Device Posture service and deviceTRUST - Better together
Securing access to enterprise applications and data now requires more than static policies. They require real-time, context-aware controls that continuously adapt throughout the user journey. The Citrix Device Posture service and deviceTRUST integration delivers comprehensive contextual access coverage across every phase; pre-authentication, enumeration, and in-session.
To configure Device Posture service and deviceTRUST for your specific environment, see the following topics:
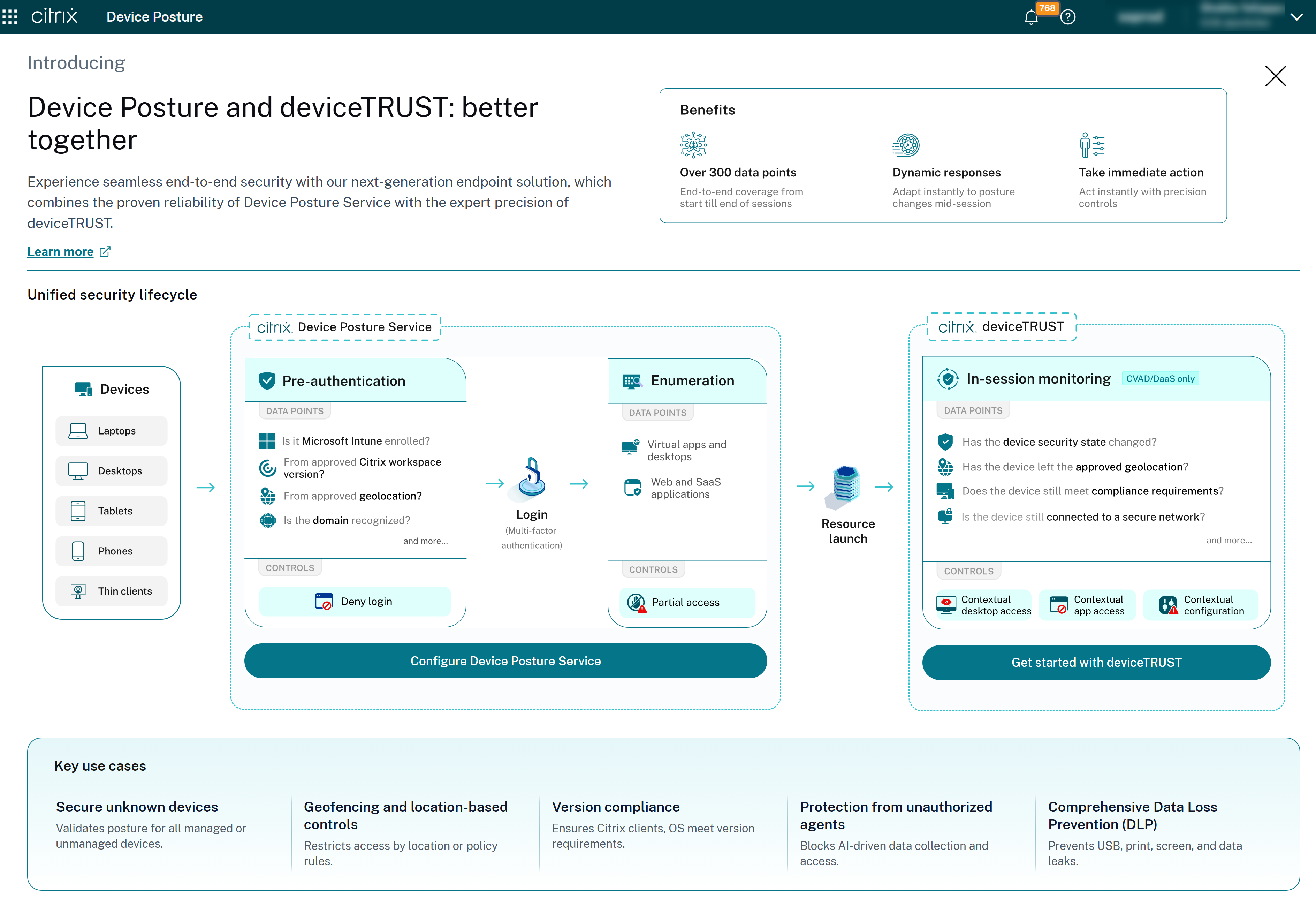
How Device Posture service and deviceTRUST work together
Pre-authentication: Establishing trust before login
The Device Posture service acts as the first line of defense, performing endpoint hygiene checks before a user is allowed to authenticate. Administrators can define policies that inspect device properties such as;
- Citrix Workspace app version
- OS version
- Security software status (Antivirus)
- Corporate enrollment via MDM solutions
- Device certificate
- Compliance with corporate standards
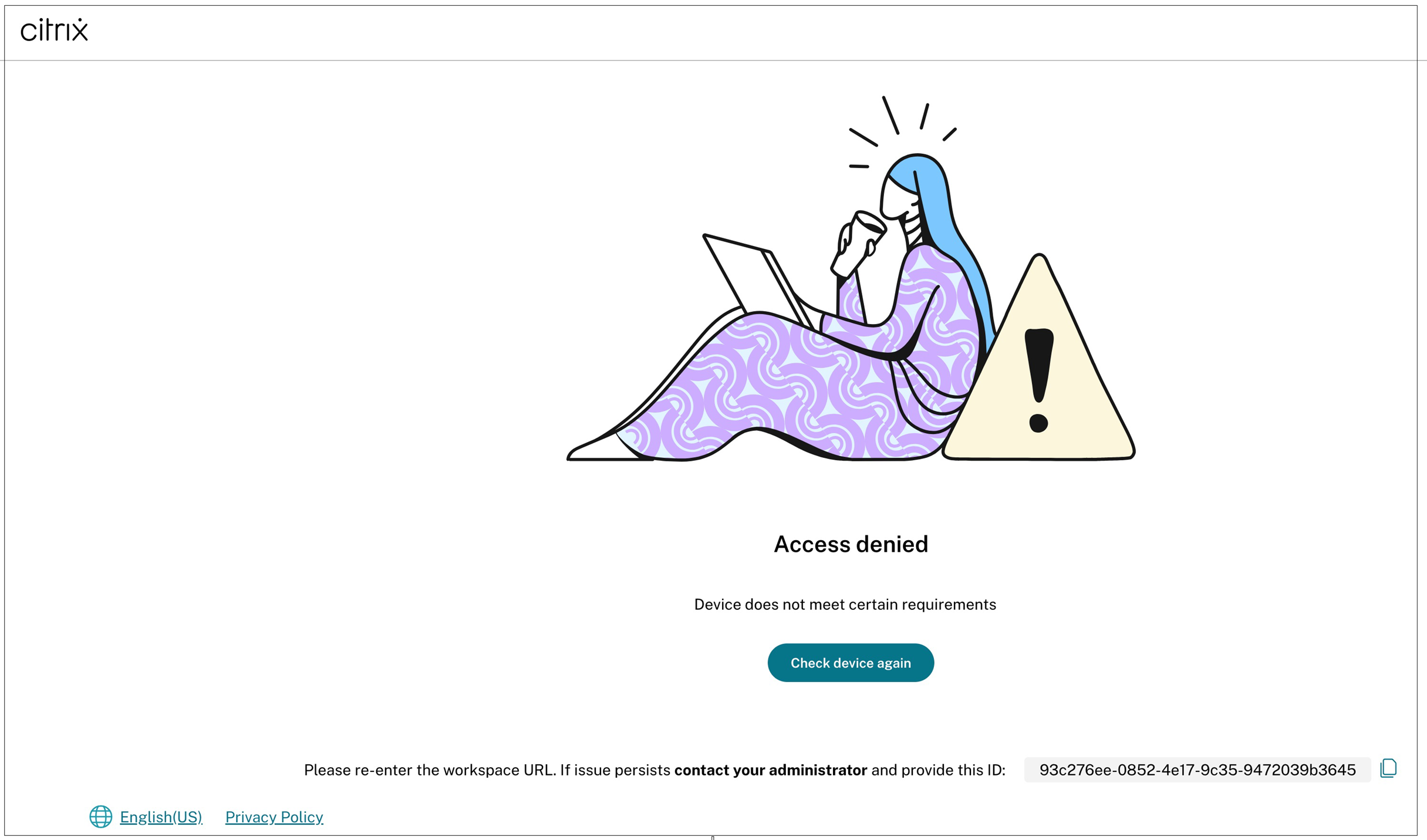
If a device fails to meet these requirements, access is blocked before authentication even begins.
Example:
When a user attempts to log in from a personal device, the Device Posture service verifies that the antivirus software is installed and running. If the device fails to meet the policy requirements created by the administrator, login is denied, ensuring only trusted devices can access sensitive resources.
Enumeration: Contextual access to applications
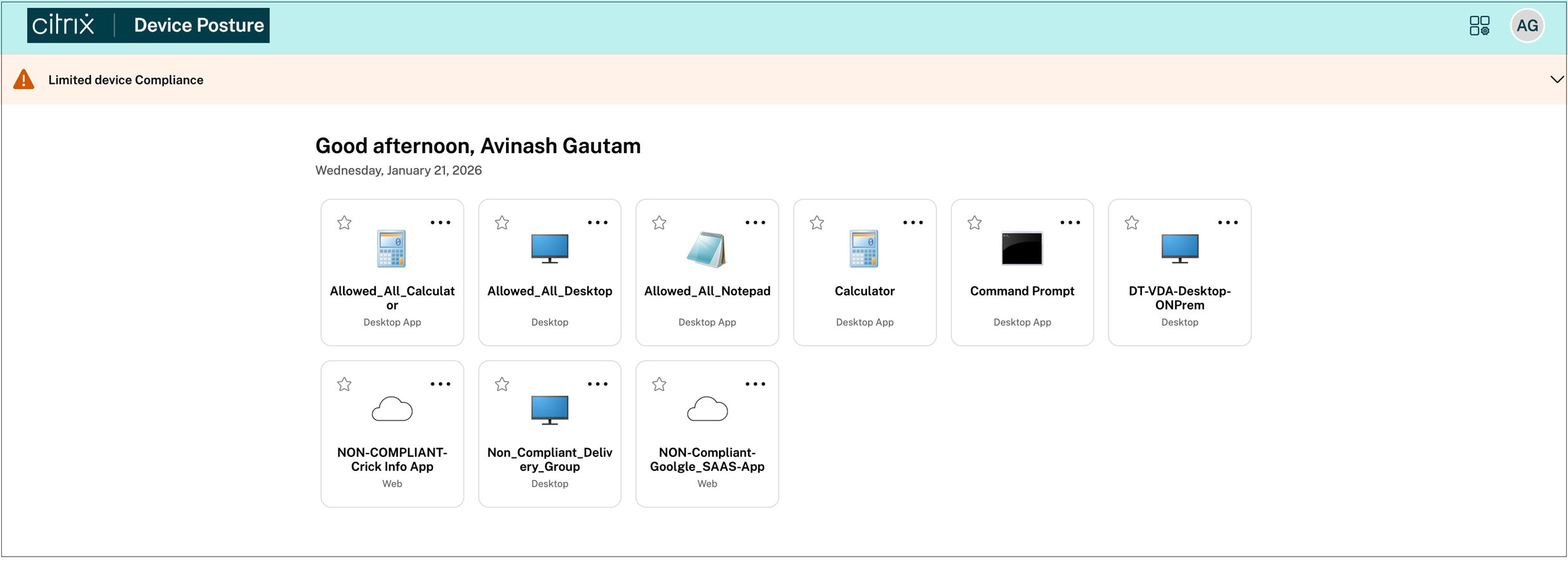
During the enumeration phase, the Device Posture service continues to enforce policies by evaluating device posture when users browse or enumerate applications in the store. Administrators can restrict which applications or desktops are visible or accessible based on context.
Example:
If a device is compliant, the user sees all entitled applications. If not, certain apps might be hidden or access might be limited, such as disabling clipboard or file transfer features.
In-Session: Continuous contextual access evaluation
Once a session is established, deviceTRUST takes over to provide continuous, in-session contextual access controls. Unlike traditional solutions that only check device posture at login, deviceTRUST monitors device context throughout the session, enabling dynamic enforcement of policies as conditions at the endpoint change.
Granular Controls: Administrators can configure actions such as session disconnects, pop-up notifications, or auditing when device context changes (for example, plugging in an unauthorized USB stick, disabling firewall, connecting to an unencrypted Wi-Fi, changing network location).
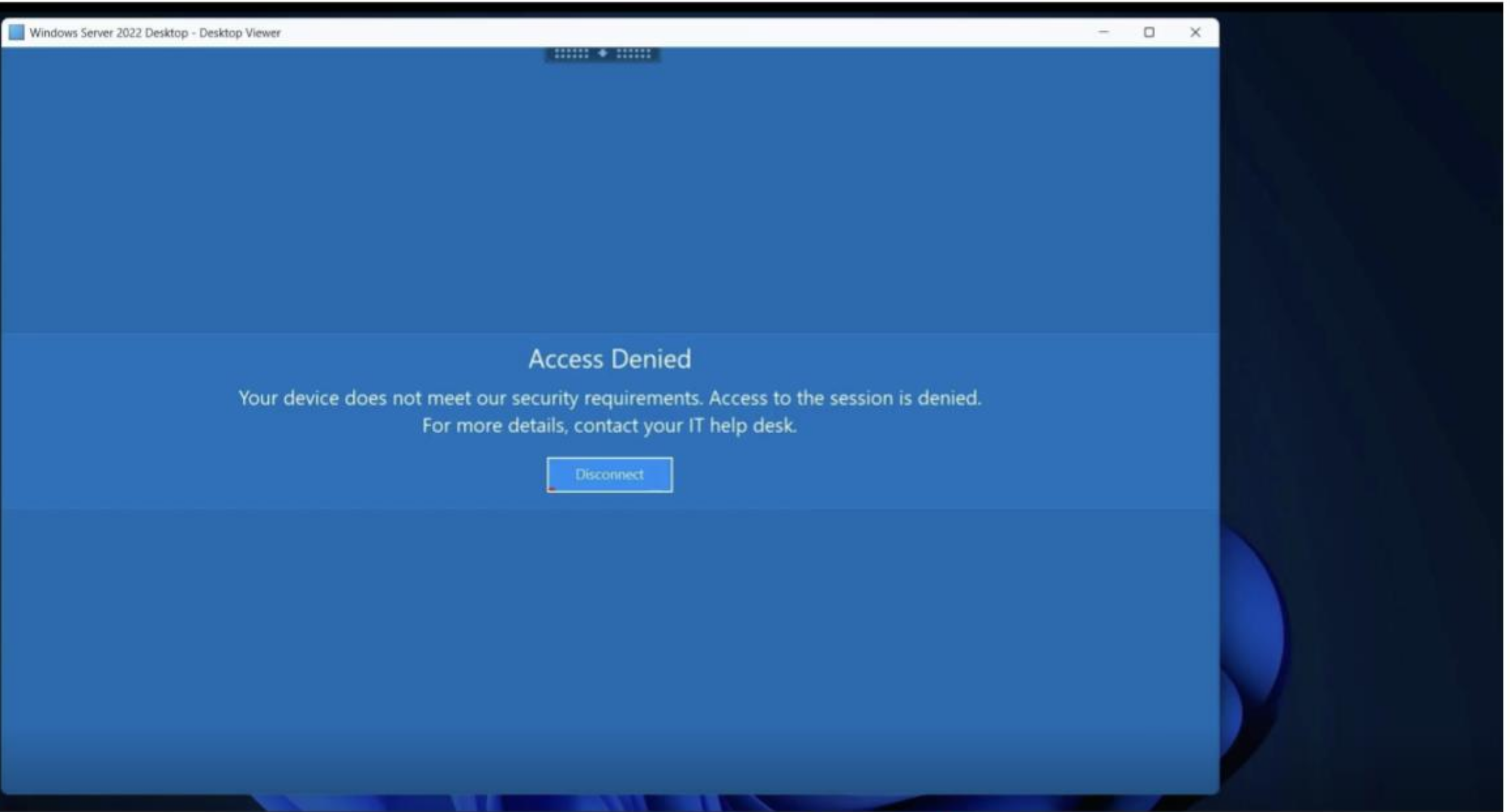
Example:
A user starts a session from a compliant device. During the session, deviceTRUST detects a change—for example, the device connects to an unsecured network or a prohibited peripheral is attached. The system can automatically restrict access, disconnect the session, or notify the user of required actions, maintaining continuous compliance.
Use case of the Device Posture service and deviceTRUST integration
The Device Posture service and deviceTRUST integration support a range of critical use cases, such as;
- Version compliance (restricting access to approved operating system and application versions)
- Geofencing (controlling access based on device location)
-
Continuous monitoring of security states such;
- Antivirus status
- Protection against unauthorized software agents - Comprehensive data loss prevention (DLP) through dynamic restriction of clipboard, file transfer, and printing
- Securing unknown or unmanaged devices in BYOD scenarios.
These capabilities empower administrators to maintain continuous compliance, reduce risk, and protect enterprise data in dynamic, hybrid environments.
Version compliance
Ensure that only devices running approved versions of operating systems and Citrix Workspace app (CWA) can access resources. This prevents outdated or vulnerable endpoints from connecting, reducing risk from unpatched systems.
For detailed policy configuration steps, see this tutorial.
Geofencing
Restrict access to applications and desktops based on the physical location of the device. For example, allow access only from approved countries or corporate offices, and revoke access if a device crosses a border.
For detailed policy configuration steps, see this tutorial.
Monitoring security state of device
Antivirus checks: Checking for antivirus is a foundational security measure that helps ensure only trusted, protected devices can access enterprise resources, both at the point of log in and throughout the user session. This is especially important in dynamic, hybrid, or BYOD environments where device compliance cannot be assumed.
For detailed policy configuration steps, see this tutorial.