CrowdStrike integration with Device Posture
CrowdStrike Zero Trust Assessment (ZTA) delivers security posture assessments by calculating a ZTA security score from 1 to 100 for each end device. A higher ZTA score means that the posture of the end device is better.
Citrix Device Posture Service can enable contextual access (Smart Access) to Citrix Desktop as a Service (DaaS) and Citrix Secure Private Access (SPA) resources by using the ZTA score of an end device.
Device Posture administrators can use ZTA score as part of policies and classify the end devices as compliant, non-compliant (partial access), or even deny access. This classification can in turn be used by organizations to provide contextual access (Smart Access) to virtual apps and desktops, and SaaS and Web Apps. ZTA score policies are supported for Windows and macOS platforms.
Configure CrowdStrike integration
CrowdStrike integration configuration is a two-step process.
Step1: Establish trust between Citrix Device Posture service and CrowdStrike ZTA service. This is a one-time activity.
Step 2: Configure policies to use the CrowdStrike ZTA score as a rule to provide smart access to Citrix DaaS and Citrix Secure Private Access resources.
Step 1: Establish trust between Citrix Device Posture service and CrowdStrike ZTA service
Perform the following to establish trust between Citrix Device Posture service and CrowdStrike ZTA service.
- Sign into Citrix Cloud, and then select Identity and Access Management from the hamburger menu.
- Click the Device Posture tab, and then click Manage.
-
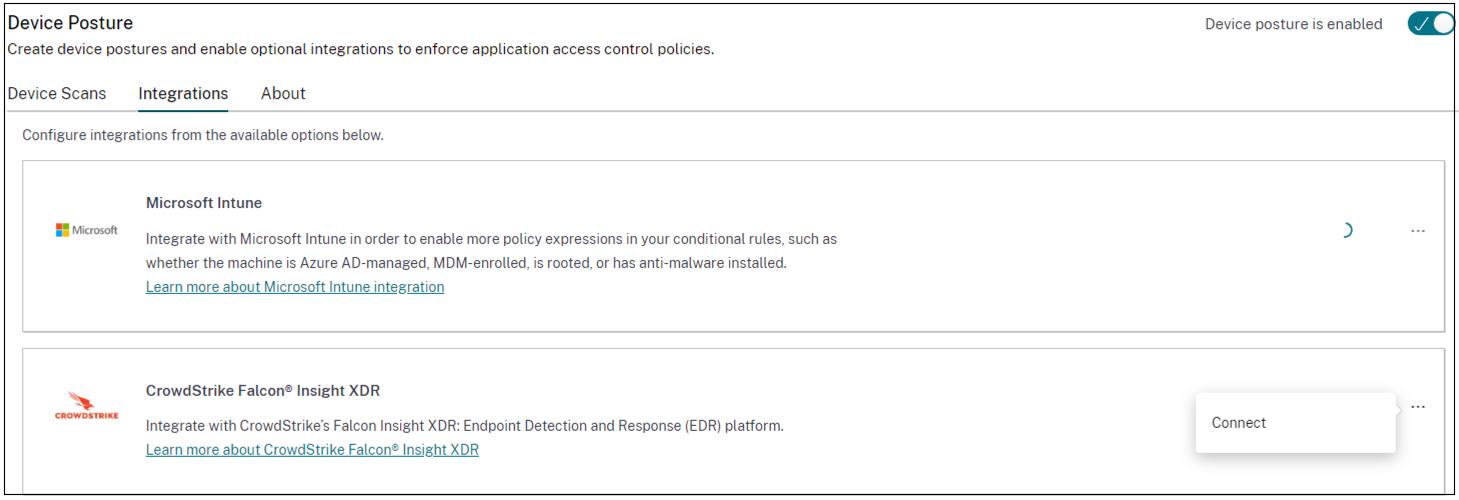
Click the Integrations tab.
Note:
Alternatively, customers can navigate to the Device Posture option on the left navigation pane of the Secure Private Access service GUI, and then click the Integrations tab.
- Click the ellipsis button in the CrowdStrike box, and then click Connect. The CrowdStrike Falcon Insight XDR integration pane appears.
-
Enter the client ID and client secret and then click Save.
Note:
- You can obtain the ZTA API client ID and client secret from the CrowdStrike portal (Support and resources > API clients and keys).
- Ensure that you select the Zero Trust Assessment and Host scopes with read permissions for establishing the trust.
The integration is considered successful after the status changes from Not Configured to Configured.
If the integration is not successful, the status appears as Pending. You must click the ellipsis button, and then click Reconnect.
Step 2: Configure device posture policies
Perform the following to configure policies to use the CrowdStrike ZTA score as a rule to provide smart access to Citrix DaaS and Citrix Secure Private Access resources.
-
Click the Device Scans tab and then click Create device policy.
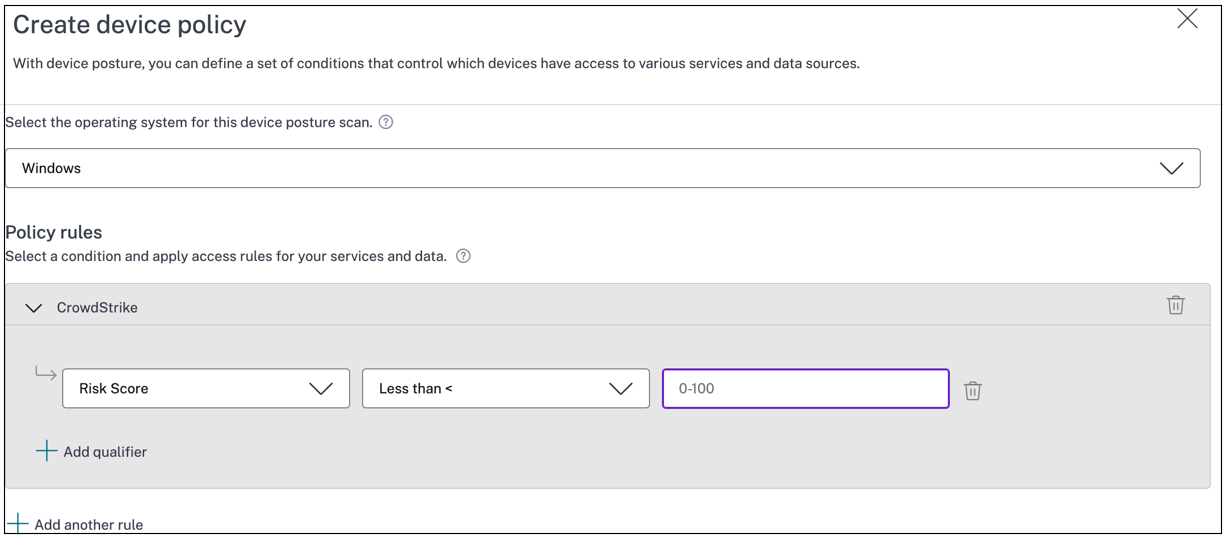
- Select the platform for which this policy is created.
- In Policy Rule, select CrowdStrike.
- For the Risk Score qualifier, select the condition, and then enter the risk score.
-
Click + to add a qualifier that checks if the CrowdStrike Falcon sensor is running.
Note:
You can use this rule with other rules that you configure for device posture.
-
In Policy result based on the conditions that you have configured, select one of the following.
- Compliant
- Non-compliant
- Denied login
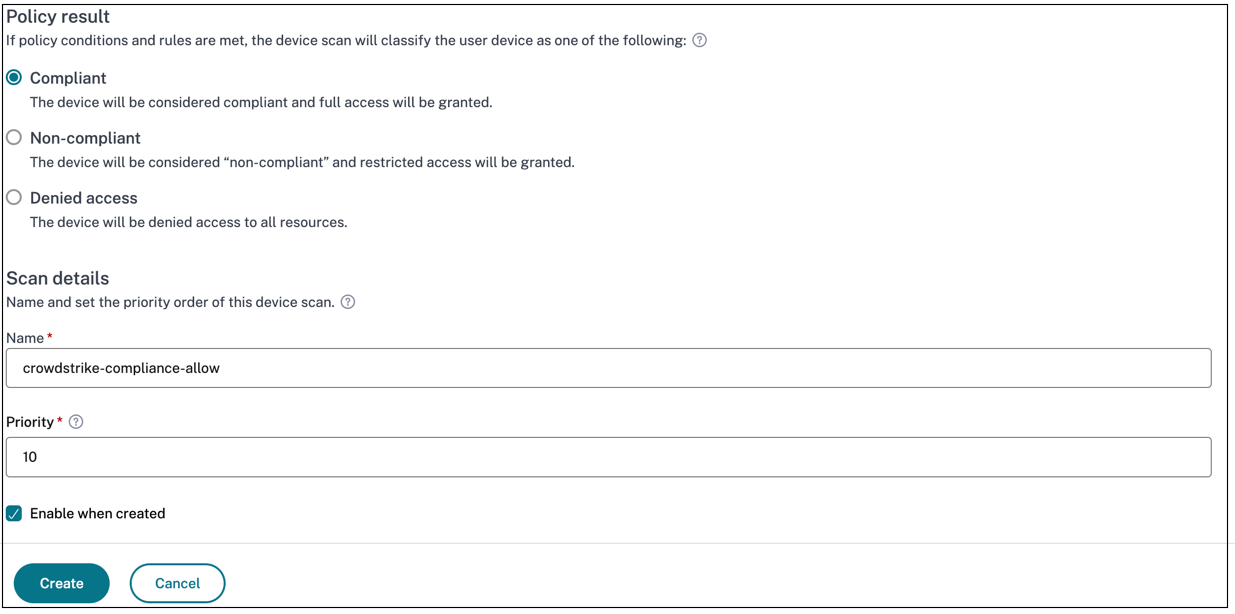
- Enter the name for the policy and set the priority.
- Click Create.
Definitions
The terms compliant and non-compliant in reference to the Device Posture service are defined as follows.
- Compliant devices – A device that meets the pre-configured policy requirements and is allowed to log in into the company’s network with full or unrestricted access to Citrix Secure Private Access resources or Citrix DaaS resources.
- Non-Compliant devices - A device that meets the pre-configured policy requirements and is allowed to log in into the company’s network with partial or restricted access to Citrix Secure Private Access resources or Citrix DaaS resources.