Azure Active Directory single sign-on
Citrix Federated Authentication Service (FAS) provides single sign-on (SSO) to domain-joined Virtual Delivery Agents (VDAs). FAS achieves SSO by supplying the VDA with a user certificate, which the VDA uses to authenticate the user to Active Directory (AD). Once you sign on to the VDA session, you can access AD resources without reauthentication.
It’s common to implement Azure Active Directory (AAD) with synchronization between your AD and AAD, which creates hybrid identities for both users and computers. This article describes the additional configuration required to achieve SSO to AAD from within your VDA session when using FAS, which allows the user to access AAD-protected applications without reauthentication.
Note:
- You don’t require any special configuration for FAS to use SSO for AAD.
- You don’t require the FAS in-session certificates.
- You can use any version of FAS.
- You can use any version of the VDA that supports FAS.
The techniques for AAD SSO are summarized in the following table:
| AAD authentication type | VDA is domain joined | VDA is hybrid joined |
|---|---|---|
| Managed | Use AAD seamless SSO | Use AAD Certificate Based Authentication |
| Federated to Active Directory Federation Services (ADFS) | Enable Windows Authentication at ADFS | Ensure that the WS-Trust certificatemixed endpoint is enabled |
| Federated to a third party identity provider | Use a third party solution | Use a third party solution |
-
A managed AAD domain is one where the user authentication happens at AAD, sometimes referred to as native AAD authentication.
-
A federated AAD domain is one where AAD is configured to redirect authentication elsewhere. For example, to ADFS or to a third party identity provider.
-
A hybrid joined VDA is AD joined and AAD joined.
Domain-joined VDAs
For domain-joined VDAs, achieve SSO to AAD using Windows Authentication (traditionally called Integrated Windows Authentication, or Kerberos). Authentication to AAD happens when the user accesses an AAD-protected application from within the VDA session. The following diagram shows the authentication process on a high-level:
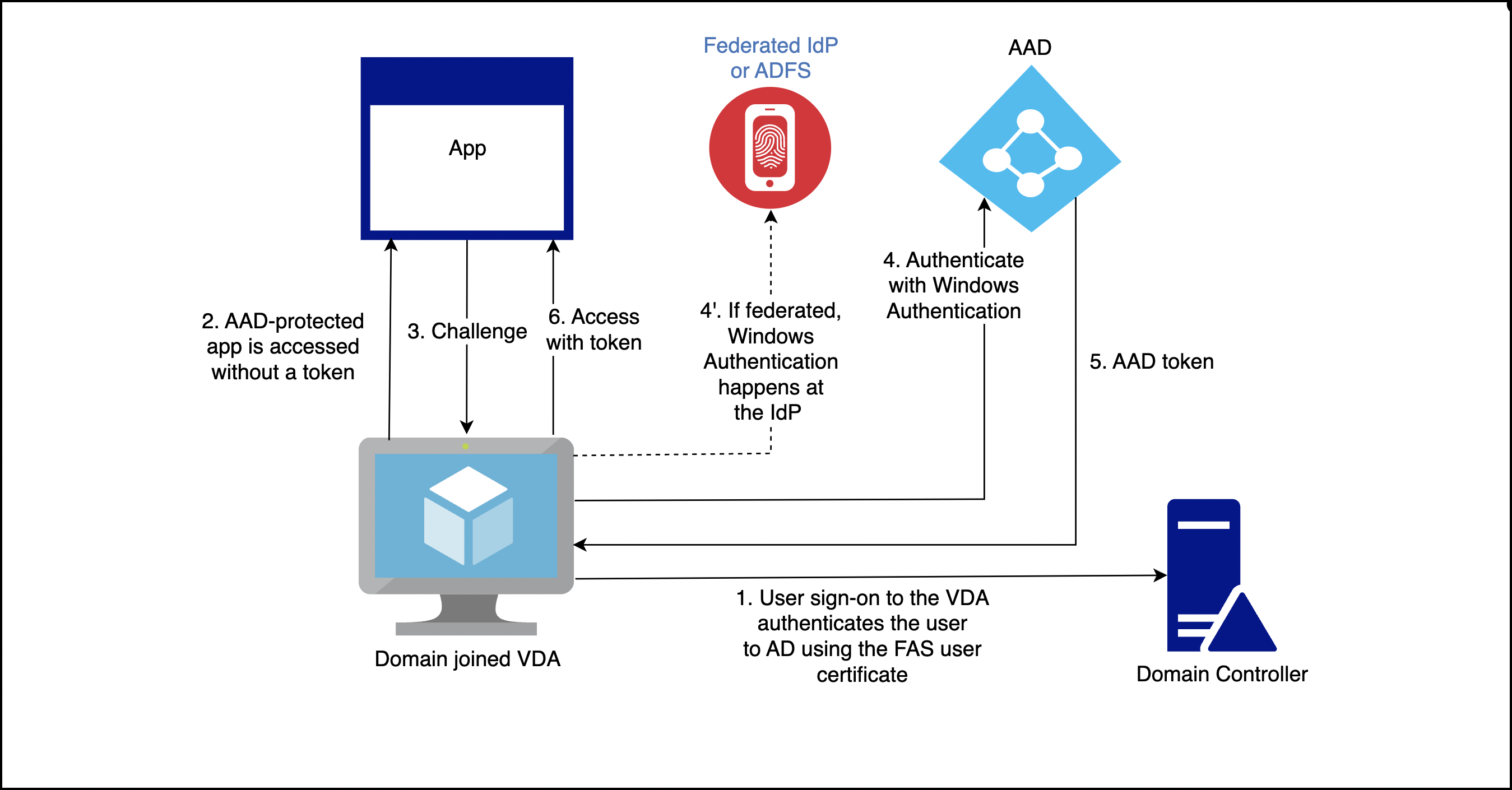
The exact details vary depending on whether the AAD domain is managed or federated.
For information on the managed AAD domain setup, see Seamless single sign-on.
For an AAD domain federated to ADFS, enable Windows Authentication at the ADFS server.
For an AAD domain federated to a third party identity provider, a similar solution exists. Contact your identity provider for help.
Note:
You can also use the solutions listed for the domain-joined VDAs for hybrid-joined VDAs. But an AAD Primary Refresh Token (PRT) isn’t generated when using FAS.
Hybrid-joined VDAs
Hybrid-joined VDAs are joined to AD and AAD at the same time. When the user signs in to the VDA, the following artifacts are created:
- A Kerberos Ticket Granting Ticket (TGT), to authenticate to AD resources
- A Primary Refresh Token (PRT), to authenticate to AAD resources
The PRT contains information about both the user and the computer. This information is used in an AAD conditional access policy if necessary.
Since FAS authenticates the user by supplying a certificate to the VDA, a PRT can only be created if certificate-based authentication for AAD is implemented. The following diagram shows the authentication process on a high-level:
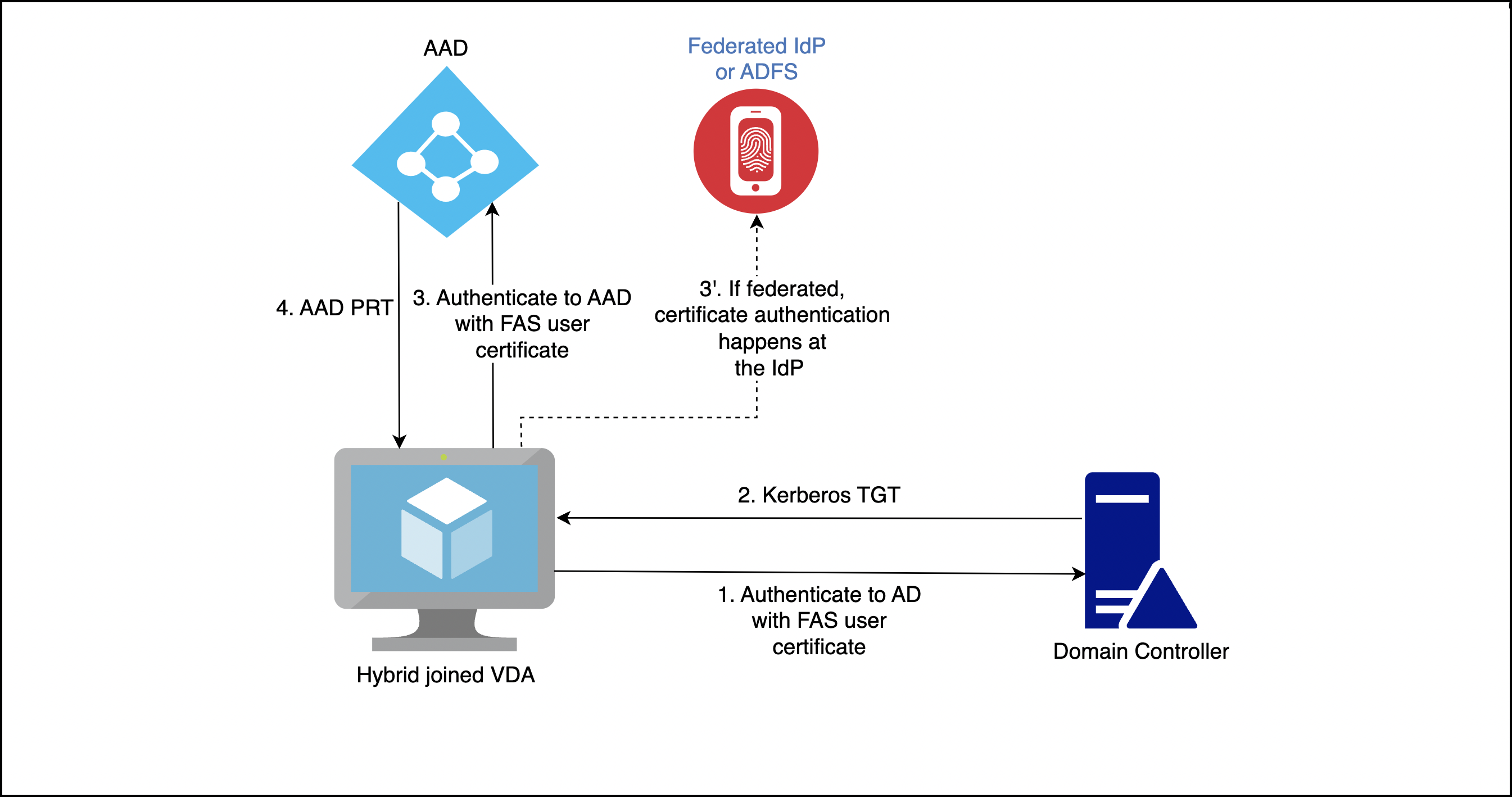
The exact details vary depending on whether the AAD domain is managed or federated.
For a managed AAD domain, configure AAD CBA. For more information, see Overview of Azure AD certificate-based authentication. The VDA uses AAD CBA to authenticate the user to AAD with the user’s FAS certificate.
Note:
The Microsoft documentation describes sign in with a smart card certificate, but the underlying technique applies when signing in to with a FAS user certificate.
For an AAD domain federated to ADFS, the VDA uses the ADFS server’s WS-Trust certificatemixed endpoint to authenticate the user to AAD with the user’s FAS certificate. This endpoint is enabled by default.
For an AAD domain federated to a third party identity provider, a similar solution may exist. The identity provider must implement a WS-Trust certificatemixed endpoint. Contact your identity provider for help.