MS Azure Government
When creating layers in Azure Government, use an MS Azure Government connector configuration. This article describes the fields included in the connector configuration. For more about App Layering connectors, see Connector configurations.
A connector configuration contains the credentials that the appliance uses to access a specific location in Azure Government. Your organization may have one Azure Government account and several storage locations. You need a connector configuration for the appliance to access each storage location.
Before you create an Azure Government connector configuration
This section explains:
- The Azure Government account information required to create this connector configuration.
- The Azure Government storage you need for App Layering.
- The servers that the appliance communicates with.
Required Azure account information
The Azure Government connector requires the same information as the Azure connector.
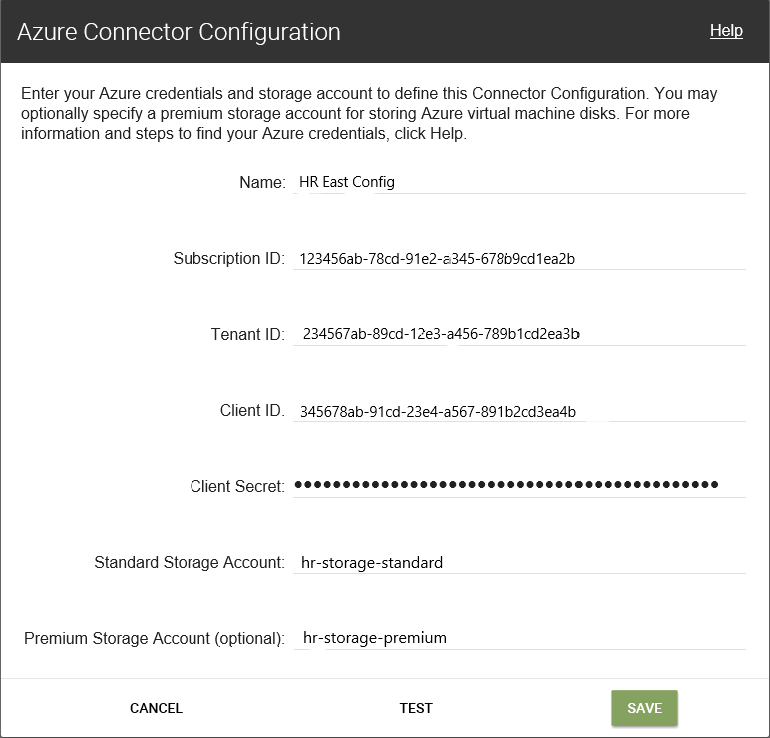
- Name - A name you use for a new connector configuration.
- Subscription ID - To deploy Azure virtual machines, your organization must have a subscription ID.
- Tenant ID - An Azure Active Directory instance, this GUID identifies your organization’s dedicated instance of Azure Active Directory (AD).
- Client ID - An identifier for the App Registration, which your organization has created for App Layering.
- Client Secret - The password for the Client ID you are using. If you have forgotten the Client Secret, you can create a new one. Note: Client secrets are logically associated with Azure tenants, so each time you use a new subscription and Tenant ID, you must use a new Client Secret.
-
Standard Azure storage (required): A storage account for Azure virtual machines (VHD files), the template file that you use to deploy Azure virtual machines, and the boot diagnostics files for those machines. When you specify Premium storage, which is optional, the virtual machines are stored there, and the template and boot diagnostics files remain in Standard storage.
The storage account must already have been created in the Azure government portal, and the name you enter must match the name in the portal. For details, see Set up the necessary storage accounts below.
-
Premium storage (optional): More storage for Azure virtual machines (VHD files). Premium storage only supports page blobs. You cannot use premium storage to store the template file for deploying Azure virtual machines, nor the boot diagnostics files for those virtual machines. When you specify a premium storage account, the virtual machine sizes available are limited to those that support premium storage.
The storage account must already have been created in the Azure government portal, and the name you enter must match the name in the portal. For details, see Set up the necessary storage accounts later in this article.
Required Azure government storage account
Any account you use for App Layering must meet the following requirements:
- Must not be a classic storage account.
- Must be separate from the storage account used for the appliance.
- Must be in the Azure government location where you plan to deploy virtual machines.
- Can be located in any resource group, as long as the resource group’s location is the same as the account’s location.
Required Standard storage account
One of the following types of Standard Azure Government) storage accounts is required to create a connector configuration.
- Standard Locally Redundant storage (LRS)
- Standard Geo-Redundant storage (GRS)
- Standard Read-Access Geo-Redundant storage (RAGRS)
When creating the required Standard Storage, enable Blob Public Access for this account. Otherwise, attempts to publish images fail with the error:
"A failure occurred while creating a storage container in the Azure storage account: Public access is not permitted on this storage account."
Premium storage account
In addition to the required Standard account, you can use Premium storage to store your App Layering virtual machine disks.
Servers that the appliance communicates with
Using this connector, the appliance communicates with the following servers:
- login.microsoftonline.us
- management.usgovcloudapi.net
- management.core.usgovcloudapi.net
- portal.azure.us/#create/Microsoft.Template/uri/
- blob.core.usgovcloudapi.net
The appliance requires network connections with these servers.
Set up your Azure Government subscription
Use the following procedures for each Azure Government subscription that you want to connect with the App Layering appliance.
Set up and retrieve your Azure Government credentials
When adding a new MS Azure Government connector configuration, retrieve your Azure Government credentials as follows:
- Identify your Azure Government Subscription ID.
- Create an App Registration in Azure Government Active Directory.
- Retrieve the Azure Government Tenant ID, Client ID, and Client Secret from the App Registration.
- Create a new storage account, or use an existing one inside the subscription.
Identify the correct Azure Government Subscription ID
- Go to the Azure Government portal.
- Click Subscriptions, and find the subscription you need in the list.
- Select and copy the Subscription ID, and paste it into the connector configuration Subscription ID field.
Create an app registration for each Azure Government subscription
You can use one Azure Government subscription for multiple Azure connector configurations. Each subscription that you want to use for your App Layering connector configurations requires an app registration.
To create an app registration:
- Log into the Azure Government portal.
- Click Azure Active Directory. If Azure Active Directory isn’t listed, click More Services and search for Azure Government Active Directory.
- On the left under Manage, select App registrations.
- At the top of the page, click New registration. A form appears.
- In the Name field, type a descriptive name, such as “Citrix App Layering access”.
- For Supported account types, select Accounts in this organizational directory only (My Company only - Single tenant).
- For Redirect URL, type
https://myapp.com/auth. - Click Register.
- In the list of App registrations, click the new app registration that you created in the preceding procedure.
- In the new window that appears, the Application ID appears near the top. Enter this value into the Client ID box in the connector configuration you are creating.
- Scroll right to see the application properties, including the Display name, Application ID, and other values.
- Copy the Directory (tenant) ID value and paste it into the Tenant ID field in the connector configuration.
- In the left column under Manage click Certificates and Secrets.
- Add a new client secret for the App Layering application, with a description such as “App Layering Key 1”.
- Type the value for the new Client Secret into the connector configuration.
Note:
This key does not appear again after you close this window. This key is sensitive information. Treat the key like a password that allows administrative access to your Azure Government subscription. Open the settings of the app registration you just created in Azure Government Active Directory > App registrations > [name you just entered] > Settings > Properties.
- Go back to Azure Home, and click Subscriptions. If Subscriptions isn’t listed, click More Services to locate it.
- Click the subscription you are using for this connector.
- In the left panel click Access Control (IAM).
- On the top bar of the Access control panel, click Add and select Add role assignment.
- The Add role assignment form appears on the right. Click the drop-down menu for Role and select Contributor.
- In the Select field, type “Citrix App Layering access” or use the name you entered for the Application registration.
- Click the Save button at the bottom of the form.
You have now set up an Azure Government app registration that has read/write access to your Azure Government subscription.
Set up the necessary Storage Account(s)
The Azure Government storage account(s) are where the App Layering software stores all images imported from and published to Azure Government (virtual hard disks, or VHDs), along with the template file that you use to deploy Azure Government virtual machines, and the boot diagnostics files for those machines.
You can use an existing storage account. It must meet these requirements:
- It is not a classic storage account.
- It is in the same subscription used in the connector configuration.
In the App Layering Azure connector configuration, enter the storage account name in the Standard Storage Account field.
If you don’t have a storage account, create a standard storage account. Connector configurations require a standard account, though you can also specify a second storage account that is premium.
- On the Azure home page, click Storage accounts.
- In the Storage accounts window, click Add.
- In the Subscription field, select the subscription you are using.
- In the Resource group field, select Create New and enter a name similar to the name of the Storage account.
- In Storage account name field, enter a name that you’ll remember.
- Select the Location.
- In the Performance field, if this is the only storage location for this connector configuration, select Standard. Otherwise, choose the best type for your needs.
- In the Account kind field, select general purpose v2 or general purpose v1.
- In the Replication field, select the type you need.
- For the Access tier (default), select Hot or Cold.
- Click Next: Networking, and select the connectivity method.
- Complete the remaining options under Networking, Advanced, and Tags.
- Select Review + Create.
- Finally, enter the new Storage account name in the connector configuration you are creating.
What to do if your Azure Government Client Secret is lost
You can generate a new Azure Client Secret using the Certificates and Secrets. For details, see the steps in the Create an app registration for each Azure subscription section earlier in this article.
Add a Connector Configuration
When all requirements are ready, create an Azure Government connector configuration:
- Click the Connectors page.
- Click Add Connector Configuration to open a dialog box.
- Select the Connector Type for the platform and location where you are creating the Layer or publishing the image. Then click New to open the Connector Configuration page.
- Complete the fields on the Connector Configuration page. For guidance, see the field definitions.
- Click the TEST button to verify that the appliance can access the location specified using the credentials supplied.
- Click Save. The new Connector Configuration appears on the Connector tab.
Azure Government data structure (Reference)
The Azure Government data structure is as follows:
Tenant
- Tenant ID
- App Registration
- Client ID
- Client Secret
- Subscription
- Subscription ID
- Storage Account
- Storage Account Name
- Storage Account
where:
- Tenant is your Azure Government Active Directory instance that users and applications can use to access Azure Government. The Tenant is identified by your Tenant ID. A Tenant can have access to one or more Azure Government Subscriptions.
- The Azure Government Active Directory Tenant contains two types of accounts.
- A User Account for logging into the Azure Government portal (portal.azure.us).
- An App Registration for accessing the subscription has a Client ID.
- The Client ID has a Client Secret, instead of a password.
- Users can generate the Client Secret, and delete it.
- An Azure Government Subscription contains everything that can be created in Azure Government, except for user accounts.
- A Subscription contains Storage Accounts. This is where App Layering VHDs are stored. It is identified by a Storage Account Name.