Active Directory with Connector Appliance
You can use Connector Appliance to connect a resource location to forests which do not contain Citrix Virtual Apps and Desktops™ resources. For example, in the case of Citrix Virtual Apps and Desktops, customers with some forests only are used for user authentication.
When using multi-domain Active Directory with Connector Appliance, the following restrictions apply:
- Connector Appliance cannot be used in place of Cloud Connectors in forests that contain VDAs.
Requirements
Active Directory requirements
- Joined to an Active Directory domain that contains the resources and users that you use to create offerings for your users. For more information, see Deployment scenarios for Connector Appliances in Active Directory in this article.
- Each Active Directory forest that you plan to use with Citrix Cloud™ must always be reachable by two Connector Appliances.
- The Connector Appliance must be able to reach domain controllers in both the forest root domain and in the domains that you intend to use with Citrix Cloud. For more information, see the following Microsoft support articles:
- How to configure domains and trusts
- “Systems services ports” section in Service overview and network port requirements for Windows
- Use universal security groups instead of global security groups. This configuration ensures that user group membership can be obtained from any domain controller in the forest.
Network requirements
- Connected to a network that can contact the resources you use in your resource location.
- Connected to the Internet. For more information, see System and Connectivity Requirements.
In addition to the ports listed in Connector Appliance communication, the Connector Appliance requires an outbound connection to the Active Directory domain via these ports:
| Service | Port | Supported Domain Protocol |
|---|---|---|
| Kerberos | 88 | TCP/UDP |
| End Point Mapper (DCE/RPC Locator Service) | 135 | TCP |
| NetBIOS Name Service | 137 | UDP |
| NetBIOS Datagram | 138 | UDP |
| NetBIOS Session | 139 | TCP |
| LDAP | 389 | TCP/UDP |
| SMB over TCP | 445 | TCP |
| Kerberos kpasswd | 464 | TCP/UDP |
| Global Catalog | 3268 | TCP |
| Dynamic RPC Ports | 49152–65535 | TCP |
The Connector Appliance uses LDAP signing to secure connections to the domain controller. This means that LDAP over SSL (LDAPS) is not required. For more information on LDAP signing, see How to enable LDAP signing in Windows Server and Microsoft Guidance for Enabling LDAP Channel Binding and LDAP Signing.
Supported Active Directory functional levels
Connector Appliance has been tested and is supported with the following forest and domain functional levels in Active Directory.
| Forest Functional Level | Domain Functional Level | Supported Domain Controllers |
|---|---|---|
| Windows Server 2016 | Windows Server 2016 | Windows Server 2019 |
Other combinations of domain controller, forest functional level, and domain functional level have not been tested with the Connector Appliance. However, these combinations are expected to work and are also supported.
Connect an Active Directory domain to Citrix Cloud by using Connector Appliance
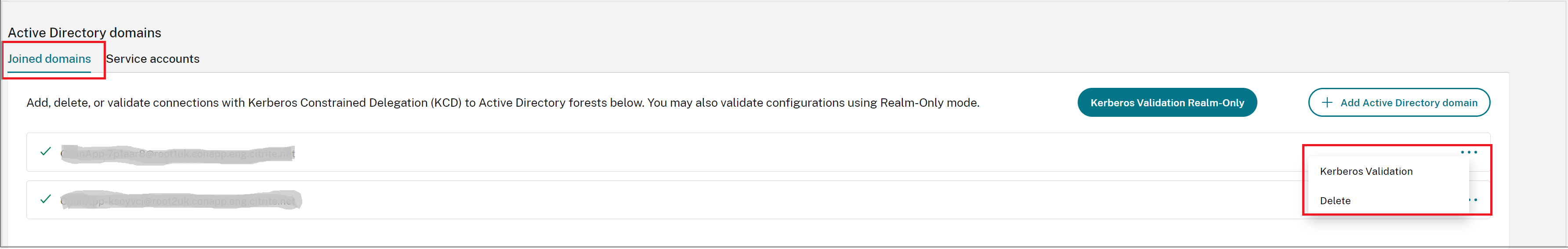
When you connect to the Connector Appliance administration webpage, the Active Directory domains section displays two tabs.
- Joined Domains – Used for joining the Connector Appliance to AD Domains by creating a machine account for the appliance in the Domain. Kerberos can be validated by clicking the ellipsis menu on the right-hand side of the joined domain. Machine account presence in the domain is required.
To configure Active Directory to connect to Citrix Cloud through the Connector Appliance, complete the following steps.
-
Install a Connector Appliance in your resource location.
You can follow the information in the Connector Appliance product documentation.
-
Connect to the Connector Appliance administration webpage in your browser by using the IP address provided in the Connector Appliance console.
-
In the Active Directory domains section, navigate to the Joined domains tab.
-
Click + Add Active Directory domain, a new pop-up window displays to enter the domain name.
The Connector Appliance checks the domain. If the check is successful, the Join Active Directory dialog opens. This new window allows you to input the user name and password to join the domain.
- Click Add.
- Provide the user name and password of an Active Directory user with join permission for the domain.
-
The Connector Appliance suggests a machine name. You can choose to override the suggested name and provide your own machine name that is up to 15 characters in length.
This machine name is created in the Active Directory domain when the Connector Appliance joins it.
-
Click Join.
The domain is now listed in the Active Directory domains section of the Connector Appliance UI.
- To add more Active Directory domains, select + Add Active Directory domain and repeat the preceding steps.
-
Go to the domains page in Citrix Cloud Console and select Connector Appliance to service your domains.
- If you have not already registered your Connector Appliance, continue with the steps as described in Register your Connector Appliance with Citrix Cloud.
Note
If you encounter an error while attempting to join the domain, ensure that your environment meets the necessary Active Directory requirements and the network requirements.
What’s next
-
You can add more domains to this Connector Appliance.
Note:
The Connector Appliance is tested with up to 10 forests.
-
For resilience, add each domain to more than one Connector Appliance in each resource location.
Viewing your Active Directory configuration
You can view the configuration of the Active Directory domains and Connector Appliances in your resource locations in the following places:
-
In Citrix Cloud:
- In the menu, go to the Identity and Access Management page.
-
Go to the Domains tab.
Your Active Directory domains are listed with the resource locations that they are part of.
-
In the Connector Appliance webpage:
- Connect to the Connector Appliance webpage by using the IP address provided in the Connector Appliance console.
- Log in with the password you created when you first registered.
- In the Active Directory domains section of the page, you can see the list of Active Directory domains this Connector Appliance is joined to.
Removing an Active Directory domain from a Connector Appliance
To leave an Active Directory domain, complete the following steps:
- Connect to the Connector Appliance webpage by using the IP address provided in the Connector Appliance console.
- Log in with the password you created when you first registered.
- In the Active Directory domains section of the page, find the domain you want to leave in the list of joined Active Directory domains.
- Note the name of the machine account created by your Connector Appliance.
- Click the delete icon (trashcan) next to the domain. A confirmation dialog appears.
- Click Continue to confirm the action.
- Go to your Active Directory controller.
- Delete the machine account created by your Connector Appliance from the controller.
Deployment scenarios for using Connector Appliance with Active Directory
You can use both Cloud Connector and Connector Appliance to connect to Active Directory controllers. The type of connector to use depends on your deployment.
Use the Connector Appliance to connect your resource location to the Active Directory forest in the following situations:
- You have one or more forests that are only used for user authentication
- You want to reduce the number of connectors required to support multiple forests
- You need a Connector Appliance for other use cases
Only users in one or more forests with a single set of Connector Appliances for all forests
This scenario applies to Workspace Standard customers or customers using Connector Appliance for Secure Private Access.
In this scenario, there are several forests that contain only user objects (forest1.local, forest2.local). These forests do not contain resources. One set of Connector Appliances is deployed within a resource location and joined to the domains for each of these forests.
- Trust relationship: None
- Domains listed in Identity and Access Management:
forest1.local,forest2.local - User logons to Citrix Workspace™: Supported for all users
- User logons to an on-premises StoreFront™: Supported for all users
Users and resources in separate forests (with trust) with a single set of Connector Appliances for all forests
This scenario applies to Citrix Virtual Apps and Desktops customers with multiple forests.
In this scenario, some forests (resourceforest1.local, resourceforest2.local) contain your resources (for example, VDAs) and some forests (userforest1.local, userforest2.local) contain only your users. A trust exists between these forests that allows users to log on to resources.
One set of Cloud Connectors is deployed within the resourceforest1.local forest. A separate set of Cloud Connectors is deployed within the resourceforest2.local forest.
One set of Connector Appliances is deployed within the userforest1.local forest and the same set is deployed within the userforest2.local forest.
- Trust relationship: Bi-directional forest trust, or uni-directional trust from the resource forests to the user forests
- Domains listed in Identity and Access Management:
resourceforest1.local,resourceforest2.local,userforest1.local,userforest2.local - User logons to Citrix Workspace: Supported for all users
- User logons to an on-premises StoreFront: Supported for all users
In this article
- Requirements
- Supported Active Directory functional levels
- Connect an Active Directory domain to Citrix Cloud by using Connector Appliance
- What’s next
- Viewing your Active Directory configuration
- Removing an Active Directory domain from a Connector Appliance
- Deployment scenarios for using Connector Appliance with Active Directory