Secure
ProGuard enabled for security
We’ve enabled ProGuard to make Citrix Workspace for Android secure through obfuscation. ProGuard renames different parts of the code to prevent inspection of stack traces and makes the Workspace app secure. ProGuard also reduces the app size by shortening the names of app classes, methods, and fields.
Cryptography
This feature is an important change to the secure communication protocol. Cipher suites with the prefix TLS_RSA_ doesn’t offer forward secrecy and are considered weak.
The TLS_RSA_ cipher suites have been removed. The releases 20.6.5 and later supports advanced TLS_ECDHE_RSA_ cipher suites. If your environment isn’t configured with the TLS_ECDHE_RSA_ cipher suites, you can’t launch the client because of weak ciphers.
The following advanced cipher suites are supported:
TLS v1.2 supports:
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS v1.3 supports:
- TLS_AES_256_GCM_SHA384
- TLS_AES_128_GCM_SHA256
Support for Transport Layer Security 1.3
Citrix Workspace app for Android now supports Transport Layer Security (TLS) 1.3. It boosts performance and efficiency. TLS 1.3 provides robust security with its strong cipher suites and one-time session keys.
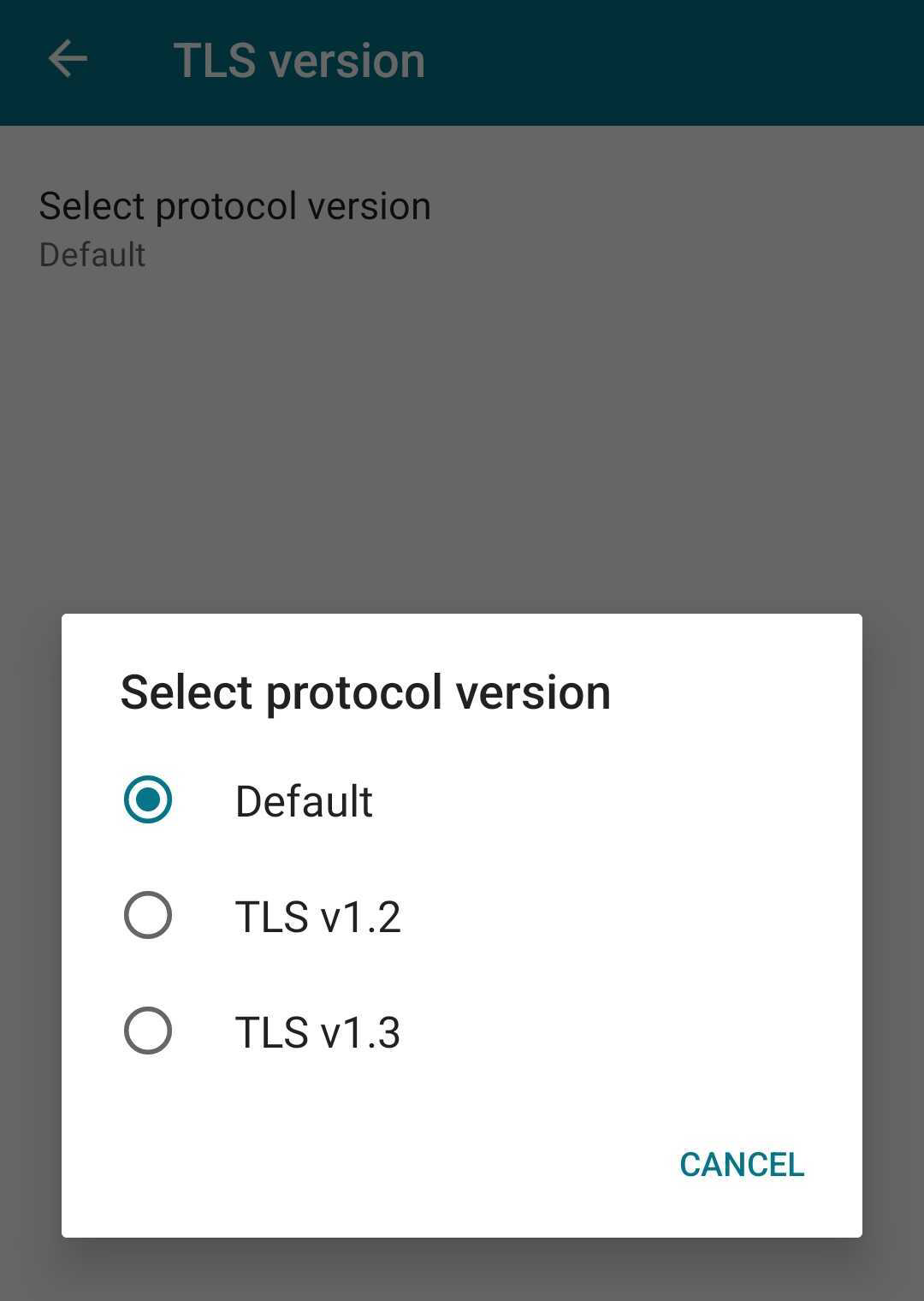
End users can enable it on Citrix Workspace app for Android as follows:
- Go to Citrix Workspace app Settings > TLS version.
-
Tap the Select protocol version option and select TLS v1.3.
For more information, see Cryptography
For more information on help documentation, see TLS version.
Jailbroken devices
Jailbroken devices are those whose owners have modified them, typically to bypass security protections. Jailbroken Android devices pose security risks to your deployment when users connect with them. When Citrix Workspace app for Android does a basic detection of a jailbroken Android device, the app displays an alert to the user.
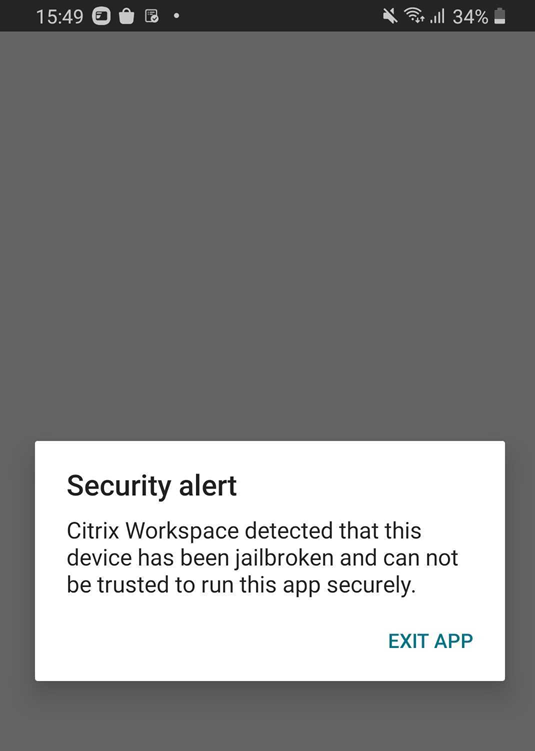
To further help secure your environment, you can configure StoreFront™ or Web Interface to help prevent detected jailbroken devices from running apps.
Note:
Citrix Workspace™ app deactivates itself if it detects a jailbroken device to protect data and maintain security. This ensures that the app cannot be used on devices with unauthorized modifications.
Requirements:
- Citrix Workspace app for Android 24.7.0 or later.
- Access to StoreFront or Web Interface through an administrator account.
To help prevent detected jailbroken devices from running apps:
- Sign in to your StoreFront or Web Interface server as a user with administrator privileges.
-
Find the file default.ica, which is in one of the following locations:
-
C:\\inetpub\\wwwroot\\Citrix\\*storename* conf(Microsoft Internet Information Services) -
C:\\inetpub\\wwwroot\\Citrix\\*storename*\\App _Data(Microsoft Internet Information Services) -
./usr/local/tomcat/webapps/Citrix/XenApp/WEB-INF(Apache Tomcat)
-
- Under the section [Application], add the following:
AllowJailBrokenDevices=OFF - Save the file and restart your StoreFront or Web Interface server.
After you restart the StoreFront server, users who see the alert about jailbroken devices can’t start the apps from your StoreFront or Web Interface server
To allow detected jailbroken devices to run apps:
If you don’t set AllowJailBrokenDevices, the default is to display the alert to jailbroken device users but still allow them to open applications.
If you want to allow your users to run applications on jailbroken devices specifically, set AllowJailBrokenDevices=ON.
When you set AllowJailBrokenDevices to ON, your users see the alert about using a jailbroken device, but they can run applications through StoreFront or Web Interface.