Splunk integration
Integrate Citrix Analytics for Security with Splunk to export and correlate the users’ data from your Citrix IT environment to Splunk and get deeper insights into your organization’s security posture.
For more information about the benefits of the integration and the type of processed data that is sent to your SIEM, see Security Information and Event Management integration.
To develop a comprehensive understanding of the Splunk Deployment Methodology and adopt the strategies for effective planning, refer Splunk architecture with Citrix® Analytics applications hosted on Splunk documentation.
Integrate Citrix Analytics for Security™ with Splunk
Follow the guidelines mentioned to integrate Citrix Analytics for Security with Splunk:
-
Data export. Citrix Analytics for Security creates a Kafka channel and exports Risk Insights and Data source events. Splunk retrieves this risk intelligence from the channel.
-
Get configuration on Citrix Analytics. Create a password for your pre-defined account for authentication. Citrix Analytics for Security prepares a configuration file required for you to configure the Citrix Analytics add-on for Splunk.
-
Download and install Citrix Analytics add-on for Splunk. Download the Citrix Analytics Add-on for Splunk either using Splunkbase or Splunk Cloud to complete the installation process.
-
Configure Citrix Analytics add-on for Splunk. Set up a data input by using the configuration details provided by Citrix Analytics for Security and configure the Citrix Analytics add-on for Splunk.
After the Citrix Analytics configuration file is prepared, see:
After the Citrix Analytics add-on for Splunk is configured, see:
Data export
-
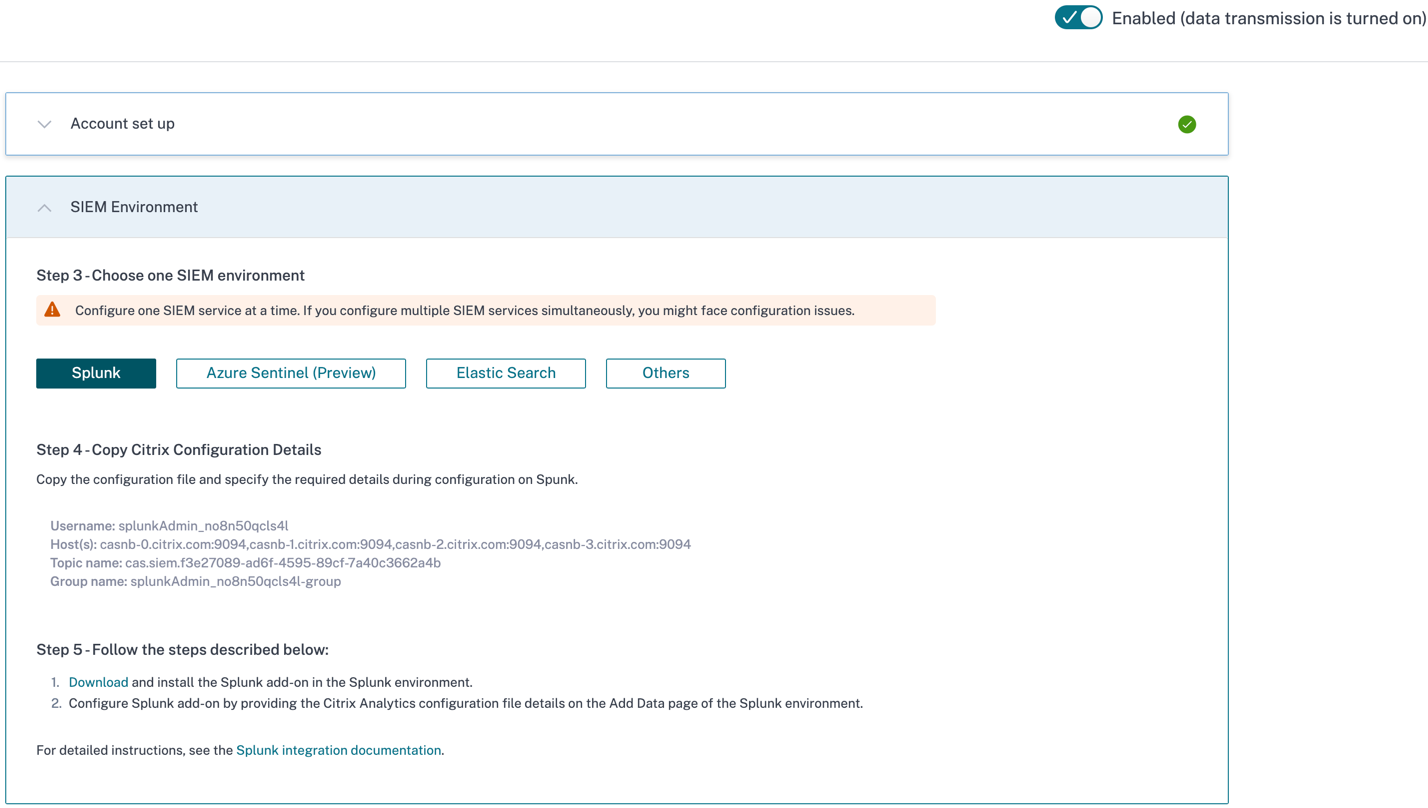
Go to Settings > Data Exports.
-
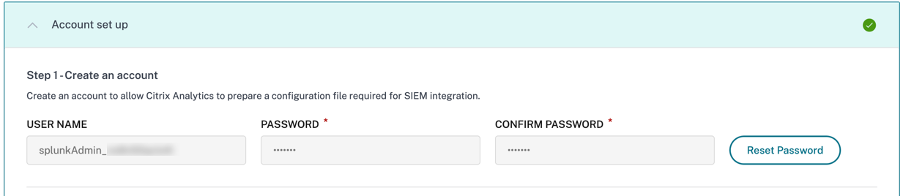
On the Account set up section, create an account by specifying the user name and a password. This account is used to prepare a configuration file, which is required for the integration.
-
Ensure that the password meets the following conditions:

-
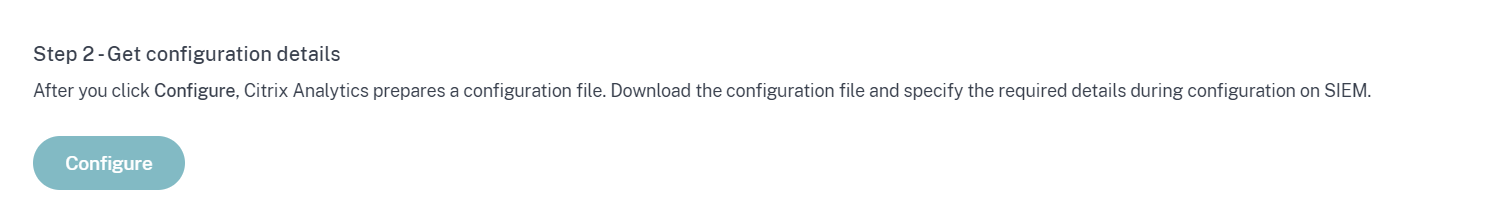
Select Configure.
Citrix Analytics for Security prepares the configuration details required for Splunk integration.
-
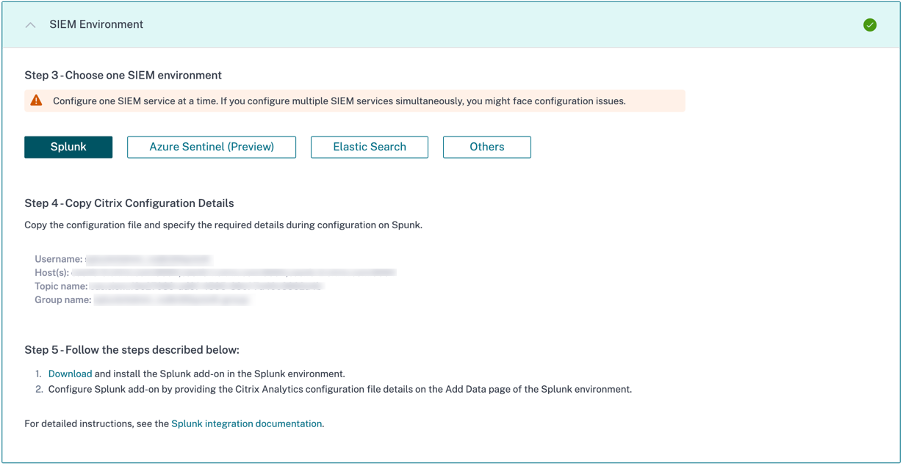
Select Splunk.
-
Copy the configuration details, which include the user name, hosts, Kafka topic name, and group name.
You require these details to configure Citrix Analytics Add-on for Splunk in the subsequent steps.
IMPORTANT
These details are sensitive and you must store them in a secure location.
To generate candidate data for Splunk Integration, either turn on data processing for at least one data source or use test event generation capability. It helps Citrix Analytics for Security to begin the Splunk integration process.
Reset Password Capability
If you want to reset your configuration password on Citrix Analytics for Security, do the following steps:
-
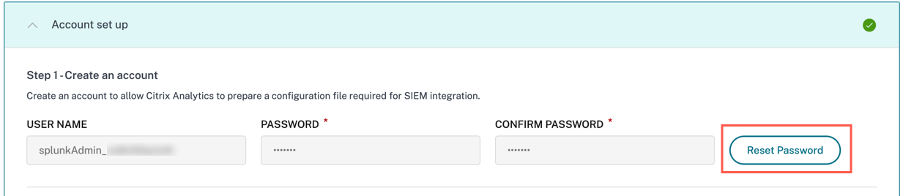
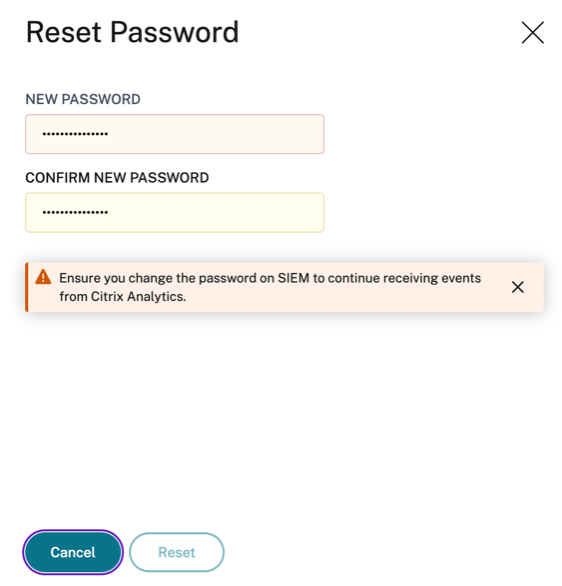
On the Account set up page, click Reset Password.
-
On the Reset Password window, specify the updated password on the NEW PASSWORD and CONFIRM NEW PASSWORD fields. Follow the password rules that are displayed.

-
Click Reset. The configuration file preparation is initiated.
Note
After you reset the configuration password, ensure you update the new password when you set up the data input on the Add Data page of your Splunk environment. It helps Citrix Analytics for Security to continue transmitting data to Splunk.
Turn on or off data transmission
Data Transmission for Splunk data export from Citrix Analytics is turned on by default.
To stop transmitting data from Citrix Analytics for Security:
-
Go to Settings > Data Exports.
-
Turn off the toggle button to disable the data transmission.
To enable data transmission again, turn on the toggle button.
Citrix Analytics Add-On for Splunk
You can choose to install the add-on application on either of the following platforms:
Citrix Analytics Add-On for Splunk (On-prem/Enterprise)
Supported versions
Citrix Analytics for Security supports Splunk integration on the following operating systems:
- CentOS Linux 7 and later
- Debian GNU/Linux 10.0 and later
- Red Hat Enterprise Linux Server 7.0 and later
- Ubuntu 18.04 LTS and later
Note
Citrix recommends using the latest version of the preceding operating systems or the versions that are still under support from the respective vendors.
For the Linux kernel (64-bit) operating systems, use a kernel version that is supported by Splunk. For more information, see Splunk documentation.
You can configure our Splunk integration on the following Splunk version: Splunk 8.1 (64-bit) and later.
Prerequisites
-
The Citrix Analytics add-on for Splunk connects to the following endpoints on Citrix Analytics for Security. Ensure that the endpoints are in the allow list in your network.
Endpoint United States region European Union region Asia Pacific South region Kafka brokers casnb-0.citrix.com:9094casnb-eu-0.citrix.com:9094casnb-aps-0.citrix.com:9094casnb-1.citrix.com:9094casnb-eu-1.citrix.com:9094casnb-aps-1.citrix.com:9094casnb-2.citrix.com:9094casnb-eu-2.citrix.com:9094casnb-aps-2.citrix.com:9094casnb-3.citrix.com:9094
Note
Try using the endpoint names not the IP addresses. The public IP addresses of the endpoints might change.
Download and install Citrix Analytics add-on for Splunk
You can choose to install the add-on using Install app from file or from within the Splunk environment.
Install app from file
-
Go to Splunkbase.
-
Download the Citrix Analytics Add-on for Splunk file.
-
On the Splunk Web home page, click the gear icon next to Apps.
-
Click Install app from file.
-
Locate the downloaded file and click Upload.
Notes
-
If you have an older version of the add-on, select Upgrade app to overwrite it.
-
If you are upgrading Citrix Analytics Add-on for Splunk from a version earlier than 2.0.0, you must delete the following files and folders located inside the /bin folder of the add-on installation folder and restart your Splunk Forwarder or Splunk Standalone environment:
cd $SPLUNK_HOME$/etc/apps/TA_CTXS_AS/binrm -rf splunklibrm -rf macrm -rf linux_x64rm CARoot.pemrm certificate.pem
-
-
Verify that the app appears in the Apps list.
Install app from within Splunk
-
From the Splunk Web home page, click +Find More Apps.
-
On the Browse More Apps page, search Citrix Analytics Add-on for Splunk.
-
Click Install next to the app.
-
Verify that the app appears in the Apps list.
Configure Citrix Analytics add-on for Splunk
Configure the Citrix Analytics add-on for Splunk using the configuration details provided by Citrix Analytics for Security. After the add-on is successfully configured, Splunk starts consuming events from Citrix Analytics for Security.
-
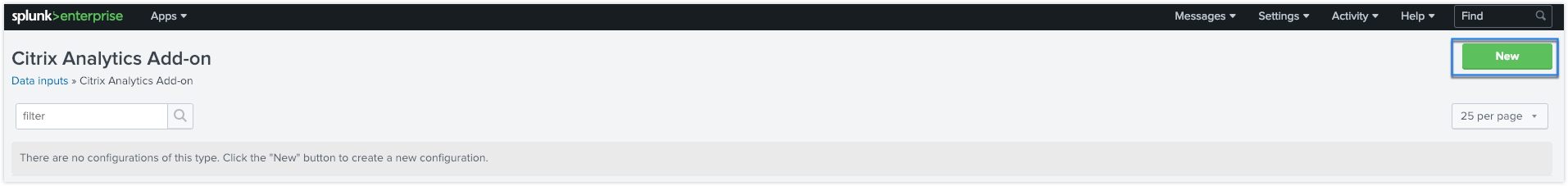
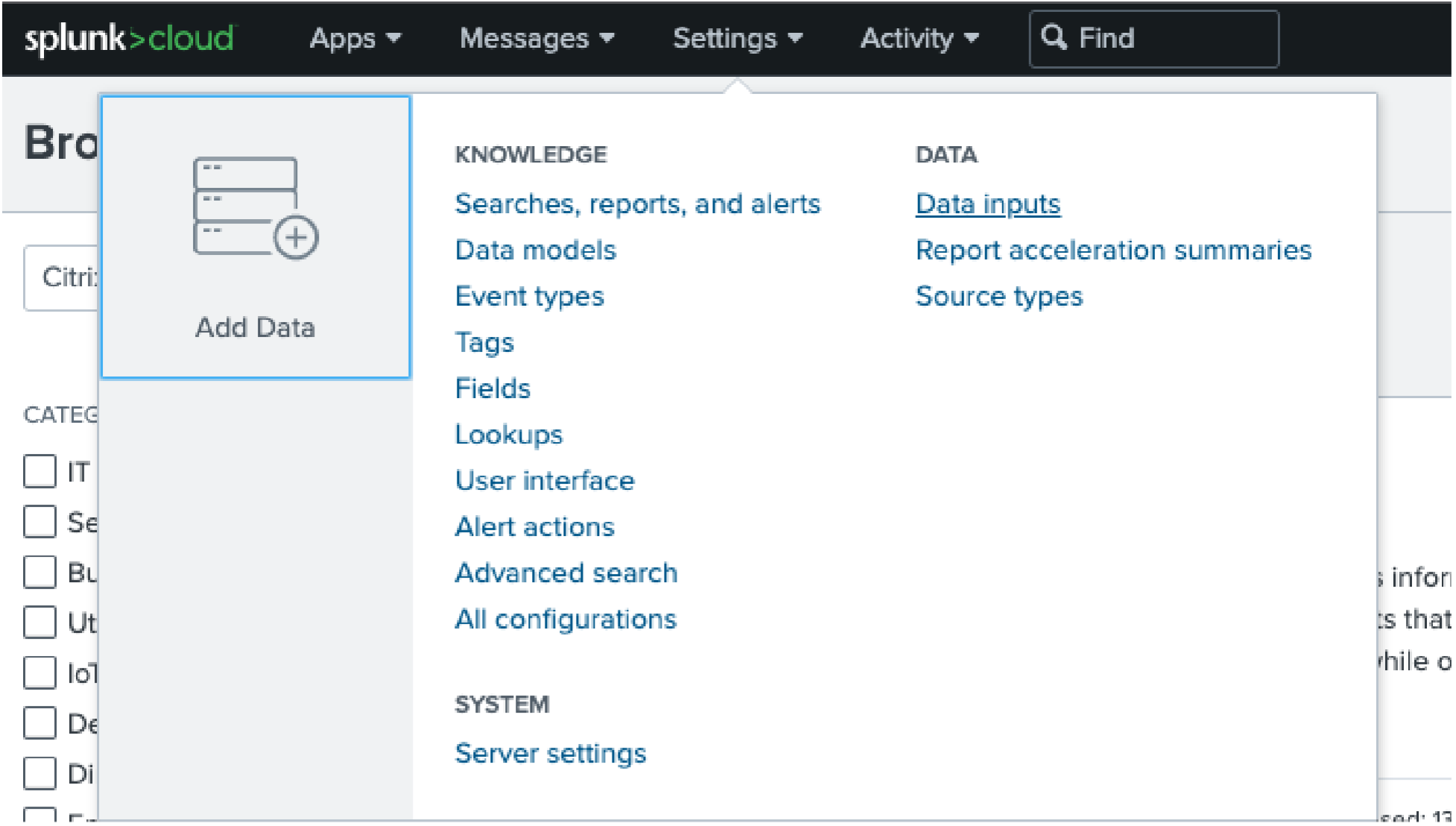
On the Splunk home page, go to Settings > Data inputs.
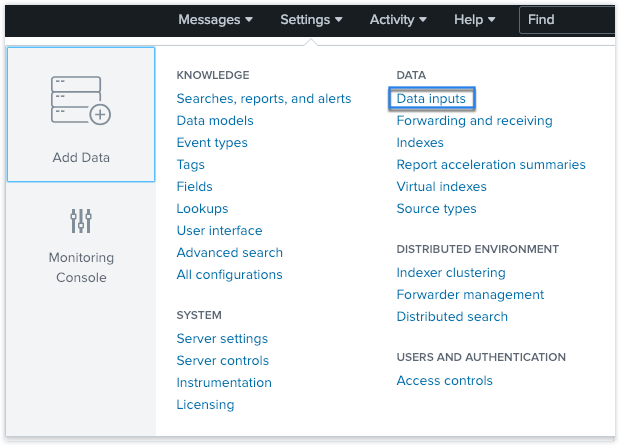
-
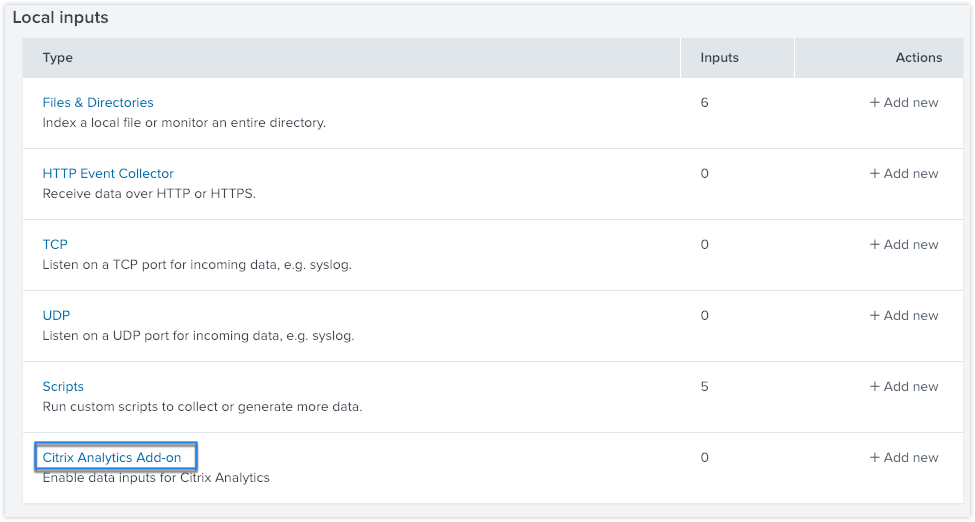
In the Local inputs section, click Citrix Analytics Add-on.
-
Click New.
-
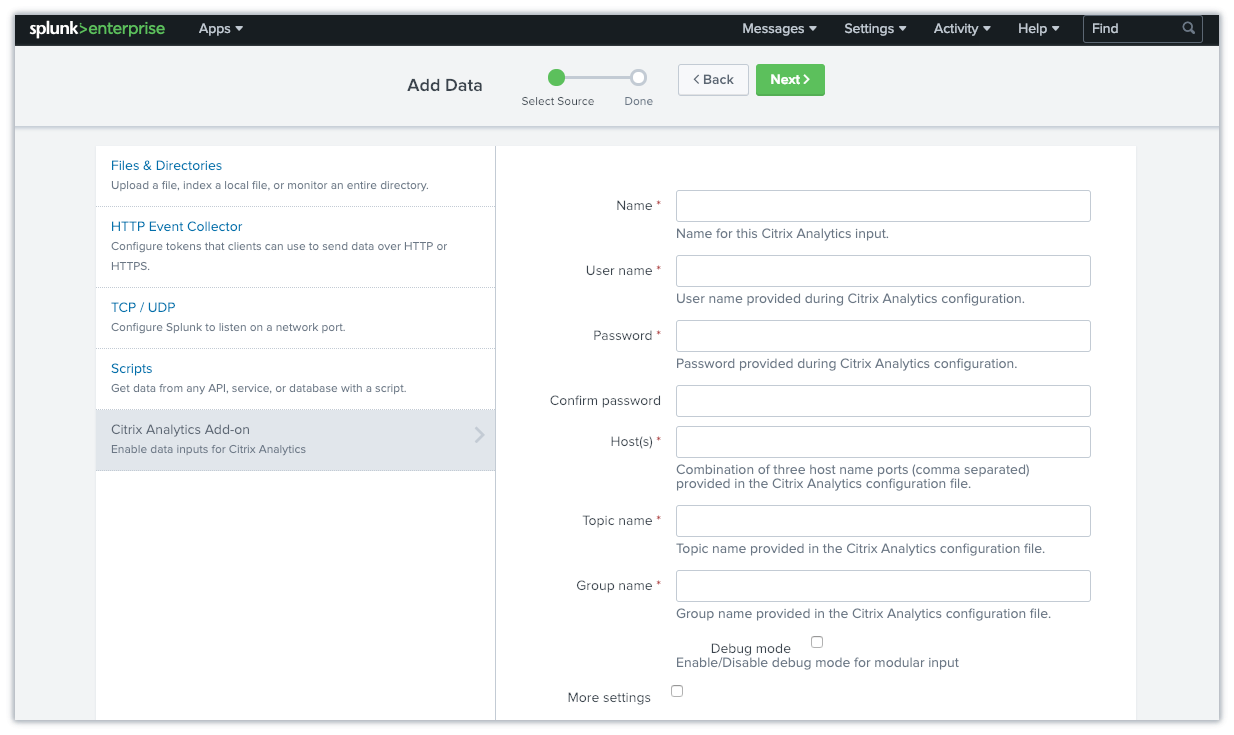
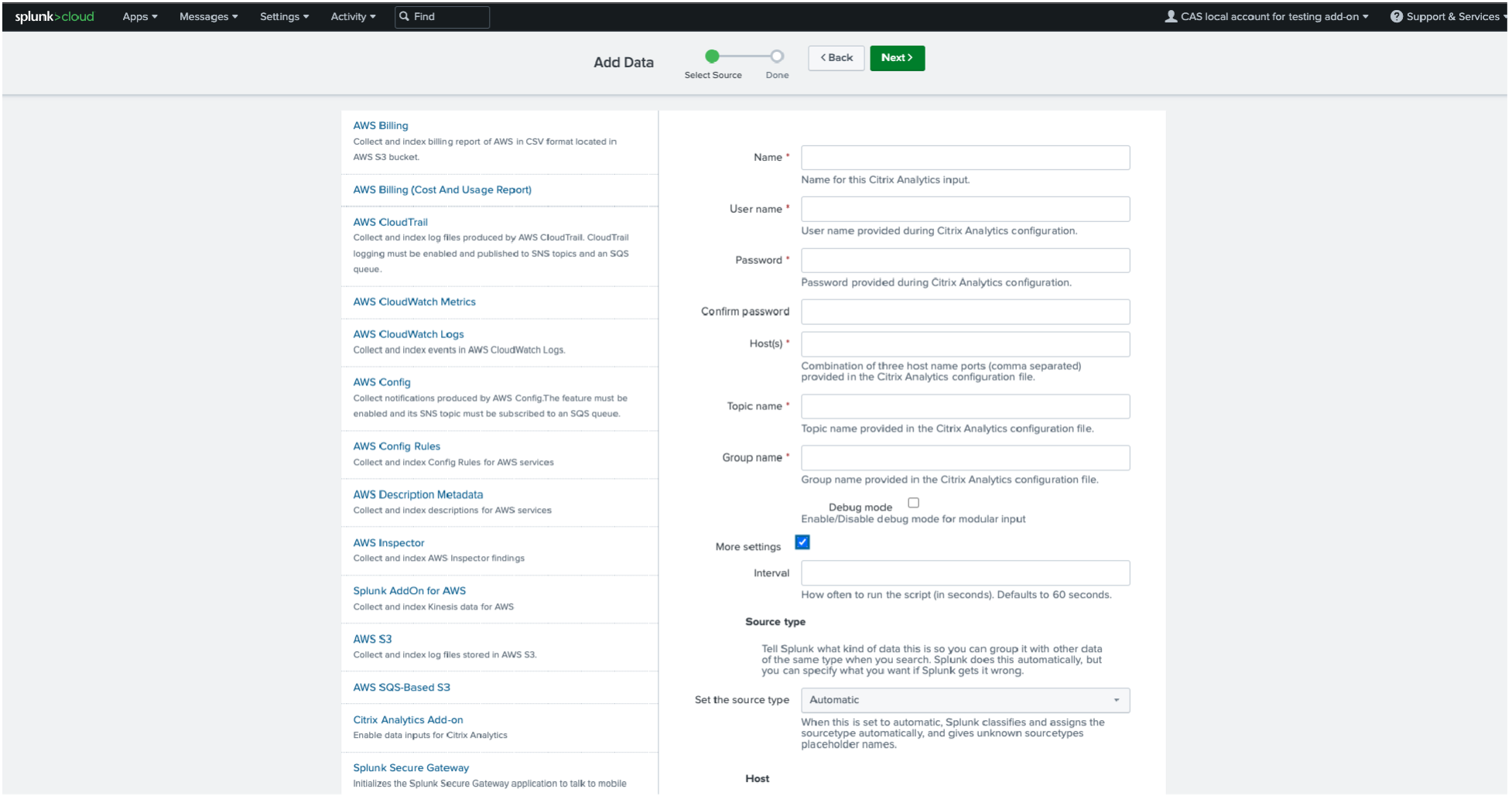
On the Add Data page, enter the details provided in the Citrix Analytics configuration file.
-
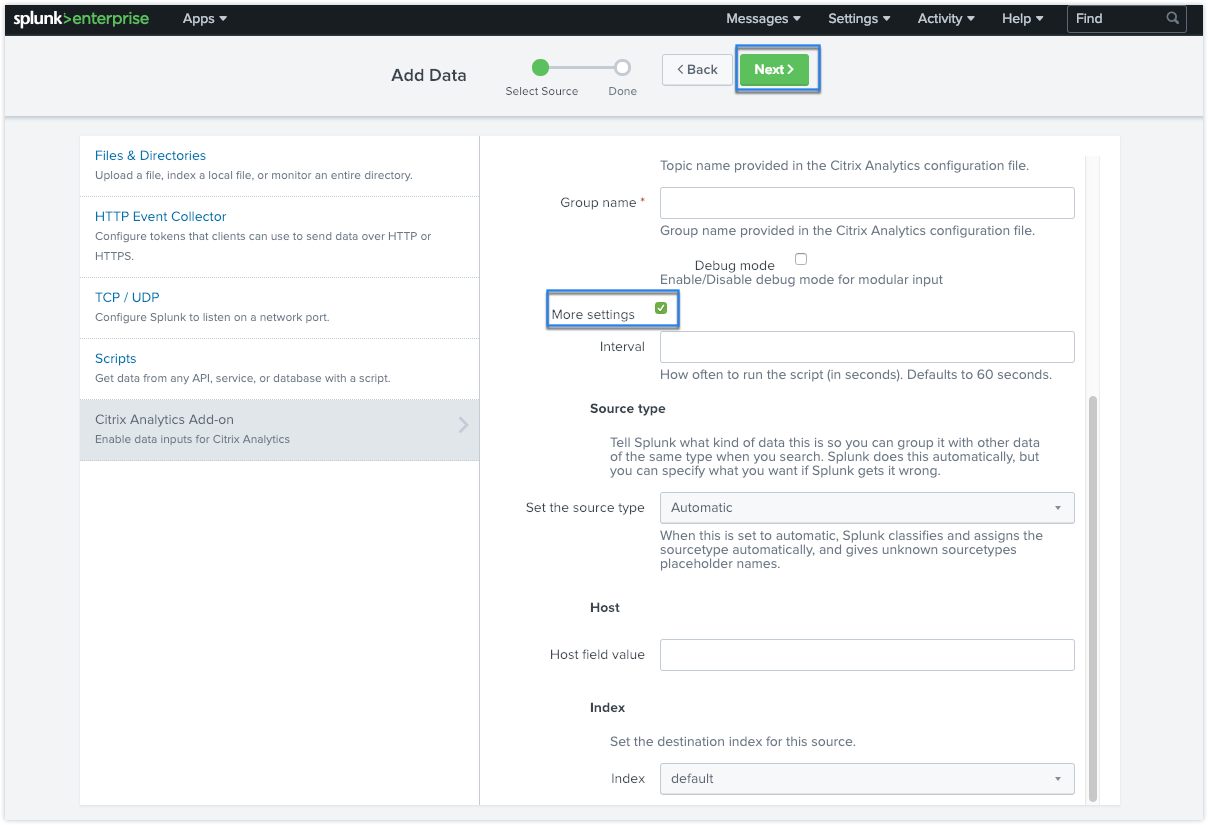
To customize your default settings, click More settings and set up the data input. You can define your own Splunk index, host name, and source type.
-
Click Next. Your Citrix Analytics data input is created and the Citrix Analytics add-on for Splunk is configured successfully.
Citrix Analytics Add-On for Splunk (Cloud)
You can configure our Splunk integration on the following Splunk version: Splunk 8.1 and later.
Prerequisites
The Citrix Analytics add-on for Splunk connects to the following IPs and outbound ports to connect to Citrix Analytics for Security. Ensure that the following IPs and outbound ports (depending upon your Citrix Cloud™ region) are in the allow list in your network. To configure these IPs and outbound ports, refer Add Citrix Analytics IPs and Outbound Ports to Splunk Cloud Allow List using Admin Configuration Service (ACS) section.
| United States region | IP | Outbound Port | European Union region | IP | Outbound Port | Asia Pacific South region | IP | Outbound Port |
|---|---|---|---|---|---|---|---|---|
| casnb-0 citrix.com | 20.242.21.84 | 9094 | casnb-eu-0 citrix.com | 20.229.150.41 | 9094 | casnb-aps-0 citrix.com | 20.211.0.214 | 9094 |
| casnb-1.citrix.com | 20.98.232.61 | 9094 | casnb-eu-1.citrix.com | 20.107.97.59 | 9094 | casnb-aps-1 citrix.com | 20.211.38.102 | 9094 |
| casnb-2.citrix.com | 20.242.21.108 | 9094 | casnb-eu-2.citrix.com | 51.124.223.162 | 9094 | casnb-aps-2 citrix.com | 20.211.36.180 | 9094 |
| casnb-3.citrix.com | 20.242.57.140 | 9094 |
Note
These IPs are subject to rotation. Make sure you keep your IP allow list updated with the most recent IPs as shown above.
Add Citrix Analytics IPs and Outbound Ports to Splunk Cloud Allow List using Admin Configuration Service (ACS)
- Depending upon your Citrix Cloud region, zero in on the IPs must be added in the allow list.
- Enable Admin Configuration Service (ACS) on Splunk Cloud Platform.
- Create token for the allow list using local account with admin privileges.
- Run cURL GET and POST commands to add subnets to the allow list on respective ports and validate if they are successfully added.
- Run cURL GET and POST commands to add outbound ports to the allow list and validate if they are successfully added.
Download and install Citrix Analytics add-on for Splunk
-
Go to Apps > Find more Apps > Search for Citrix Analytics Add-on for Splunk.
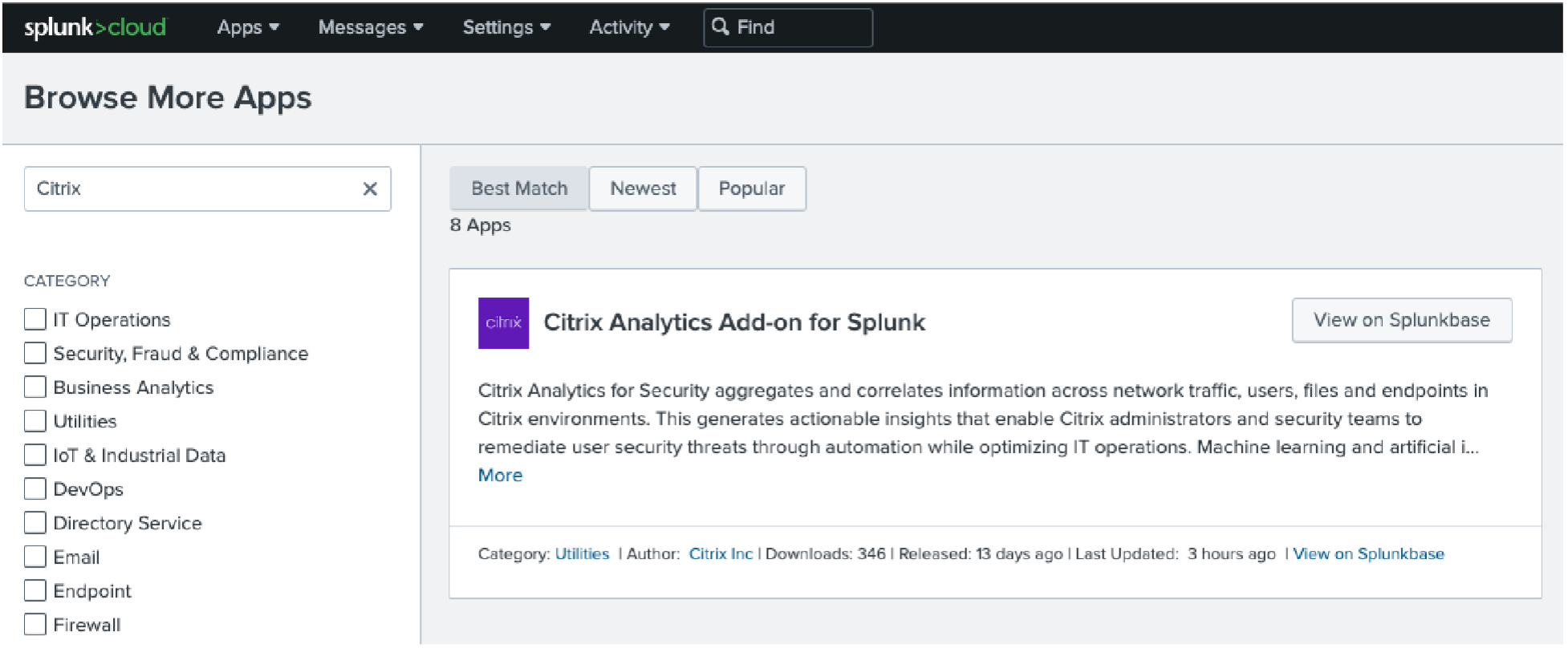
- Install the app.
- Verify that the app appears in the Apps list.
Configure Citrix Analytics add-on for Splunk
-
Go to Settings > Data Inputs > Citrix Analytics Add-on.
-
Add the input: Splunk integration Citrix Analytics for Security. Click Add New. 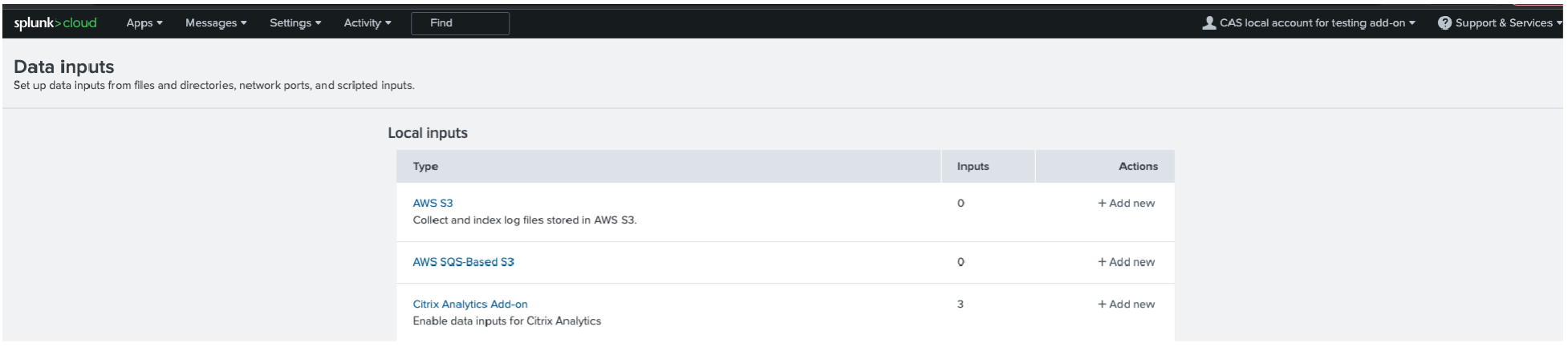
-
Configure Data Input by entering the details configured on Citrix Analytics Data Exports page.
-
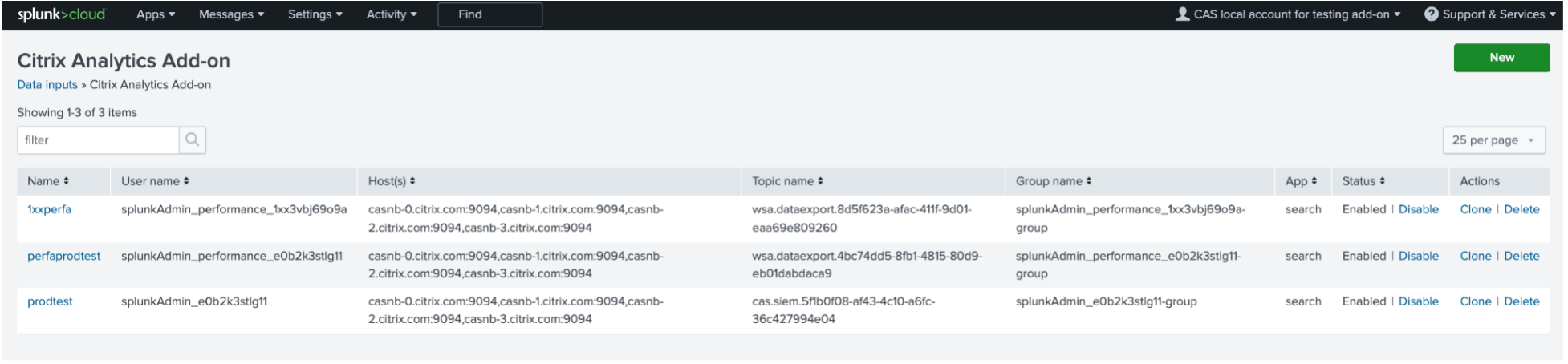
Verify if your data input has successfully been added.
How to consume events in your Splunk Environment
After you configure the add-on, Splunk starts retrieving risk intelligence from Citrix Analytics for Security. You can start searching your organization’s events on the Splunk search head based on the configured data input.
The search results are displayed in the following format:
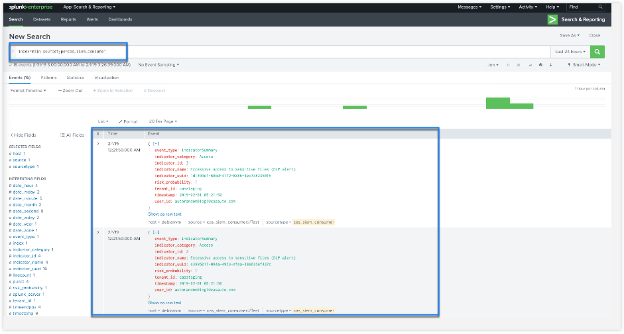
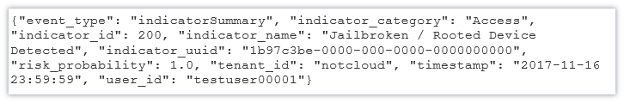
A sample output:
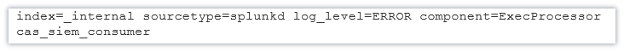
To search and debug issues with the add-on, use the following search query:
The results are displayed in the following format:
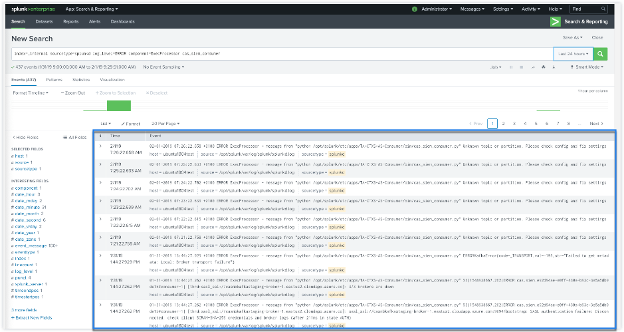
For more information about the data format, see Citrix Analytics data format for SIEM.
Troubleshoot Citrix Analytics add-on for Splunk
If you don’t see any data in your Splunk dashboards or encountered issues while configuring Citrix Analytics add-on for Splunk, perform the debugging steps to fix the issue. For more information, see Configuration issues with Citrix Analytics add-on for Splunk.
Note
Contact CAS-PM-Ext@cloud.com to request assistance for the Splunk integration, exporting data to Splunk, or provide feedback.
Citrix Analytics App for Splunk
Note
This app is in preview.
Citrix Analytics App for Splunk enables Splunk Enterprise administrators to view the user data collected from Citrix Analytics for Security in the form of insightful and actionable dashboards on Splunk. Using these dashboards, you get a detailed view of the users’ risky behavior in your organization and taking timely actions to mitigate any insider threats. You can also correlate the data collected from Citrix Analytics for Security with other data sources configured on your Splunk. This correlation provides you with visibility into the users’ risky activities from multiple sources and takes actions to protect your IT environment.
Supported Splunk version
The Citrix Analytics App for Splunk runs on the following Splunk versions:
-
Splunk 9.0 64-bit
-
Splunk 8.2 64-bit
-
Splunk 8.1 64-bit
Prerequisites for Citrix Analytics App for Splunk
-
Install the Citrix Analytics add-on for Splunk.
-
Ensure the prerequisites mentioned for the Citrix Analytics add-on for Splunk are already met.
-
Ensure that the data is flowing from Citrix Analytics for Security to Splunk.
Installation and configuration
Where to install the app?
Splunk search head
How to install and configure the app?
You can install the Citrix Analytics App for Splunk by downloading it from Splunkbase or by installing it from within Splunk.
Install app from file
-
Go to Splunkbase.
-
Download the Citrix Analytics App for Splunk file.
-
On the Splunk Web home page, click the gear icon next to Apps.
-
Click Install app from file.
-
Locate the downloaded file and click Upload.
Note
If you have an older version of the app, select Upgrade app to overwrite it.
-
Verify that the app appears in the Apps list.
Install app from within Splunk
-
From the Splunk Web home page, click +Find More Apps.
-
On the Browse More Apps page, search Citrix Analytics App for Splunk.
-
Click Install next to the app.
Configure your index and source type to correlate data
-
After you install the app, click Set up now.
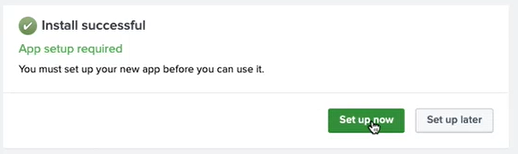
-
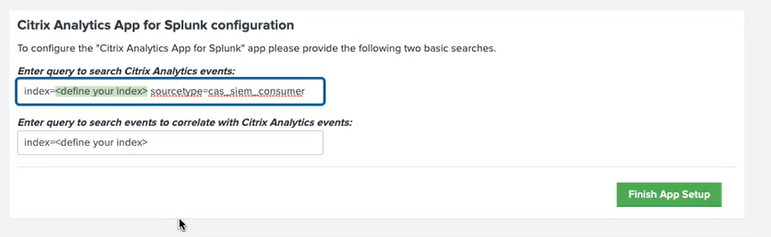
Enter the following queries:
-
Index and source type where the data from Citrix Analytics for Security are stored.
Note
These query values must be the same as specified in the Citrix Analytics add-on for Splunk. For more information, see Configure Citrix Analytics add-on for Splunk.
-
Index from which you want to correlate your data with Citrix Analytics for Security.
-
-
Click Finish App Setup to complete the configuration.
After you have configured and set up the Citrix Analytics App for Splunk, use the Citrix Analytics dashboards to view the user events on your Splunk.
For more information about Splunk integration, refer the following links: