contributed to the risk score.
-
Risk breakdown: Indicates the number of risk indicators triggered by the user for each risk factor. Expand the row to view the details.
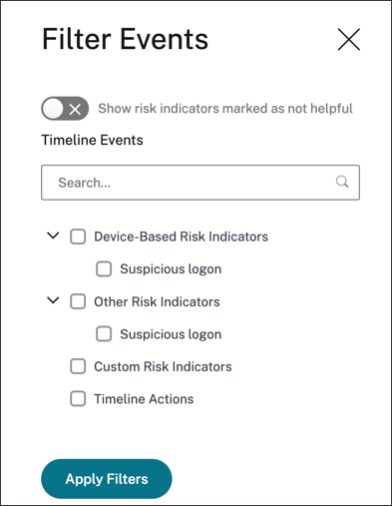
On the user timeline, click Filter and select the risk factors, the applied actions, or the privileged user status associated with the user and view the corresponding events.
User profile
The User Profile page displays the following user information that comes from the user’s active directory:
- Job Title
- Address
- Phone
- Location
- Organization