Device Posture
Citrix Device Posture service is a cloud-based solution that helps admins to enforce certain requirements that the end devices must meet to gain access to Citrix DaaS (virtual apps and desktops) or Citrix Secure Private Access resources (SaaS, Web apps, TCP, and UDP apps). Establishing device trust by checking the device’s posture is critical to implement zero-trust-based access. Device Posture service enforces zero trust principles in your network by checking the end devices for compliance (managed/BYOD and security posture) before allowing an end user to log in.
Prerequisites
-
Licensing requirements: The entitlement for Citrix Device Posture service is part of Citrix DaaS Premium, Citrix DaaS Premium Plus, and Citrix Secure Private Access Advanced licenses. Customers with other licenses can purchase a Device Posture Service entitlement as an add-on. For an add-on, customers must purchase a standalone Adaptive Authentication SKU, but don’t necessarily have to deploy it to use the Device Posture service.
-
Supported platforms:
- Windows (10 and 11)
- macOS 13 Ventura
- macOS 12 Monterey
- iOS
- IGEL
Note:
-
A device running on a non-supported platform is marked as non-compliant by default. You can change the classification from Non-compliant to Denied login from the Settings tab on the Device Posture page.
-
A device that is running on a supported platform but does not match any pre-defined device posture policy is marked as non-compliant, by default. You can change the classification from Non-compliant to Denied login from the Settings tab on the Device Posture page.
-
For iOS support on Device Posture service, the EPA client is built in as part of the Citrix Workspace app for iOS. For details on the versions, see Citrix Workspace app for iOS.
-
For IGEL OS support on the Device Posture service, the EPA client is built in as part of the IGEL OS. Contact the IGEL support team for installing the EPA client on the IGEL devices.
-
Citrix Device Posture client (EPA client): A lightweight application that must be installed on the endpoint device to run device posture scans. This application does not require local admin rights to download and install on an endpoint.
Note:
If you’re using a device certificate check, then you must install the EPA client with administrative rights.
-
Supported browsers: Chrome, Edge, and Firefox.
-
Firewall configuration: To allow the Device Posture service to update the EPA clients on an end device, the firewall/proxy must be configured to allow the following domains:
https://swa-ui-cdn-endpoint-prod.azureedge.nethttps://productioniconstorage.blob.core.windows.net- *.netscalergateway.net
- *.nssvc.net
- *.cloud.com
- *.pendo.io
- *.citrixworkspacesapi.net
Preview features
Device Posture service with IGEL. Sign up for the preview using https://podio.com/webforms/29062020/2362942.
How it works
The admins can create device posture policies to check the posture of endpoint devices and determine whether an endpoint device is allowed or denied login. The devices which are allowed to log in are further classified as compliant or non-compliant. Users can log in from a browser or the Citrix Workspace app.
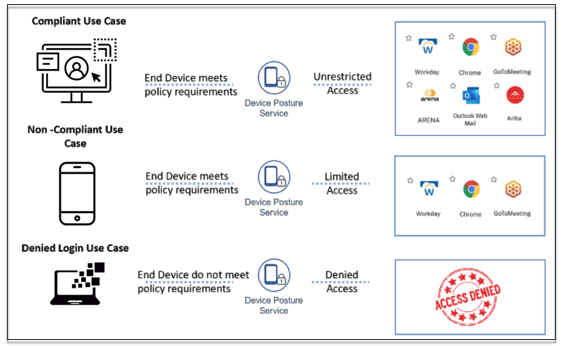
Following are the high-level conditions used to classify a device as compliant, non-compliant, and denied login.
- Compliant devices – A device that meets the pre-configured policy requirements and is allowed to log in into the company’s network with full or unrestricted access to Citrix Secure Private Access resources or Citrix DaaS resources.
- Non-Compliant devices - A device that meets the pre-configured policy requirements and is allowed to log in into the company’s network with partial or restricted access to Citrix Secure Private Access resources or Citrix DaaS resources.
- Denied login: - A device that fails to meet the policy requirements is denied login.
The classification of devices as compliant, non-compliant, and denied login is passed onto the Citrix DaaS and Citrix Secure Private Access service that in turn uses the device classification to provide smart access capabilities.
Note:
- The device posture policies must be configured specifically for each platform. For example, for macOS, an admin can allow access for the devices that have a specific OS version. Similarly, for Windows, the admin can configure policies to include a specific authorization file, registry settings, and so on.
- Device posture scans are done only during pre-authentication/before logging in.
- For definitions of “compliant” and “non-compliant,” see Definitions.
Scans supported by device posture
The following scans are supported by the Citrix Device Posture service:
| Windows | macOS | iOS | IGEL |
|---|---|---|---|
| Citrix Workspace app version | Citrix Workspace app version | Citrix Workspace app version | - |
| Operating System version | Operating System version | Operating System version | - |
| File (exists, file name, and path) | File (exists, file name, and path) | - | File (exists, file name, and path) |
| Geolocation | Geolocation | - | - |
| Network location | Network location | - | - |
| MAC Address | MAC Address | - | - |
| Process (exists) | Process (exists) | - | - |
| Microsoft Endpoint Manager | Microsoft Endpoint Manager | - | - |
| CrowdStrike | CrowdStrike | - | - |
| Device Certificate | Device Certificate | - | - |
| Browser | Browser | - | - |
| Antivirus | Antivirus | - | - |
| Non-Numeric Registry (32 Bit) | - | - | - |
| Non-Numeric Registry (64 Bit) | - | - | - |
| Numeric Registry (32 Bit) | - | - | - |
| Numeric Registry (64 Bit) | - | - | - |
| Windows Update Installation Type | - | - | - |
| Windows Update Installation Last Update check | - | - | - |
Note:
- The browser and antivirus checks are in preview.
- For iOS support on Device Posture service, the EPA client is built in as part of the Citrix Workspace app for iOS. For details on the versions, see Citrix Workspace app for iOS.
Third-party integration with device posture
In addition to the native scans offered by the Device Posture service, the service can also be integrated with the following third-party solutions on Windows and macOS.
- Microsoft Intune. For details, see Microsoft Intune integration with Device Posture.
- CrowdStrike. For details, see CrowdStrike integration with Device Posture.
Configure device posture
The device posture is a combination of policies and rules that a device must meet to gain access to the resources. Each policy is attached with one of the actions namely compliant, non-compliant, and denied login. In addition, each policy is associated with a priority and the policy evaluation stops if a policy evaluates to true and the associated action is taken.
- Sign in to Citrix Cloud, and then select Identity and Access Management from the hamburger menu.
-
Click the Device Posture, tab and then click Manage.
Note:
- Secure Private Access service customers can directly click Device Posture on the left navigation in the admin user interface.
- For the first-time users, the Device Posture landing page prompts you to create a device posture policy. Device posture policy must individually be configured for each platform. Once you create a device posture policy, it gets listed under the appropriate platforms.
- A policy comes into effect only after device posture is enabled. To enable device posture, slide the Device posture is disabled toggle on the right hand top corner to ON.
- Click Create device policy.
-
In Platform, select the platform for which you want to apply a policy. You can change the platform from Windows to macOS or conversely irrespective of the tab that you selected on the Device Posture home page.
-
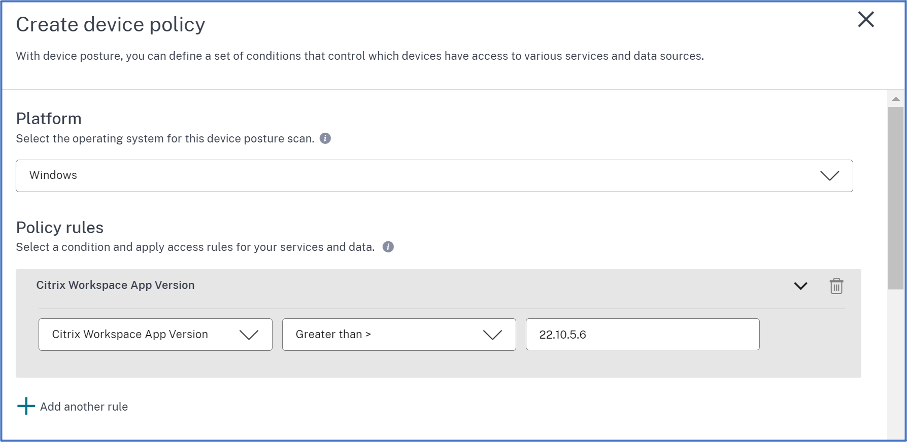
In Policy rules, select the check that you want to perform as part of device posture and select the conditions that must be matched.
Note:
- For device certificate check, ensure that the issuer certificate exists on the device. Else, you can import a device certificate while creating the device posture policy or upload the certificate from Settings on the Device Posture home page. For details, see Import device certificate while creating the policy for device certificate and Upload device certificate.
- For the device certificate check, the EPA client on the end device must be installed with administrative rights.
- The device certificate check with the Device Posture service does not support the Certificate Revocation check.
-
Click Add another rule to create multiple rules. An AND condition is applied on multiple rules.
-
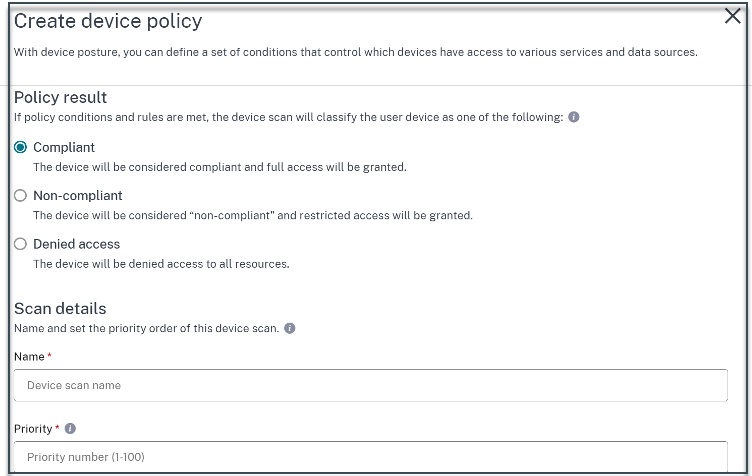
In Policy result based on the conditions that you’ve configured, select the type under which the device scan must classify the user device.
- Compliant
- Non-compliant
- Denied access
- Enter a name for the policy.
-
In Priority, enter the order in which the policies must be evaluated.
- You can enter a value between 1 through 100. It’s recommended that you configure deny policies with higher priority, followed by non-compliant, and finally compliant.
- The priority with the lower value has the highest preference.
- Only the policies that are enabled are evaluated based on the priority.
-
Click Create.
Important:
You must turn the Enable when created toggle switch to ON for the device posture policies to take effect. Before you enable the policies, it’s recommended that you ensure that the policies are correctly configured and you’re performing these tasks in your test setup.
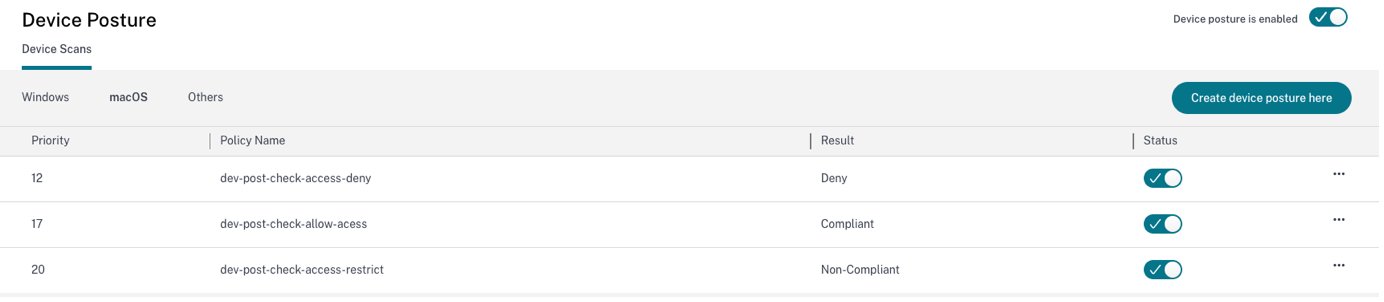
Edit a device posture policy
The configured device posture policies are listed under the specific platform in the Device Scans page. You can search for the policy you want to edit from this page. You can also enable, disable, or delete a policy from this page.
Configure contextual access (smart access) using device posture
After the device posture verification, the device is allowed to log in and classified as compliant or non-compliant. This information is available as tags to the Citrix DaaS service and Citrix Secure Private Access service and is used to provide contextual access based on device posture. Therefore, Citrix DaaS and Citrix Secure Private Access must be configured to enforce access control using device posture tags.
Citrix DaaS configuration with Device Posture
Sign up for the preview.
- Sign into Citrix Cloud.
- On the DaaS tile, click Manage.
- Go to the Delivery Group section from the left-hand menu.
- Select the delivery group for which you want to configure access control based on device posture and click Edit.
- In the Edit Delivery Group page, click Access Policy.
-
Click the edit icon on the Citrix Gateway connections row to edit the gateway connections policy.
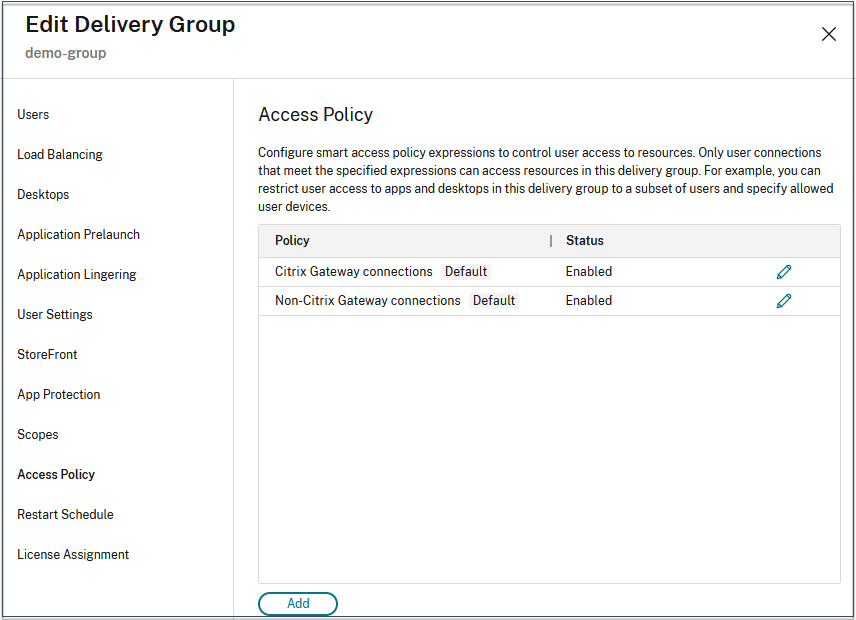
- On the Edit policy page, select Connections meeting the following criteria.
- Select Match any, and then click Add criterion.
- Add criteria for all location tags you configured in Configure network locations: Type Workspace for Filter and COMPLIANT or NON-COMPLIANT for Value.
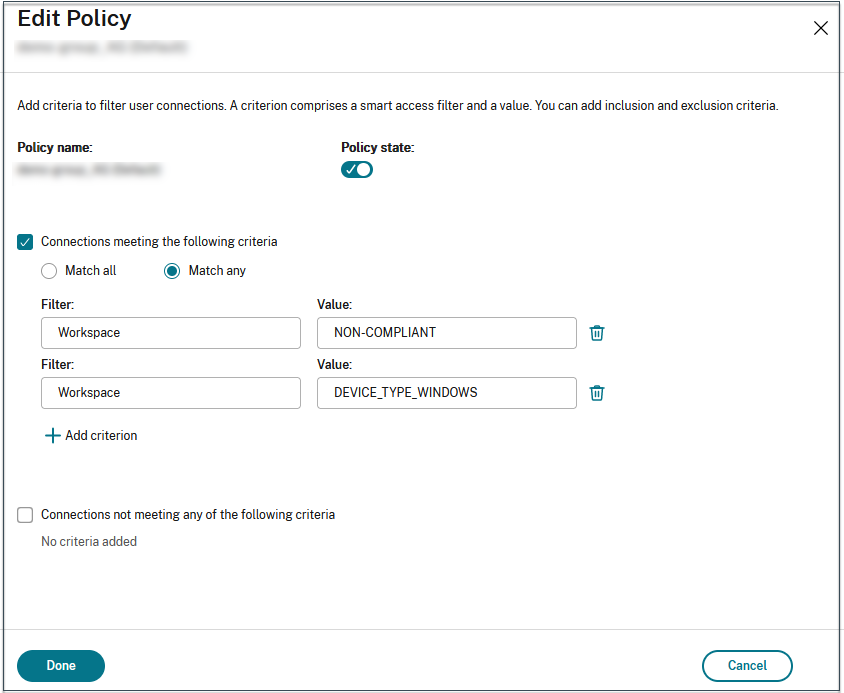
Note:
The syntax for the device classification tags must be entered in the same manner as captured earlier, that is all in uppercase (COMPLIANT and NON-COMPLIANT). Else the device posture policies do not work as intended.
In addition to the device classification tags, the Device Posture service also returns the operating system tag and the access policy tag associated with the device. The operating system tags and the access policy tags must be entered in uppercase only.
- DEVICE_TYPE_WINDOWS
- DEVICE_TYPE_MAC
- Exact policy name (uppercase)
Citrix Secure Private Access configuration with Device Posture
- Sign into Citrix Cloud.
- On the Secure Private Access tile, click Manage.
- Click Access Policies on the left navigation and then click Create policy.
- Enter the policy name and description of the policy.
- In Applications, select the app or set of apps on which this policy must be enforced.
- Click Create Rule to create rules for the policy.
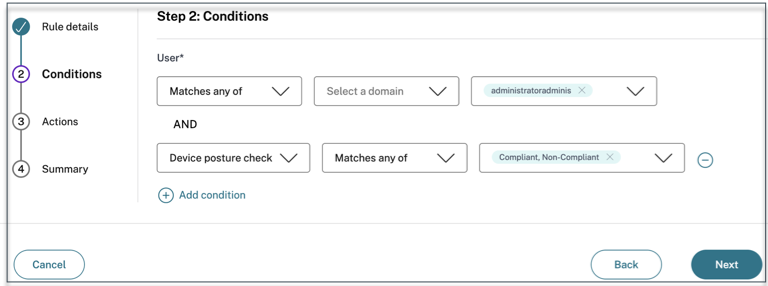
- Enter the rule name and a brief description of the rule, and then click Next.
- Select the users’ conditions. The Users condition is a mandatory condition to be met to grant access to the applications for the users.
- Click + to add device posture condition.
- Select Device posture check and the logical expression from the drop-down menu.
-
Enter one of the following values in the custom tags:
- Compliant - For compliant devices
- Non-Compliant - For non-compliant devices
- Click Next.
-
Select the actions that must be applied based on the condition evaluation, and then click Next.
The Summary page displays the policy details.
-
You can verify the details and click Finish.
For more details on creating access policies, see Configure an access policy with multiple rules.
Note:
Any Secure Private Access application which isn’t tagged as compliant or non-compliant in the access policy is treated as the default application and is accessible on all the endpoints regardless of device posture.
End-user flow
Once the device posture policies are set and device posture is enabled, the following are the end-user flows based on how the end user is logging into Citrix Workspace.
End-user flow via browser access
Note:
The macOS client and Chrome browser are used as an example for illustration purposes. The screens and the notifications vary depending on the client and the browser that you use for accessing the Citrix Workspace URL.
-
When an end-user logs on to the Citrix Workspace URL
https://<your-workspace-URLthrough a browser, the end user is prompted to run the Citrix EndPointAnalysis application.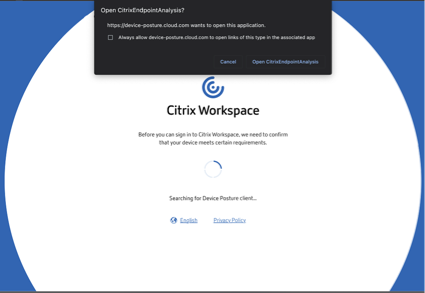
-
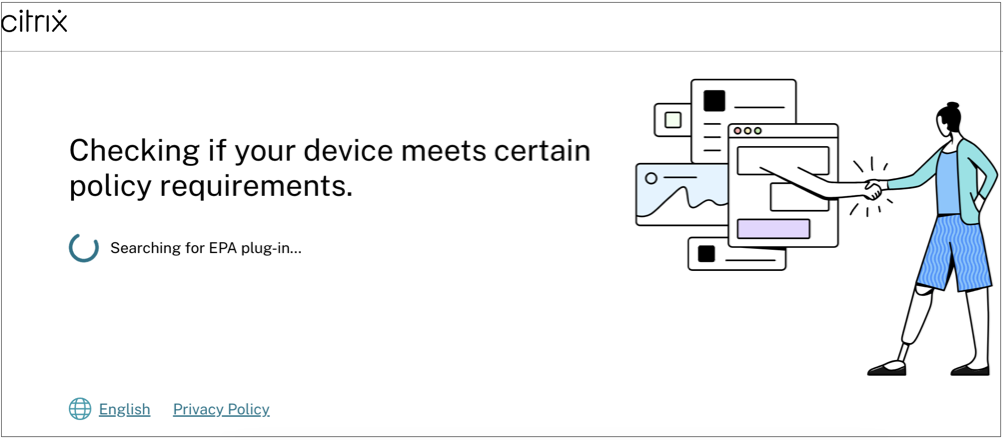
When the end user clicks Open Citrix End Point Analysis, the device posture client runs and scans the endpoint parameters based on device posture policy requirements.
-
If the latest device posture client isn’t installed on the endpoint, the users are redirected to the page that displays the options Check again and Download Client. The user must click Download Client.
-
If the latest device posture client is already installed on the endpoint, the user must click Check again.
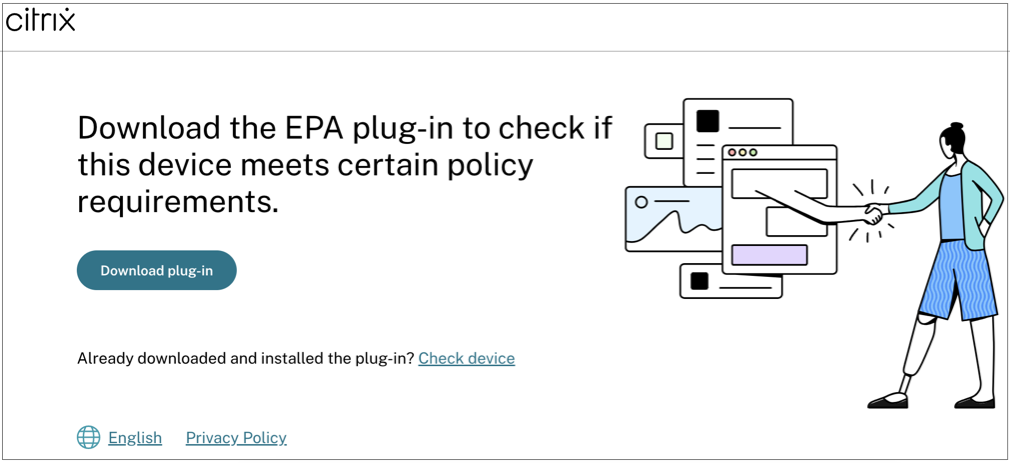
End-user flow via Citrix Workspace application
- When an end-user logs on to the Citrix Workspace URL
https://your-workspace-urlthrough the Citrix Workspace application, the device posture client installed on the endpoint runs and scans the endpoint parameters based on device posture policy requirements. - If the latest device posture client isn’t installed on the endpoint, the users are redirected to the page that displays the options, Check again and Download Client. The user must click Download Client.
- If the latest device posture client is already installed on the endpoint, the user must click Check again.
End-user flow - Device posture results
Based on the device posture policy conditions, three possibilities can occur.
If an endpoint meets the policy conditions such that the device is categorized as;
- Compliant - The end user is allowed to log in with unrestricted access to Secure Private Access or Citrix DaaS resources.
-
Non-compliant - The end user is allowed to log in with restricted access to Secure Private Access or Citrix DaaS resources.
If an endpoint meets the policy conditions such that the device is categorized as Denied access, the Access denied message appears.
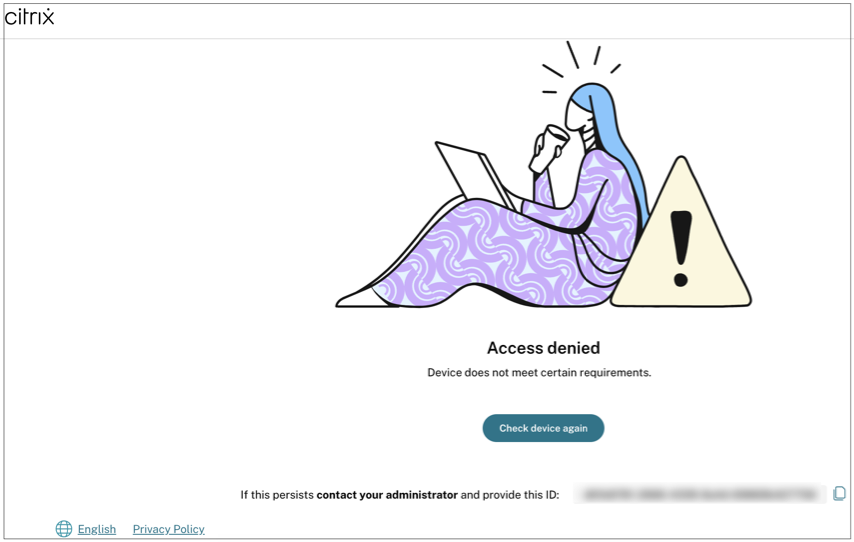
Customized messages for access denied scenarios (Preview)
Admins have the option to customize the message that is displayed on the end device when an access is denied.
This feature is under preview. Sign up for the preview using https://podio.com/webforms/29219975/2385710.
Perform the following steps to add customized messages:
- Navigate to the Device Posture > Device Scans page.
- Click Settings.
- Click Edit and in the Message box, enter the message that must be displayed in access denied scenarios. You can enter a maximum of 256 characters.
-
Click Enable custom message on save to enforce the option of displaying the custom message. If you do not select this checkbox, the custom message is created but not displayed on the devices in access denied scenarios.
Alternatively, you can enable the Custom message toggle switch on the Settings page to display the message on the devices.
- Click Save.
The message that you have entered appears whenever access is denied for the end device.
Monitor and troubleshoot Device Posture events
Device posture event logs can be viewed at two places:
- Citrix DaaS Monitor
- Citrix Secure Private Access dashboard
Device posture events on Citrix DaaS Monitor
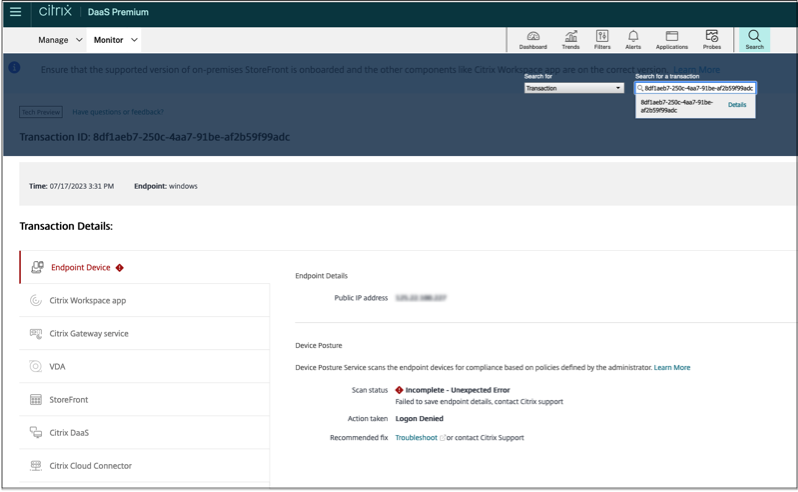
Perform the following steps to view the events logs for the Device Posture service.
- Copy the transaction ID of the failed or access denied session from the end user device.
- Sign into Citrix Cloud.
- On the DaaS tile, click Manage, and then click the Monitor tab.
- In the Monitor UI, search for the 32-digit transaction ID and click Details.
Device posture events on Secure Private Access dashboard
Perform the following steps to view the events logs for the Device Posture service.
- Sign into Citrix Cloud.
- On the Secure Private Access tile, click Manage.
- Go to the Dashboard section from the left-hand menu.
-
Click the See more link in the Diagnostic Logs chart to view the device posture event logs.
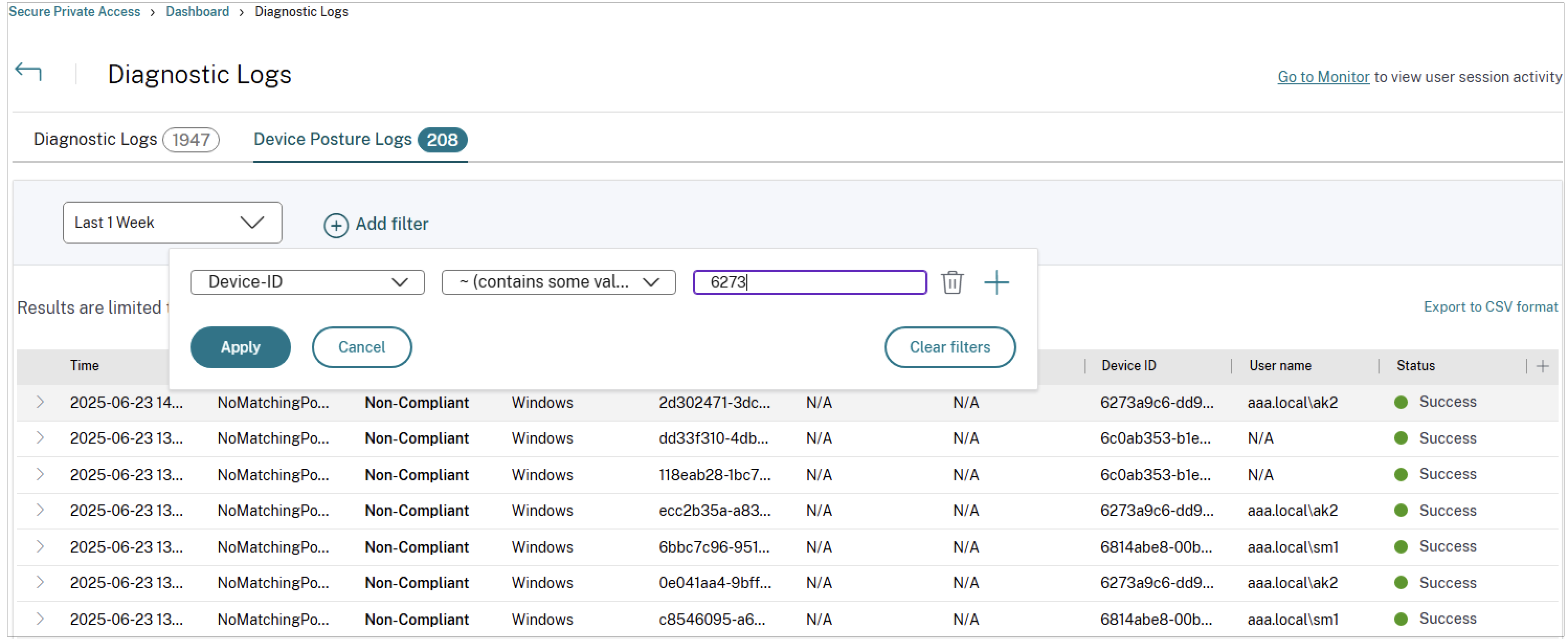
-
Admins can filter the logs based on the transaction ID in the Diagnostic logs chart. The transaction ID is also displayed to the end user whenever access is denied.
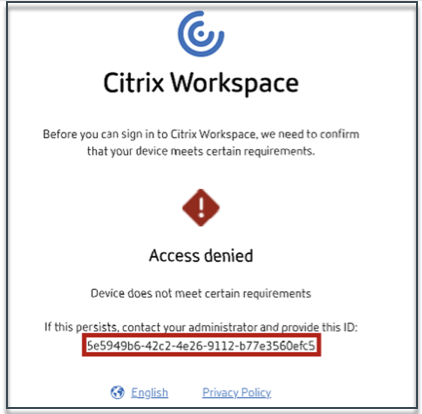
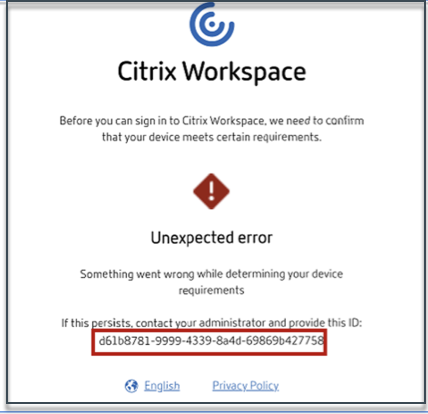
-
If there’s an error or a scan failure, the Device Posture service displays a transaction ID. This transaction ID is available in the Secure Private Access service dashboard. If the logs do not help resolve the issue, end users can share the transaction ID with Citrix Support for resolving the issue.
-
The Windows client logs can be found at:
- %localappdata%\Citrix\EPA\dpaCitrix.txt
- %localappdata%\Citrix\EPA\epalib.txt
-
The macOS client logs can be found at:
- ~/Library/Application Support/Citrix/EPAPlugin/EpaCloud.log
- ~/Library/Application Support/Citrix/EPAPlugin/epaplugin.log
Device posture error logs
The following logs related to the Device Posture service can be viewed on the Citrix Monitor and Secure Private Access dashboard. For all these logs, it’s recommended that you contact Citrix Support for resolution.
- Failed to read configured policies
- Failed to evaluate endpoint scans
- Failed to process policies/expression
- Failed to save endpoint details
- Failed to process scan results from endpoints
Known limitations
- The time taken for the device posture functionality to be enabled or disabled after the device posture toggle button is turned On or Off can take a few minutes to an hour.
- Any changes in the device posture configuration do not take effect immediately. It might take around 10 minutes for the changes to take effect.
- If you have enabled the Service Continuity option in Citrix Workspace and if the Device Posture service is down, users might be unable to sign in to Workspace. This is because Citrix Workspace enumerates apps and desktops based on local cache on the user device.
- If you have configured a long-lived token and password on Citrix Workspace, the device posture scan does not work for this configuration. The devices are scanned only when the users log in to Citrix Workspace.
- Each platform can have a maximum of 10 policies and each policy can have a maximum of 10 rules.
- Role-based access is not supported with the Device Posture service.
Quality of service
- Performance: Under ideal conditions, the Device Posture service adds an additional 2 seconds of delay during login. This delay might increase depending on additional configurations such as third-party integrations like Microsoft Intune.
- Resiliency: Device Posture service is highly resilient with multiple POPs to ensure that there’s no downtime.
Definitions
The terms “compliant” and “non-compliant” in reference to the Device Posture service are defined as follows.
- Compliant devices – A device that meets the pre-configured policy requirements and is allowed to log in into the company’s network with full or unrestricted access to Citrix Secure Private Access resources or Citrix DaaS resources.
- Non-Compliant devices - A device that meets the pre-configured policy requirements and is allowed to log in into the company’s network with partial or restricted access to Citrix Secure Private Access resources or Citrix DaaS resources.
In this article
- Prerequisites
- Preview features
- How it works
- Scans supported by device posture
- Third-party integration with device posture
- Configure device posture
- Configure contextual access (smart access) using device posture
- End-user flow
- Monitor and troubleshoot Device Posture events
- Known limitations
- Quality of service
- Definitions