This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Dynamic NAT
Dynamic NAT is a many-to-one mapping of a private IP address or subnets inside the SD-WAN network to a public IP address or subnet outside the SD-WAN network. The traffic from different zones and subnets over trusted (inside) IP addresses in the LAN segment is sent over a single public (outside) IP address.
Dynamic NAT types
Dynamic NAT does Port Address Translation (PAT) along with IP address translation. Port numbers are used to distinguish which traffic belongs to which IP address. A single public IP address is used for all internal private IP addresses, but a different port number is assigned to each private IP address. PAT is a cost effective way to allow multiple hosts to connect to the Internet using a single Public IP address.
- Port Restricted: Port Restricted NAT uses the same outside port for all translations related to an Inside IP Address and Port pair. This mode is typically used to allow Internet P2P applications.
- Symmetric: Symmetric NAT uses the same outside port for all translations related to an Inside IP Address, Inside Port, Outside IP Address, and Outside Port tuple. This mode is typically used to enhance security or expand the maximum number of NAT sessions.
Inbound and Outbound NAT
The direction for a connection can either be inside to outside or outside to inside. When a NAT rule is created, it is applied to both the directions depending on the direction match type.
- Outbound: The destination address is translated for packets received on the service. The source address is translated for packets transmitted on the service. Outbound dynamic NAT is supported on Local, Internet, Intranet, and Inter-routing domain services. For WAN services such as Internet and Intranet services, the configured WAN link IP address is dynamically chosen as the outside IP address. For Local and Inter-routing domain services, provide an outside IP address. The Outside zone is derived from the selected service. A typical use case of outbound dynamic NAT is to simultaneously allow multiple users in your LAN to securely access the internet using a single Public IP address.
- Inbound: The source address is translated for packets received on the service. The destination address is translated for packets transmitted on the service. Inbound dynamic NAT is not supported on WAN services such as Internet and Intranet. There is an explicit audit error to indicate the same. Inbound dynamic NAT is supported on Local and Inter-routing domain services only. Provide an outside zone and outside IP address to be translated to. A typical use case for inbound dynamic NAT is to allow external users access email or web servers hosted in your private network.
Port Forwarding
Dynamic NAT with port forwarding allows you to port forward specific traffic to a defined IP address. This is typically used for inside hosts like web servers. Once the dynamic NAT is configured you can define the port forwarding policies. Configure dynamic NAT for IP address translation and define the port forwarding policy to map an outside port to an inside port. Dynamic NAT port forwarding is typically used to allow remote hosts to connect to a host or server on your private network. For a more detailed use case see, Citrix SD-WAN Dynamic NAT explained.
Auto-created Dynamic NAT policies
Dynamic NAT policies for the Internet service are auto created in the following cases:
- Configuring internet service on an untrusted interface (WAN link).
- Enabling internet access for all routing domains on a single WAN link using Citrix SD-WAN Orchestrator service. For more details, see Configure firewall segmentation.
- Configuring DNS forwarders or DNS proxy on SD-WAN Orchestrator service. For more details, see Domain name system.
Monitoring
To monitor dynamic NAT, navigate to Monitoring > Firewall Statistics > Connections. For a connection you can see if NAT is done or not.
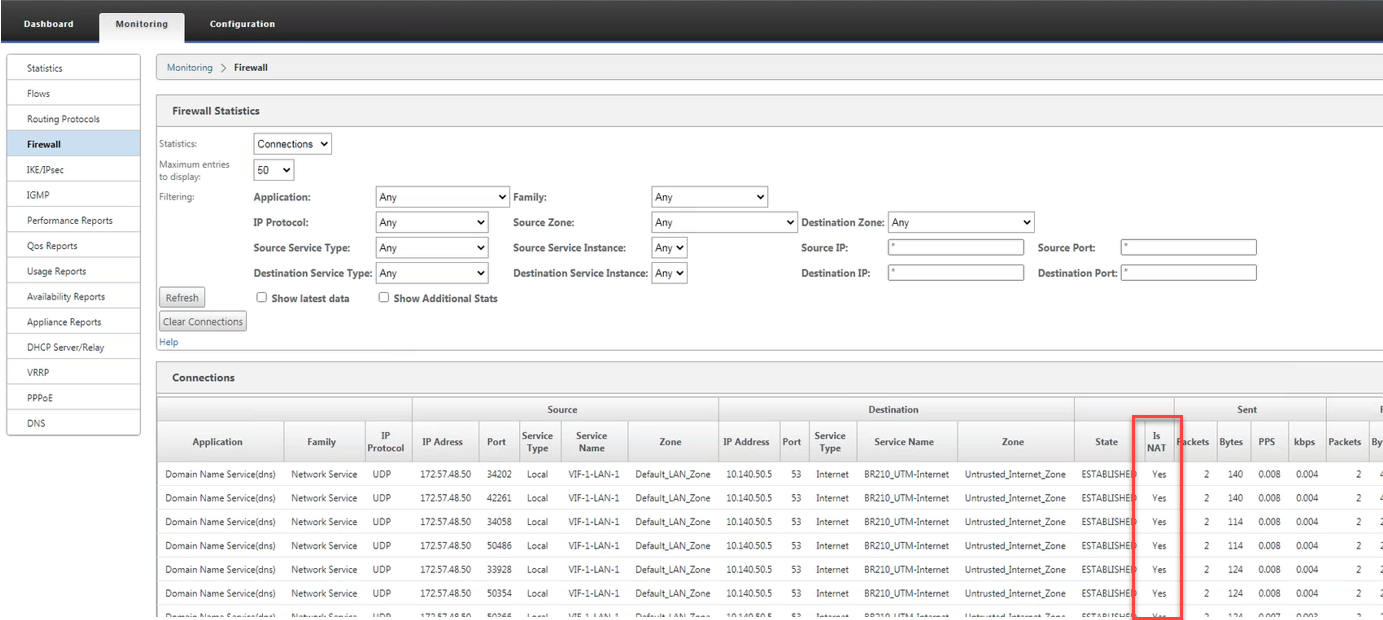
To further see the inside IP address to outside IP address mapping, click Pre-Route NAT or Post-route NAT under Related Objects or navigate to Monitoring > Firewall Statistics > NAT policies.
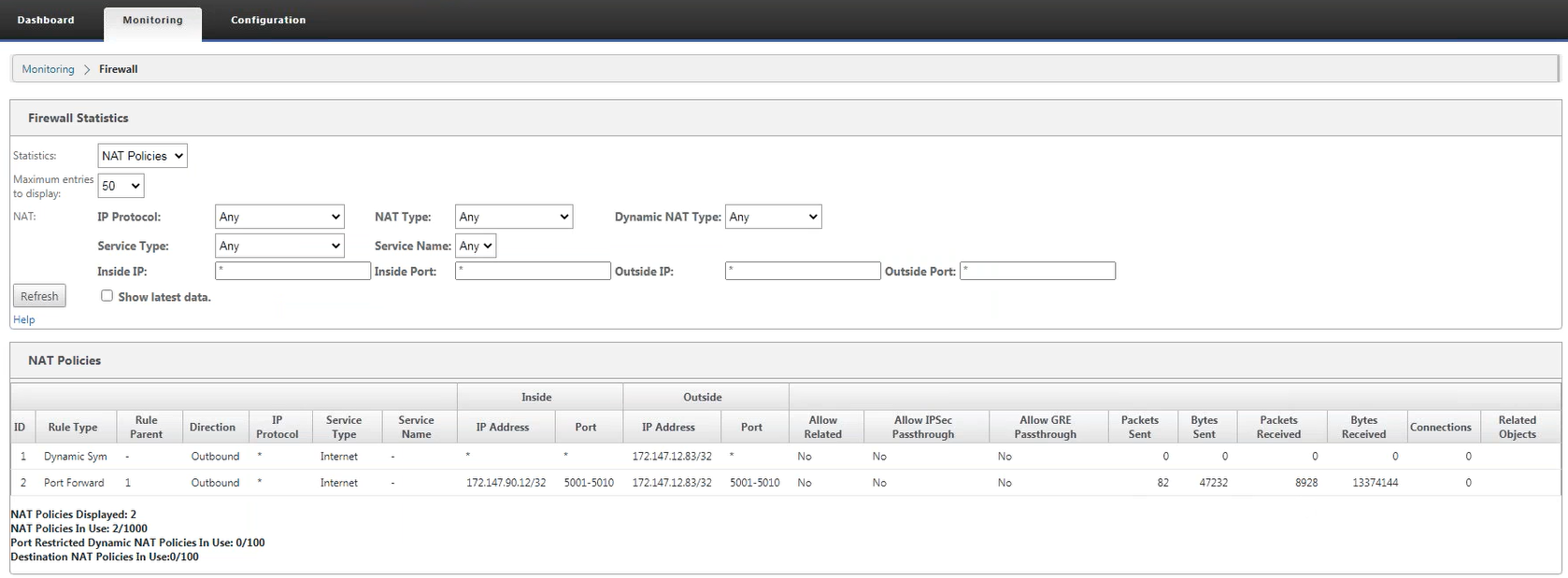
The following screenshot shows the statistics for the Dynamic NAT rule of type symmetric and its corresponding port forwarding rule.
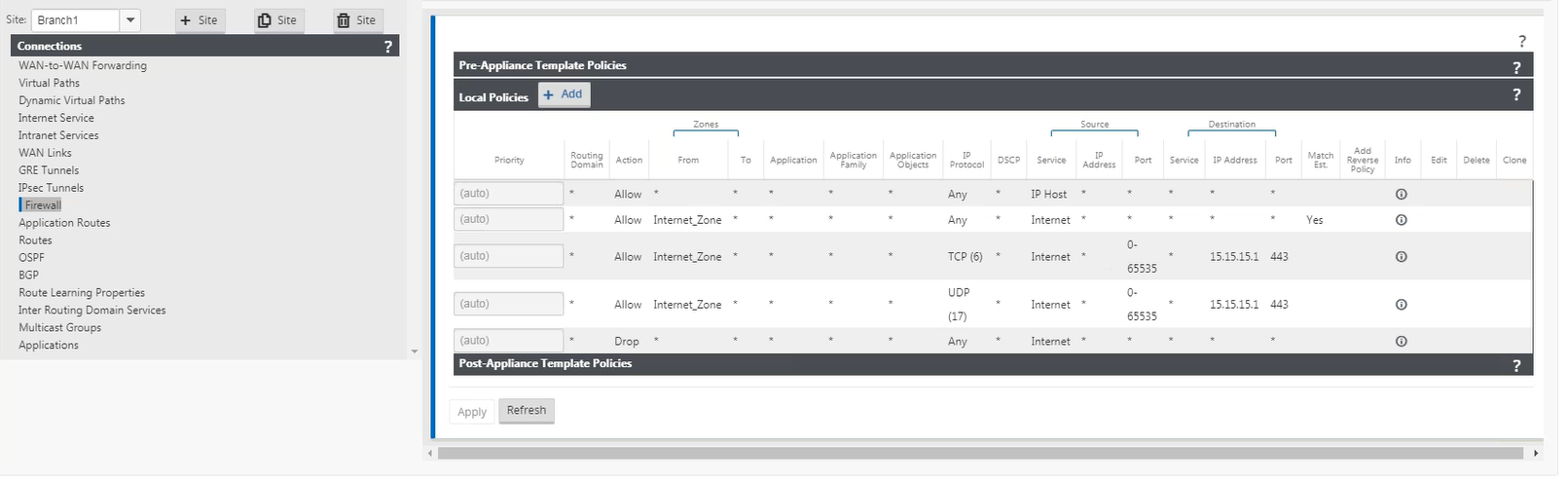
When a port forwarding rule is created a corresponding firewall rule is also created.
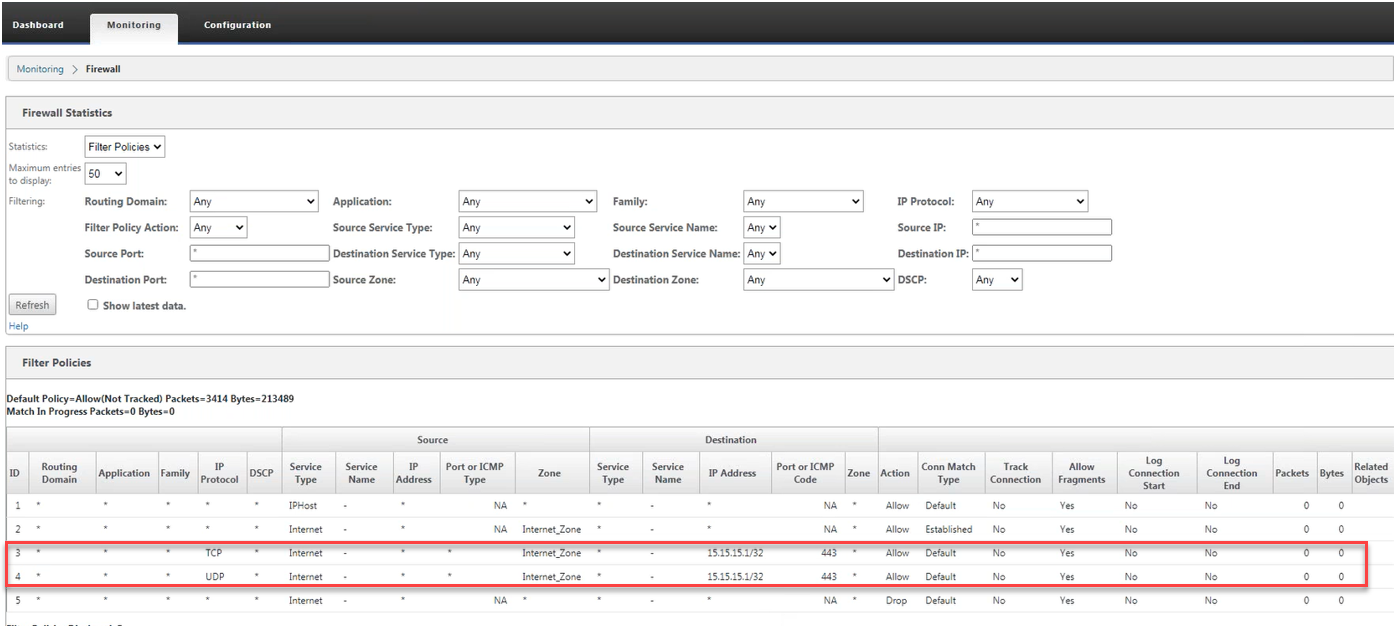
You can see the filter policy statistics by navigating to Monitoring > Firewall Statistics > Filter Policies.
Logs
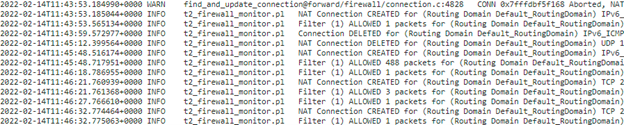
You can view logs related to NAT in firewall logs. To view logs for NAT, create a firewall policy that matches your NAT policy and ensure that logging is enabled on the firewall filter. NAT logs contain the following information:
- Date and time
- Routing domain
- IP protocol
- Source port
- Source IP address
- Translated IP address
- Translated port
- Destination IP address
- Destination port
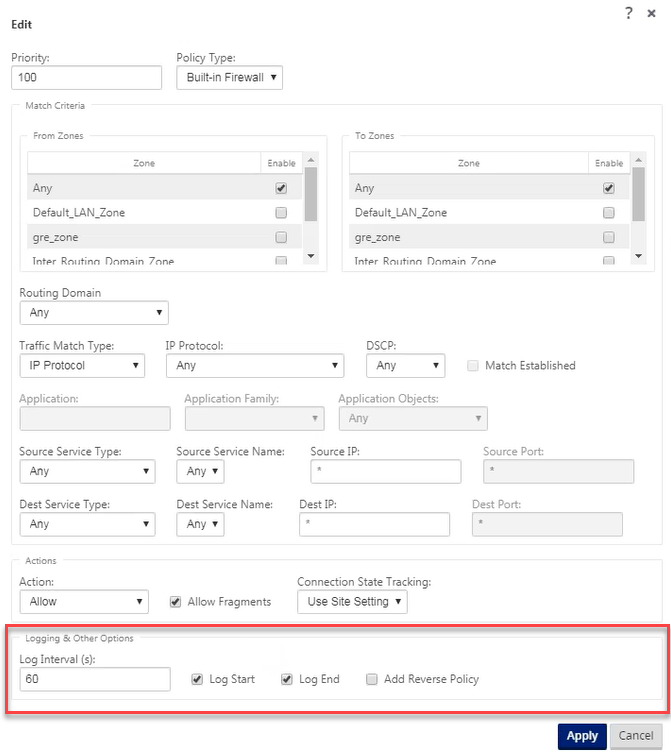
To generate NAT logs, navigate to Logging/Monitoring > Log Options, select SDWAN_firewall.log, and click View Log.
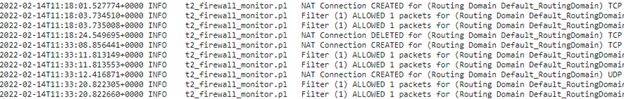
The NAT connection details are displayed in the log file.
Share
Share
This Preview product documentation is Cloud Software Group Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Cloud Software Group Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Cloud Software Group product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.