System requirements
This article provides the system requirements for using the MDX Toolkit to wrap mobile apps. The article also provides the requirements specific to app platforms.
Important:
The XenMobile App SDK 10.2 now requires the following components: JavaScriptCore.framework and LocalAuthentication.framework.
- Java Development Kit (JDK) 1.7 or 1.8: You can download the JDK 1.8 from Java SE Development Kit Downloads on the Oracle website. For installation instructions, see the JDK 8 and JRE 8 Installation Guide on the Oracle website. Be sure to install the full JDK and set JDK 1.8 as the default.
- macOS: Use the most recent version. The installer for the MDX Toolkit and XenMobile® App SDK must run on macOS. The installer includes macOS tools that wrap both iOS and Android apps and a Java command-line tool that wraps Android apps.
- XenMobile App SDK: Use the most recent version of the XenMobile iOS SDK and the Xcode; bitcode generation disabled.
Other requirements for wrapping iOS mobile apps
To obtain access to the app wrapping prerequisites for iOS, you must register for an Apple distribution account. There are three types of iOS developer accounts: Enterprise, Individual, and University. Citrix® strongly recommends iOS Developer Enterprise accounts. The MDX Toolkit is also compatible with iPadOS.
- iOS Developer Enterprise accounts: The only type of Apple Developer account that allows you to provision, deploy, and test unlimited apps to unlimited devices, with or without app wrapping. Be sure to distribute your Developer Certificate to your developers so they can sign apps.
- iOS Developer Individual accounts: Limited to 100 registered devices per year and do not qualify for app wrapping and enterprise distribution with Citrix Endpoint Management.
- iOS Developer University accounts: Limited to 200 registered devices per year and do not qualify for app wrapping and enterprise distribution with Endpoint Management.
Important:
Be sure to track when the provisioning profiles for your account are due to expire and renew the profiles before they expire. When a profile used to wrap apps expires, you must renew the profile, rewrap the apps, and then reinstall the apps on user devices. To renew a provisioning profile, log on to your Apple Developer account, go to Certificates, Identifiers & Profiles, and then select Provisioning Profiles.
Download the Xcode command-line tools from the Xcode Apple Developer website. macOS 10.10 does not install the tools automatically. To install the tools, follow these steps:
-
In Applications > Utilities, click Terminal to use the Mac command line interface (CLI).
-
Type the following command:
xcode-select --install <!--NeedCopy-->Be sure to include two hyphens before the word install in the command.
-
After the Xcode command-line tools install, run Xcode to install any prerequisites.
Other requirements for wrapping Android mobile apps
To wrap Android wraps, you also need a compatible Android software development kit (SDK) and a valid keystore. To download, create, and properly configure the SDK and keystore, follow these instructions:
Android software development kit
The MDX Toolkit is compatible with API Level 26 of the Android SDK.
-
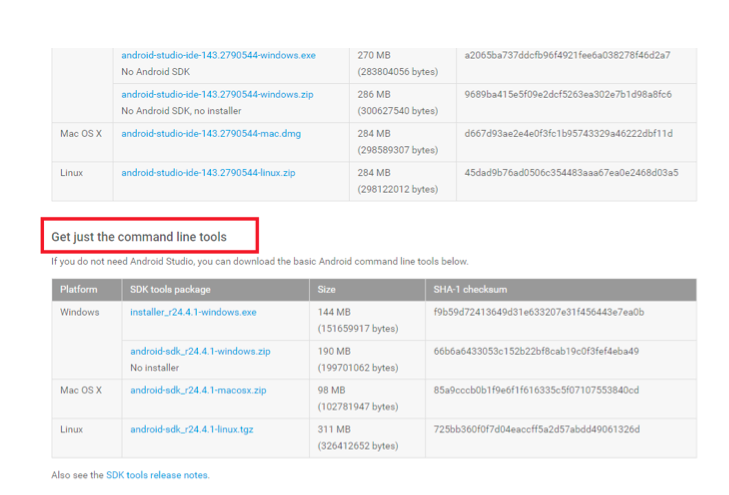
Go to the Google developer website and download the Android SDK from the SDK download page. The full Android Studio is not required. You can download the command-line tools from the section near the bottom of the page.
-
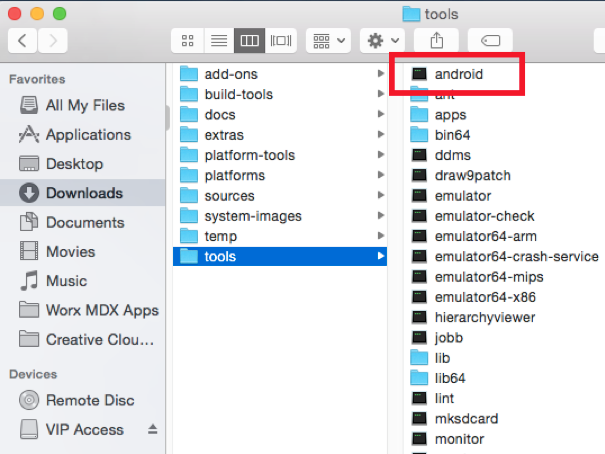
Install the latest tools, platform-tools, and build-tools. This installation requires using the Android tool in Android SDK > tools to start the SDK Manager:
- Unzip the SDK file you downloaded.
- Go to the tools folder and then click Android to run the SDK Manager.
-
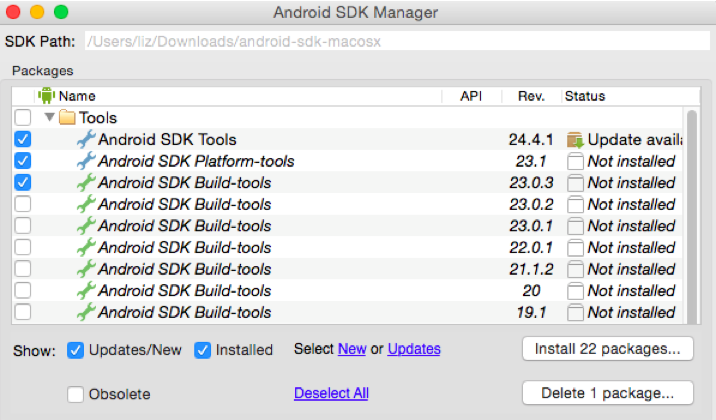
In the SDK Manager, select the latest versions of the following:
- Android SDK Tools
- Android SDK Platform
- Android SDK Platform-tools
- Android SDK Build-tools
-
Click Install Packages.
-
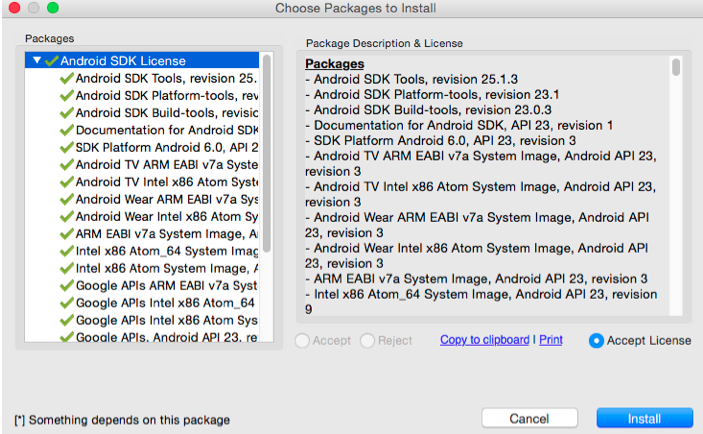
On the Choose Packages to Install screen, click Accept License for all the packages you are installing and then click Install.
-
To verify that you downloaded the appropriate SDK Tools and APIs, check that the .aapt file is in Android SDK > build-tools > 23.0.3.
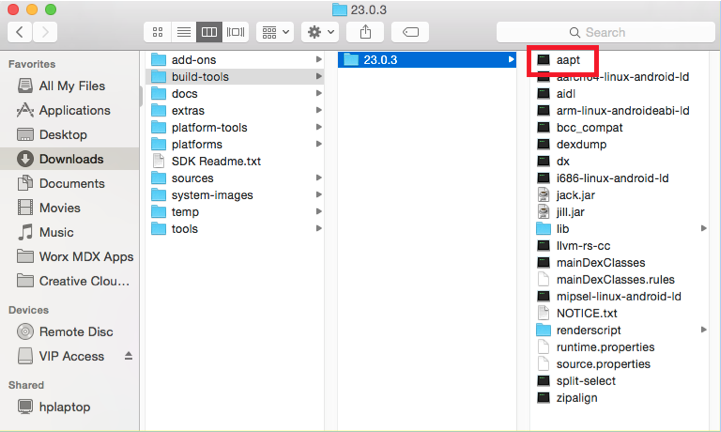
-
When updating your SDK, you have to delete all .aapt files from the platform-tools folder. Ensure that the .aapt file is in build-tools only.
-
If the zipalign file is missing from build-tools, copy the file from the platform-tools folder to the build-tools folder, and then delete it from platform-tools.
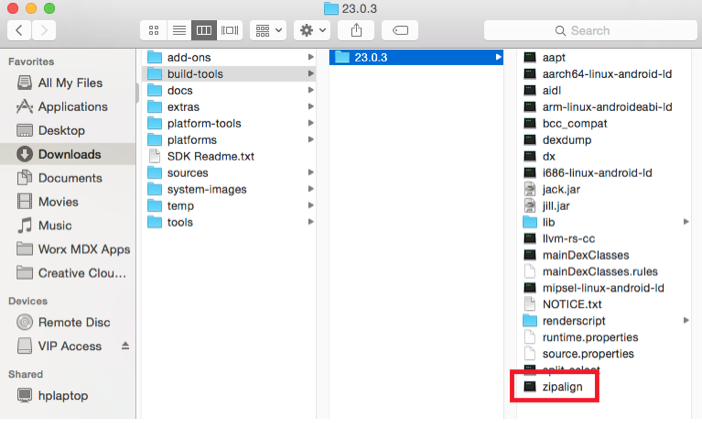
-
Add the location of the newly installed folders to the android_settings.txt file in the MDX Toolkit install folder.
-
In Applications > Citrix > MDX Toolkit, open the android_settings.txt file and then add the full path for the following folders:
- Android SDK
- Android SDK > tools
- Android SDK > platform-tools
- Android SDK > build-tools > [version]
Note:
Be sure to remove the Android SDK > apktools path from the android_settings file, as that path is no longer required.
To find the full path of your SDK folder, right-click on the file, select Get Info and then on the Info panel, review the Where information.
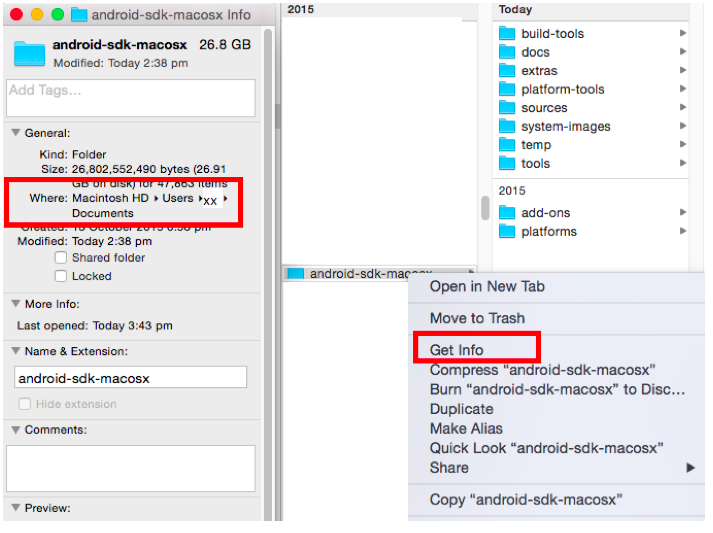
-
Before editing the android_settings file, make a copy of the file.
-
Go to Applications > Citrix > MDXToolkit > Android_settings.
-
Add the new paths.
-
Save the file outside of the Applications > Citrix > MDX Toolkit folder.
-
Rename the original android_settings file in the Applications > Citrix > MDX Toolkit folder; for example, android_settings.old.
-
Copy the new android_settings file with the added paths into the Applications > Citrix > MDX Toolkit folder.
The following example shows the file with the paths added:
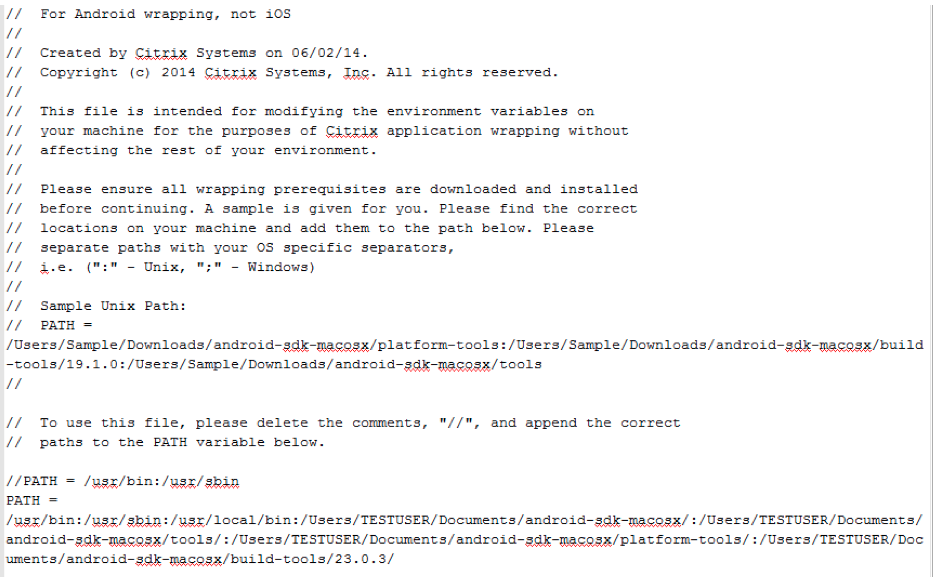
-
Valid Keystore
A valid keystore contains digitally signed certificates that you use to sign Android apps. You create a keystore one time and retain this file for current and future wrapping. If you do not use the same keystore when wrapping new versions of apps that you’ve previously deployed, upgrades of those apps don’t work. Instead, users must manually remove older versions before installing new versions.
A keystore can contain multiple private keys. Usually, though, the keystore has only one key.
For details about certificates, see Signing Your Applications.
Sign your apps with a key that meets the following guidelines:
- 2048-bit key size
- DSA or RSA key algorithm (-keyalg)
- Do not use MD5.
The MDX Toolkit signs apps using SHA1 to support older versions of Android. This algorithm deprecates soon in favor of SHA256. If you want to sign your app with another algorithm, use another tool.
If you don’t want to use the debug keystore, create a keystore. To create a keystore, start Terminal and then enter the command:
keytool -genkey -keystore my-release-key.keystore -alias alias_name -keyalg RSA -key size 2048 -validity 10000
Provide the information requested, such as a password for the keystore and the domain name of your organization (example: example.com). The key is valid for 25 years.
To sign an app, use this command:
jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore my_application.apk alias_name
You can now wrap Android apps. For details, see Wrapping Android apps.