Configure allow list for the apps which use LD_PRELOAD functionalities
Note:
Configuring allow list using LD_PRELOAD functionality is only available for Citrix Workspace™ app for Linux.
App protection blocks the launch of a protected session if other apps running use LD_PRELOAD. If there are genuine apps or if approved by the admin, you can use the allow list feature. To permit the use of other apps which use LD_PRELOAD, you must configure the allow list.
App protection stops a protected session from starting if other apps using LD_PRELOAD are running. But if there are legitimate apps or if the admin approves, you can use the allow list feature. To allow these apps to run, you need to set up the allow list.
You can add apps with preload functionalities to the allow list using the following steps:
- Identify the process that is blocking the protected VDA/App session from starting.
- Create a configuration file for the allow list and add the identified process.
Identify the process preventing protected VDA launch
When AppProtection prevents the launch of a protected VDA due to LD_PRELOAD usage, verify processes using LD_PRELOAD. Genuine processes can be added to the allow list.
To identify processes using LD_PRELOAD, use the following script. Save it with a .sh extension and run it as sudo in a terminal window:
#!/bin/bash
for pid in /proc/*/; do
pid=${pid%*/}
pid=${pid##*/}
environ_file="/proc/$pid/environ"
if [[ ! -f "$environ_file" ]]; then
continue
fi
ld_preload_entry=$(tr '\0' '\n' < "$environ_file" | grep -w "LD_PRELOAD")
if [[ -n "$ld_preload_entry" ]]; then
cmdline_file="/proc/$pid/cmdline"
cmdline=$(tr '\0' ' ' < "$cmdline_file" | awk '{print $1}')
echo "\"$ld_preload_entry\" : \"$cmdline\""
fi
done
<!--NeedCopy-->
Based on the output of the preceding script, identify the processes that are causing the protected VDA launch to fail and add those processes to the allow list.
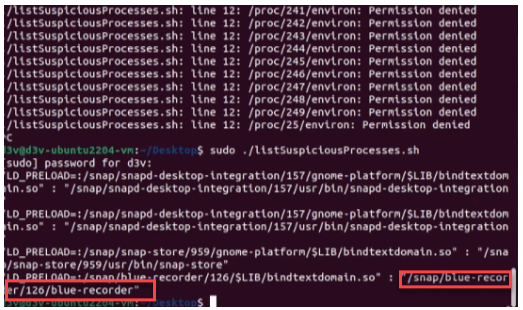
Here is a sample image displaying the output with a list of apps with a preload list.
Creating the allow list configuration file
The process allow list configuration file isn’t installed by default for security reasons. You need to create this configuration file the first time it’s needed.
- Create an empty file named AppProtection_Preload_Allowlist.json in the “$ICAROOT/config/” folder.
-
Add the process details in the following format:
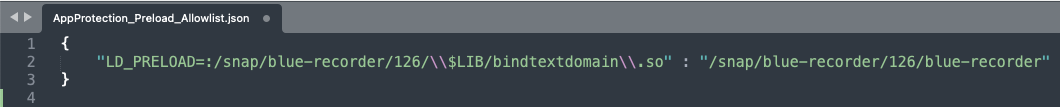
{ "LD_PRELOAD_PATH1" : "PROCESS_PATH1", "LD_PRELOAD_PATH2" : "PROCESS_PATH2" } <!--NeedCopy-->Here is a sample image displaying the newly added configuration:
- Save the file and then set the permissions to the AppProtection_Preload_Allowlist.json file using the following command.
sudo chmod 644 $ICAROOT/config/AppProtection_Preload_Allowlist.json
Note:
Minimal regex expressions are allowed in configuration entries to prevent redundancy. Special regex characters must be checked and escaped with a double backslash (\).
- For example, consider that the script output is as follows:
LD_PRELOAD=:/snap/blue-recorder/126/$LIB/bindtextdomain.so" : "/snap/blue-recorder/126/blue-recorder
- You can see that the output includes ‘.’, ‘$’ which are special characters in regex patterns. So, you must escape them using a backslash as follows:
LD_PRELOAD=:/snap/blue-recorder/126/\\$LIB/bindtextdomain\\.so" : "/snap/blue-recorder/126/blue-recorder
- To use variable elements like the number 126, regex expressions can be used for a more generic allow list entry:
LD_PRELOAD=:/snap/blue-recorder/\\d+/\\$LIB/bindtextdomain\\.so" : "/snap/blue-recorder/\\d+/blue-recorder