SIEM integration using Kafka or Logstash based data connector
Citrix Analytics for Security™ SIEM integration enables you to export and correlate the users’ data from the Citrix Analytics to your SIEM environment and get deeper insights into your organization’s security posture.
For more information about the benefits of the integration and the type of data events (risk insights and data source events) that is sent to your SIEM, see Security Information and Event Management integration.
You can integrate Citrix Analytics for Security with your SIEM solutions through the following two mechanisms (supported by your SIEM and IT deployment):
- Connect via Kafka endpoints
- Connect via Logstash data broker with Kafka-based ingestion
Prerequisites
-
Turn on data processing for at least one data source. It helps Citrix Analytics for Security to begin the integration with your SIEM tool.
-
Ensure that the following endpoint is in the allow list in your network.
Endpoint United States region European Union region Asia Pacific South region Kafka brokers casnb-0.citrix.com:9094casnb-eu-0.citrix.com:9094casnb-aps-0.citrix.com:9094casnb-1.citrix.com:9094casnb-eu-1.citrix.com:9094casnb-aps-1.citrix.com:9094casnb-2.citrix.com:9094casnb-eu-2.citrix.com:9094casnb-aps-2.citrix.com:9094casnb-3.citrix.com:9094
Integrate with a SIEM service using Kafka
Kafka is an open source software and used for real-time streaming of data. Using Kafka, you can analyze the real-time data to gain faster insights. Mostly, the large organizations who handle adequate data, use Kafka.
Northbound Kafka is an internal middle layer enabling Citrix Analytics to share real-time data feeds with the SIEM customers through Kafka endpoints. If your SIEM supports Kafka endpoints, use the parameters provided in the Logstash config file and the certificate details in the JKS file or the PEM file to integrate your SIEM with Citrix Analytics for Security.
The following parameters are required to integrate using Kafka:
| Attribute name | Description | Configuration data sample |
|---|---|---|
| User name | User name provided by Kafka. | 'sasl.username': cas_siem_user_name, |
| Host | Host name of the Kafka server to which you want to connect. | 'bootstrap.servers': cas_siem_host, |
| Topic name/Client ID | Client ID assigned to each tenant. | 'client.id': cas_siem_topic, |
| Group name/ID | Group name that you need to read the messages shared by the consumers. | 'group.id': cas_siem_group_id, |
| Security protocol | Name of the security protocol. | 'security.protocol': 'SASL_SSL', |
| SASL mechanisms | Authentication mechanism that is typically used for encryption to implement secure authentication. | 'sasl.mechanisms': 'SCRAM-SHA-256', |
| SSL truststore location | Location where you can store the certificate file. The client truststore password is optional and is expected to be left empty. | 'ssl.ca.location': ca_location |
| Session timeout | The session timeout used to detect client failures while using Kafka. | 'session.timeout.ms': 60000, |
| Auto offset reset | Defines the behavior while consuming data from a topic partition when there is no initial offset. You can set the values such as, latest, earliest, or none. | 'auto.offset.reset': 'earliest', |
The following is a sample configuration output:
{'bootstrap.servers': cas_siem_host,
'client.id': cas_siem_topic,
'group.id': cas_siem_group_id,
'session.timeout.ms': 60000,
'auto.offset.reset': 'earliest',
'security.protocol': 'SASL_SSL',
'sasl.mechanisms': 'SCRAM-SHA-256',
'sasl.username': cas_siem_user_name,
'sasl.password': self.CLEAR_PASSWORD,
'ssl.ca.location': ca_location
}
<!--NeedCopy-->
The aforementioned parameters are available in the Logstash configuration file. To download the configuration file, navigate to Settings > Data Exports > SIEM Environment > select Others tab > click Download Logstash Config File.
To understand/know more about the configuration values, refer Configuration.
Data flow
The authentication data communication happens between the Kafka server side Brokers (Citrix Analytics for Security cloud) and Kafka clients. All brokers/external clients’ communication uses the enabled SASL_SSL security protocol and target 9094 port for public access.
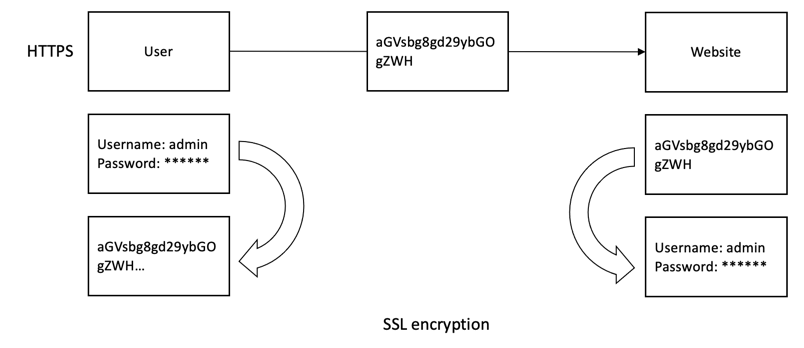
Apache Kafka has a security component to encrypt the data in flight using SSL encryption. The data transmission over the network is encrypted and secured when encryption is enabled and SSL certificates are set. Only the first and the final machine possess the ability to decrypt the packets being sent through SSL.
Authentications
There are two levels of authentication available as below:
-
TLS/between client and server.
- The server certificates (public keys) for TLS authentication exchange between client and server.
- The client-based authentication or two way authentications are not supported (where client private key certificates is required).
-
Username/password for access control to TOPICS/endpoints
- Ensures that specific client can read only from specific customer topic
- SASL/SCRAM is used for username/password authentication mechanism along with TLS encryption to implement secure authentication.
Encryption with SSL and Authentication with SASL/SSL&SASL/PLAINTEXT
By default, Apache Kafka communicates in PLAINTEXT, where all data is sent in the clear and any of the routers can read the data content. Apache Kafka has a security component to encrypt the data in flight using SSL encryption. With encryption enabled and carefully setup SSL certificates, the data is now encrypted and securely transmitted over the network. With SSL encryption, only the first and the final machine possesses the ability to decrypt the packet being sent.
Since the two-way SSL encryption is used, user name/password login is safe for external communications.
The encryption is only in-flight and the data still sits unencrypted on broker’s disk.
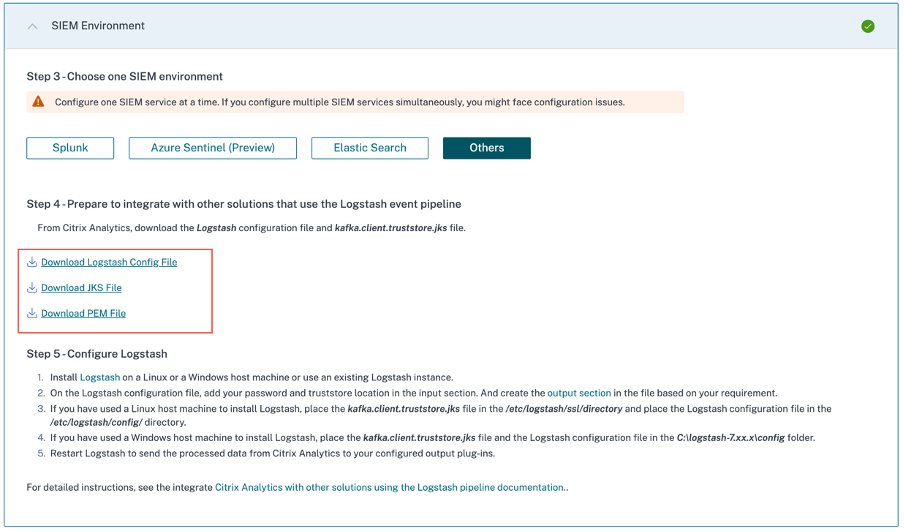
In the client configuration, the client truststore JKS file and PEM file (converted from truststore jks file) are required. You can download these files from Citrix Analytics for Security GUI as shown in the following screenshot:
SIEM integration using Logstash
If your SIEM does not support Kafka endpoints, then you can use the Logstash data collection engine. You can send the data events from Citrix Analytics for Security to one of the output plug-ins that are supported by Logstash.
The following section describes the steps that you must follow to integrate your SIEM with Citrix Analytics for Security by using Logstash.
Integrate with a SIEM service using Logstash
-
Go to Settings > Data Exports.
-
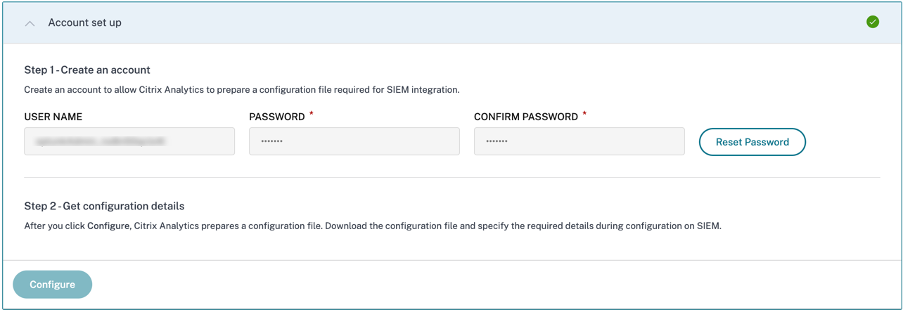
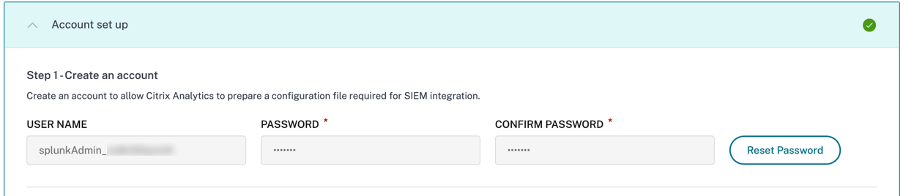
On the Account set up page, create an account by specifying the user name and a password. This account is used to prepare a configuration file, which is required for integration.
-
Ensure that the password meets the following conditions:

-
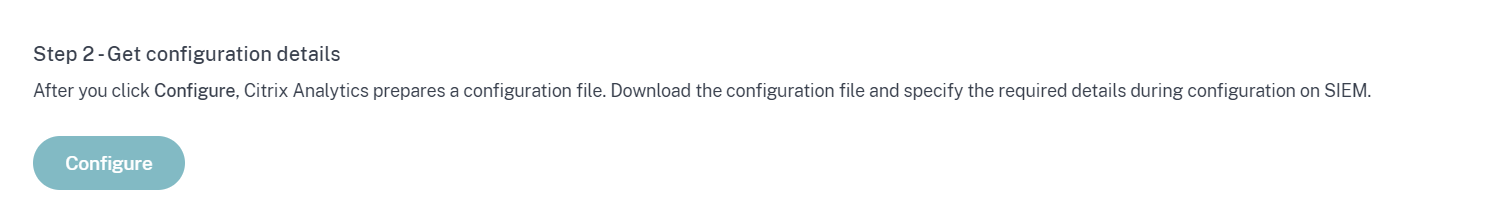
Select Configure to generate the Logstash configuration file.
-
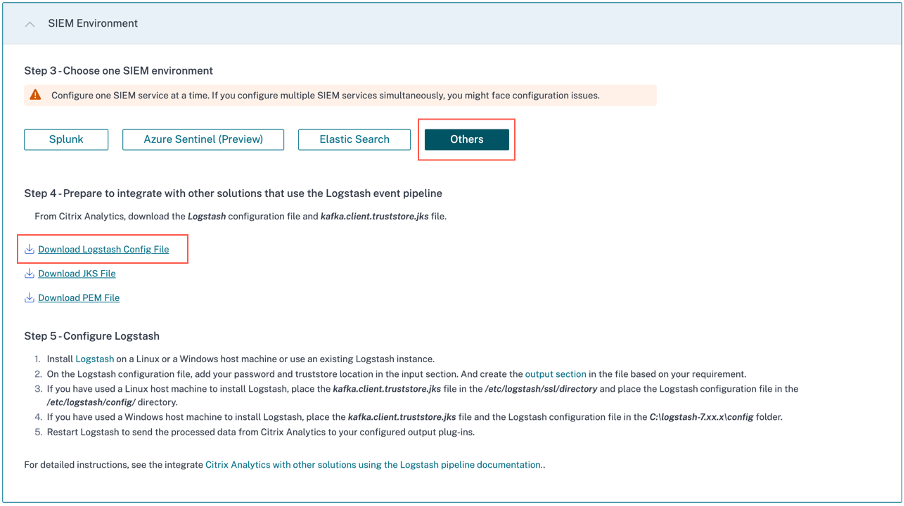
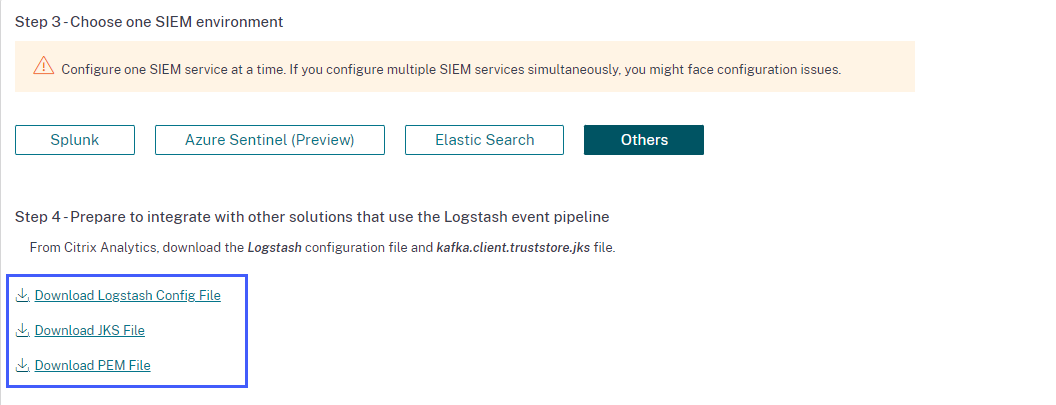
Select the Others tab to download the configuration files.
-
Logstash config file: This file contains the configuration data (input, filter, and output sections) for sending events from Citrix Analytics for Security using the Logstash data collection engine. For information on Logstash config file structure, see the Logstash documentation.
-
JKS file: This file contains the certificates required for SSL connection. This file is required when you integrate your SIEM using Logstash.
-
PEM file: This file contains the certificates required for SSL connection. This file is required when you integrate your SIEM using Kafka.
Note
These files contain sensitive information. Keep them in a safe and secure location.
-
-
Configure Logstash:
-
On your Linux or Windows host machine, install Logstash (tested versions for compatibility with Citrix Analytics for Security: v7.17.7 and v8.5.3). You can also use your existing Logstash instance.
-
On the host machine where you have installed Logstash, place the following files in the specified directory:
Host machine type File name Directory path Linux CAS_Others_LogStash_Config.config For Debian and RPM packages: /etc/logstash/conf.d/For .zip and .tar.gz archives: {extract.path}/configkafka.client.truststore.jks For Debian and RPM packages: /etc/logstash/ssl/For .zip and .tar.gz archives: {extract.path}/sslWindows CAS_Others_LogStash_Config.config C:\logstash-7.xx.x\configkafka.client.truststore.jks C:\logstash-7.xx.x\config -
Logstash configuration file contains sensitive information such as Kafka credentials, LogAnalytics Workspace IDs, Primary Keys. It is recommended that these sensitive credentials are not stored as a plaintext. To secure the integration, a Logstash keystore can be used to add keys with their respective values which can in turn be referenced using key names in the configuration file. For additional information on the Logstash keystore and how it enhances the security of your settings, see Secrets keystore for secure settings.
-
Open the Logstash config file and do the following:
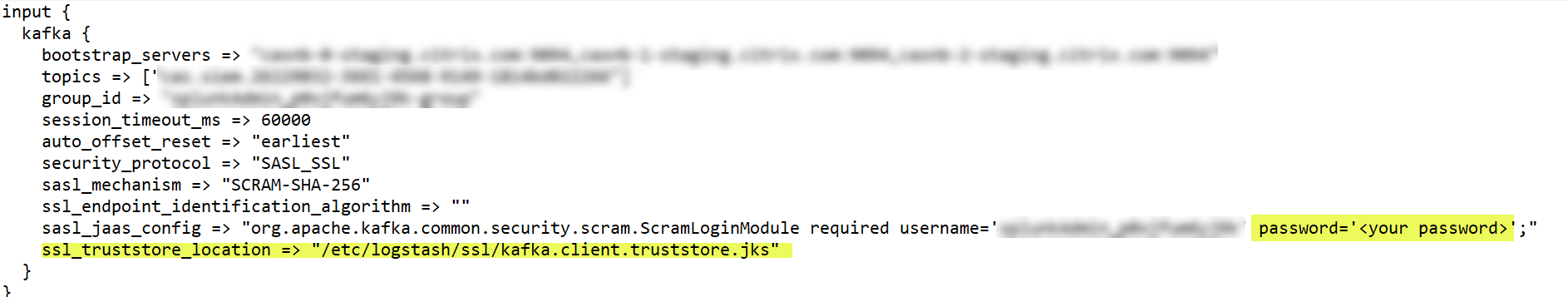
In the input section of the file, enter the following information:
-
Password: The password of the account that you have created in Citrix Analytics for Security to prepare the configuration file.
-
SSL truststore location: The location of your SSL client certificate. This is the location of the kafka.client.truststore.jks file in your host machine.
In the output section of the file, enter the destination path or details where you want to send the data. For information on the output plug-ins, see the Logstash documentation.
The following snippet shows that the output is written to a local log file.
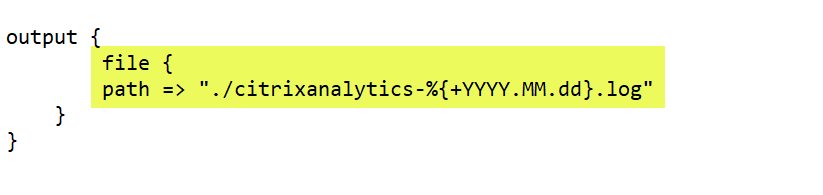
-
-
Restart your host machine to send processed data from Citrix Analytics for Security to your SIEM service.
-
After configuration is complete, log in to your SIEM service and verify the Citrix Analytics data in your SIEM.
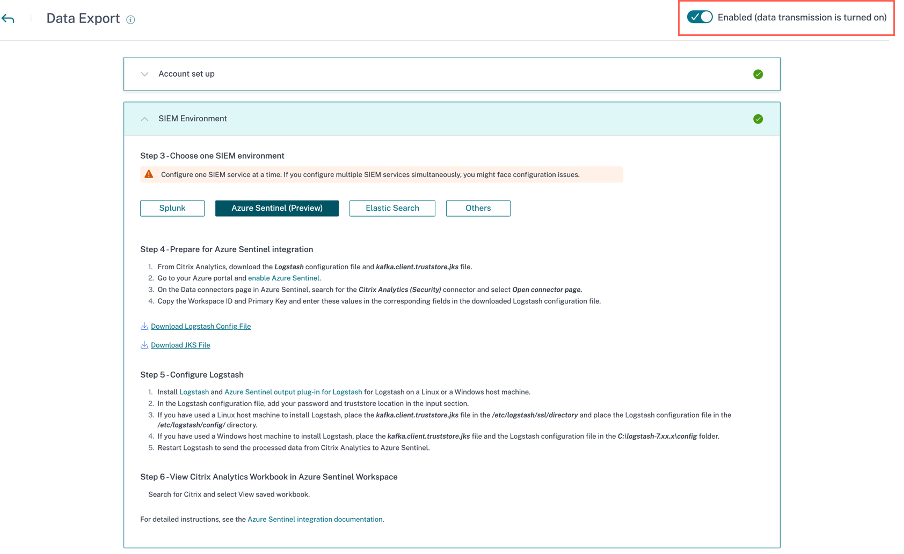
Turn on or off data transmission
After Citrix Analytics for Security prepares the configuration file, data transmission is turned on for your SIEM.
To stop transmitting data from Citrix Analytics for Security:
- Go to Settings > Data Exports.
-
Turn off the toggle button to disable the data transmission. By default the data transmission always enabled.
A warning window appears for your confirmation. Click the Turn off data transmission button to stop the transmission activity.
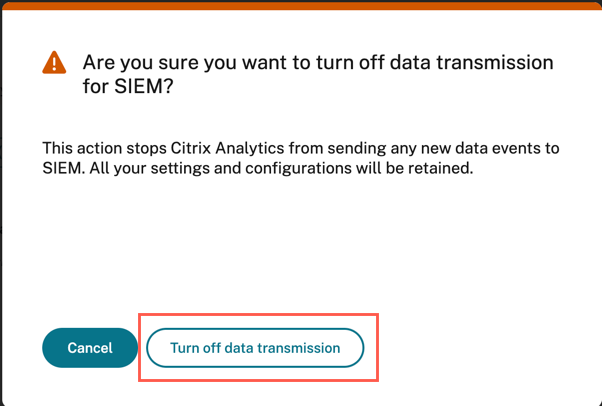
To enable data transmission again, turn on the toggle button.
Note
Contact CAS-PM-Ext@cloud.com to request assistance for your SIEM integration, exporting data to your SIEM, or provide feedback.