Citrix Endpoint Management™ risk indicators
Device with blacklisted apps detected
Citrix Analytics detects access threats based on activity in a device with blacklisted apps and triggers the corresponding risk indicator.
The Device with blacklisted apps detected risk indicator is triggered when Endpoint Management service detects a blacklisted app during software inventory. The alert ensures that only authorized apps are run on devices that are on your organization’s network.
The risk factor associated with the Device with blacklisted apps detected risk indicator is the Other risk indicators. For more information about the risk factors, see Citrix user risk indicators.
When is the device with blacklisted apps detected risk indicator triggered?
The Device with blacklisted apps detected risk indicator is reported when blacklisted apps are detected on a user’s device. When Endpoint Management service detects one or more blacklisted apps on a device during software inventory, an event is sent to Citrix Analytics.
Citrix Analytics monitors these events and updates the user’s risk score. Also, it adds a Device with blacklisted apps detected risk indicator entry to the user’s risk timeline.
How to analyze the device with blacklisted apps detected risk indicator?
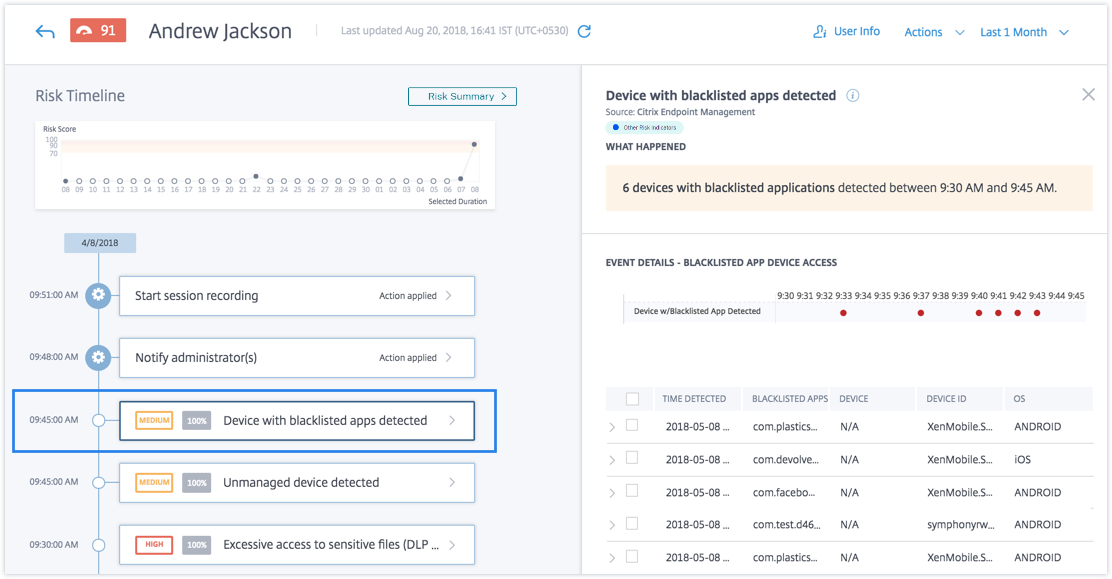
Consider the user Andrew Jackson, who used a device that had blacklisted apps recently installed. Endpoint Management reports this condition to Citrix Analytics, which assigns an updated risk score to Andrew Jackson.
From Andrew Jackson’s risk timeline, you can select the reported Device with blacklisted apps detected risk indicator. The reason for the event is displayed along with details such as the list of blacklisted apps, time Endpoint Management detected the blacklisted app, and so on.
To view the Device with blacklisted apps detected risk indicator for a user, navigate to Security > Users, and select the user.
-
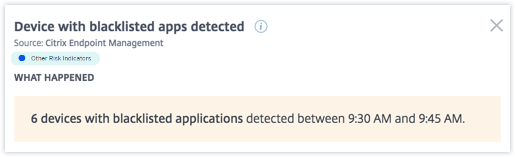
In the WHAT HAPPENED section, you can view the summary of the event. You can view the number of devices with blacklisted applications detected by the Endpoint Management service and the time the events occurred.
-
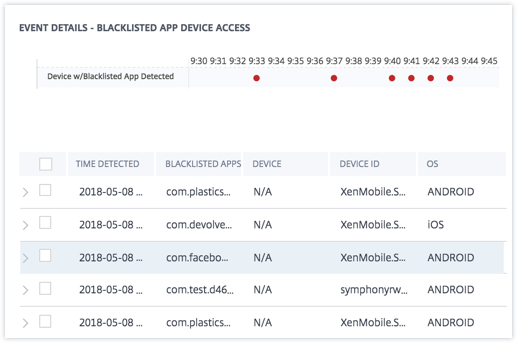
The EVENT DETAILS – BLACKLISTED APP DEVICE ACCESS section, the events are displayed in graphical and tabular format. The events are also displayed as individual entries in the graph, and the table provides the following key information:
-
Time detected- When the presence of blacklisted apps reported by Endpoint Management.
-
Blacklisted apps- The blacklisted apps on the device.
-
Device- The mobile device used.
-
Device ID- Information about the ID of the device that is used to log on to the session.
-
OS- The operating system of the mobile device.
-
Note
In addition to viewing the details in a tabular format, you can click the arrow against an alert’s instance to see more details.
What actions you can apply to the user?
You can perform the following actions on the user’s account:
-
Add to watchlist. When you want to monitor a user for future potential threats, you can add them to a watchlist.
-
Notify administrator(s). When there is any unusual or suspicious activity on the user’s account, an email notification is sent to all or selected administrators.
To learn more about actions and how to configure them manually, see Policies and Actions.
To apply the actions to the user manually, navigate to the user’s profile and select the appropriate risk indicator. From the Actions menu, select an action and click Apply.
Note
Irrespective of the data source that triggers a risk indicator, actions pertaining to other data sources can be applied.
Jailbroken or rooted device detected
Citrix Analytics detects access threats based on jailbroken or rooted device activity and triggers the corresponding risk indicator.
The Jailbroken or rooted device risk indicator is triggered when a user uses a jailbroken or rooted device to connect to the network. Secure Hub detects the device and reports the incident to Endpoint Management service. The alert ensures that only authorized users and devices are on your organization’s network.
The risk factor associated with the Jailbroken or rooted device risk indicator is the Other risk indicators. For more information about the risk factors, see Citrix user risk indicators.
When is the jailbroken or rooted device detected risk indicator triggered?
It is important for security officers to be able to ensure that users connect using network-compliant devices. The Jailbroken or rooted device detected risk indicator alerts you to users with iOS devices that are jailbroken or Android devices that are rooted.
The Jailbroken or rooted device risk indicator is triggered when an enrolled device becomes jailbroken or rooted. Secure Hub detects the event on the device and reports it to the Endpoint Management service.
How to analyze the jailbroken or rooted device detected risk indicator?
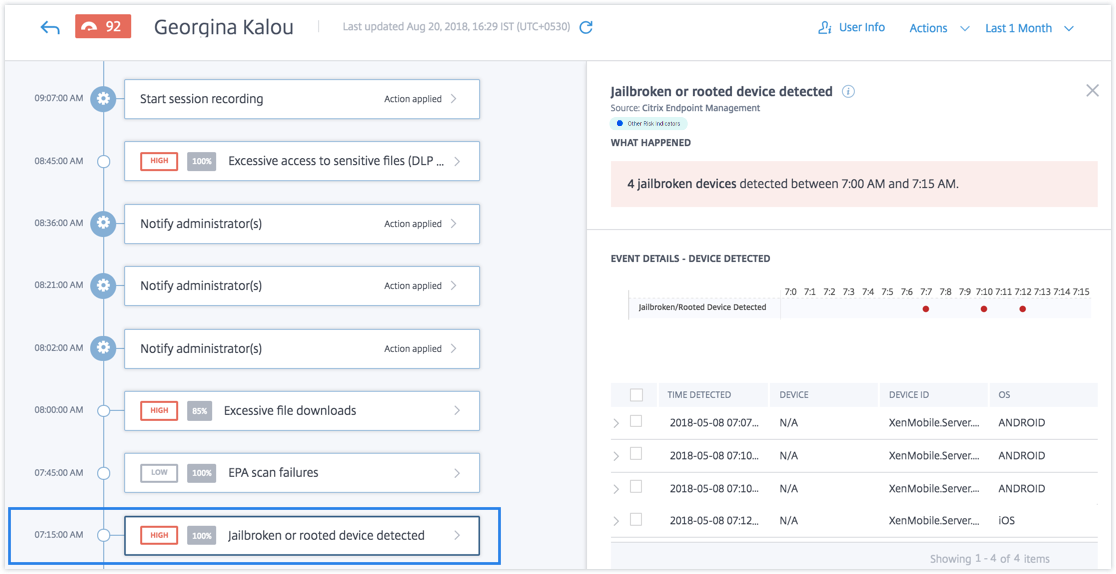
Consider the user Georgina Kalou, whose enrolled iOS device recently became jailbroken. This suspicious behavior is detected by Citrix Analytics and a risk score is assigned to Georgina Kalou.
From Georgina Kalou’s risk timeline, you can select the reported Jailbroken or rooted device detected risk indicator. The reason for the event is displayed along with the details such as time the risk indicator was triggered, description of the event, and so on.
To view the Jailbroken or rooted device detected risk indicator for a user, navigate to Security > Users, and select the user.
-
The WHAT HAPPENED section, you can view the summary of the event. You can view the number of jailbroken or rooted devices detected and the time the events occurred.
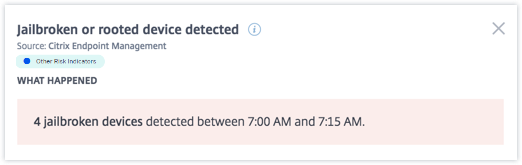
-
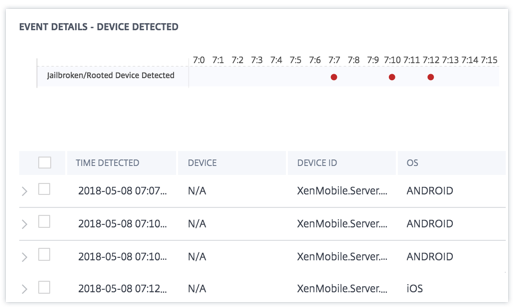
The EVENT DETAILS – DEVICE DETECTED section, the events are displayed in graphical and tabular format. The events are also displayed as individual entries in the graph, and the table provides the following key information:
-
Time detected. The time the jailbroken or rooted device is detected.
-
Device. The mobile device used.
-
Device ID. Information about the ID of the device that is used to log on to the session.
-
OS. The operating system of the mobile device.
-
Note
In addition to viewing the details in tabular format, click the arrow against an alert’s instance to see more details.
What actions you can apply to the user?
You can perform the following actions on the user’s account:
-
Add to watchlist. When you want to monitor a user for future potential threats, you can add them to a watchlist.
-
Notify administrator(s). When there is any unusual or suspicious activity on the user’s account, an email notification is sent to all or selected administrators.
To learn more about actions and how to configure them manually, see Policies and Actions.
To apply the actions to the user manually, navigate to the user’s profile and select the appropriate risk indicator. From the Actions menu, select an action and click Apply.
Note
Irrespective of the data source that triggers a risk indicator, actions pertaining to other data sources can be applied.
Unmanaged device detected
Citrix Analytics detects access threats based on unmanaged device activity and triggers the corresponding risk indicator.
The Unmanaged device detected risk indicator is triggered when a device is:
-
Remotely wiped due to an automated action.
-
Manually wiped by the administrator.
-
Unenrolled by the user.
The risk factor associated with the Unmanaged device detected risk indicator is the Other risk indicators. For more information about the risk factors, see Citrix user risk indicators.
When is the unmanaged device detected risk indicator triggered?
The Unmanaged device detected risk indicator is reported when a user’s device has become unmanaged. A device changes to an unmanaged state due to:
-
An action performed by the user.
-
An action performed by the Endpoint Management administrator or the server.
In your organization, using Endpoint Management service you can manage the devices and apps that access the network. For more information, see Management Modes.
When a user’s device changes to an unmanaged state, Endpoint Management service detects this event and reports it to Citrix Analytics. The user’s risk score is updated. The Unmanaged device detected risk indicator is added to user’s risk timeline.
How to analyze unmanaged device detected risk indicator?
Consider the user Georgina Kalou, whose device is remotely wiped by an automated action on the server. Endpoint Management reports this event to Citrix Analytics, which assigns an updated risk score to Georgina Kalou.
From Georgina Kalou’s risk timeline, you can select the reported Unmanaged device detected risk indicator. The reason for the event is displayed along with details such as, time the risk indicator was triggered, description of the event, and so on.
To view the Unmanaged device detected risk indicator for a user, navigate to Security > Users, and select the user.
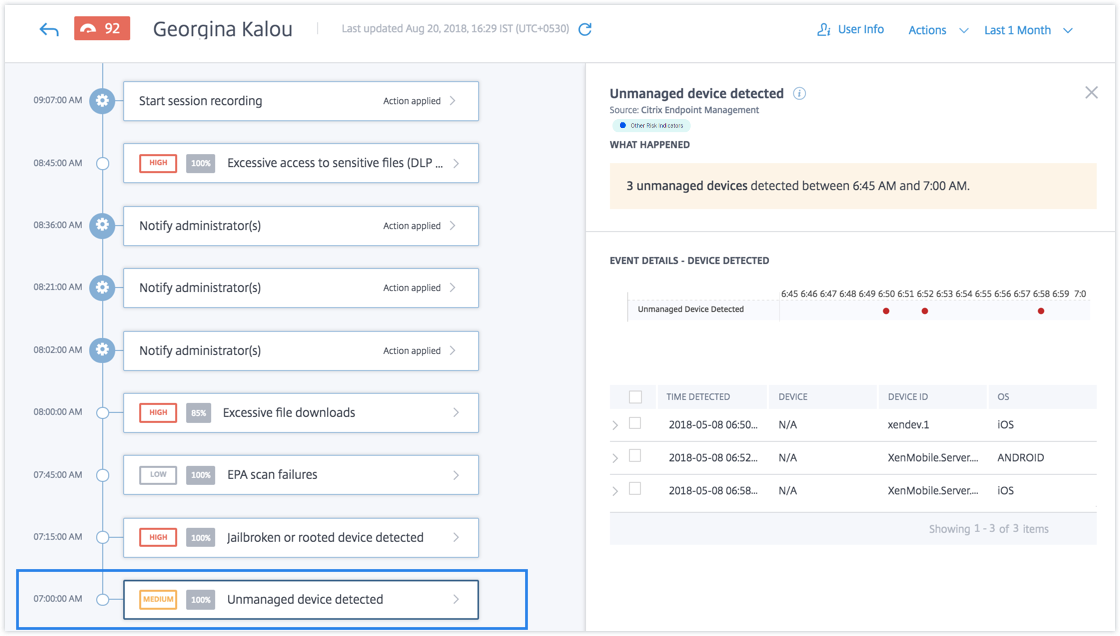
- The WHAT HAPPENED section, you can view a summary of the event. You can view the number of unmanaged devices detected and the time the events occurred.
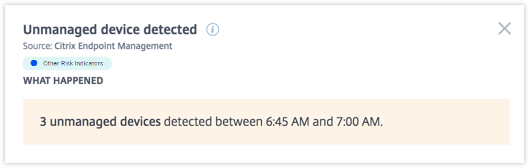
-
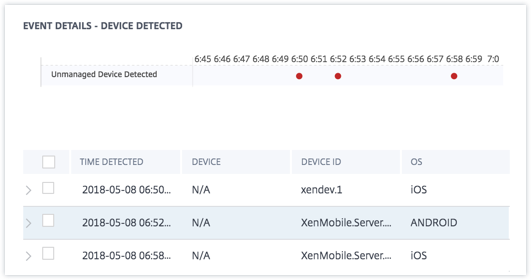
The EVENT DETAILS – DEVICE DETECTED section, the events are displayed in graphical and tabular format. The events are also displayed as individual entries in the graph, and the table provides the following key information:
-
Time detected. The time the event was detected.
-
Device. The mobile device used.
-
Device ID. The device ID of the mobile device.
-
OS. The operating system of the mobile device.
-
What actions you can apply to the user?
You can perform the following actions on the user’s account:
-
Add to watchlist. When you want to monitor a user for future potential threats, you can add them to a watchlist.
-
Notify administrator(s). When there is any unusual or suspicious activity on the user’s account, an email notification is sent to all or selected administrators.
To learn more about actions and how to configure them manually, see Policies and Actions.
To apply the actions to the user manually, navigate to the user’s profile and select the appropriate risk indicator. From the Actions menu, select an action and click Apply.
Note
Irrespective of the data source that triggers a risk indicator, actions pertaining to other data sources can be applied.