Tech Brief: Secure Private Access
Overview
Citrix Secure Private Access™ is a cloud delivered Zero Trust Network Access (ZTNA) solution that delivers adaptive access to IT sanctioned applications whether they are deployed on-prem or in the cloud. Traditional VPN solutions provide access at the network level and are:
- Prone to network level attacks
- Require backhauling of all traffic
- Often requires device management to capture the state of the end user device
Citrix Secure Private Access helps avoid these pitfalls. Secure Private Access provides access only at the application layer thereby preventing network level attacks, does not require backhauling thereby providing a much better end user experience, and provides IT with a set of security controls offering employees with a choice to access IT sanctioned applications on any device, regardless of it being managed or BYO.
Watch this video to learn more:
Conceptual Architecture
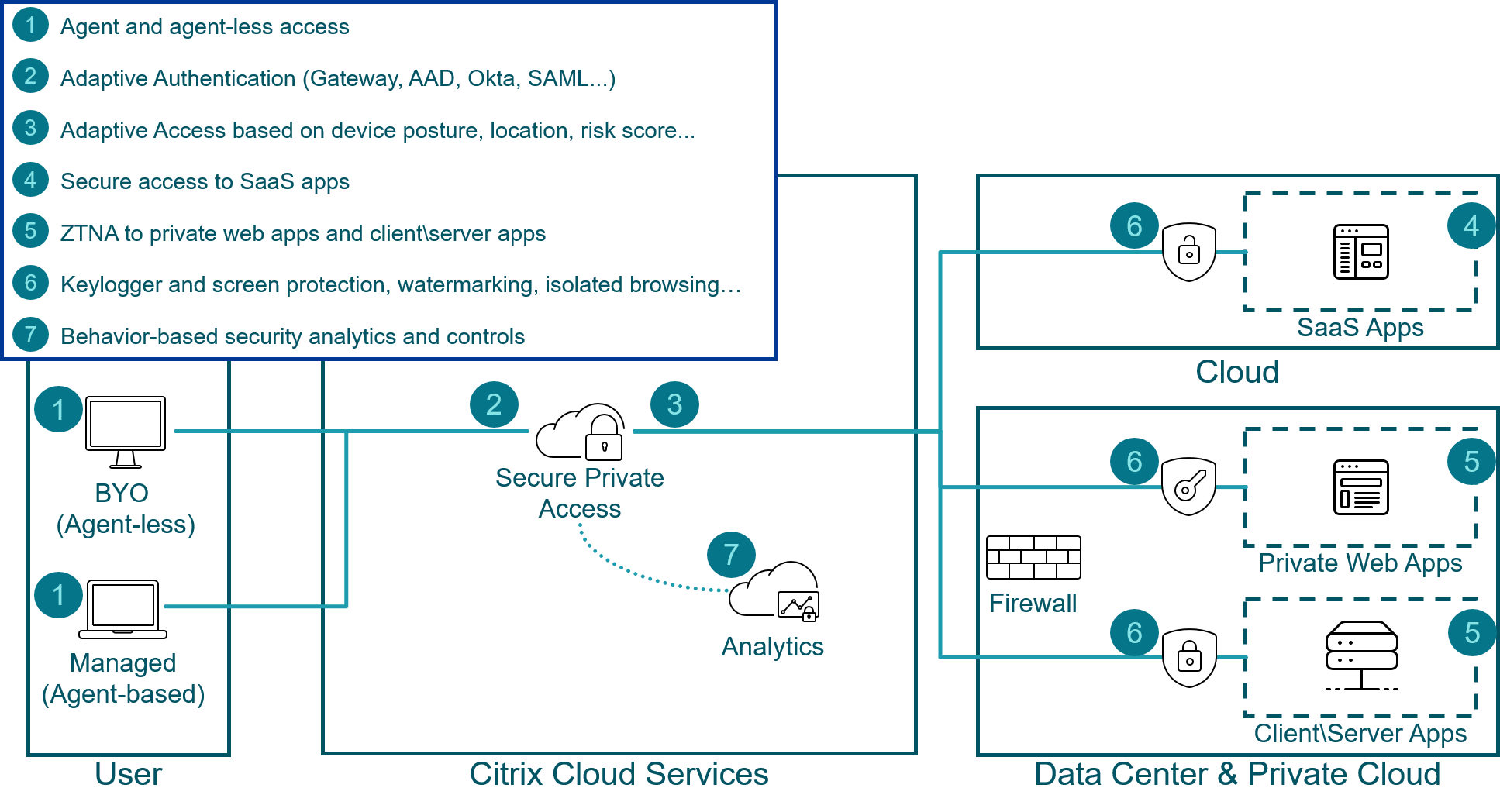
At a high-level, Citrix Secure Private Access allows users to securely connect to public SaaS apps, private web apps, and client/server apps.
Conceptually, when accessing a sanctioned resource, Secure Private Access
- Determines if the endpoint is agent-less or agent-based. This determines if the user can access a resource and what capabilities within the app the user has.
- Utilizes adaptive authentication to properly validate the user’s identity across multiple identity providers (IdP).
- Provides adaptive access to authorized resources. Utilizing criteria like device posture, user risk, and user location, Secure Private Access can allow full access, deny all access, or provide restricted access.
- Establishes a Zero Trust Network Access (ZTNA) connection to private web and client/server apps. Utilizing an outbound only connection, and relaying all traffic through the Secure Private Access service, a user’s endpoint device is never in direct contact with the secure network.
- Applies session restrictions that limits the user’s capabilities. Session security policies can include keylogger and screen capturing protections, watermarking, isolated browsing, and printing/downloading/clipboard restrictions.
- Monitors user behavior with the Analytics for Security service. The Analytics service builds a user behavior profile and identifies potential threats that can be mitigated automatically or manually.
The capabilities of Secure Private Access can be broken down into the following categories:
- Adaptive Security
- Application Access
- Browser Security
- User and Experience Behavior Analytics
Adaptive Security
Secure Private Access incorporates adaptive security to on-prem and cloud-hosted resources. Oftentimes, a user’s access level is granted on initial logon. With adaptive security, a user’s security risk profile is continuously monitored, which impacts security settings. Adaptive Security influences how users authenticate (Adaptive Authentication) and the capabilities users have within applications (Adaptive Access). And by integrating single sign-on, the adaptive security policies can be seamlessly applied while simplifying the user authentication experience.
Adaptive Authentication
Adaptive authentication determines the right authentication flow for the current request. Adaptive authentication can identify the device posture, geographical location, network segment, user organization/department membership. Based on the information obtained, an admin can define how they want to authenticate users to their IT sanctioned apps. This allows organizations to implement the same authentication policy framework across every resource including public SaaS apps, private web apps, private client/server apps, and Desktops as a Service (DaaS).
Watch this video to learn more:
Adaptive Authentication policies can easily incorporate business logic to create a stronger authentication solution. This could include scenarios like:
- Internal vs External: Users who connect from internal locations from managed devices could authenticate with a username and password. External users on BYO devices would require multi-factor authentication that incorporates a Time-based One Time Password (TOTP) token.
- Employee vs Contractor vs Partner: Organizations will often require different authentication flows based on the user identity. If an employee, authenticate against Active Directory. If the user is a contractor, utilize a personal Gmail account. If the user is a partner, utilize a managed Azure Active Directory account.
- Mergers and Acquisitions: Adaptive Authentication can help organizations overcome the authentication challenges associated with a merger or acquisition. Adaptive Authentication lets users authenticate against their pre-merger identity provider. The pre-merger identity can then be used to provide ZTNA access to authorized resources from either organization.
Adaptive Access
With adaptive access, organizations can provide users with full access, no access, or restricted access to SaaS, private web, and private client/server apps.
When a user tries to access an authorized resource, adaptive access determines how the current request aligns with the defined conditions. The conditions can include a combination of:
- User or group membership
- Device type: mobile or desktop
- GEO Location
- Network Location
- Device Posture based on automated endpoint analysis scans
Based on the results of the conditions, access to the resource is either allowed, denied, or restricted. Restricted access applies security policies to the session, which can include:
Watch this video to learn more:
- Preferred browser: Disables the use of the local browser. Automatically uses the Enterprise Browser or the Remote Browser Isolation service. To learn more about different browser options, review the Browser Security section.
- Keylogger Protection: One risk that must be mitigated when end users use their personal devices for work is malware. Keylogger malware tries to exfiltrate and harvest sensitive information like user credentials or personally identifiable information. Keylogger Protection prevents malware on the endpoint device from capturing user keystrokes. The keystrokes are encrypted before they can be captured by malware, helping to protect against stolen passwords, user identities, or credit card information.
- Screen Capture Protection: The line between personal and work usage on devices has been blurred, so it’s become common for end users to move from working on a business app to a virtual hangout with friends or family on that device. In these scenarios, accidental screen sharing of sensitive data in the business app can result in significant issues, especially for end users in highly regulated industries. Screen Capture Protection prevents the protected application’s screen contents from being shared within web conferencing tools, screen capture software, and malware.
- Restrict clipboard access: Disables cut/copy/paste operations between the app and endpoint clipboard.
- Restrict printing: Disables ability to print from within the app browser.
- Restrict navigation: Disables the next/back browser buttons.
- Restrict downloads: Disables the user’s ability to download from within the SaaS app.
- Display watermark: Overlays a screen-based watermark showing the user name and IP address of the endpoint. If a user tries to print or take a screenshot, the watermark appears as displayed on the screen.
The following provides demonstrations of these capabilities.
| Links | ||
|---|---|---|
 |
View demo: Browser Restrictions - Video coming soon | |
 |
View demo: Keylogger Protection | |
 |
View demo: Screen Sharing Protection | |
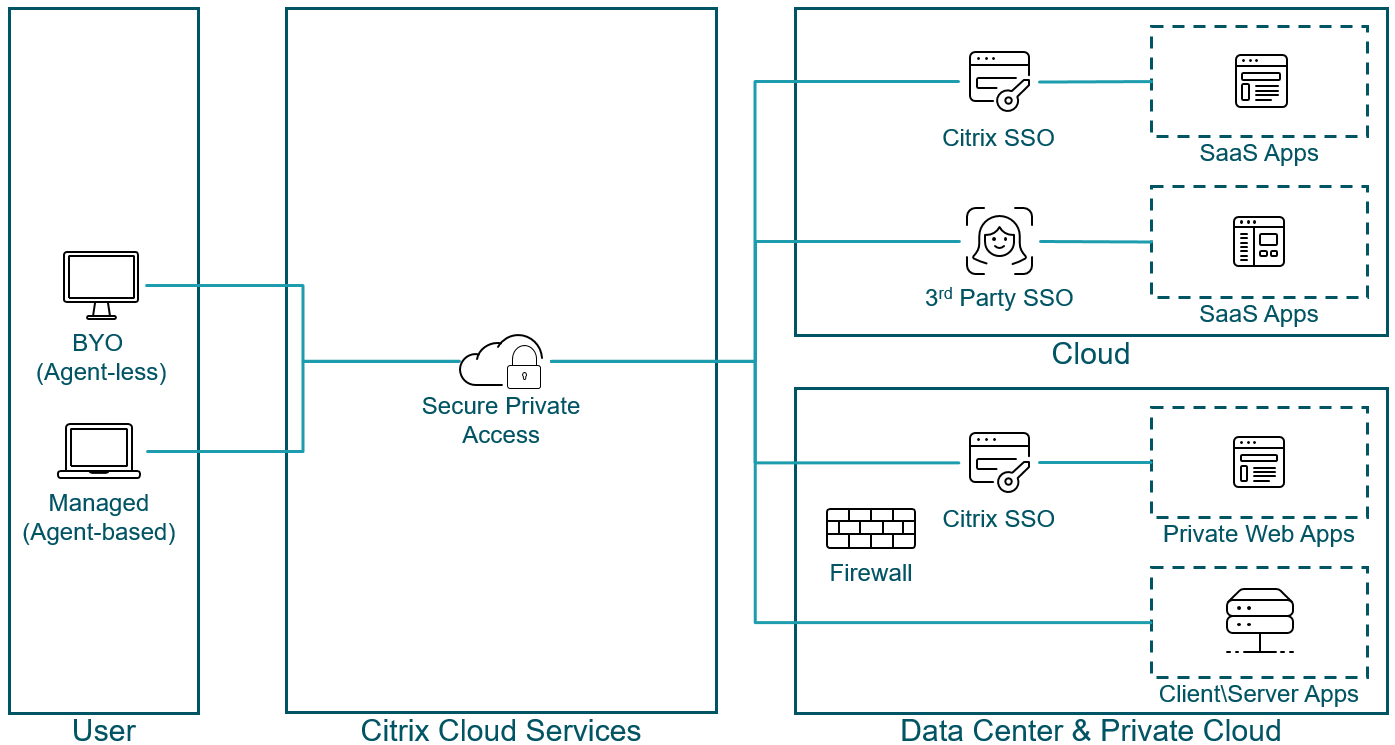
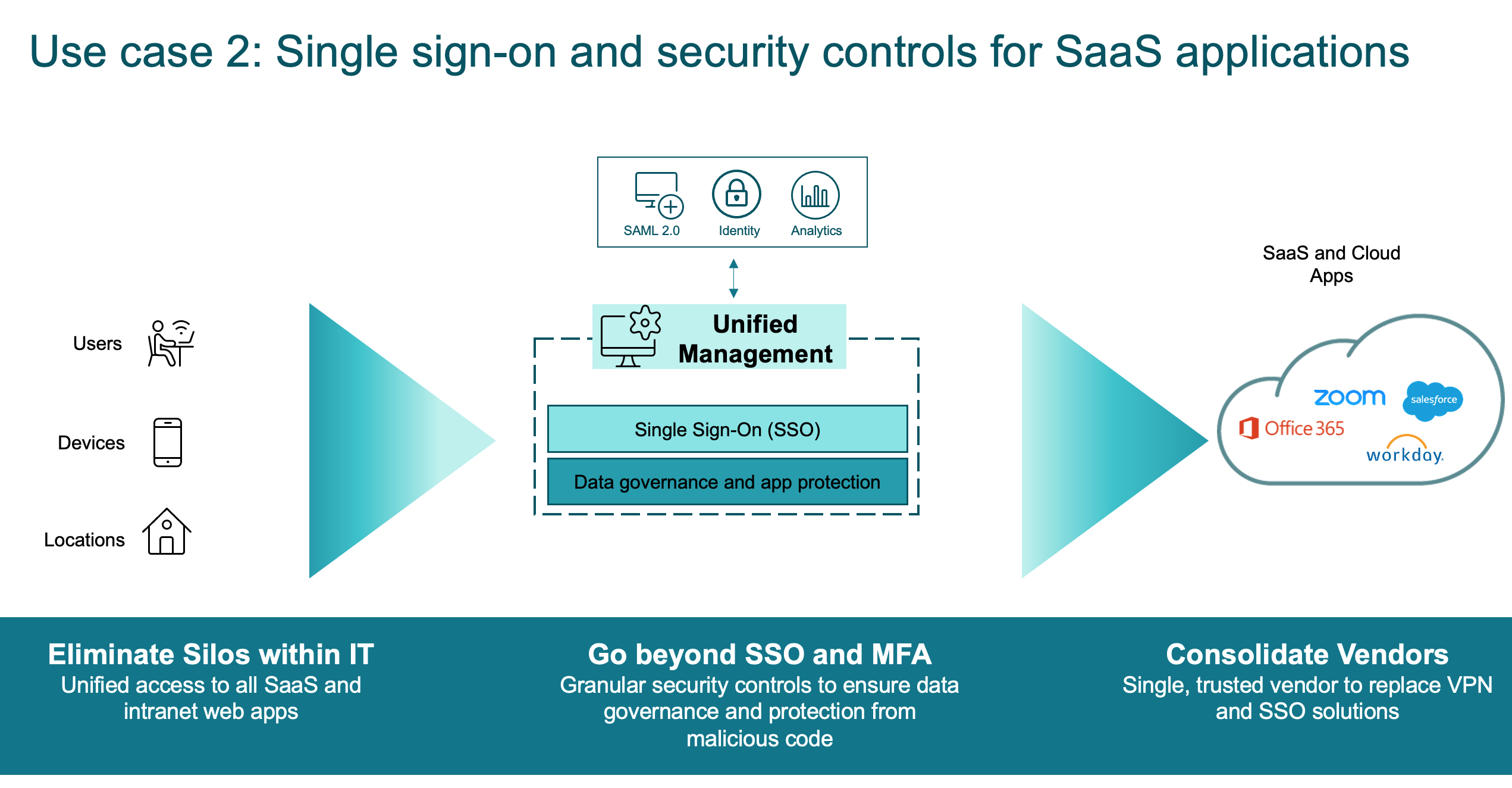
Single Sign-On
With adaptive authentication, organizations can provide strong authentication policies to help reduce the risk of compromised user accounts. The single sign-on capabilities of Secure Private Access use the same adaptive authentication policies for all SaaS, private web, and client/server apps.
A single set of credentials helps organizations solve a few user and admin experience challenges:
- Users do not have to remember a user name and password for each application
- Users do not have to create complex passwords for each application
- Users do not have to setup/configure MFA keys/tokens for each application
- Users do not have to start a VPN connection to access an internal web application
- Admins can disable access to all applications by disabling the user’s primary identity
Once the user is authenticated with a primary identity, the single sign-on feature in Citrix Cloud™ uses SAML assertions to automatically fulfill subsequent authentication challenges to SaaS and web apps. There are 300+ SAML SSO templates available for quick configuration for web and SaaS apps.

Some organizations might have already standardized on an SSO provider. Secure Private Access is able to utilize third party SSO providers while still applying adaptive access policies onto the user sessions.
For additional information on Single Sign-On, please review the following papers:
| Links | ||
|---|---|---|
 |
More information: SSO for SaaS Apps | |
 |
More information: SSO for Private Web Apps | |
 |
More information: IdP Chaining | |
Application Access
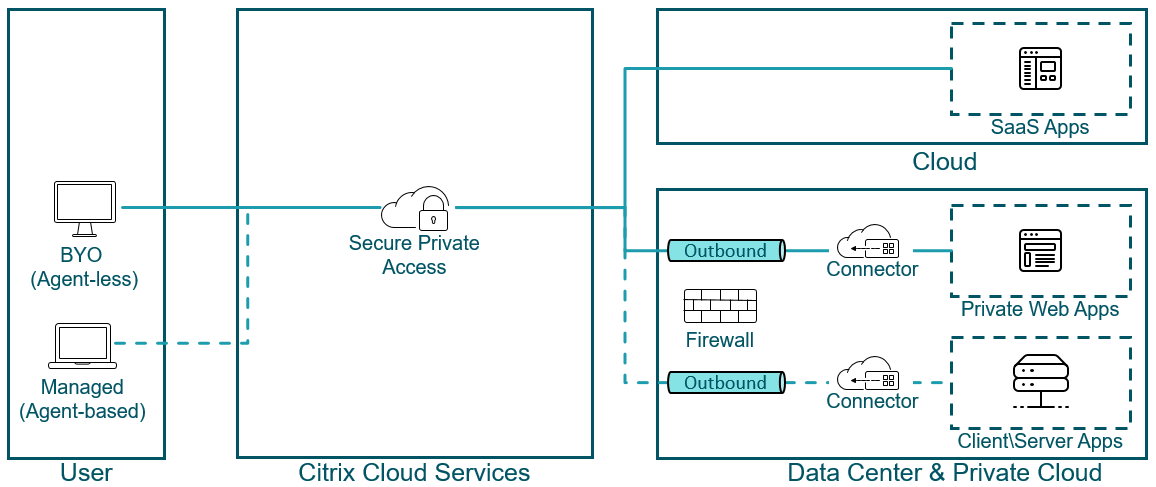
Secure Private Access is able to create a connection to on-premises web apps without relying on a VPN. This VPN-less connection utilizes an on-prem deployed Connector Appliance. The Connector Appliance creates an outbound control channel to the organization’s Citrix Cloud subscription. From there, Secure Private Access is able to tunnel connections to the internal web apps without the need for a VPN.
When accessing SaaS apps and private web apps, Secure Private Access provides the connection without the need for an agent on the endpoint. However, when accessing a private client/server app, the user must have an agent deployed on the endpoint.
To see the user’s experience when accessing these different types of resources from Secure Private Access, please view the following demos.
| Links | ||
|---|---|---|
 |
View demo: Private Client/Server App Access | |
 |
View demo: Private Web App Access | |
 |
View demo: Public SaaS App Access | |
Browser Security
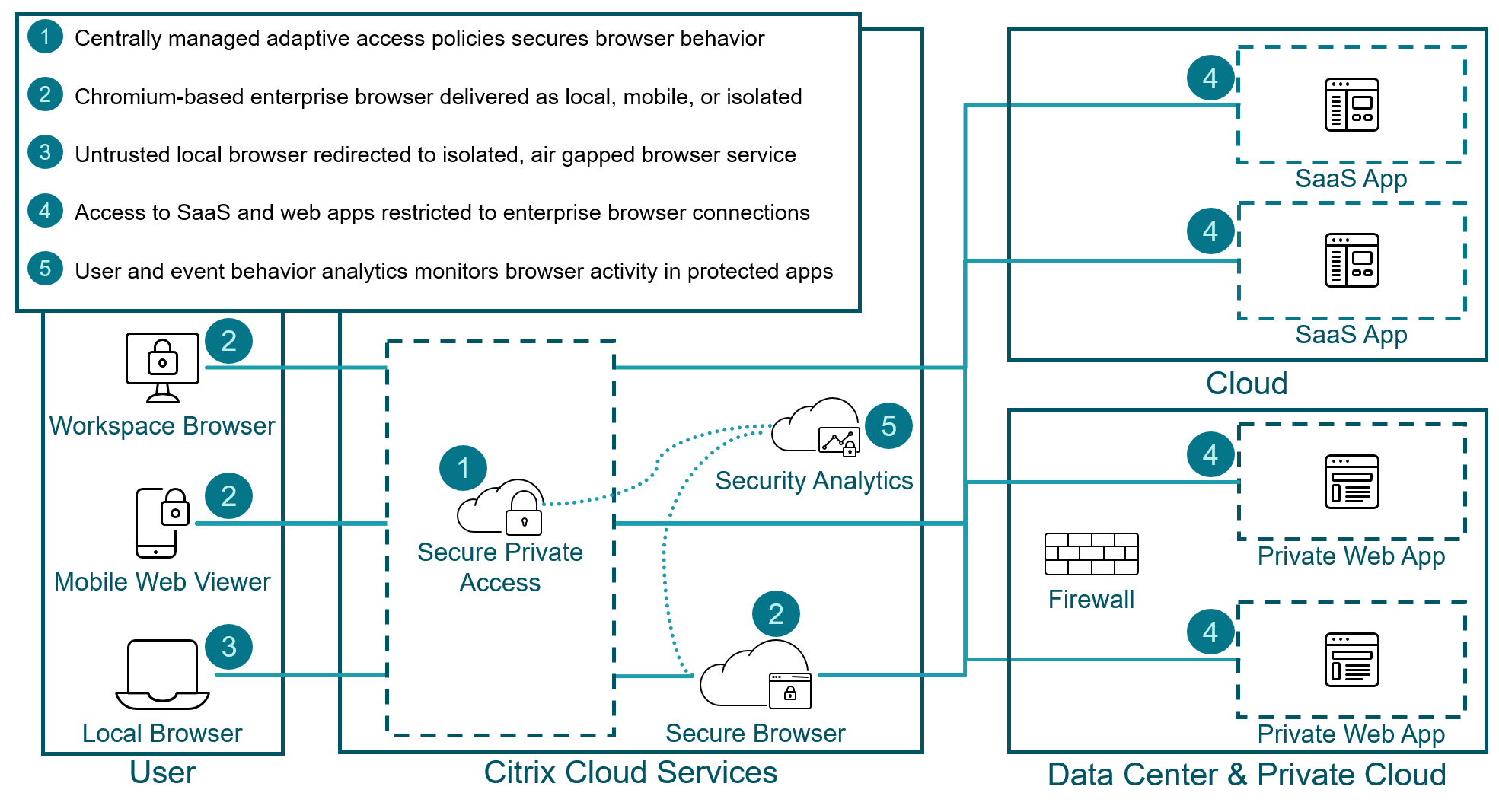
Secure Private Access enables end users to safely browse the internet with a centrally managed and secured enterprise browser. When an end user launches a SaaS or private web app, several decisions are dynamically made to decide how best to serve this application.
Secure Private Access provides the following three ways:
- Local Browser: Launch the application in the user’s traditional, unmanaged local browser.
- Enterprise Browser: Launch the application with Citrix Enterprise Browser™ (formerly Citrix Workspace™ Browser) on the local device. Enterprise Browser is an enterprise-ready browser with easy-to-apply, centrally-managed security restrictions.
- Isolated Enterprise Browser: Launch the application in a remote, air-gapped virtual browser instance with the Citrix Remote Browser Isolation™ service. The service utilizes Citrix Enterprise Browser and applies the same centrally-managed security restrictions.
- Mobile Enterprise Browser: Utilizes the mobile web viewer to deliver a secured, enterprise browser on mobile devices. The mobile web viewer utilizes Citrix Enterprise Browser and applies the same centrally-managed security restrictions.
Local Browser
The local browser is how most users and organizations deliver SaaS and private web apps to users. This approach trusts that the user and device are not accessing sensitive or confidential data. When following a zero trust strategy, the local browser is not a suitable solution.
Enterprise Browser
Citrix Enterprise Browser is an enterprise browser, based on Chrome, running on the endpoint. Enterprise Browser creates a security sandbox for the web session. Running locally gives end users the best performance for rendering webpages of SaaS and private web applications as the browser looks and acts like a user’s traditional browser.
The secure sandbox protects the end user and the enterprise against malware, performance degradation, data loss, and unintended end user behavior. With Enterprise Browser, organizations can centrally apply adaptive access policies that limits keyloggers, screen captures, clipboard operations, and more.
Watch this video to learn more:
Citrix Enterprise Browser incorporates the following adaptive access security capabilities:
- Keylogger protection
- Screen sharing protection
- Watermarking
- Download restrictions
- Printing restrictions
- Navigation restrictions
- Clipboard restrictions
Isolated Enterprise Browser
The Citrix Remote Browser Isolation service is a isolated, cloud hosted, enterprise browser. The Remote Browser Isolation service leverages Citrix Enterprise Browser except that it runs in an isolated, virtualized, and temporary cloud session. The hosted browser service provides a secure way to access internet and corporate browser-based applications. It creates an air gap between the browser and users, devices, and networks, protecting them from dangerous malware.
Watch this video to learn more:
If adaptive access policies are applied with policy restrictions in place, the Remote Browser Isolation service is automatically used if the user’s endpoint does not have a local version of Citrix Enterprise Browser. Secure Browser is often used in situations where Workspace App is not installed, like kiosks or personal devices.
Citrix Remote Browser Isolation service incorporates the following adaptive access security capabilities:
- Air-gapped\isolated
- Watermarking
- Download restrictions
- Printing restrictions
- Navigation restrictions
- Clipboard restrictions
Mobile Enterprise Browser
When on a mobile device, the security benefits of the Citrix Enterprise Browser are still applied with the mobile web viewer. The same adaptive access policy settings are applied with the Citrix Enterprise Browser, but the mobile web viewer provides a touch-based interface users are familiar with.
Watch this video to learn more:
The mobile web viewer for Workspace app incorporates the following adaptive access security capabilities:
- Watermarking
- Download restrictions
- Printing restrictions
- Navigation restrictions
- Clipboard restrictions
User and Experience Behavior Analytics (UEBA)
Administrators need visibility into their environment. The need to know about potential threats, usage, and performance. Secure Private Access sends user behavior information to the Analytics service to help organizations secure their SaaS apps, private web apps, and client server apps.
Security
Citrix Analytics for Security™ continuously assesses the behavior of Secure Private Access users to proactively detect and resolve security threats. It generates individualized user risk scores based on user behavior to surface potential high-risk users.
Analytics for Security detects malicious user activity and prevents harm to the business with prescriptive, automated remediation actions. The risk score generated can be used within Secure Private Access to automate security controls like watermarking, disable clipboard access, and prevent downloads with Adaptive Access policies.
Admins can create custom risk indicators using criteria like the following:
- App launch time
- App end time
- Print action
- Clipboard access
- URL Access
- Data upload
- Data download
The following provides demonstrations of these capabilities.
| Links | ||
|---|---|---|
 |
More Information: Analytics for Security | |
 |
More Information: Identity Risky User Behavior | |
Usage
Usage Analytics provides insights into the basic usage data of Secure Private Access. Admins get the visibility into how users interact with the SaaS and Web applications that are being used in their organization.
The usage data helps them to understand the user adoption and engagement of a product. The following metrics can help admins determine if apps are useful or should be slated for retirement.
- Number of unique users using the SaaS and Web applications
- Top SaaS and Web application users
- Number of SaaS and Web applications launched
- Top SaaS and Web applications
- Top domains accessed by the users
- Total amount of data uploaded and downloaded across users, applications, and domains
Use Cases
VPN-less Access
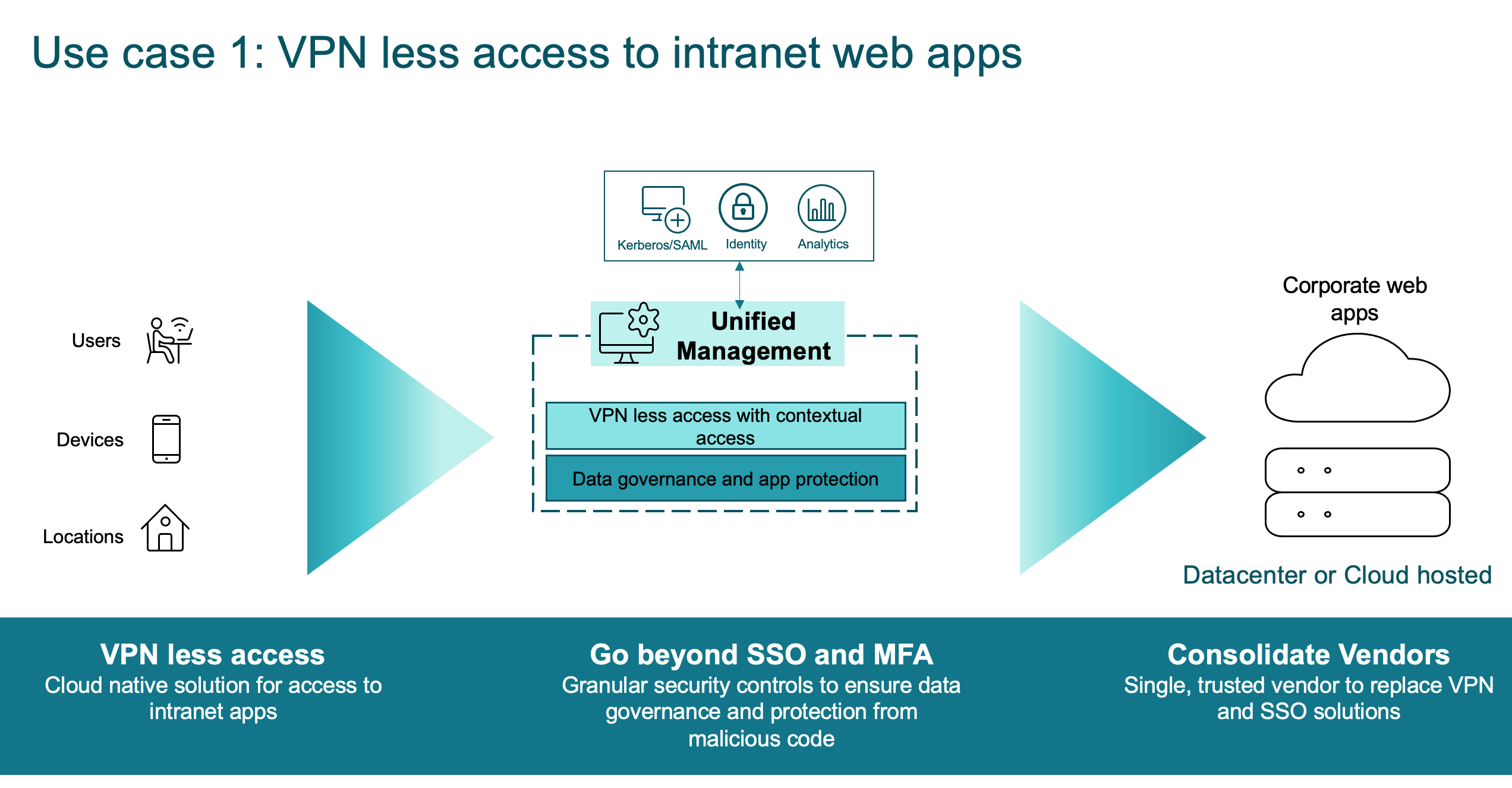
Citrix Secure Private Access complements or replaces existing VPN solutions with a Zero Trust solution that allows access for remote users without a VPN. This solution solves many challenges with providing access to internal resources for external users. With Secure Private Access there is:
- No network device to manage, maintain, and secure – reducing appliance sprawl
- No public IP address required as the cloud services are able to contact internal resources via the Connector Appliances
- No firewall rules required as the Connector Appliance establishes outbound connections to the cloud-based services (no inbound communication required)
- A global deployment, organizations are automatically routed/rerouted to the optimal Secure Private Access service, greatly simplifying any configurations required by the organization.
- No change to the underlying data center infrastructure.
Secure Private Access is able to create a connection to on-premises web apps without relying on a VPN. This VPN-less connection utilizes an on-prem deployed Connector Appliance. The Connector Appliance creates an outbound control channel to the organization’s Citrix Cloud subscription. From there, Secure Private Access is able to tunnel connections to the internal web apps while providing SSO. VPN-less access not only improves security and privacy but also improves end user experience.
| Links | ||
|---|---|---|
 |
View demo: ZTNA vs VPN - Logon Experience | |
 |
View demo: ZTNA vs VPN - Port Scanning | |
SSO and Adaptive Access for Browser-based Apps
Secure Private Access offers single sign-on and adaptive access policies for web and SaaS apps. With adaptive authentication, organizations can tailor their authentication flow to align with the business. Adaptive authentication protects an organization’s existing identity ecosystem investment and eases their move to cloud without a rip and replace forklift upgrade.
Although an authorized SaaS app is considered safe, content in the SaaS app actually can be dangerous - constituting a security risk. Adaptive access policies provides IT with a way to enforce security policies on both web and SaaS applications that they provision to employees. These policies protect data stored in these applications by applying the following controls:
- Watermarking
- Restrict navigating
- Restrict downloads
- Restrict keylogging
- Restrict screen capture
- Restrict printing
More remote workers mean more remote meetings and web conferencing through various applications. These meetings usually require employees to share their screen, which opens the possibility of exposing sensitive data by mistake. The keylogger and screen capture restrictions helps protect against endpoint malware and user mistakes. If users accidently share financial data in a web conference, attendees only see a blank screen. This protection also applies to the most common snipping tools, print-screen tools, screen capture, and recording tools.
Browser isolation for internet traffic protects end users and enterprises from web-based threats. With Enterprise Browser and the Remote Browser Isolation service, admins get a choice to access sites in a local Chrome based browser a cloud hosted and isolated Enterprise Browser instance. With the service, possible attacks are contained in the cloud. Secure Browser run destroys the virtualized Enterprise Browser instance after use. When a new session starts, the user receives a new Enterprise Browser instance. Policies control functions like “Copy and Paste” so that no files or data can reach the corporate network.
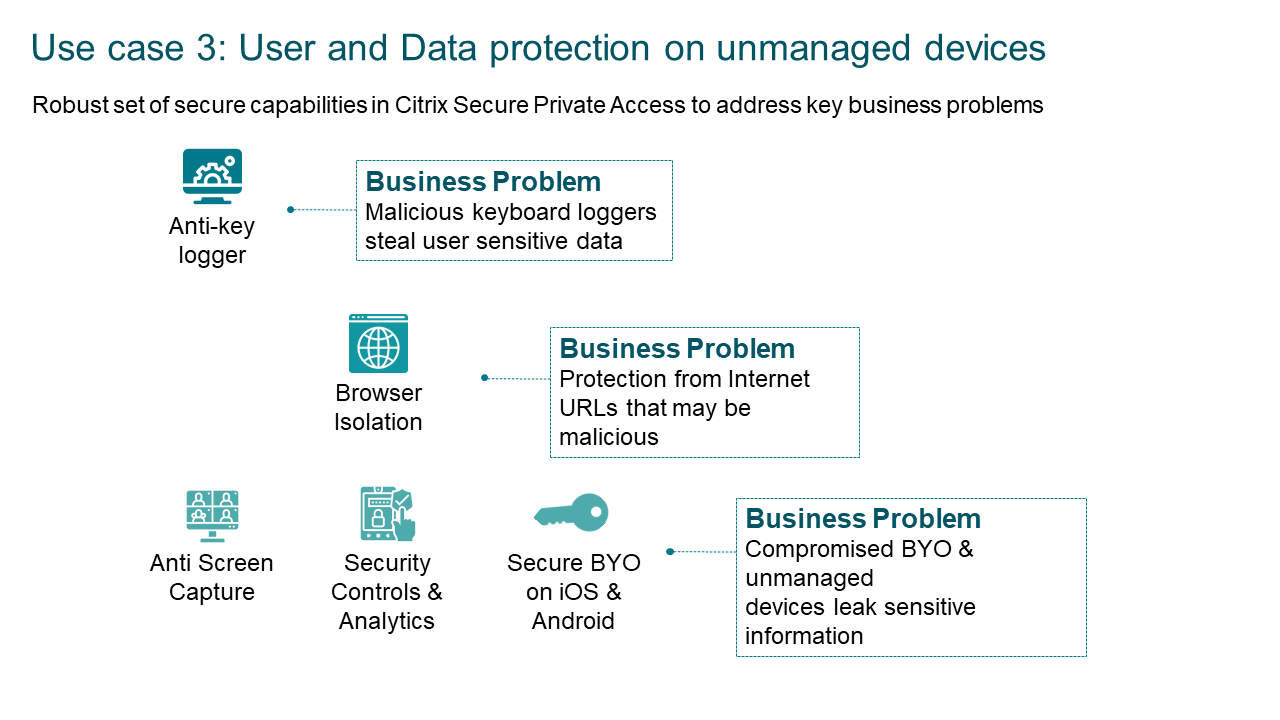
Protecting User and Corporate Data on BYO and Unmanaged Endpoints
Using adaptive authentication and access policies, Secure Private Access gives admins the ability to protect their organizations from data loss and credential theft. Adaptive authentication and access policies are even more critical when employees use personal devices to access corporate resources.
Adaptive access policies can enable keylogger and screen capture protection features. The feature protects employees from dormant screen-grabbing malware or keyloggers that can potentially capture passwords or personal information.
Keylogger and screen capture protections work by controlling access to specific API calls of the underlying OS required to capture screens or keyboard presses. These policies can protect against even the most customized and purpose-built hacker tools. It helps to secure any virtual or web application that employees use within Citrix Secure Private Access and authentication dialog boxes (preventing password leaks).
The keylogger and screen capture protections feature makes the text entered by the user indecipherable by encrypting it before a keylogging tool can access it. A keylogger installed on the client endpoint reading the data would capture gibberish characters instead of the keystrokes the user is typing.
More Use Cases
| Links | ||
|---|---|---|
 |
Read more: Tech Brief: Secure Private Access - Use Cases | |