Security Information and Event Management (SIEM) integration
Note
Contact CAS-PM-Ext@cloud.com to request assistance for the SIEM integration, exporting data to SIEM, and provide feedback.
Integrate Citrix Analytics for Security™ with your SIEM services and export the users’ data from the Citrix IT environment to your SIEM. Correlate the exported data with the data available in your SIEM to get deeper insights into your organization’s security posture.
This integration enhances the value of both your Citrix Analytics for Security and your SIEM.
Benefits
-
Enables your Security Operations teams to correlate, analyze, and search data from disparate logs.
-
Helps your Security Operations teams to identify and quickly remediate the security risks.
-
Visibility of security alerts in a centralized place.
-
Centralized approach to detect potential security threats for organizational risk analysis capabilities such as risk indicators, user profiles, and risk scores.
-
Ability to combine and correlate the Citrix Analytics risk intelligence information of a user account with the external data sources connected within your SIEM.
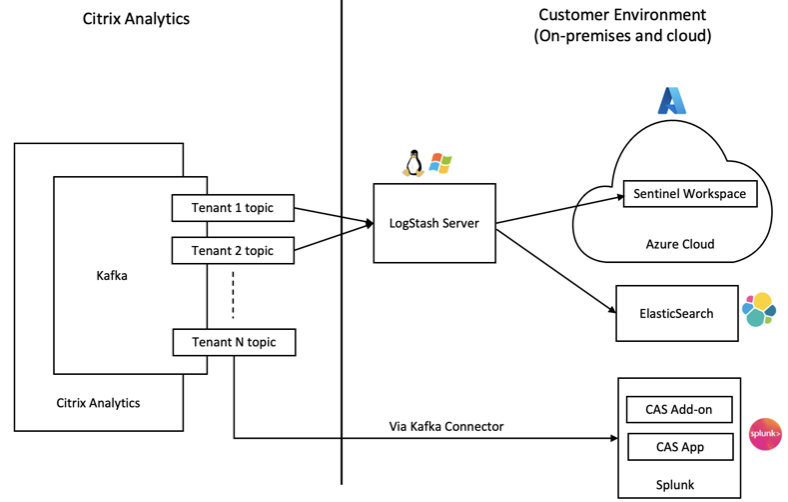
SIEM integration architecture
Your SIEM Integration connects with the north-bound Kafka deployed on Citrix Analytics for Security cloud. This can be achieved in the following two ways:
-
Kafka endpoints: If your SIEM supports Kafka endpoints, use the parameters provided in the Logstash config file and the certificate details in the JKS file or the PEM file to integrate your SIEM with Citrix Analytics for Security. Using the Kafka endpoints, you can connect and pull the data to the SIEM of choice.
-
Logstash engine: If your SIEM does not support Kafka endpoints, then you can use the Logstash data collection engine. You can send the risk insights data from Citrix Analytics for Security to one of the output plug-ins that are supported by Logstash.
Refer to the following SIEM solution architecture diagram to understand how data flows from Citrix Analytics for Security to your SIEM service:
Turn on or off data transmission
To stop transmitting data from Citrix Analytics for Security:
-
Go to Settings > Data Exports.
-
Turn off the toggle button to disable the data transmission.
Note By default, the data transmission is always turned on/enabled for SIEM.
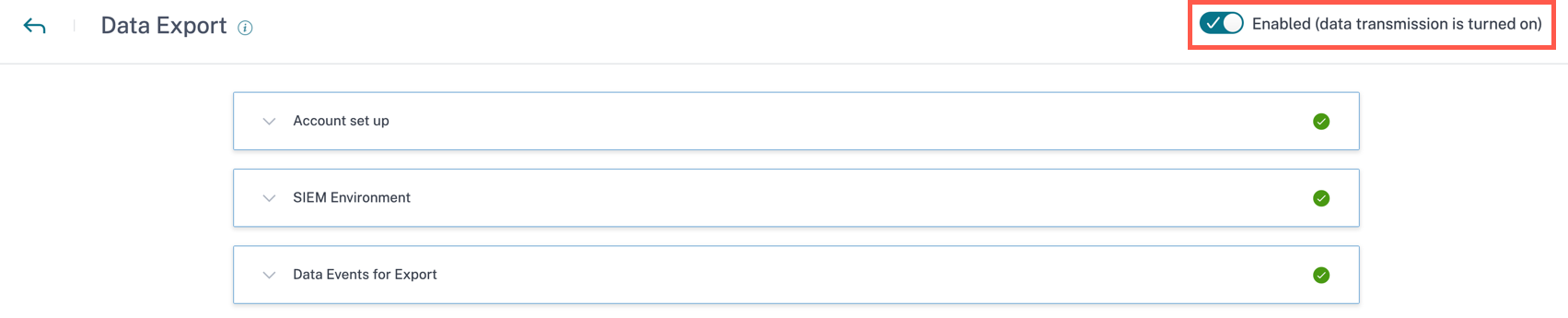
To enable data transmission again, turn on the toggle button.
Setting up SIEM environment
To export data to SIEM, you must perform the following actions:
- Set up your Kafka account and authentication credentials
- Download the pre-populated configuration and set up the SIEM environment
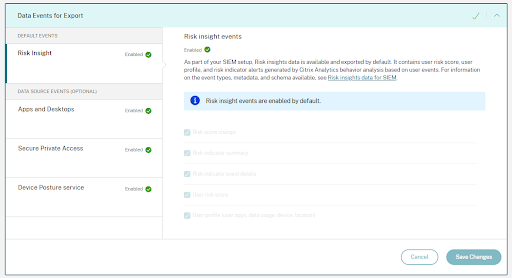
- Data Events for Export
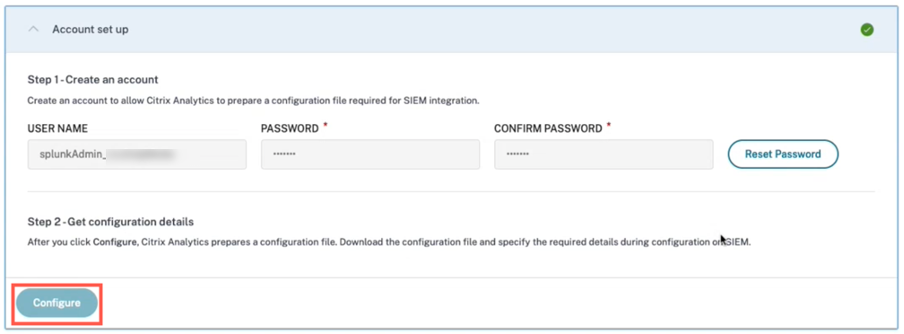
SIEM export account setup
-
For setting up your account, navigate to Settings > Data Exports > expand Account set up. Create an account by specifying the user name and password. Once you set up your account, your Kafka details are generated. These details are automatically embedded while generating the configuration file.
-
Click Configure to generate the configuration file. The configuration file contains details such as Kafka endpoints, your specific subscription topics, and group IDs. Also, it pre-configures the Kafka and SSL attributes which are required for completing authentication and data flow.
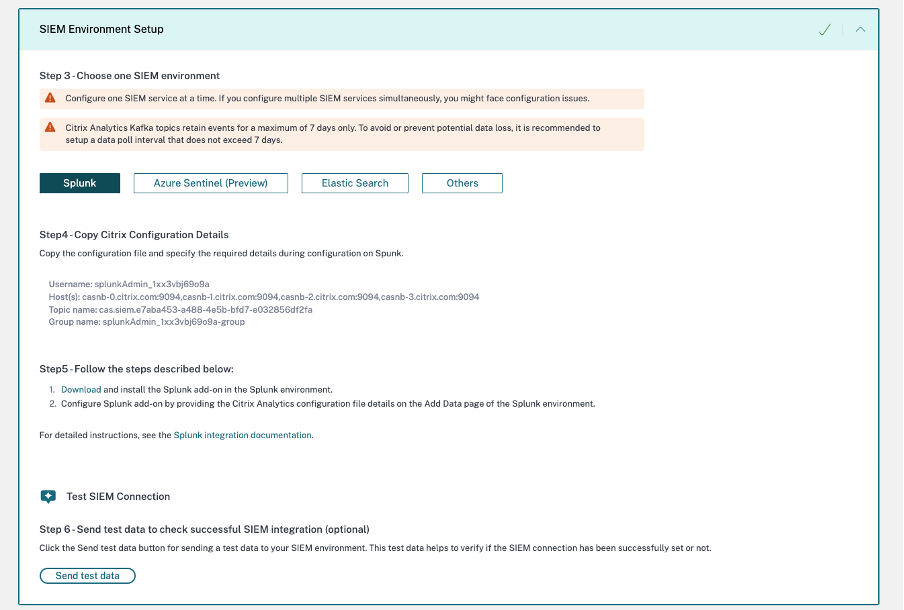
SIEM configuration and environment setup
Choose the SIEM environment as needed. You can integrate Citrix Analytics for Security with the following services. Refer the following links to get detailed information and SIEM specific configurations:
Data events exported from Citrix Analytics for Security to your SIEM service
As part of SIEM exports, there are two types of data sets:
-
Risk insights events (Default exports) – Once you have completed the account configuration and SIEM setup, default data (risk insights events) start flowing to your SIEM deployment. Risk insights data contains user risk score, user profile, and risk indicator alerts. These are generated by Citrix Analytics machine learning algorithm, user behavior analysis, and based on user events. For information on the event types, metadata, and schema available, see Risk insights data for SIEM.
-
Data Source events (Optional exports) - Additionally, you can configure the Data exports feature to export user events from your Citrix Analytics for Security enabled products data sources. When you perform any activity in the Citrix environment, the data source events are generated. The exported events are unprocessed real time user and product usage data as available in self-service view. The meta data contained in these events can further be used for deeper threat analysis, creating new dashboards, and co related with other non-Citrix data source events across your security and IT infra.
Currently, Citrix Analytics for Security sends user events to your SIEM for these data sources: Citrix Virtual Apps and Desktops™, Secure Private Access, and Device Posture service.
For information on the event types, metadata, and schema available, see Data source events.
Note
Customers who are using a Logstash data broker, it is recommended that the latest configuration file is downloaded from Citrix Analytics for Security portal, and updated on the Logstash service deployment. This ensures that the correct data source event tables are created and the events are now available in SIEM indexes.
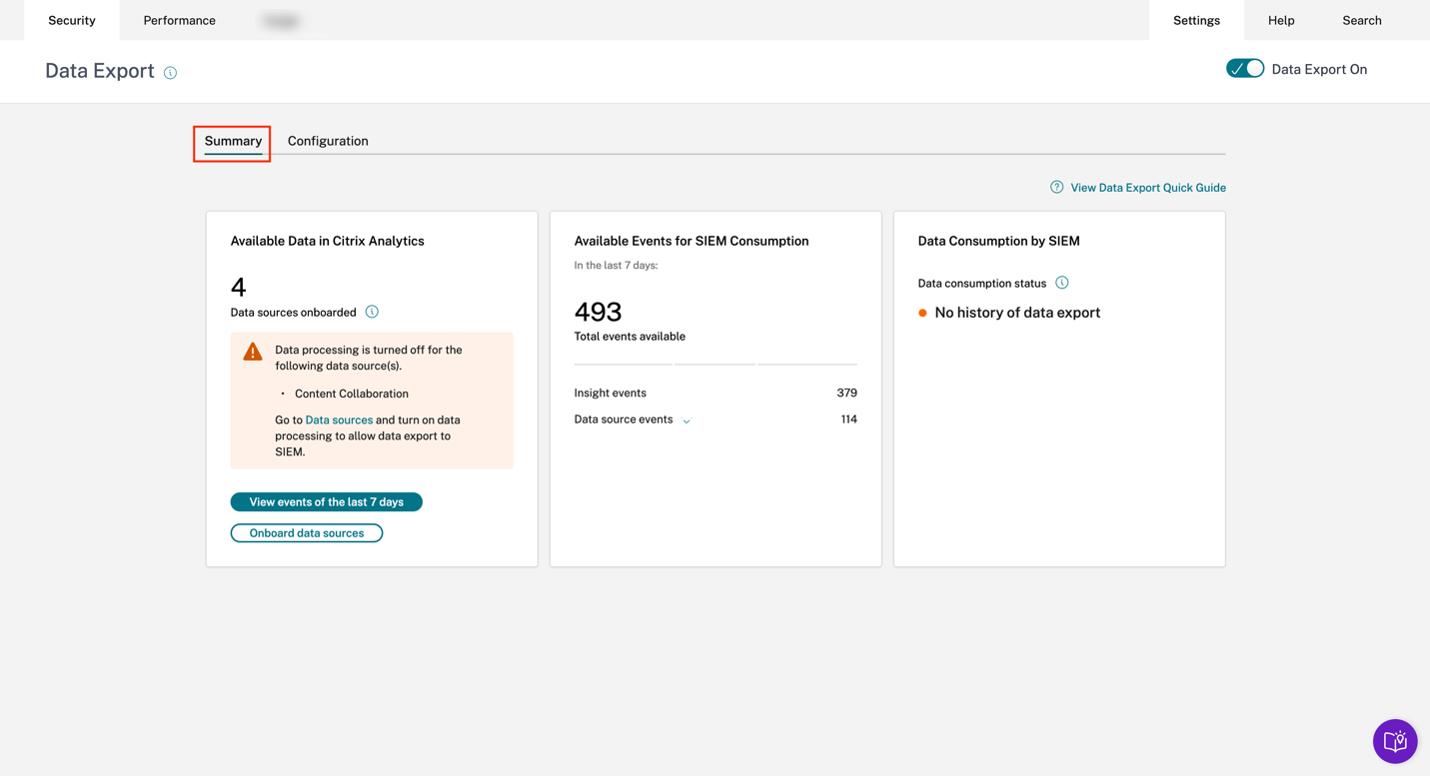
Troubleshooting SIEM Integration
The Data Exports for Security view includes a Summary tab to help administrators troubleshoot their SIEM integration with Citrix Analytics. The Summary dashboard provides visibility into the health and flow of data by taking them through the checkpoints that aid the troubleshooting process.
To learn more about this capability, refer Troubleshooting Data Exports.