-
-
-
-
MITRE ATT&CK Integration
-
-
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
MITRE ATT&CK Integration
MITRE ATT&CK
The MITRE ATT&CK® framework is a knowledge base of adversary tactics and techniques based on real-world observations of cybersecurity threats. With the help of ATT&CK, different stakeholders (offense, defense, SOCs, third-party vendors, and so on) can speak the same language to describe attacks on enterprise IT and mobile devices. While there are other similar frameworks available, ATT&CK is the de-facto industry standard.
Integration With uberAgent® ESA
When an uberAgent ESA Threat Detection rule matches suspicious activity, uberAgent’s endpoint agent sends an event to its configured SIEM backend. uberAgent annotates Threat Detection events with ATT&CK technique IDs.
Annotations are part of the ESA Threat Detection rule specification. Implementation details can be found here. Below is a rule sample:
[ActivityMonitoringRule]
# Detects suspicious DNS queries known from Cobalt Strike beacons
RuleName = Cobalt Strike DNS Beaconing
EventType = Dns.Query
Tag = cobalt-strike-dns-beaconing
RiskScore = 100
Annotation = {"mitre_attack": ["T1071", "T1071.004"]}
Query = (Dns.QueryRequest like r"aaa.stage.%" or Dns.QueryRequest like r"post.1%")
GenericProperty1 = Dns.QueryRequest
GenericProperty2 = Dns.QueryResponse
<!--NeedCopy-->
Visualization
The uberAgent ESA Splunk app processes the Threat Detection events with technique ID annotations and adds context like the technique’s name, its description and detection, and the URL to the technique on the MITRE website.
This processed information is visualized in the Threat Detection Events dashboard. In the screenshot below you can see the number of events by technique ID, and the distribution of events by ID over time.
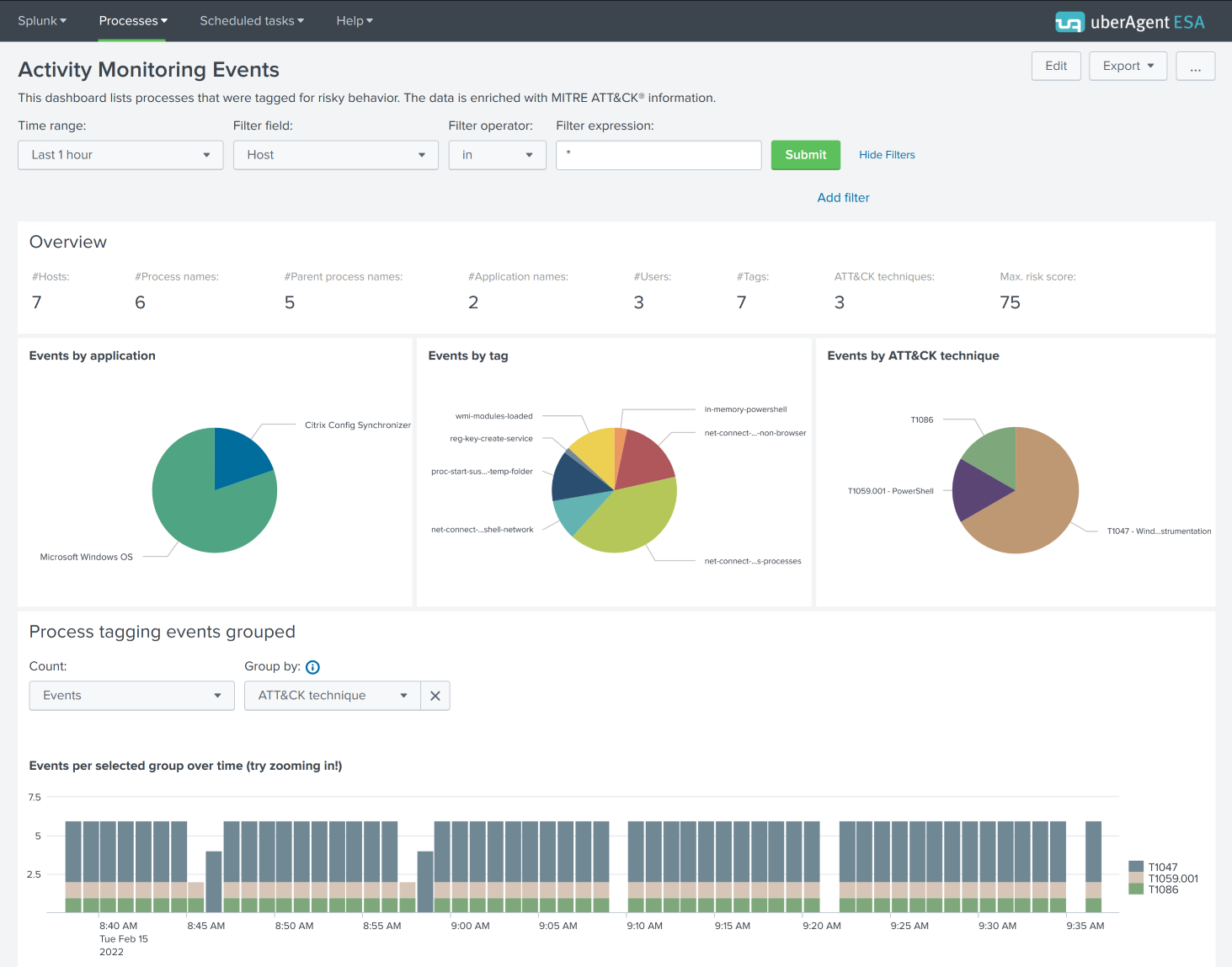
The further you scroll down the more details you get. The first table in the screenshot below shows details for each technique. A click on a technique row lists all events where the technique was detected in the second table in the screenshot below.
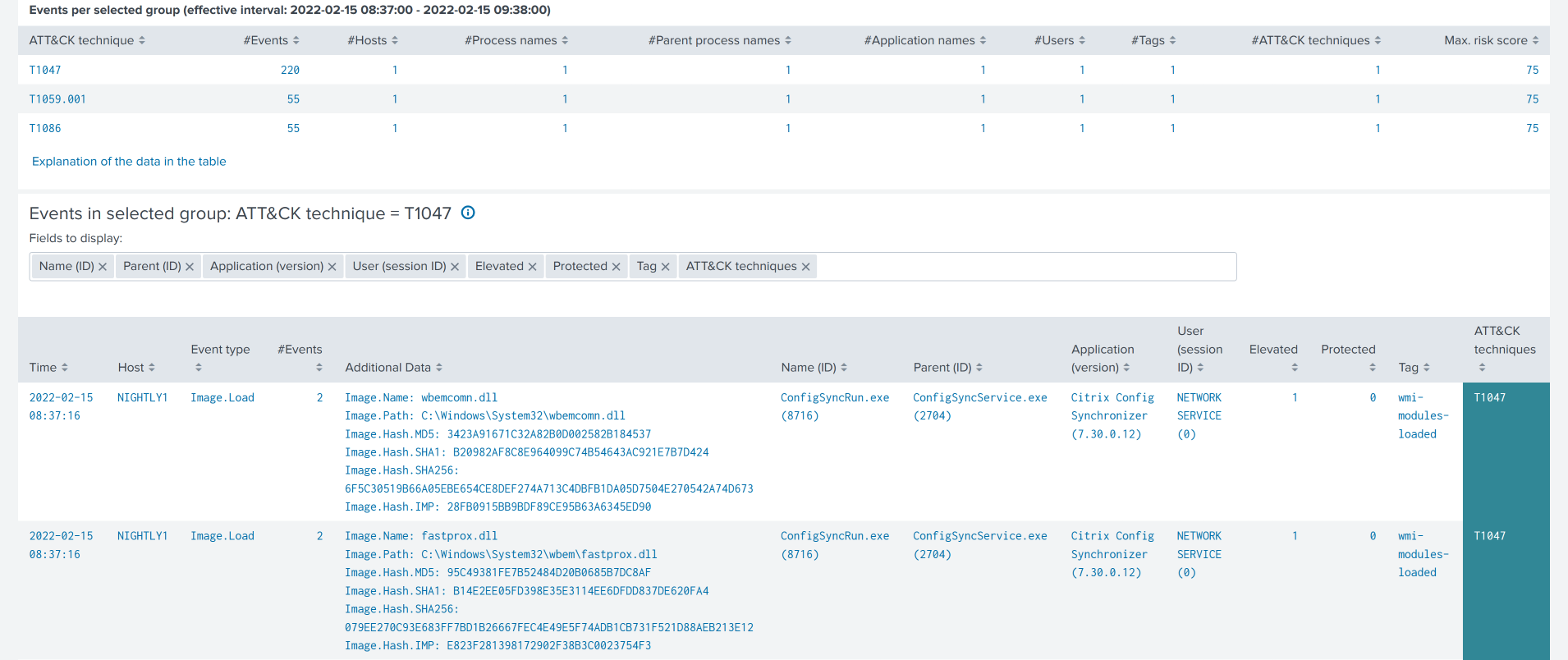
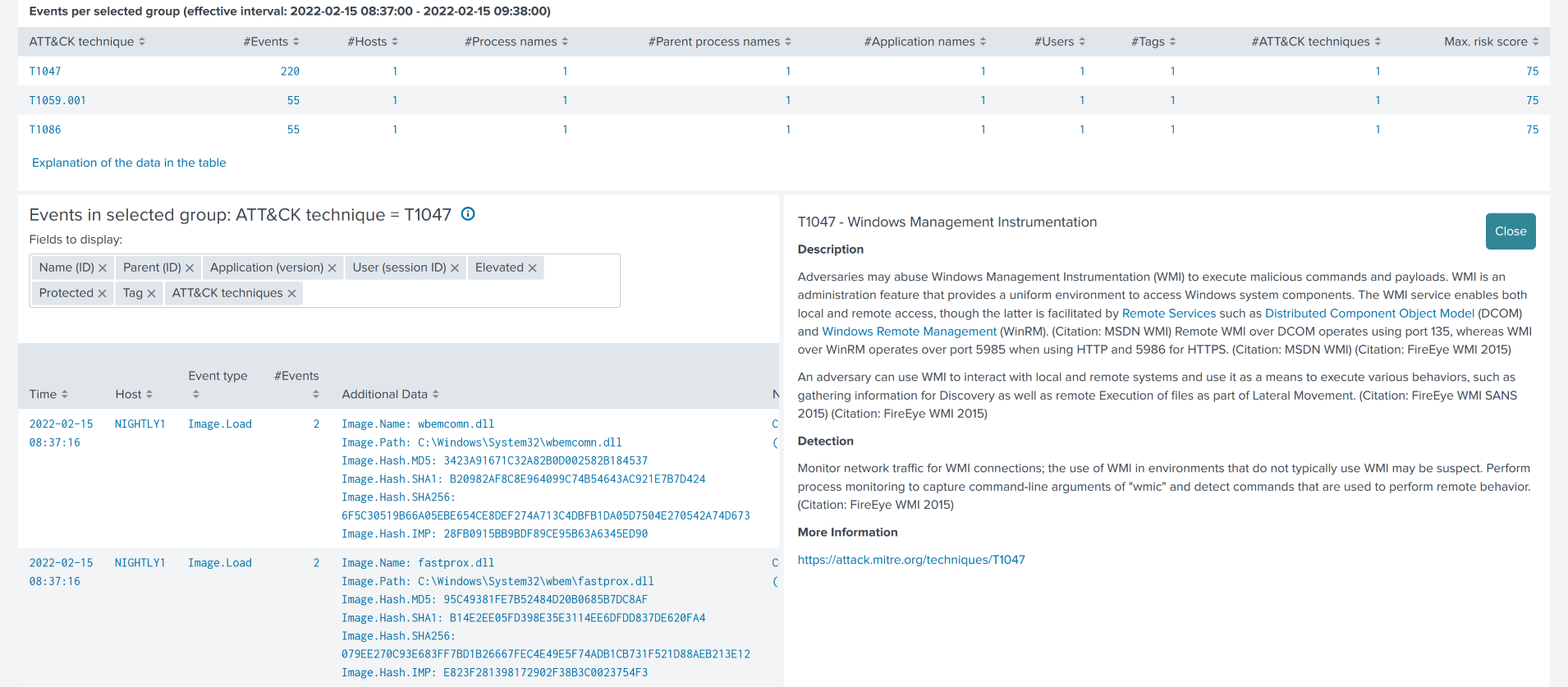
Note that the rightmost column ATT&CK techniques is highlighted in blue. When you click on it you get detailed ATT&CK information on the technique ID in a pop-up.
Installation
The ATT&CK integration is enabled by default. You don’t need to do anything except install the uberAgent ESA Splunk app on your Splunk search heads. The installation is documented here.
Keeping ATT&CK Up-to-Date
Every uberAgent release includes the latest ATT&CK information. If you notice that MITRE made changes to their ATT&CK framework and want the updated data in Splunk, you have two options:
- Wait for the next uberAgent version and update the ESA Splunk app
-
Update the CSV file for the ATT&CK Splunk lookup manually
- The current CSV is always accessible in our GitHub repository. Download the file
annotation_mitre_attack.csvfrom there. - Replace the file in
$SPLUNK_HOME/etc/apps/uberAgent_ESA/lookups - Restart Splunk
- The current CSV is always accessible in our GitHub repository. Download the file
- Context: in the year 2021, MITRE made five changes to the source
uberAgent ESA and Splunk Enterprise Security
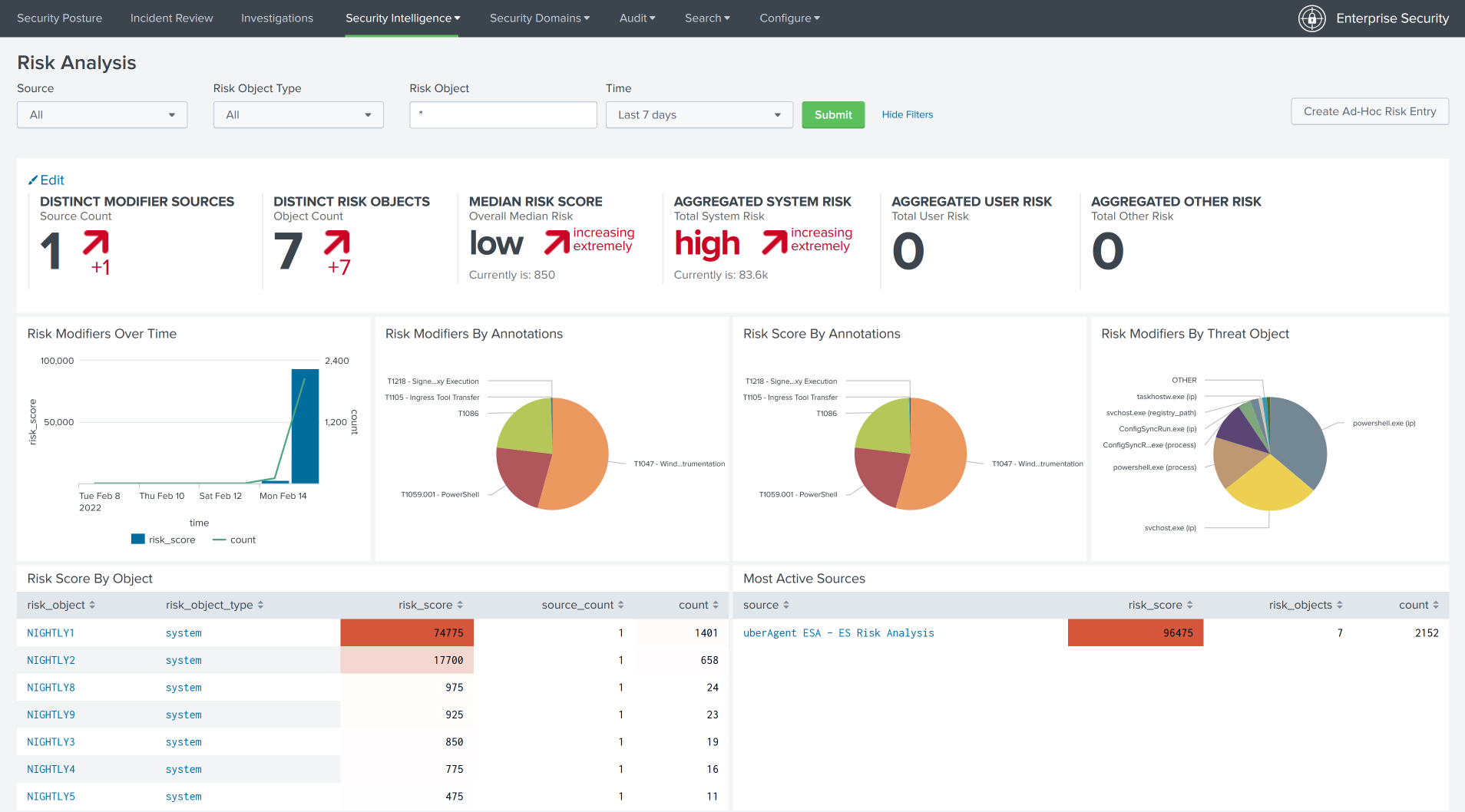
Splunk Enterprise Security also has an ATT&CK integration and uberAgent integrates with ES, too. Below is a short summary of both integrations to avoid confusion.
uberAgent MITRE ATT&CK Data in uberAgent ESA Dashboards
The uberAgent ESA Splunk app visualizes the data collected by uberAgent’s endpoint agents. The uberAgent ESA Splunk app is compatible with Splunk Enterprise and Cloud. It has an ATT&CK integration built-in that can be used without the need to purchase Splunk Enterprise Security.
Use it when:
- You don’t have Splunk Enterprise Security
- You only need ATT&CK and no other cybersecurity framework
uberAgent MITRE ATT&CK Data in Splunk Enterprise Security
Splunk Enterprise Security is a paid premium app developed by Splunk that needs to be licensed on top of Splunk Enterprise or Cloud. It comes with support for multiple cybersecurity frameworks, ATT&CK is one of them. If you are an ES customer you may want to install the uberAgent ESA ES companion app to enjoy the benefits of uberAgent ESA data in Enterprise Security, enriched with data from cybersecurity frameworks (more information).
Use it when:
- You have Splunk Enterprise Security
- You need more cybersecurity frameworks than ATT&CK
Note: in this scenario, you can use both the uberAgent ESA app and Splunk’s Enterprise Security dashboards.
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.