SAML authentication
SAML (Security Assertion Markup Language) is an open standard used by identity and authentication products. Using SAML, you can configure StoreFront to redirect users to an external identity provider for authentication.
Note
Configure StoreFront with SAML authentication for internal access. For external access configure Citrix Gateway with SAML authentication then configure StoreFront with Gateway pass-through authentication.
StoreFront requires a SAML 2.0-compliant identity provider (IdP) such as:
- Microsoft AD Federation Services using SAML bindings (not WS-Federation bindings). For more information, see CTX220638.
- Citrix Gateway (configured as an IdP).
- Microsoft Entra ID. For more information, see CTX237490.
The SAML assertion must contain a saml:Subject attribute containing the user’s UPN.
To enable or disable SAML authentication for a store when connecting using Citrix Workspace app, in the Authentication Methods window select SAML Authentication. Enabling SAML authentication for a store by default also enables it for all websites for that store. You can independently configure SAML for a particular website on the Authentication methods tab.
StoreFront™ SAML Endpoints
To configure SAML, your identity provider may require the following endpoints:
- The URL of the Entity ID. This is the path to the auth service of the store, normally https://[storefront host]/Citrix/[StoreName]Auth
- The URL of the Assertion Consumer Service, normally https://[storefront host]/Citrix/[StoreName]Auth/SamlForms/AssertionConsumerService
- The Metadata service, normally https://[storefront host]/Citrix/[StoreName]Auth/SamlForms/ServiceProvider/Metadata
In addition there is a test endpoint, normally https://[storefront host]/Citrix/[StoreName]Auth/SamlTest
You can use the following PowerShell script to list out the endpoints for a specified store.
# Change this value for your Store
$storeVirtualPath = "/Citrix/Store"
$auth = Get-STFAuthenticationService -Store (Get-STFStoreService -VirtualPath $storeVirtualPath)
$spId = $auth.AuthenticationSettings["samlForms"].SamlSettings.ServiceProvider.Uri.AbsoluteUri
$acs = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + "/SamlForms/AssertionConsumerService")
$md = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + "/SamlForms/ServiceProvider/Metadata")
$samlTest = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + "/SamlTest")
Write-Host "SAML Service Provider information:
Entity ID: $spId
Assertion Consumer Service: $acs
Metadata: $md
Test Page: $samlTest"
<!--NeedCopy-->
Example of the output:
SAML Service Provider information:
Entity ID: https://storefront.example.com/Citrix/StoreAuth
Assertion Consumer Service: https://storefront.example.com/Citrix/StoreAuth/SamlForms/AssertionConsumerService
Metadata: https://storefront.example.com/Citrix/StoreAuth/SamlForms/ServiceProvider/Metadata
Test Page: https://storefront.example.com/Citrix/StoreAuth/SamlTest
<!--NeedCopy-->
Configure using Metadata exchange
To simplify configuration, you can exchange metadata (identifiers, certificates, endpoints and other configuration) between the Identity Provider and the Service Provider, which is StoreFront in this case.
If your Identity Provider supports metadata import, then you can point it at the StoreFront MetaData endpoint. Note:: This must be done over HTTPS.
To configure StoreFront using the metadata from an Identity Provider, use the Update-STFSamlIdPFromMetadata cmdlet, for example:
Get-Module "Citrix.StoreFront*" -ListAvailable | Import-Module
# Remember to change this with the virtual path of your Store.
$StoreVirtualPath = "/Citrix/Store"
$store = Get-STFStoreService -VirtualPath $StoreVirtualPath
$auth = Get-STFAuthenticationService -StoreService $store
# To read the metadata directly from the Identity Provider, use the following:
# Note again this is only allowed for https endpoints
Update-STFSamlIdPFromMetadata -AuthenticationService $auth -Url https://example.com/FederationMetadata/2007-06/FederationMetadata.xml
# If the metadata has already been download, use the following:
# Note: Ensure that the file is encoded as UTF-8
Update-STFSamlIdPFromMetadata -AuthenticationService $auth -FilePath "C:\Users\exampleusername\Downloads\FederationMetadata.xml"
<!--NeedCopy-->
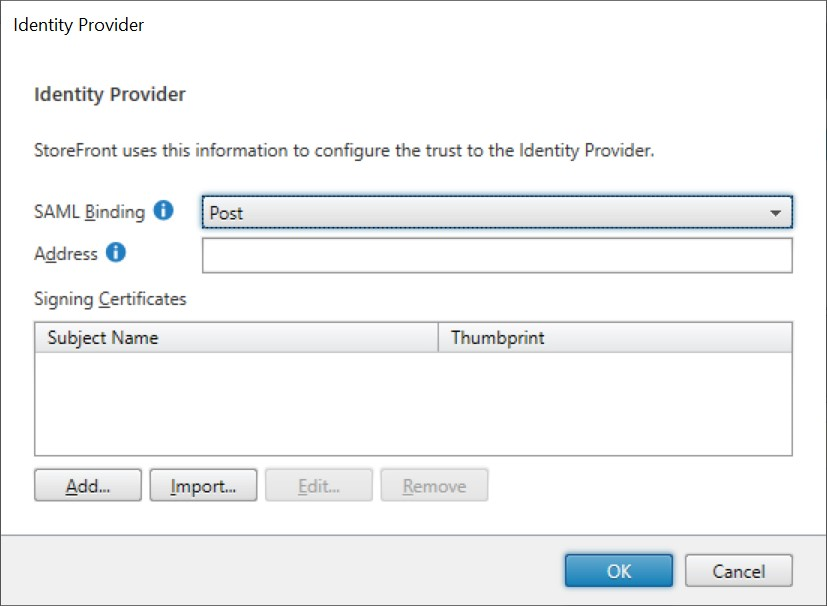
Configure Identity Provider
-
Click the settings drop down in the SAML Authentication row and click Identity Provider.
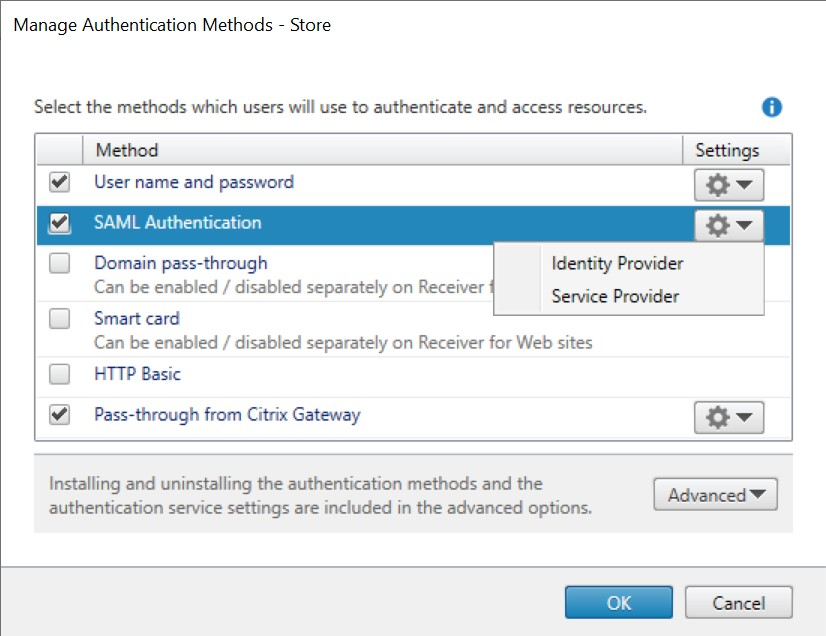
-
Choose SAML Binding of Post or Redirect.
-
Enter the Address of the Identity Provider.
-
Import the certificate used to sign the SAML tokens.
-
Press OK to save changes.
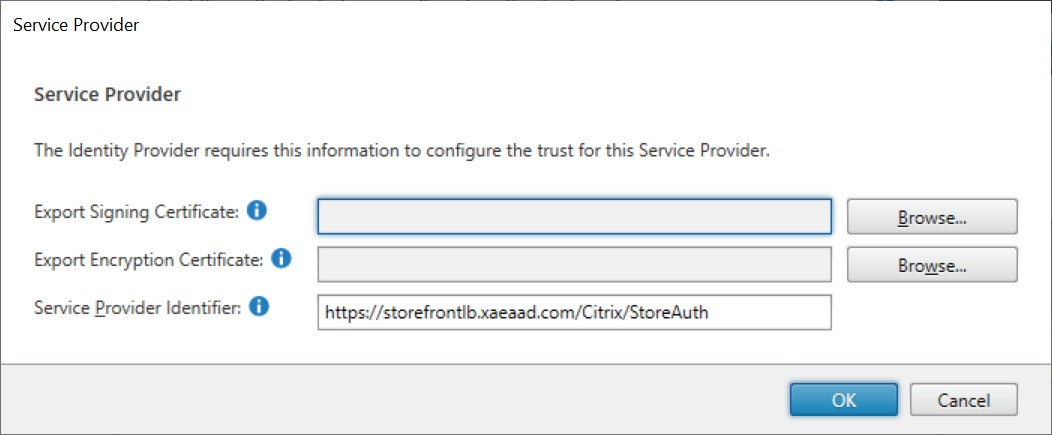
Configure Service Provider
-
Click the settings drop down in the SAML Authentication row and click Service Provider.
-
Optionally, choose an Export Signing Certificate, used to sign messages to the identity provider.
-
Optionally, choose an Export Encryption Certificate, used to decrypt messages received from the identity provider.
-
The Service Provider Identifier is pre-filled with the authentication service for the store.
-
Press OK to save changes.
PowerShell SDK
Using the PowerShell SDK:
-
To import a signing certificate call cmdlet Import-STFSamlSigningCertificate.
-
To import an encryption certificate call cmdlet Import-STFSamlEncryptionCertificate.
Testing
To test the SAML integration:
- Go to the SAML test page, see StoreFront SAML Endpoints.
- This redirects you to the identity provider. Enter your credentials.
- You are redirected back to the test page that displays the identity claims and assertions.
Configure Delivery Controller™ to trust StoreFront
When using SAML authentication, StoreFront does not have access to the user’s credentials so is unable to authenticate to Citrix Virtual Apps and Desktops. You must therefore configure the Delivery Controller to trust requests from StoreFront, see Citrix Virtual Apps and Desktops Security considerations and best practices.
Single sign-on to VDAs using Federated Authentication Service
When using SAML authentication, StoreFront does not have access to the user’s credentials so single sign-on to VDAs is not available by default. You can use Federated Authentication Service to provide single sign-on.