Configuring the external authentication server
The NetScaler SDX Management Service can authenticate users with local user accounts or by using an external authentication server. The appliance supports the following authentication types:
- Local—Authenticates to the Management Service by using a password, without reference to an external authentication server. User data is stored locally on the Management Service.
- RADIUS—Authenticates to an external RADIUS authentication server.
- LDAP—Authenticates to an external LDAP authentication server.
- TACACS—Authenticates to an external Terminal Access Controller Access-Control System (TACACS) authentication server.
To configure an external authentication, specify the authentication type, and configure an authentication server.
Adding a RADIUS server
To configure RADIUS authentication, specify the authentication type as RADIUS, and configure the RADIUS authentication server.
Management Service supports RADIUS challenge response authentication according to the RADIUS specifications. RADIUS users can be configured with a one-time password on the RADIUS server. When the user logs on to an SDX appliance the user is prompted to specify this one time password.
To add a RADIUS server
- On the Configuration tab, under System, expand Authentication, and then click Radius.
- In the details pane, click Add.
- In the Create Radius Server dialogue box, type or select the values for the parameters:
- Name*—Name of the server.
- Server Name / IP Address*—fully qualified domain name (FQDN) or Server IP address. Note: DNS must be able to resolve the specified FQDN to an IP address, and only the primary DNS is used to resolve the FQDN. To manually set the primary DNS, see the section “Adding a Primary DNS for FQDN Name Resolution.”
- Port*—Port on which the RADIUS server is running. Default value: 1812.
- Time-out*—Number of seconds the system waits for a response from the RADIUS server. Default value: 3.
- Secret Key*—Key shared between the client and the server. This information is required for communication between the system and the RADIUS server.
- Enable NAS IP Address Extraction—If enabled, the Management Service IP address is sent to the server as the
nasipin accordance with the RADIUS protocol. - NASID—If configured, this string is sent to the RADIUS server as the
nasidin accordance with the RADIUS protocol. - Group Prefix—Prefix string that precedes group names within a RADIUS attribute for RADIUS group extraction.
- Group Vendor ID—Vendor ID for using RADIUS group extraction.
- Group Attribute Type—Attribute type for RADIUS group extraction.
- Group Separator—Group separator string that delimits group names within a RADIUS attribute for RADIUS group extraction.
- IP Address Vendor Identifier—Vendor ID of the attribute in the RADIUS which denotes the intranet IP. A value of 0 denotes that the attribute is not vendor encoded.
- IP Address Attribute Type—Attribute type of the remote IP address attribute in a RADIUS response.
- Password Vendor Identifier—Vendor ID of the password in the RADIUS response. Used to extract the user password.
- Password Attribute Type—Attribute type of the password attribute in a RADIUS response.
- Password Encoding—How passwords must be encoded in the RADIUS packets traveling from the system to the RADIUS server. Possible values: pap, chap, mschapv1, and mschapv2.
- Default Authentication Group—Default group that is chosen when the authentication succeeds in addition to extracted groups.
- Accounting—Enable Management Service to log audit information with RADIUS server.
- Click Create, and then, click Close.
Adding an LDAP authentication server
To configure LDAP authentication, specify the authentication type as LDAP, and configure the LDAP authentication server.
To add an LDAP server
- On the Configuration tab, under System, expand Authentication, and then click LDAP.
- In the details pane, click Add.
- In the Create LDAP Server dialogue box, type or select the values for the parameters:
-
Name*—Name of the server.
-
Server Name / IP Address*—FQDN or Server IP address.
Note: DNS must be able to resolve the specified FQDN to an IP address, and only the primary DNS is used to resolve the FQDN. To manually set the primary DNS, see the section “Adding a Primary DNS for FQDN Name Resolution.” -
Port*—Port on which the LDAP server is running. Default value: 389.
-
Time-out*—Number of seconds the system waits for a response from the LDAP server.
-
Base DN—Base, or node where the LDAP search must start.
-
Type—Type of LDAP server. Possible values: Active Directory (AD) and Novell Directory Service (NDS).
-
Administrative Bind DN—Full distinguished name that is used to bind to the LDAP server.
-
Administrative Password—Password that is used to bind to the LDAP server.
-
Validate LDAP Certificate—Check this option to validate the certificate received from the LDAP server.
-
LDAP Host Name—Host name for the LDAP server. If the validateServerCert parameter is enabled, this parameter specifies the host name on the certificate from the LDAP server. A host-name mismatch causes a connection failure.
-
Server Logon Name Attribute—Name attribute used by the system to query the external LDAP server or an Active Directory.
-
Search Filter—String to be combined with the default LDAP user search string to form the value. For example, vpnallowed=true with ldaploginame
samaccountand the user-supplied user name bob would yield an LDAP search string of: (&(vpnallowed=true)(samaccount=bob). -
Group Attribute—Attribute name for group extraction from the LDAP server.
-
Sub Attribute Name—Subattribute name for group extraction from the LDAP server.
-
Security Type—Type of encryption for communication between the appliance and the authentication server. Possible values:
PLAINTEXT: No encryption required.
TLS: Communicate using TLS protocol.
SSL: Communicate using SSL Protocol
-
Default Authentication Group—Default group that is chosen when the authentication succeeds in addition to extracted groups.
-
Referrals—Enable following of LDAP referrals received from LDAP server.
-
Maximum LDAP Referrals—Maximum number of LDAP referrals to follow.
-
Enable Change Password—Allow the user to modify the password if the password expires. You can change the password only when the Security Type configured is TLS or SSL.
-
Enable Nested Group Extraction—Enable Nested Group extraction feature.
-
Maximum Nesting Level—Number of levels at which group extraction is allowed.
-
Group Name Identifier—Name that uniquely identifies a group in the LDAP server.
-
Group Search Attribute—LDAP group search attribute. Used to determine to which groups a group belongs.
-
Group Search Subattribute—LDAP group search subattribute. Used to determine to which groups a group belongs.
-
Group Search Filter—String to be combined with the default LDAP group search string to form the search value.
-
- Click Create, and then click Close.
SSH public key authentication support for LDAP users
The SDX appliance can now authenticate the LDAP users through SSH public key authentication for logon. The list of public keys is stored on the user object in the LDAP server. During authentication, SSH extracts the SSH public keys from the LDAP server. The logon succeeds if any of the retrieved public keys supports SSH.
The same attribute name of the extracted public key must be present in both the LDAP server and in the NetScaler SDX appliance.
Important
For key-based authentication, you must specify a location of the public keys by setting the value of
Authorizedkeysfilein the/etc/sshd_configfile in the following aspect:
AuthorizedKeysFile .ssh/authorized_keys
System User. You can specify the location of public keys for any system user by setting the value of Authorizedkeysfile in the /etc/sshd_config*` file.
LDAP Users. The retrieved public key is stored in the /var/pubkey/<user_name>/tmp_authorized_keys-<pid> directory. The pid is the unique number added to differentiate between concurrent SSH requests from the same user. This location is a temporary location to hold the public key during the authentication process. The public key is removed from the system once authentication is complete.
To log in with the user, run the following command from the shell prompt:
$ ssh –i <private key> <username>@<IPAddress>
To configure LDAP server by using the GUI:
- Navigate to System > Authentication > LDAP.
- On the LDAP page, click **Servers** tab.
- Click any of the available LDAP servers.
- On the Configure Authentication LDAP Server page, select Authentication.
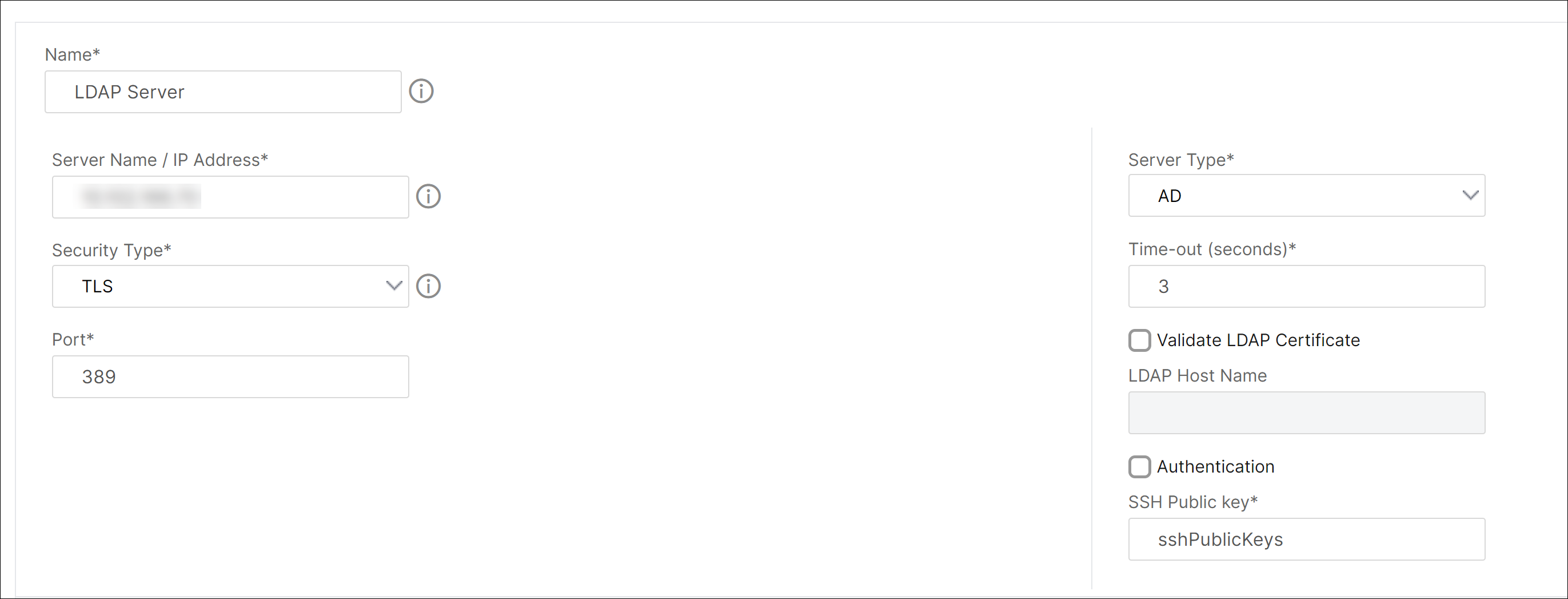
Note:
Clear the Authentication check box to use “sshPublicKeys” for authentication of LDAP users.
Adding a primary DNS for FQDN name resolution
If you define a RADIUS or an LDAP server by using the FQDN of the server instead of its IP address, manually set the primary DNS to resolve the server name. You can use either the GUI or CLI.
To set the primary DNS by using the GUI, go to System > Network Configuration > DNS.
To set the primary DNS by using the CLI, follow these steps.
- Open a Secure Shell (SSH) console.
- Log on to the NetScaler SDX appliance by using the admin credentials.
- Run the
networkconfigcommand. - Select the appropriate menu and update the DNS IPv4 Address, and save the changes.
If you run the networkconfig command again, you see the updated DNS address.
Adding a TACACS Server
To configure TACACS authentication, specify the authentication type as TACACS, and configure the TACACS authentication server.
To add a TACACS server
- On the Configuration tab, under System, expand Authentication, and then click TACACS.
- In the details pane, click Add.
- In the Create TACACS Server dialogue box, type or select the values for the parameters:
- Name—Name of the TACAS server
- IP Address—IP address of the TACACS server
- Port—Port on which the TACACS Server is running. Default value: 49
- Time-out—Maximum number of seconds the system waits for a response from the TACACS server
- TACACS Key—Key shared between the client and the server. This information is required for the system to communicate with the TACACS server
- Accounting—Enables Management Service to log audit information with TACACAS server
- Group Attribute Name—Name of the group attribute configured in the TACACS+ server
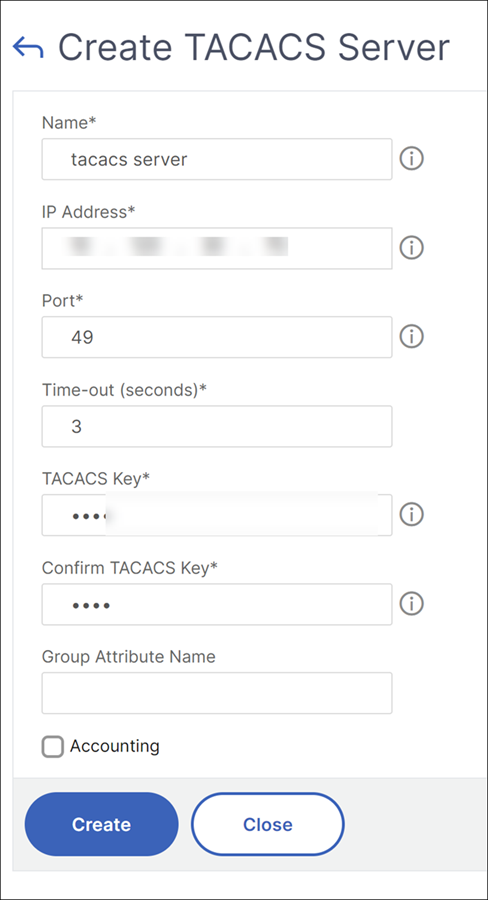
- Click Create, and then click Close.