Troubleshoot
How to check app’s version
To check your Citrix Workspace app version, open your app. Tap Settings > About. The version information is displayed on your screen.

How to upgrade Citrix Workspace app to the latest version
You can upgrade to the latest version of Citrix Workspace app from the App Store. Search for Citrix Workspace app and tap the Upgrade button.
How to reset Citrix Workspace app
You can reset your Citrix Workspace app using one of the following methods:
- Delete any existing accounts from Citrix Workspace app
- Clear the Citrix Workspace app storage data
- Uninstall Citrix Workspace app and install the latest Citrix Workspace app for iOS that has the latest fix.
How to collect logs
- Open your Citrix Workspace app and navigate to Settings.
-
Under Help & Support, select Report Issue.
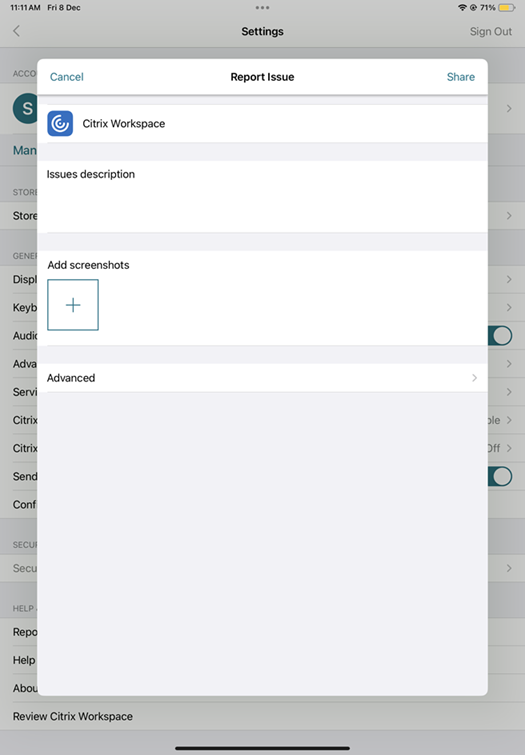
- Reproduce your issue.
-
On the Select log level page, select Verbose.
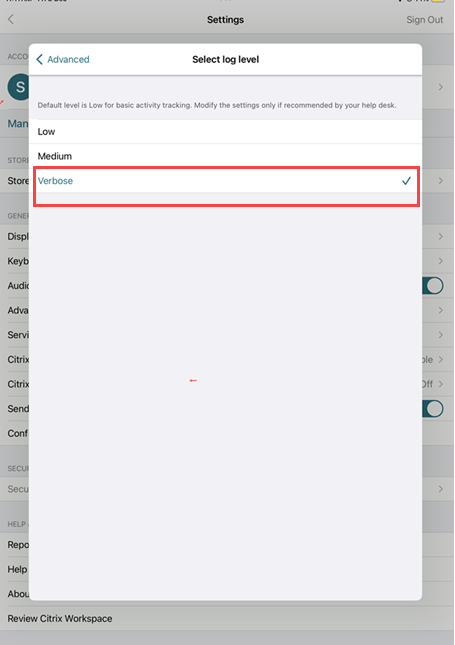
- On the Select Log location page, select Both Console & File.
-
Share the zip file with Citrix.
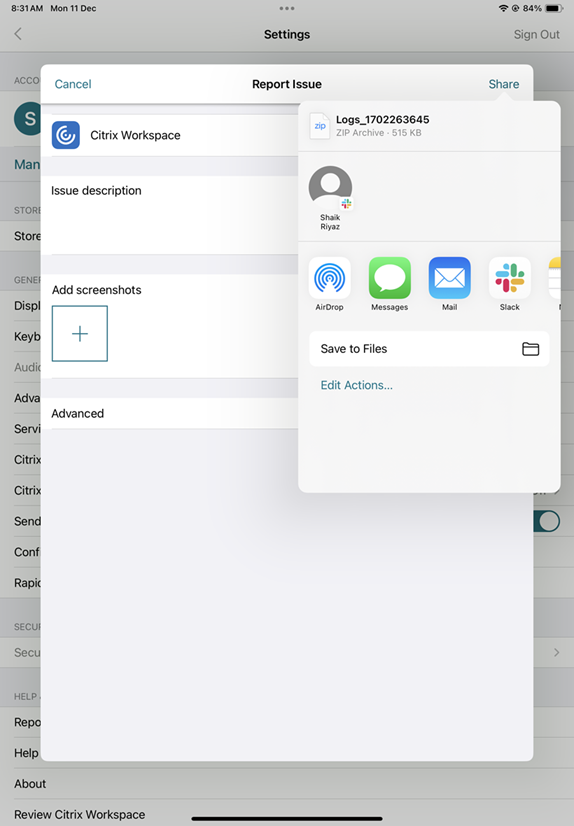
How to request for enhancements
You can send in your requests for enhancements by email at ios_ear_support@citrix.com.
How to access technical preview features
You can request for Technical Preview features by email at ios_ear_support@citrix.com that is unique to each feature. You can find this form attached with the Technical preview announcement in the Product Documentation.
How to provide feedback on EAR
You can provide EAR feedback by email at ios_ear_support@citrix.com.
Common issues and troubleshooting tips
Disconnected sessions
Users can disconnect (but not log off) from a Citrix Workspace app for iOS session in the following ways:
- While viewing a published app or desktop in session:
- tap the arrow at the top of the screen to view the in-session drop-down menu.
- tap the Home button to return to the launch pad.
- notice the white shadow under the icon of one of the published apps that are still in an active session; tap the icon.
- tap disconnect.
- Close Citrix Workspace app for iOS:
- double-tap the device’s Home button.
- locate Citrix Workspace app for iOS in the iOS app switcher view.
- tap disconnect in the dialog that appears.
- Pressing the home button on their mobile device.
- Tapping Home or Switch in the app’s drop-down menu.
The session stays in a disconnected state. Although the user can reconnect later, you can verify that disconnected sessions are shown inactive after a specific interval.
To display the app in inactive mode, configure a session timeout for the ICA-TCP connection in Remote Desktop Session Host Configuration (formerly known as “Terminal Services Configuration”).
For more information about configuring Remote Desktop Services (formerly known as “Terminal Services”), refer to the Microsoft Windows Server product documentation.
Expired passwords
Citrix Workspace app for iOS supports the ability for users to change their expired passwords. Prompts appear for users to enter the required information.
Jailbroken devices
Your users can compromise the security of your deployment by connecting with jailbroken iOS devices. Jailbroken devices are those devices whose owners have modified them, usually with the effect of bypassing certain security protections.
When Citrix Workspace app for iOS detects a jailbroken iOS device, Citrix Workspace app for iOS displays an alert to the user.
To further help to secure your environment, you can configure StoreFront or Web Interface to help to prevent detected jailbroken devices from running apps.
Requirements
- Citrix Receiver for iOS 6.1 or later
- StoreFront 3.0 or Web Interface 5.4 or later
- Access to StoreFront or Web Interface through an administrator account
Note:
Citrix Workspace™ app deactivates itself if it detects a jailbroken device to protect data and maintain security. This ensures that the app cannot be used on devices with unauthorized modifications.
Loss of HDX™ audio quality
From Citrix Virtual Apps and Desktops and Citrix DaaS (formerly Citrix Virtual Apps and Desktops service), HDX audio to Citrix Workspace app for iOS might lose quality. The issue occurs when you use audio and video simultaneously.
The issue occurs when the Citrix Virtual Apps and Desktops™ and Citrix DaaS HDX policies can’t handle the amount of audio data with the video data.
For suggestions about how to create policies to improve audio quality, see Knowledge Center article CTX123543.
Failed to launch desktop and app sessions for customized store experience
You might fail to launch desktop and app sessions from Citrix Workspace app if you have customized store experience. The auto-discovery of store type is supported only for e-mail addresses and not for store URLs. It is recommended to use email address or Web-interface login mode if you have a customized store. For more information, see Manual setupand Configuring email-based account discovery.
To configure an account manually through Web-interface login mode, do the following steps:
- Tap the Accounts icon > Accounts Screen > Plus Sign (+). The New Account screen appears.
- In the lower left corner of the screen, tap the icon to the left of Options and tap Manual setup. Other fields appear on the screen.
- In the Address field, type the secure URL of the site or Citrix Gateway (for example, agee.mycompany.com).
-
Select the Web Interface connection. This connection mode displays a Citrix Virtual Apps™ website similar to a Web browser. This UI is also known as Web View.
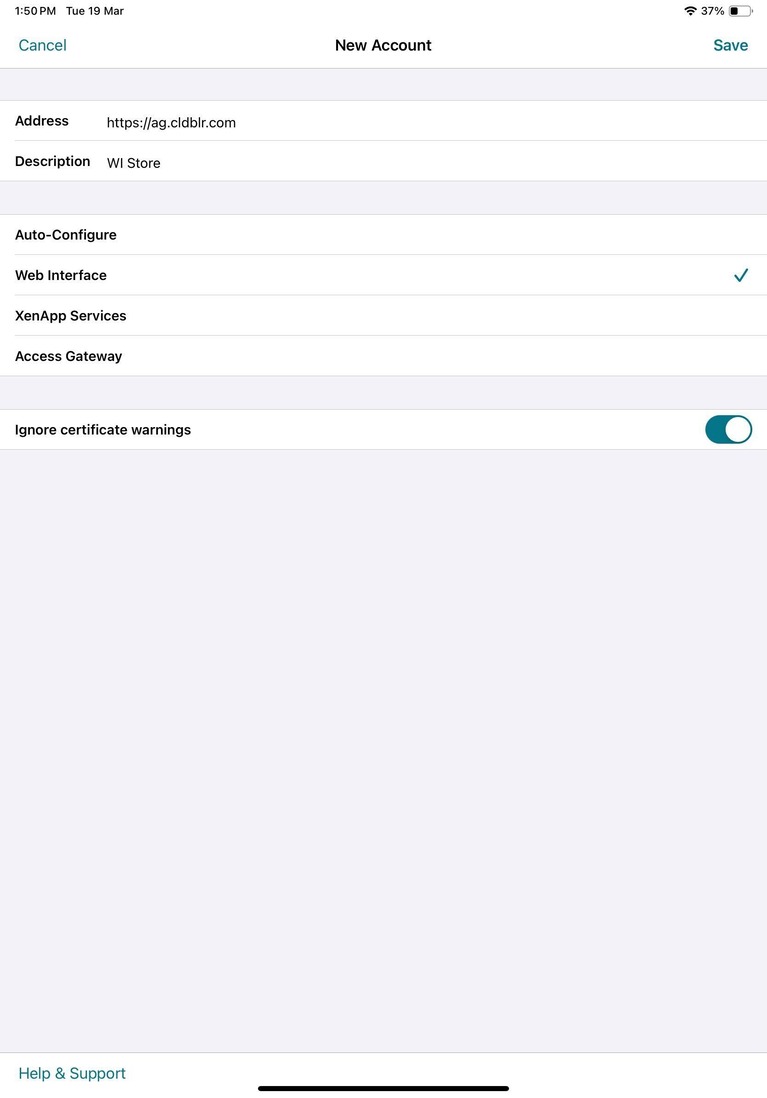
- For certificate security, use the setting in the Ignore certificate warnings field to determine whether you want to connect to the server even if it has an invalid, self-signed, or expired certificate. The default setting is OFF.
Important:
If you do enable this option, make sure you’re connecting to the correct server. Citrix strongly recommends that all servers have a valid certificate to protect user devices from online security attacks. A secure server uses an SSL certificate issued by a certificate authority. Citrix does not support self-signed certificates and does not recommend by-passing the certificate security.
- Tap Save.
- Type your user name and password (or token, if you selected two-factor authentication), and then tap Log On. The Citrix Workspace app for iOS screen appears, in which you can access your desktops and add and open your apps.
Note:
You must enter the user credentials for each connection, as they are not saved in the Web interface login mode.
Citrix Troubleshoot Connection
The Citrix Troubleshoot Connection feature is designed to empower end-users to effectively self-troubleshoot potential desktop or application launch failures. This enhancement aims to provide users with clear diagnostics, potential recommendations, and the ability to run fixes with a simple click.
How It Works
The feature delivers more granular and enhanced error messages to help users clearly understand the root cause of launch failures. The Troubleshoot Connection feature analyzes connection issues to the Virtual Delivery Agent (VDA) in real time during the launch process. It then presents user-friendly error messages and recommendations, enabling users to either resolve the issue directly or gather logs for a support ticket if needed.
Connection paths analyzed
The feature diagnoses potential virtual app and desktop launch issues across critical connection points, including:
- Network connectivity from the Client to the Gateway.
- Gateway to StoreFront server connection.
- StoreFront server to Broker connection.
- Broker to VDA connection.
Enhanced error messages and diagnostics
In the event of launch failures, Citrix now displays clear, user-friendly error messages that pinpoint specific connection issues, such as network errors, server unavailability, or VDA failures. For administrators, detailed error codes are provided in the logs, categorized into server-side and client-side errors, serving as valuable references for deeper investigation.
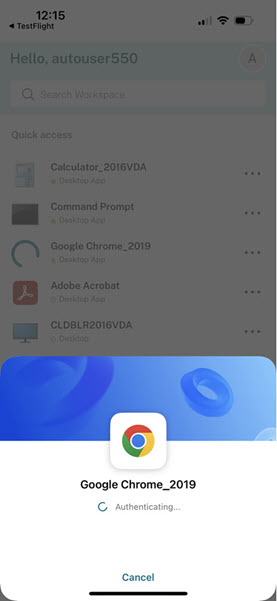
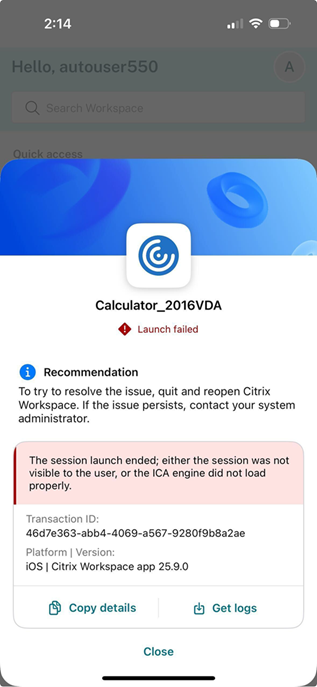
Self-recovery and remediation actions
The Citrix Troubleshoot Connection feature includes steps that users can take to automatically recover from common issues, thereby minimizing the need for support intervention. Following are the potential problems that can be resolved with guided remediation:
- Restart VDA
- Restart Citrix Workspace app (CWA) - Re-Login to CWA
- Refresh the resource list
- Refresh the app and try
- Reconfigure the store
- Upgrade CWA
- Reinstall CWA
- Check the network
- Wait And retry
System requirements
To use the Troubleshoot Connection feature, have the following Citrix Workspace app versions:
- Citrix Workspace app for iOS: Version 2509 and later
Note:
The error messages include server error codes as well, the details of the same for both on-premises and cloud can be obtained from the section Error codes
The Troubleshoot Connection feature is enabled by default in DaaS environments. Granular error messages and recommendations are available for both browser-launched sessions and sessions started with Citrix Workspace app. Error codes and transaction IDs are recorded in logs for administrator reference. Error codes are categorized as server-side or client-side. For certain errors, a remediation option to restart the Virtual Delivery Agent (VDA) is provided. This feature does not support sessions in hybrid mode. For example, it cannot be used when you download an ICA file in a browser, then open that file using Citrix Workspace app.
FAQs
How to improve the video performance on virtual app and virtual desktop for low-powered or mobile devices
For information on how to improve and configure virtual desktop video performance using the MaxFramesPerSecond registry value or using HDX policies, depending on your Citrix Virtual Apps and Desktops version, see the Knowledge Center article CTX123543.
I can’t see my apps or desktops after signing on to Citrix Workspace app
Contact your company’s help desk or your IT Support team administrator for further assistance.
How to troubleshoot slow connections
If you face any of the following issues, follow the steps mentioned in the following Workaround section.
- Slow connections to the Citrix Virtual Apps and Desktops site
- Missing app icons
- Recurring Protocol Driver Error messages
Workaround
Disable Citrix PV Ethernet Adapter properties for the network interface on Citrix Virtual Apps server, Citrix Secure Web Gateway™, and Web Interface server. The Citrix PV Ethernet Adapter properties include the following properties that are enabled by default. You need to disable all of these properties.
- Large Send Offload
- Offload IP Checksum
- Offload TCP Checksum
- Offload UDP Checksum
Note:
Server restart isn’t required. This workaround applies to the Windows Server 2003 and 2008 32-bit. This issue does not affect the Windows Server 2008 R2.
Troubleshoot issue with Numeric keys and special characters
If numeric keys or Chinese IME characters do not function as expected, you need to disable the Unicode Keyboard option. To disable the Unicode Keyboard option:
- Navigate to Settings > Keyboard Options.
- Set Use Unicode Keyboard to Off.
In this article
- How to check app’s version
- How to upgrade Citrix Workspace app to the latest version
- How to reset Citrix Workspace app
- How to collect logs
- How to request for enhancements
- How to access technical preview features
- How to provide feedback on EAR
- Common issues and troubleshooting tips
- Citrix Troubleshoot Connection
- FAQs