User authentication
StoreFront supports a number of different authentication methods for users accessing stores; although, not all are available depending on the user access method and their network location. For security reasons, some authentication methods are disabled by default when you create your first store. For more information about enabling and disabling user authentication methods, see Create and configure the authentication service.
User name and password
Users enter their credentials and are authenticated when they access their stores. Explicit authentication is enabled by default. All user access methods support explicit authentication.
When a user employs NetScaler Gateway to access Citrix Receiver for Web, NetScaler Gateway handles the logon and password change at expiration. Users can make elective password changes with the Citrix Receiver for Web UI. After an elective password change, the NetScaler Gateway session terminates and the user must log on again. Citrix Receiver for Linux users can change only expired passwords.
SAML authentication
Users authenticate to a SAML Identity Provider and are automatically logged on when they access their stores. StoreFront can support SAML authentication directly within the corporate network, without the need to go through NetScaler.
SAML (Security Assertion Markup Language) is an open standard used by identity and authentication products such as Microsoft AD FS (Active Directory Federation Services). With the integration of SAML authentication through StoreFront, administrators can allow users to, for example, log on once to their corporate network and then get single sign-on to their published apps.
Requirements:
- Implementation of the Citrix Federated Authentication Service.
- SAML 2.0-compliant identity providers (IdPs):
- Microsoft AD FS v4.0 (Windows Server 2016) using SAML bindings only (not WS-Federation bindings). For more information, see AD FS Deployment and AD FS Operations.
- Microsoft AD FS v3.0 (Windows Server 2012 R2)
- Microsoft AD FS v2.0 (Windows Server 2008 R2)
- NetScaler Gateway (configured as an IdP)
- Configure SAML authentication in StoreFront using the StoreFront management console in a new deployment (see Create a new deployment), or in an existing deployment (see Configure the authentication service). You can also configure SAML authentication using PowerShell cmdlets, see StoreFront SDK.
- Citrix Receiver for Windows (4.6 and higher) or Citrix Receiver for Web.
Using SAML authentication with NetScaler is currently supported with Receiver for Web sites.
Domain pass-through
Users authenticate to their domain-joined Windows computers, and their credentials are used to log them on automatically when they access their stores. When you install StoreFront, domain pass-through authentication is disabled by default. Domain pass-through authentication can be enabled for users connecting to stores through Citrix Receiver and XenApp Services URLs. Citrix Receiver for Web sites support domain pass-through authentication for Internet Explorer, Microsoft Edge, Mozilla Firefox, and Google Chrome. Enable domain pass-through authentication in the Citrix Receiver for Web site node in the administration console and requires you to configure SSON on Citrix Receiver for Windows. Citrix Receiver for HTML5 does not support domain pass-through authentication. To use domain pass-through authentication, users require Citrix Receiver for Windows or the Online Plug-in for Windows. Pass-through authentication must be enabled when Citrix Receiver for Windows or the Online Plug-in for Windows are installed on users’ devices.
Pass-through from NetScaler Gateway
Users authenticate to NetScaler Gateway and are automatically logged on when they access their stores. Pass-through from NetScaler Gateway authentication is enabled by default when you first configure remote access to a store. Users can connect through NetScaler Gateway to stores using Citrix Receiver or Citrix Receiver for Web sites. Desktop Appliance sites do not support connections through NetScaler Gateway. For more information about configuring StoreFront for NetScaler Gateway, see Add a NetScaler Gateway connection.
StoreFront supports pass-through with the following NetScaler Gateway authentication methods.
- Security token. Users log on to NetScaler Gateway using passcodes that are derived from tokencodes generated by security tokens combined, in some cases, with personal identification numbers. If you enable pass-through authentication by security token only, ensure that the resources you make available do not require additional or alternative forms of authentication, such as users’ Microsoft Active Directory domain credentials.
- Domain and security token. Users logging on to NetScaler Gateway are required to enter both their domain credentials and security token passcodes.
- Client certificate. Users log on to NetScaler Gateway and are authenticated based on the attributes of the client certificate presented to NetScaler Gateway. Configure client certificate authentication to enable users to log on to NetScaler Gateway using smart cards. Client certificate authentication can also be used with other authentication types to provide double-source authentication.
StoreFront uses the NetScaler Gateway authentication service to provide pass-through authentication for remote users so that they only need to enter their credentials once. However, by default, pass-through authentication is only enabled for users logging on to NetScaler Gateway with a password. To configure pass-through authentication from NetScaler Gateway to StoreFront for smart card users, delegate credential validation to NetScaler Gateway. For more information, see Create and configure the authentication service.
Users can connect to stores within Citrix Receiver with pass-through authentication through a Secure Sockets Layer (SSL) virtual private network (VPN) tunnel using the NetScaler Gateway Plug-in. Remote users who cannot install the NetScaler Gateway Plug-in can use clientless access to connect to stores within Citrix Receiver with pass-through authentication. To use clientless access to connect to stores, users require a version of Citrix Receiver that supports clientless access.
Additionally, you can enable clientless access with pass-through authentication to Citrix Receiver for Web sites. To do this, configure NetScaler Gateway to act as a secure remote proxy. Users log on to NetScaler Gateway directly and use the Citrix Receiver for Web site to access their applications without needing to authenticate again.
Users connecting with clientless access to App Controller resources can only access external software-as-a-service (SaaS) applications. To access internal web applications, remote users must use the NetScaler Gateway Plug-in.
If you configure double-source authentication to NetScaler Gateway for remote users accessing stores from within Citrix Receiver, you must create two authentication policies on NetScaler Gateway. Configure RADIUS (Remote Authentication Dial-In User Service) as the primary authentication method and LDAP (Lightweight Directory Access Protocol) as the secondary method. Modify the credential index to use the secondary authentication method in the session profile so that LDAP credentials are passed to StoreFront. When you add the NetScaler Gateway appliance to your StoreFront configuration, set the Logon type to Domain and security token. For more information, see http://support.citrix.com/article/CTX125364
To enable multidomain authentication through NetScaler Gateway to StoreFront, set SSO Name Attribute to userPrincipalName in the NetScaler Gateway LDAP authentication policy for each domain. You can require users to specify a domain on the NetScaler Gateway logon page so that the appropriate LDAP policy to use can be determined. When you configure the NetScaler Gateway session profiles for connections to StoreFront, do not specify a single sign-on domain. You must configure trust relationships between each of the domains. Ensure that you allow users to log on to StoreFront from any domain by not restricting access to explicitly trusted domains only.
Where supported by your NetScaler Gateway deployment, you can use SmartAccess to control user access to XenDesktop and XenApp resources on the basis of NetScaler Gateway session policies. For more information about SmartAccess, see How SmartAccess works for XenApp and XenDesktop.
Smart cards
Users authenticate using smart cards and PINs when they access their stores. When you install StoreFront, smart card authentication is disabled by default. Smart card authentication can be enabled for users connecting to stores through Citrix Receiver, Citrix Receiver for Web, Desktop Appliance sites, and XenApp Services URLs.
Use smart card authentication to streamline the logon process for your users while also enhancing the security of user access to your infrastructure. Access to the internal corporate network is protected by certificate-based two-factor authentication using public key infrastructure. Private keys are protected by hardware controls and never leave the smart card. Your users get the convenience of accessing their desktops and applications from a range of corporate devices using their smart cards and PINs.
You can use smart cards for user authentication through StoreFront to desktops and applications provided by XenDesktop and XenApp. Smart card users logging on to StoreFront can also access applications provided by App Controller. However, users must authenticate again to access App Controller web applications that use client certificate authentication.
To enable smart card authentication, users’ accounts must be configured either within the Microsoft Active Directory domain containing the StoreFront servers or within a domain that has a direct two-way trust relationship with the StoreFront server domain. Multi-forest deployments involving two-way trusts are supported.
The configuration of smart card authentication with StoreFront depends on the user devices, the clients installed, and whether the devices are domain-joined. In this context, domain-joined means devices that are joined to a domain within the Active Directory forest containing the StoreFront servers.
Use smart cards with Citrix Receiver for Windows
Users with devices running Citrix Receiver for Windows can authenticate using smart cards, either directly or through NetScaler Gateway. Both domain-joined and non-domain-joined devices can be used, although the user experience is slightly different.
The figure shows the options for smart card authentication through Citrix Receiver for Windows.
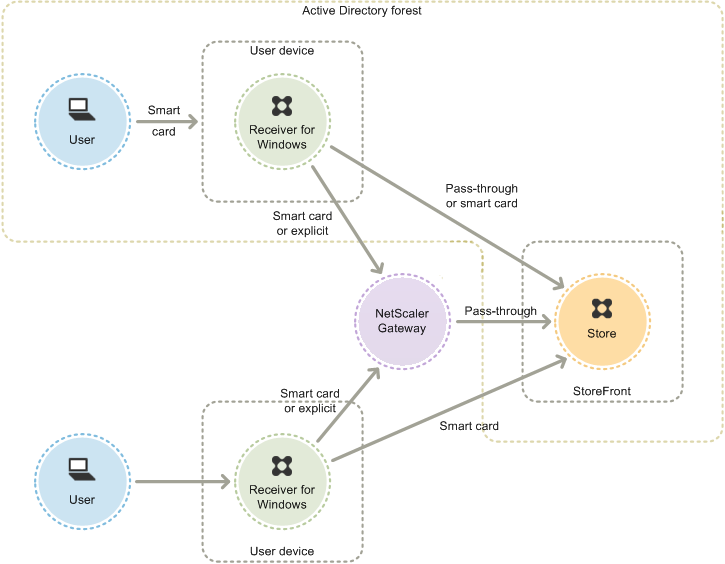
For local users with domain-joined devices, you can configure smart card authentication so that users are only prompted for their credentials once. Users log on to their devices using their smart cards and PINs and, with the appropriate configuration in place, are not prompted for their PINs again. Users are silently authenticated to StoreFront and also when they access their desktops and applications. To achieve this, you configure Citrix Receiver for Windows for pass-through authentication and enable domain pass-through authentication to StoreFront.
Users log on to their devices and then authenticate to Citrix Receiver for Windows using their PINs. There is no further PIN prompts when they try to start apps and desktops
Because users of non-domain-joined devices log on to Citrix Receiver for Windows directly, you can enable users to fall back to explicit authentication. If you configure both smart card and explicit authentication, users are initially prompted to log on using their smart cards and PINs but have the option to select explicit authentication if they experience any issues with their smart cards.
Users connecting through NetScaler Gateway must log on using their smart cards and PINs at least twice to access their desktops and applications. This applies to both domain-joined and non-domain-joined devices. Users authenticate using their smart cards and PINs, and, with the appropriate configuration in place, are only prompted to enter their PINs again when they access their desktops and applications. To achieve this, you enable pass-through with NetScaler Gateway authentication to StoreFront and delegate credential validation to NetScaler Gateway. Then, create an additional NetScaler Gateway virtual server through which you route user connections to resources. In the case of domain-joined devices, you must also configure Citrix Receiver for Windows for pass-through authentication.
Note: If you are using Citrix Receiver for Windows 4.2 - the current version, you can set up a second vServer and use the optimal gateway routing feature to remove the need for PIN prompts when starting apps and desktops.
Users can log on to NetScaler Gateway using either their smart cards and PINs, or with explicit credentials. This enables you to provide users with the option to fall back to explicit authentication for NetScaler Gateway logons. Configure pass-through authentication from NetScaler Gateway to StoreFront and delegate credential validation to NetScaler Gateway for smart card users so that users are silently authenticated to StoreFront.
Use smart cards with Desktop Appliance sites
Non-domain-joined Windows desktop appliances can be configured to enable users to log on to their desktops using smart cards. The Citrix Desktop Lock is required on the appliance and Internet Explorer must be used to access the Desktop Appliance site.
The figure shows smart card authentication from a non-domain-joined desktop appliance.

When users access their desktop appliances, Internet Explorer starts in full-screen mode displaying the logon screen for a Desktop Appliance site. Users authenticate to the site using their smart cards and PINs. If the Desktop Appliance site is configured for pass-through authentication, users are automatically authenticated when they access their desktops and applications. Users are not prompted for their PINs again. Without pass-through authentication, users must enter their PINs a second time when they start a desktop or application.
You can enable users to fall back to explicit authentication if they experience any issues with their smart cards. To do this, you configure the Desktop Appliance site for both smart card and explicit authentication. In this configuration, smart card authentication is considered to be primary access method so users are prompted for their PINs first. However, the site also provides a link that enables users to log on with explicit credentials instead.
Use smart cards with XenApp Services URLs
Users of domain-joined desktop appliances and repurposed PCs running the Citrix Desktop Lock can authenticate using smart cards. Unlike other access methods, pass-through of smart card credentials is automatically enabled when smart card authentication is configured for a XenApp Services URL.
The figure shows smart card authentication from a domain-joined device running the Citrix Desktop Lock.

Users log on to their devices using their smart cards and PINs. The Citrix Desktop Lock then silently authenticates users to StoreFront through the XenApp Services URL. Users are automatically authenticated when they access their desktops and applications, and are not prompted for their PINs again.
Use smart cards with Citrix Receiver for Web
You can enable smart card authentication to Citrix Receiver for Web from the StoreFront Administration Console.
- Select the Citrix Receiver for Web node in the left panel.
- Select the site you want to use smart card authentication.
- Select the Choose Authentication Methods task in the right panel.
- Check the Smart card checkbox in the popup dialog screen and click OK.
If you enable pass-through with smart card authentication to XenDesktop and XenApp for Citrix Receiver for Windows users with domain-joined devices who do not access stores through NetScaler Gateway, this setting applies to all users of the store. To enable both domain pass-through and pass-through with smart card authentication to desktops and applications, you must create separate stores for each authentication method. Your users must then connect to the appropriate store for their method of authentication.
If you enable pass-through with smart card authentication to XenDesktop and XenApp for Citrix Receiver for Windows users with domain-joined devices accessing stores through NetScaler Gateway, this setting applies to all users of the store. To enable pass-through authentication for some users and require others to log on to their desktops and applications, you must create separate stores for each group of users. Then, direct your users to the appropriate store for their method of authentication.
Use smart cards with Citrix Receiver for iOS and Android
Users with devices running Citrix Receiver for iOS and Citrix Receiver for Android can authenticate using smart cards, either directly or through NetScaler Gateway. Non-domain-joined devices can be used.
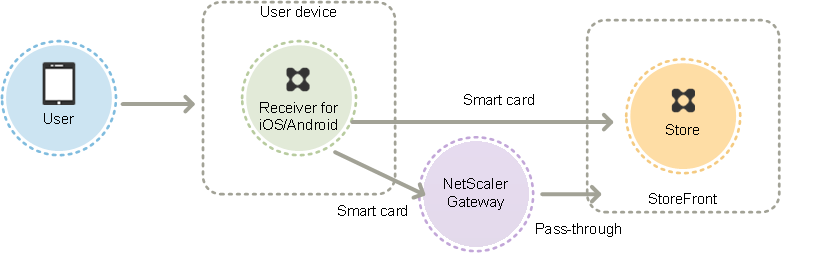
In the case of devices on the local network, the minimum number of logon prompts that users can receive is two. When users authenticate to StoreFront or initially create the store, they are prompted for the smart card PIN. With the appropriate configuration in place, users are prompted to enter their PINs again only when they access their desktops and applications. To achieve this, you enable smart card authentication to StoreFront and install smart card drivers on the VDA.
With these Citrix Receivers, you have the option of specifying smart cards OR domain credentials. If you created a store to use smart cards and you want to connect to the same store using domain credentials, you must add a separate store without turning on smart cards.
Users connecting through NetScaler Gateway must log on using their smart cards and PINs at least twice to access their desktops and applications. Users authenticate using their smart cards and PINs, and, with the appropriate configuration in place, are only prompted to enter their PINs again when they access their desktops and applications. To achieve this, you enable pass-through with NetScaler Gateway authentication to StoreFront and delegate credential validation to NetScaler Gateway. Then, create an additional NetScaler Gateway virtual server through which you route user connections to resources.
Users can log on to NetScaler Gateway using either their smart cards and PINs or with explicit credentials, depending on how you specified the authentication for the connection. Configure pass-through authentication from NetScaler Gateway to StoreFront and delegate credential validation to NetScaler Gateway for smart card users so that users are silently authenticated to StoreFront. If you want to change the authentication method, you must delete and recreate the connection.
Use smart cards with Citrix Receiver for Linux
Users with devices running Citrix Receiver for Linux can authenticate using smart cards in a similar way to users of non-domain-joined Windows devices. Even if the user authenticates to the Linux device with a smart card, Citrix Receiver for Linux has no mechanism to acquire or reuse the PIN entered.
Configure the server side components for smart cards the same way you configure them for use with the Citrix Receiver for Windows. Refer to How To Configure StoreFront 2.x and Smart Card Authentication for Internal Users using Stores and for instructions on using smart cards, see Citrix Receiver for Linux.
The minimum number of logon prompts that users can receive is one. Users log on to their devices and then authenticate to Citrix Receiver for Linux using their smart cards and PINs. Users are not prompted to enter their PINs again when they access their desktops and applications. To achieve this, you enable smart card authentication to StoreFront.
Because users log on to Citrix Receiver for Linux directly, you can enable users to fall back to explicit authentication. If you configure both smart card and explicit authentication, users are initially prompted to log on using their smart cards and PINs but have the option to select explicit authentication if they experience any issues with their smart cards.
Users connecting through NetScaler Gateway must log on using their smart cards and PINs at least once to access their desktops and applications. Users authenticate using their smart cards and PINs and, with the appropriate configuration in place, are not prompted to enter their PINs again when they access their desktops and applications. To achieve this, you enable pass-through with NetScaler Gateway authentication to StoreFront and delegate credential validation to NetScaler Gateway. Then, create an additional NetScaler Gateway virtual server through which you route user connections to resources.
Users can log on to NetScaler Gateway using either their smart cards and PINs, or with explicit credentials. This enables you to provide users with the option to fall back to explicit authentication for NetScaler Gateway logons. Configure pass-through authentication from NetScaler Gateway to StoreFront and delegate credential validation to NetScaler Gateway for smart card users so that users are silently authenticated to StoreFront.
Smart cards for Citrix Receiver for Linux are not supported with the XenApp Services Support sites.
Once smart card support is enabled for both the server and Citrix Receiver, provided the application policy of the smart card certificates allow it, you can use smart cards for the following purposes:
- Smart card logon authentication. Use smart cards to authenticate users to Citrix XenApp and XenDesktop servers.
- Smart card application support. Enable smart card-aware published applications to access local smart card devices.
Use smart cards with XenApp Services Support
Users logging on to XenApp Services Support sites to start applications and desktops can authenticate using smart cards without depending on specific hardware, operating systems, and Citrix Receivers. When a user accesses a XenApp Services Support site and successfully enters a smart card and PIN, PNA determines the user identity, authenticates the user with StoreFront, and returns the available resources.
For pass-through and smart card authentication to work, you must enable Trust requests sent to the XML service.
Use an account with local administrator permissions on the Delivery Controller to start Windows PowerShell and, at a command prompt, enter the following commands to enable the Delivery Controller to trust XML requests sent from StoreFront. The following procedure applies to XenApp 7.5 through 7.8 and XenDesktop 7.0 through 7.8.
- Load the Citrix cmdlets by typing asnp Citrix*. (including the period).
- Type Add-PSSnapin citrix.broker.admin.v2.
- Type Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $True
- Close PowerShell.
For information about configuring the XenApp Services Support smart card authentication method, see Configure authentication for XenApp Services URLs.
Important considerations
Use of smart cards for user authentication with StoreFront is subject to the following requirements and restrictions.
-
To use virtual private network (VPN) tunnels with smart card authentication, users must install the NetScaler Gateway Plug-in and log on through a web page, using their smart cards and PINs to authenticate at each step. Pass-through authentication to StoreFront with the NetScaler Gateway Plug-in is not available for smart card users.
-
Multiple smart cards and multiple readers can be used on the same user device, but if you enable pass-through with smart card authentication, users must ensure that only one smart card is inserted when accessing a desktop or application.
-
When a smart card is used within an application, such as for digital signing or encryption, users might see additional prompts to insert a smart card or enter a PIN. This can occur if more than one smart card has been inserted at the same time. It can also occur due to configuration settings - such as middleware settings like PIN caching that are typically configured using group policy.Users who are prompted to insert a smart card when the smart card is already in the reader must click Cancel. If users are prompted for a PIN, they must enter their PINs again.
-
If you enable pass-through with smart card authentication to XenDesktop and XenApp for Citrix Receiver for Windows users with domain-joined devices who do not access stores through NetScaler Gateway, this setting applies to all users of the store. To enable both domain pass-through and pass-through with smart card authentication to desktops and applications, you must create separate stores for each authentication method. Your users must then connect to the appropriate store for their method of authentication.
-
If you enable pass-through with smart card authentication to XenDesktop and XenApp for Citrix Receiver for Windows users with domain-joined devices accessing stores through NetScaler Gateway, this setting applies to all users of the store. To enable pass-through authentication for some users and require others to log on to their desktops and applications, you must create separate stores for each group of users. Then, direct your users to the appropriate store for their method of authentication.
-
Only one authentication method can be configured for each XenApp Services URL and only one URL is available per store. If you need to enable other types of authentication in addition to smart card authentication, you must create separate stores, each with a XenApp Services URL, for each authentication method. Then, direct your users to the appropriate store for their method of authentication.
-
When StoreFront is installed, the default configuration in Microsoft Internet Information Services (IIS) only requires that client certificates are presented for HTTPS connections to the certificate authentication URL of the StoreFront authentication service. IIS does not request client certificates for any other StoreFront URLs. This configuration enables you to provide smart card users with the option to fall back to explicit authentication if they experience any issues with their smart cards. Subject to the appropriate Windows policy settings, users can also remove their smart cards without needing to reauthenticate.
If you decide to configure IIS to require client certificates for HTTPS connections to all StoreFront URLs, the authentication service and stores must be collocated on the same server. You must use a client certificate that is valid for all the stores. With this IIS site configuration, smart card users cannot connect through NetScaler Gateway and cannot fall back to explicit authentication. Users must log on again if they remove their smart cards from their devices.