Security considerations
This article discusses Secure Mail security considerations and specific settings that you can enable to help increase data security.
Microsoft IRM and AIP email rights protection support
Secure Mail for Android and iOS support messages protected with Microsoft Information Rights Management (IRM) and the Azure Information Protection (AIP) solution. This support is subject to the configured IRM policy on Citrix Endpoint Management.
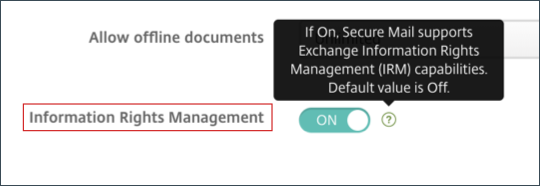
This feature allows organizations that use IRM to apply protection to messaging content. The feature also allows mobile device users to be able to create and consume rights-protected content. By default IRM support is Off. To enable IRM support, set the Information Rights Management policy to On.
To enable Information Rights Management in Secure Mail
- Log on to Endpoint Management and navigate to Configure > Apps and click Add.
- In the Add App screen, click MDX.
- In the App Information screen, enter the app details and click Next.
- Based on your device OS, select and upload the .mdx file.
- Enable Information Rights Management under App Settings.
Note:
Enable Information Rights Management for both iOS and Android.
When you receive a rights protected email
When users receive a mail with protected content, they see the following screen:
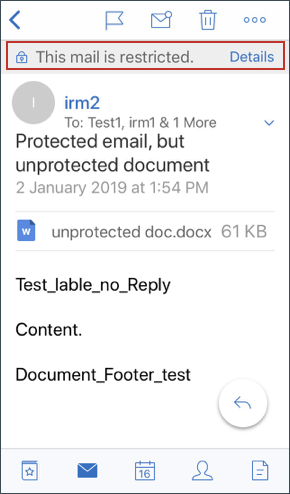
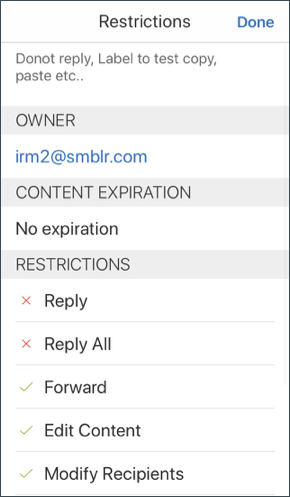
To view details about the rights that user is entitled to, tap Details.
When you compose a rights protected email
When users compose a mail, they can set restriction profiles to enable email protection.
To set restrictions to your email:
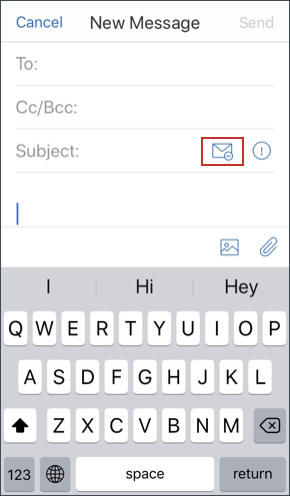
- Log in to Secure Mail and tap the Compose icon.
-
In the compose screen, tap the Email Restriction icon.
-
In the Restriction Profiles screen, tap the desired restrictions to apply to the email and then click back.
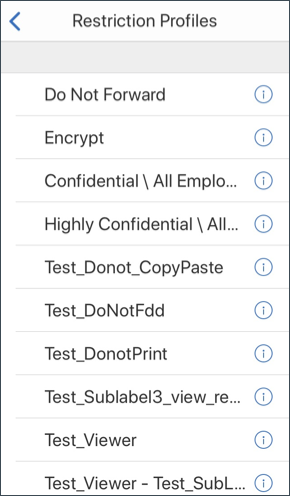
The applied restrictions appear below the subject field.
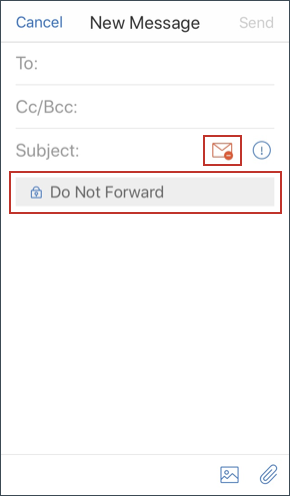
Some organizations may require strict adherence to their IRM policy. Users with access to Secure Mail may attempt to bypass the IRM policy by tampering with Secure Mail, the operating system, or even the hardware platform.
Although Endpoint Management can detect certain attacks, consider the following precautionary measures to increase security:
- Review the security guidance supplied by the device vendor.
- Configure devices accordingly, using Endpoint Management capabilities or otherwise.
- Provide guidance to your users for the appropriate use of IRM features, including Secure Mail.
- Deploy additional third-party security software to resist this type of attack.
Email security classifications
Secure Mail for iOS and Android supports email classification markings, enabling users to specify security (SEC) and dissemination limiting markers (DLM) when sending emails. SEC markings include Protected, Confidential, and Secret. DLM includes Sensitive, Legal, or Personal. When composing an email, a Secure Mail user can select a marking to indicate the classification level of the email, as shown in the following images.
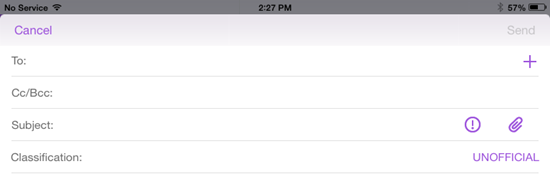

Recipients can view the classification marking in the email subject. For example:
- Subject: Planning [SEC = PROTECTED, DLM = Sensitive]
- Subject: Planning [DLM = Sensitive]
- Subject: Planning [SEC = UNCLASSIFIED]
Email headers include classification markings as an Internet Message Header Extension, shown in bold text in this example:
Date: Fri, 01 May 2015 12:34:50 +530
Subject: Planning [SEC = PROTECTED, DLM = Sensitive]
Priority: normal
X-Priority: normal X-Protective-Marking: VER-2012.3, NS=gov.au,SEC = PROTECTED, DLM = Sensitive,ORIGIN=operations@example.com
From: operations@example.com
To: Team <mylist@example.com>
MIME-Version: 1.0 Content-Type: multipart/alternative;boundary="_com.example.email_6428E5E4-9DB3-4133-9F48-155913E39A980"
Secure Mail only displays classification markings. The app does not take actions based on those markings.
When a user replies to or forwards an email that has classification markings, the SEC and DLM values default to the marking of the original email. The user can choose a different marking. Secure Mail does not validate such changes in relation to the original email.
You configure email classification markings through the following MDX policies.
-
Email classification: If On, Secure Mail supports email classification markings for SEC and DLM. Classification markings appear in email headers as “X-Protective-Marking” values. Be sure to configure the related email classification policies. Default value is Off.
-
Email classification namespace: Specifies the classification namespace that is required in the email header by the classification standard used. For example, the namespace “gov.au” appears in the header as “NS=gov.au”. Default value is empty.
-
Email classification version: Specifies the classification version that is required in the email header by the classification standard used. For example, the version “2012.3” appears in the header as “VER=2012.3”. Default value is empty.
-
Default email classification: Specifies the protective marking that Secure Mail applies to an email if a user does not choose a marking. This value must be in the list for the Email classification markings policy. Default value is UNOFFICIAL.
-
Email classification markings: Specifies the classification markings to be made available to users. If the list is empty, Secure Mail does not include a list of protective markings. The markings list contains value pairs that are separated by semicolons. Each pair includes the list value that appears in Secure Mail and the marking value that is the text appended to the email subject and header in Secure Mail. For example, in the marking pair “UNOFFICIAL,SEC=UNOFFICIAL;”, the list value is “UNOFFICIAL” and the marking value is “SEC=UNOFFICIAL”.
Default value is a list of classification markings that you can modify. The following markings are provided with Secure Mail.
- UNOFFICIAL,SEC=UNOFFICIAL
- UNCLASSIFIED,SEC=UNCLASSIFIED
- For Official Use Only,DLM=For-Official-Use-Only
- Sensitive,DLM=Sensitive
- Sensitive:Legal,DLM=Sensitive:Legal
- Sensitive:Personal,DLM=Sensitive:Personal
- PROTECTED,SEC=PROTECTED
- PROTECTED+Sensitive,SEC=PROTECTED
- PROTECTED+Sensitive:Legal,SEC=PROTECTED DLM=Sensitive:Legal
- PROTECTED+Sensitive:Personal,SEC=PROTECTED DLM=Sensitive:Personal
- PROTECTED+Sensitive:Cabinet,SEC=PROTECTED,DLM=Sensitive:Cabinet
- CONFIDENTIAL,SEC=CONFIDENTIAL
- CONFIDENTIAL+Sensitive,SEC=CONFIDENTIAL,DLM=Sensitive
- CONFIDENTIAL+Sensitive:Legal,SEC=CONFIDENTIAL DLM=Sensitive:Legal
- CONFIDENTIAL+Sensitive:Personal,SEC=CONFIDENTIAL,DLM=Sensitive:Personal
- CONFIDENTIAL+Sensitive:Cabinet,SEC=CONFIDENTIAL DLM=Sensitive:Cabinet
- SECRET,SEC=SECRET
- SECRET+Sensitive,SEC=SECRET,DLM=Sensitive
- SECRET+Sensitive:Legal,SEC=SECRET,DLM=Sensitive:Legal
- SECRET+Sensitive:Personal,SEC=SECRET,DLM=Sensitive:Personal
- SECRET+Sensitive:Cabinet,SEC=SECRET,DLM=Sensitive:Cabinet
- TOP-SECRET,SEC=TOP-SECRET
- TOP-SECRET+Sensitive,SEC=TOP-SECRET,DLM=Sensitive
- TOP-SECRET+Sensitive:Legal,SEC=TOP-SECRET DLM=Sensitive:Legal
- TOP-SECRET+Sensitive:Personal,SEC=TOP-SECRET DLM=Sensitive:Personal
- TOP-SECRET+Sensitive:Cabinet,SEC=TOP-SECRET DLM=Sensitive:Cabinet
iOS data protection
Enterprises that must meet Australian Signals Directorate (ASD) data protection requirements can use the Enable iOS data protection policies for Secure Mail and Secure Web. By default, the policies are Off.
When Enable iOS data protection is On for Secure Web, Secure Web uses Class A protection level for all files in the sandbox. For details about Secure Mail data protection, see Australian Signals Directorate Data Protection. If you enable this policy, the highest data protection class is used so there is no need to also specify the Minimum data protection class policy.
To change the Enable iOS data protection policy
-
Use the Endpoint Management console to load the Secure Web and Secure Mail MDX files to Endpoint Management: For a new app, navigate to Configure > Apps > Add and then click MDX. For an upgrade, see Upgrade MDX or enterprise apps.
-
For Secure Mail, browse to the App settings, locate the Enable iOS data protection policy, and set it to On. Devices running older operating system versions are not affected when this policy is enabled.
-
For Secure Web, browse to the App settings, locate the Enable iOS data protection policy, and set it to On. Devices running older operating system versions are not affected when this policy is enabled.
-
Configure the app policies as usual and save your settings to deploy the app to the Endpoint Management app store.
Australian Signals Directorate Data Protection
Secure Mail supports Australian Signals Directorate (ASD) data protection for those enterprises that must meet ASD computer security requirements. By default, the Enable iOS data protection policy is Off and Secure Mail provides Class C data protection or uses the data protection set in the provisioning profile.
If the policy is On, Secure Mail specifies the protection level when creating and opening files in the app sandbox. Secure Mail sets Class A data protection on:
- Outbox items
- Photos from the camera or camera roll
- Images pasted from other apps
- Downloaded file attachments
Secure Mail sets Class B data protection on:
- Stored mail
- Calendar items
- Contacts
- ActiveSync policy files
Class B protection enables a locked device to sync and enables downloads to complete if a device is locked after the download starts.
With data protection enabled, queued outbox items are not sent when a device is locked because the files cannot be opened. If the device terminates and then restarts Secure Mail when a device is locked, Secure Mail cannot sync until the device is unlocked and Secure Mail starts.
Citrix® recommends that, if you enable this policy, you enable Secure Mail logging only when needed to avoid the creation of log files with Class C data protection.
Obscure screen contents
Secure Mail for Android and iOS supports screen obscuring when the app enters the background. This feature enhances user privacy, protects sensitive data, and prevents unauthorized access. To enable this feature for Secure Mail on iOS or Android devices, see the following sections.
On iOS devices:
- Sign in to the Citrix Endpoint Management console using administrator credentials.
- Navigate to Configure > Apps > MDX.
- Select the iOS option under the Platform section.
-
Enable the Obscure screen contents option under the App Restrictions section.
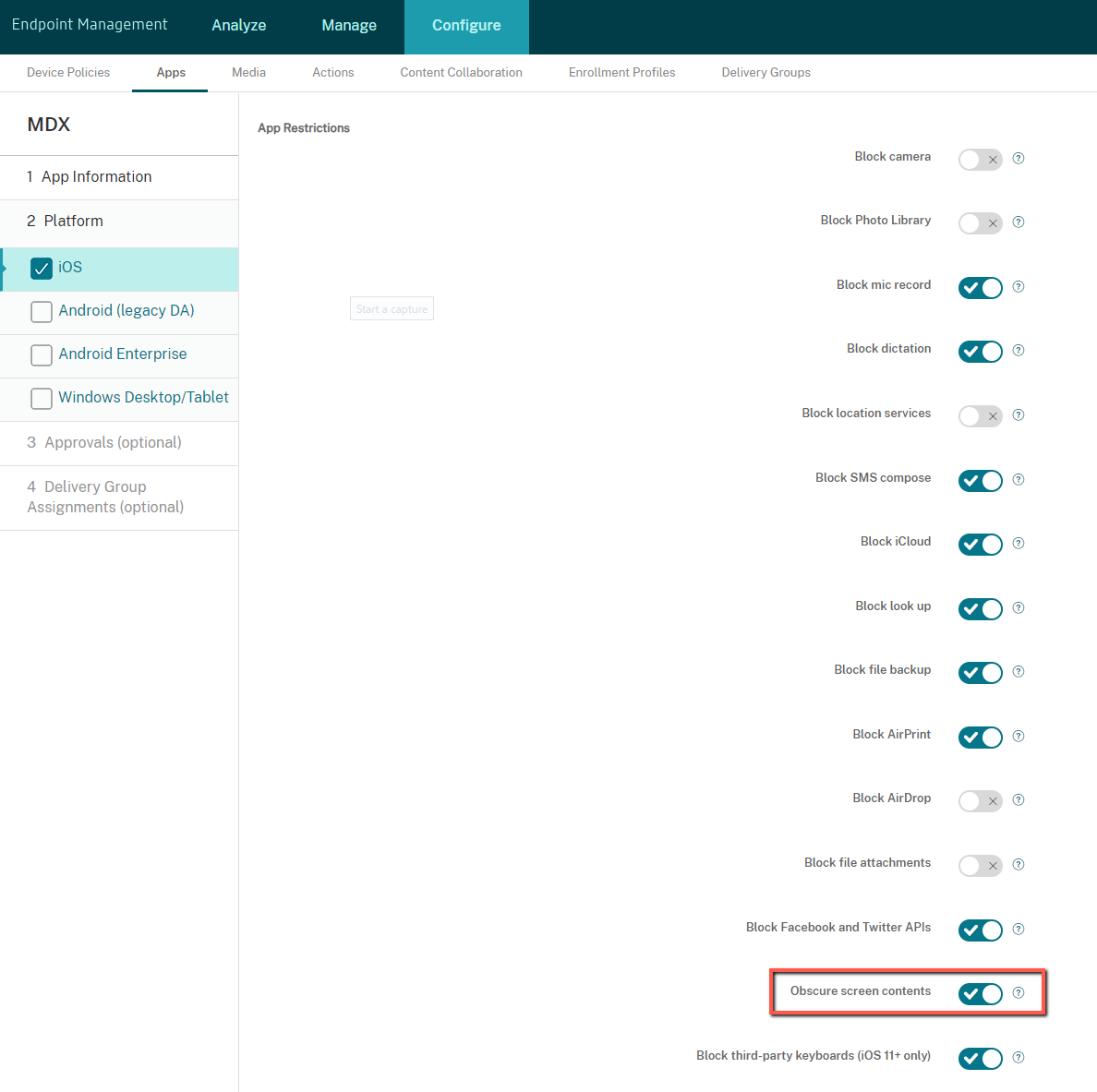
Once you enable the Obscure screen contents option, Secure Mail shows a gray screen when the app goes into the background.

On Android devices:
To obscure the Secure Mail app content, you can use the policy we use for restricting screen capture, known as the Allow screen capture policy. Disabling this policy also obscures app content when the app goes into the background. For more information on disabling the Allow screen capture policy, see the Android settings in the Citrix Endpoint Management documentation.