Device Posture overview
Citrix Device Posture service is a cloud-based solution that helps admins to enforce certain requirements that the end devices must meet to gain access to Citrix DaaS (virtual apps and desktops) or Citrix Secure Private Access resources (SaaS, Web apps, TCP, and UDP apps). Establishing device trust by checking the device’s posture is critical to implement zero-trust-based access. Device Posture service enforces zero trust principles in your network by checking the end devices for compliance (managed/BYOD and security posture) before allowing an end user to log in.
Prerequisites
-
Licensing requirements: The Device Posture service is available as part of the Universal Hybrid Multi Cloud License (UHMC) and Platform License (CPL). For more information, see https://www.citrix.com/buy/licensing/product.html.
-
Supported platforms:
- Windows (10 and 11)
- macOS 13 Ventura
- macOS 12 Monterey
- iOS
- Linux
Note:
-
A device running on a non-supported platform is marked as non-compliant by default. You can change the classification from Non-compliant to Denied login from the Settings tab on the Device Posture page. For the definitions of “compliant” and “non-compliant,” see Definitions.
-
A device that is running on a supported platform but does not match any pre-defined device posture policy is marked as non-compliant, by default. You can change the classification from Non-compliant to Denied login from the Settings tab on the Device Posture page.
-
For Device Posture service support on iOS, the EPA client is built in as part of the Citrix Workspace app for iOS. For details on the versions, see Citrix Workspace app for iOS.
-
For Linux support, reach out to Citrix Support to request enablement of Device Posture capabilities.
-
Citrix Device Posture client (EPA client): A lightweight application that must be installed on the endpoint device to run device posture scans. This application does not require local admin rights to download and install on an endpoint.
Note:
If you’re using a device certificate check, then you must install the EPA client with administrative rights.
-
Supported browsers: Chrome, Edge, and Firefox.
-
Firewall configuration: To allow the Device Posture service to update the EPA clients on an end device, the firewall/proxy must be configured to allow the following domains:
https://swa-ui-cdn-endpoint-prod.azureedge.nethttps://productioniconstorage.blob.core.windows.net- *.netscalergateway.net
- *.nssvc.net
- *.cloud.com
- *.pendo.io
- *.citrixworkspacesapi.net
Definitions
The terms “compliant” and “non-compliant” in reference to the Device Posture service are defined as follows.
- Compliant devices – A device that meets the pre-configured policy requirements and is allowed to log into the company’s network with full or unrestricted access to Citrix Secure Private Access resources or Citrix DaaS resources.
- Non-Compliant devices - A device that meets the pre-configured policy requirements and is allowed to log in into the company’s network with partial or restricted access to Citrix Secure Private Access resources or Citrix DaaS resources.
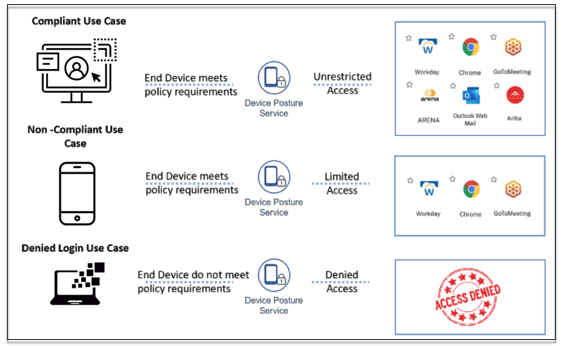
How it works
The admins can create device posture policies to check the posture of endpoint devices and determine whether an endpoint device is allowed or denied login. The devices, which are allowed to log in are further classified as compliant or non-compliant. Users can log in from a browser or the Citrix Workspace™ app.
Following are the high-level conditions used to classify a device as compliant, non-compliant, and denied login.
- Compliant devices – A device that meets the pre-configured policy requirements and is allowed to log in into the company’s network with full or unrestricted access to Citrix Secure Private Access™ resources or Citrix DaaS resources.
-
Non-Compliant devices - A device that meets the pre-configured policy requirements and is allowed to log in into the company’s network with partial or restricted access to Citrix Secure Private Access resources or Citrix DaaS resources based on your DaaS and Secure Private Access configuration for Device Posture.
- DaaS: Administrators can specify the delivery groups to restrict access for non-compliant devices. For details on how to configure restricted access to delivery groups, see Citrix DaaS configuration with Device Posture.
- Secure Private Access: Administrators can choose specific applications to restrict access for these devices. For details on how to restrict access to specific applications, see Citrix Secure Private Access configuration with Device Posture.
- Denied login: - A device that fails to meet the policy requirements is denied login.
The classification of devices as compliant, non-compliant, and denied login is passed onto the Citrix DaaS and Citrix Secure Private Access service that in turn uses the device classification to provide smart access capabilities.
Note:
- The device posture policies must be configured specifically for each platform. For example, for macOS, an admin can allow access for the devices that have a specific OS version. Similarly, for Windows, the admin can configure policies to include a specific authorization file, registry settings, and so on.
- Device posture scans are done only during pre-authentication/before logging in.
- For definitions of “compliant” and “non-compliant,” see Definitions.
Scans supported by the Device Posture service
The following scans are supported by the Citrix Device Posture service:
| Windows | macOS | iOS | Linux |
|---|---|---|---|
| Citrix Workspace App Version | Citrix Workspace App Version | Citrix Workspace App Version | - |
| OS Version | OS Version | OS Version | OS Version |
| File (Exists, Last Modified Time, MD5) | File (Exists, Last Modified Time, MD5) | - | File (Exists, Last Modified Time, MD5) |
| Geo Location | Geo Location | - | - |
| Network Location | Network Location | - | - |
| MAC Address | MAC Address | - | - |
| Process (Exists, MD5, SHA1) | Process (Exists, MD5, SHA1) | - | Process (Exists, MD5, SHA1) |
| Microsoft Endpoint Manager | Microsoft Endpoint Manager | - | - |
| CrowdStrike | CrowdStrike | - | - |
| Device Certificate | Device Certificate | - | - |
| Web Browser | Web Browser | - | - |
| Antivirus | Antivirus | - | - |
| Non-Numeric Registry (32 Bit) | - | - | - |
| Non-Numeric Registry (64 Bit) | - | - | - |
| Numeric Registry (32 Bit) | - | - | - |
| Numeric Registry (64 Bit) | - | - | - |
| Windows Update Installation Type | - | - | - |
| Windows Update Last Update Check | - | - | - |
| External Device Connected | - | - | - |
| Network Settings | - | - | - |
| - | - | - | Mount Point |
Note:
- Starting from EPA library version 24.9.1.1, the Windows Update Last Update scan also includes updates installed through BigFix, Microsoft Intune, and other third-party tools, in addition to those installed through the Windows Auto Upgrade service.
- The Windows Update Last Update scan is not applicable for manually installed updates where the update patch is downloaded and installed by the user.
- For iOS support on Device Posture service, the EPA client is built in as part of the Citrix Workspace app for iOS. For details on the versions, see Citrix Workspace app for iOS.
Third-party integration with the Device Posture service
In addition to the native scans offered by the Device Posture service, the service can also be integrated with the following third-party solutions on Windows and macOS.
- Microsoft Intune. For details, see Microsoft Intune integration with Device Posture.
- CrowdStrike. For details, see CrowdStrike integration with Device Posture.
Known limitations
- The time taken for the device posture functionality to be enabled or disabled after the device posture toggle button is turned On or Off can take a few minutes to an hour.
- Any changes in the device posture configuration do not take effect immediately. It might take around 10 minutes for the changes to take effect.
- If you have enabled the Service Continuity option in Citrix Workspace and if the Device Posture service is down, users might be unable to sign in to Workspace. This is because Citrix Workspace enumerates apps and desktops based on local cache on the user device.
- If you have configured a long-lived token and password on Citrix Workspace, the device posture scan does not work for this configuration. The devices are scanned only when the users log in to Citrix Workspace.
- Each platform can have a maximum of 10 policies and each policy can have a maximum of 10 rules.
- Role-based access is not supported with the Device Posture service.
- The Device Posture service is not supported in Citrix Cloud™ Japan.
Quality of service
- Performance: Under ideal conditions, the Device Posture service adds an additional 2 seconds of delay during login. This delay might increase depending on additional configurations such as third-party integrations like Microsoft Intune.
- Resiliency: Device Posture service is highly resilient with multiple POPs to ensure that there’s no downtime.
Integration with Chrome Enterprise Premium
By integrating the Device Posture service with Google Chrome Enterprise Premium, you can extend device compliance checks to Chrome browser-based access scenarios. This integration enables organizations to enforce device posture policies when users access applications through Chrome Enterprise Premium managed browsers.
To enable integration between the Device Posture service and Chrome Enterprise Premium, you must configure OpenID Connect (OIDC) authentication as the primary authentication method.
For more details, see the following topics: