Authenticate
Enhancing Citrix® security with pre-populated user name
Starting with version 2411, administrators can use Mobile Device Management (MDM) to push the user name in a specific format to manage devices. Citrix Workspace™ app reads this configuration, retrieves the user name, and pre-populates it within the authentication prompt, making it read-only. This ensures that only end users to whom a Mac is registered can authenticate to the Citrix Workspace app on that specific machine. This feature enhances sign-in security and gives administrators greater control over authentication.
You can configure this feature through MDM using the following settings:
<array>
<dict>
<key>LockUserName</key>
<true/>
<key>CitrixUserName</key>
<string>UserNameValue</string>
</dict>
</array>
<!--NeedCopy-->
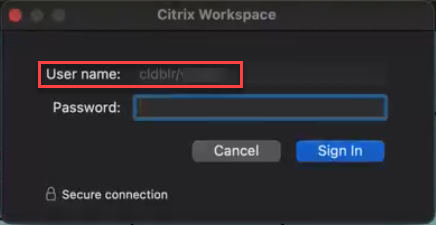
Limitations:
- This solution works only with on-premises stores that use basic authentication.
- It is not compatible with SAML (WebView) authentication.
- The scope is limited to the Citrix Workspace app and browser-based logins are not managed.
For more information on how to use MDM, see Mobile Device Management.
Mandate end users to authenticate and access apps and desktops through native app
Starting with version 2411, admins can mandate users on Mac devices to access Citrix Workspace app exclusively through the native app. When this feature is enabled, users attempting to access the store URL and third-party browsers are automatically redirected to the Citrix Workspace app. This ensures they can take advantage of all the native app’s capabilities and enjoy a seamless user experience. Also, users connecting through a browser while invoking the HDX™ engine are prompted to add the store to the native client for future access. This feature also gives admins greater control over the user environment and enhances security by keeping the authentication process within the native app, eliminating the need to download ICA files.
Admins can enable this feature using their Citrix Cloud account. This feature is currently supported for Cloud stores only. For more information, see Mandate end users to authenticate and access apps and desktops through native app.
Enhancements to the smart card reader authentication
Starting with the version 2409, Citrix Workspace app supports the plug and play functionality for the smart card readers. With this feature, users can conveniently use their smart cards without needing to manually connect the reader before launching an ICA® session. The system automatically detects and initializes the reader once the smart card is inserted.
Also, Citrix Workspace app handles concurrent smart card command requests more efficiently. When multiple processes on the Virtual Delivery Agent (VDA) read the smart card simultaneously, the redirection speed is improved.
These enhancements ensure a smoother user experience while using the smart card reader for authentication.
Support for fast smart card
Starting with the version 2409, Citrix Workspace app supports the Fast smart card feature. Fast Smart card is an improvement over the existing HDX PC/SC-based smart card redirection. It improves performance significantly when smart cards are used in high-latency WAN environments.
Enabling the fast smart card logon on Citrix Workspace app
To enable this feature, you need to specify the location of the PKCS#11 library file on the Smart card settings in Citrix Workspace app preferences. For more information, see Specifying a PKCS#11 module for smart card authentication.
Disabling the fast smart card logon on Citrix Workspace app
To disable fast smart card logon on Citrix Workspace app, set the “PKCS#11 module” in Citrix Workspace app Preferences to “None Selected”.
Note:
- Fast smart card logon is enabled by default on the VDA and disabled by default on Citrix Workspace app.
- Earlier versions of Citrix Workspace app for Mac employed the PKCS#11 module to establish SSL connections, rather than relying on smart card redirection and authentication. Presently, fast smart cards on Citrix Workspace app for Mac exclusively support cards that use the RSA algorithm. Attempting to configure an incompatible PKCS#11 module can lead to authentication failure.
Smart card
Citrix Workspace app for Mac supports smart card authentication in the following configurations:
-
Smart card authentication to Workspace for Web or StoreFront 3.12 and later.
-
Citrix Virtual Apps and Desktops™ 7 2203 and later.
-
XenApp and XenDesktop 7.15 and later.
-
Smart card-enabled applications, such as Microsoft Outlook and Microsoft Office that allow users to digitally sign or encrypt documents available in virtual desktop or application sessions.
-
Citrix Workspace app for Mac supports using multiple certificates with a single smart card or with multiple smart cards. When your user inserts a smart card into a card reader, the certificates are available to all applications running on the device, including Citrix Workspace app for Mac.
-
For double-hop sessions, a further connection is established between Citrix Workspace app for Mac and your user’s virtual desktop.
About smart card authentication to Citrix Gateway
There are multiple usable certificates when you use a smart card to authenticate a connection. Citrix Workspace app for Mac prompts you to select a certificate. After you select a certificate, Citrix Workspace app for Mac prompts you to enter the smart card password. Once authenticated, the session launches.
If there’s only one suitable certificate on the smart card, Citrix Workspace app for Mac uses that certificate and does not prompt you to select it. However, you must still enter the password associated with the smart card to authenticate the connection and to start the session.
Specifying a PKCS#11 module for smart card authentication
Note:
Installing the PKCS#11 module isn’t mandatory. This section only applies to ICA sessions. It does not apply to Citrix Workspace access to Citrix Gateway or StoreFront where a smart card is required.
To specify the PKCS#11 module for smart card authentication:
- In Citrix Workspace app for Mac, select Preferences.
- Click Security & Privacy.
- In the Security & Privacy section, click Smart Card.
- In the PKCS#11 field, select the appropriate module. Click Other to browse to the location of the PKCS#11 module if the module you wanted isn’t listed.
- After selecting the appropriate module, click Add.
Supported readers, middleware, and smart card profiles
Citrix Workspace app for Mac supports most macOS-compatible smart card readers and cryptographic middleware. Citrix has validated the operation with the following.
Supported readers:
- Common USB connect smart card readers
Supported middleware:
- Clarify
- ActivIdentity client version
- Charismathics client version
Supported smart cards:
- PIV cards
- Common Access Card (CAC)
- Gemalto .NET cards
Follow the instructions provided by your vendor’s macOS-compatible smart card reader and cryptographic middleware for configuring user devices.
Restrictions
- Certificates must be stored on a smart card, not on the user device.
- Citrix Workspace app for Mac does not save the user certificate choice.
- Citrix Workspace app for Mac does not store or save the user’s smart card PIN. OS handles the PIN acquisitions, which might have its own caching mechanism.
- Citrix Workspace app for Mac does not reconnect sessions when a smart card is inserted.
- To use VPN tunnels with smart card authentication, you must install the Citrix Gateway Plug-in and log on through a webpage. Use your smart cards and PINs to authenticate at each step. Pass-through authentication to StoreFront with the Citrix Gateway Plug-in isn’t available for smart card users.
Conditional Access with Azure Active Directory
This authentication method is currently not supported on Citrix Workspace app for Mac.
User-Agent
Citrix Workspace app sends a user agent in network requests that can be used to configure authentication policies including redirection of authentication to other Identity Providers (IdPs).
Note:
Don’t mention the version numbers while configuring the policies.
| Scenario | Description | User-Agent |
|---|---|---|
|
Regular HTTP Requests
|
In general, a network request made by Citrix Workspace app contains a general User-Agent.
For example, the following network requests contain a general User-Agent |
CitrixReceiver/23.05.0.36 MacOSX/13.4.0 com.citrix.receiver.nomas X1Class CWACapable
|
|
Cloud Store
|
When users add a cloud store to Citrix Workspace app, the network requests made by Citrix Workspace app contains a specific User-Agent.
For example, network requests with path /core/connect/authorize contains a specific User-Agent. |
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Citrix Workspace/23.05.0.36 MacOSX/13.4.0 com.citrix.receiver.nomas X1Class CWACapable
|
|
OnPrem Store with Gateway Advanced Auth
|
When users add an on-premises store with Advanced Auth configured on Gateway to Citrix Workspace app, the network requests made by Citrix Workspace app contains a specific User-Agent.
For example, network requests with requests containing |
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko), CWAWEBVIEW/23.05.0.36
|
| Custom Web Store | When a user adds a custom web store Citrix Workspace app, the network requests made by Citrix Workspace app contains a specific User-Agent. | Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Safari CWA/23.05.0.18 MacOSX/13.4.0 |
FIDO2 for password-less authentication
Citrix Workspace app for Mac supports password-less authentication using FIDO2 security keys when connecting to a cloud store or within an HDX session. FIDO2 security keys provide a seamless way for enterprise employees to authenticate to apps or desktops that support FIDO2 without entering a user name or password. This feature currently supports roaming authenticators (USB only) with PIN code and touchID. This feature is supported on macOS 12 and later versions.
For more information about FIDO2 see FIDO2 Authentication.
For information about the prerequisites and using this feature, see Local authorization and virtual authentication using FIDO2.
FIDO2-based authentication when connecting to cloud and on-premises store
Citrix Workspace app uses the user’s default browser for FIDO2 authentication (Web Authentication), when connecting to the cloud and on-premises stores. Administrators can configure the type of browser to authenticate to Citrix Workspace app. For more information on the web browser settings, see Global App Configuration service documentation.
The following settings allow you to select the type of browser that is used for authenticating an end user into Citrix Workspace app:
| Settings | Description |
|---|---|
| System | Allows you to use the user’s default browser for authentication (for example, Safari or Chrome). Authentication occurs outside Citrix Workspace app. Use this setting to support passwordless authentication. This setting tries to use the existing user session from the user’s browser. |
| SystemWithPrivateSession | This setting is similar to the System setting. Citrix Workspace app uses a private session in the browser for authentication. The browser doesn’t save authentication cookies or data. Single sign-on isn’t supported in this option. |
| Embedded | Allows you to authenticate within Citrix Workspace app. Citrix Workspace app saves the session data or cookies for single sign-on (for example, SaaS apps) when the enhanced single sign-on feature is enabled. This authentication method does not support passwordless authentications such as FIDO2. |
| EmbeddedWithPrivateSession | This setting is similar to the Embedded setting. Single sign-on isn’t supported as session data or cookies aren’t present in Citrix Workspace app. |
To push the configured settings, run the following commands using the Mobile Device Management (MDM), Global App Configuration service (GACS), or the command line interface methods:
-
Enable FIDO2 using MDM: To enable authentication through MDM, administrators must use the following setting:
<key>WebBrowserForAuthentication</key><string>System</string>
For more information on how to use MDM, see Mobile Device Management.
- Enable FIDO2 using GACS: To enable authentication through GACS, administrators must use the following setting:
{
"serviceURL": {
"url": "https://serviceURL:443"
},
"settings": {
"name": "Web browser for Authenticating into Citrix Workspace",
"description": "Allows admin to select the type of browser used for authenticating an end user into Citrix Workspace app",
"useForAppConfig": true,
"appSettings": {
"macos": [
{
"assignedTo": [
"AllUsersNoAuthentication"
],
"category": "authentication",
"settings": [
{
"name": "web browser for authentication",
"value": "SystemWithPrivateSession"
}
],
"userOverride": false
}
]
}
}
}
<!--NeedCopy-->
-
Enable FIDO2 using the command-line interface: To enable authentication using the command-line interface, administrators must run the following command:
defaults write com.citrix.receiver.nomas WebBrowserForAuthentication System
FIDO2-based authentication within an HDX session
You can configure FIDO2 Security Keys to authenticate within an HDX session. This feature currently supports roaming authenticators (USB only) with PIN code.
When you access an app or a website that supports FIDO2, a prompt appears, requesting access to the security key. If you’ve previously registered your security key with a PIN (a minimum of 4 and a maximum of 64 characters), then you must enter the PIN while signing in.
If you’ve registered your security key previously without a PIN, simply touch the security key to sign in.
This feature is enabled by default for Citrix Workspace app for 2307 and future releases. You can disable FIDO2 authentication using the Mobile Device Management (MDM) or command-line interface methods by running the following commands:
-
Disable FIDO2 based authentication using MDM: To disable this feature through MDM, administrators must use the following setting:
<key>Fido2Enabled</key><false/>
For more information on how to use MDM, see Mobile Device Management.
-
Disable FIDO2 based authentication using the command-line interface: To disable this feature, run the following command in command-line interface methods:
defaults write com.citrix.receiver.nomas Fido2Enabled -bool NO
Support for device touch ID for FIDO2 password-less authentication
Previously, Citrix Workspace app supported FIDO2 password-less authentication through the roaming authenticators (USB only) with PIN code and touch.
Starting with the version 2405, Citrix Workspace app now supports device touch ID for FIDO2 password-less authentication, enhancing the sign-in experience for users. With this feature, users can securely sign in to the store configured on the Citrix Workspace app using the device touch ID, eliminating the need for passcodes or passwords. This feature enhances both the usability and security of Citrix Workspace app for macOS users. This feature is enabled by default.
Support for Certificate-based authentication
Starting with the 2305 version, Workspace administrators can configure and enforce Azure Active Directory conditional access policies for users authenticating to Citrix Workspace app.
The following methods can be used to enable the authentication using conditional access:
- Mobile Device Management (MDM)
- Global App Configuration service (GACS)
The flag values read by Citrix Workspace app take precedence in the following order:
- Mobile Device Management (MDM)
- Global App Configuration service (GACS)
Enabling authentication using conditional access through MDM
To enable authentication using conditional access with Azure AD through MDM, admins must use the following setting:
<key>enableAAD</key>
<true/>
This setting supports Boolean values. The value is set to false by default. The default value is considered if the key value isn’t available.
For more information on how to use MDM, see Mobile Device Management.
Enabling authentication using conditional access through GACS
To enable authentication using conditional access with Azure AD through GACS, admins must use the following setting:
enable conditional AAD
For more information, see Supported settings and their values per platform for macOS in the GACS documentation.
Simplified authentication into on-premises store
Starting with the 2505 version, administrators can control the Remember password checkbox behavior in Citrix Workspace app for Mac.
Administrators can configure this feature using an MDM-based key-value pair:
key: SaveCredentials
value type: Boolean
The following logic determines the behavior of the Remember password checkbox based on StoreFront™ configuration and the presence of the SaveCredentials MDM key:
- If
SaveCredentialis not set in StoreFront:- The system displays the Remember password checkbox to the user.
- If the MDM key
SaveCredentialsis present:- If
SaveCredentials = true: The system selects the checkbox and disables it, so the user can’t change its state. - If
SaveCredentials = false: The system unchecks, disables, and locks the checkbox.
- If
- If the MDM key is not present: The StoreFront configuration solely controls the checkbox behavior.
-
If
SaveCredentialis set in StoreFront to False:- The system does not display the Remember password checkbox to the user.
- If the MDM key is set, the system still saves credentials to disk according to its value, but keeps the checkbox hidden.
Note:
- If the MDM key is present, it overrides user interaction with the checkbox.
- MDM policy manages credentials even if the UI element is hidden.
Limitations
This solution applies only to on-premises environments where Citrix Workspace app can access StoreFront directly using the user name and password authentication method exclusively.
Support for Entra ID Single Sign‑On (SSO)
Starting with version 2508, Citrix Workspace app for MAC supports Single Sign‑On (SSO) with Microsoft Entra ID.
Single Sign-On with Microsoft Entra ID
Users can sign in to Citrix Workspace app using their Microsoft Entra ID credentials and seamlessly launch Citrix Virtual Apps and Desktops with SSO, reducing repeated prompts and improving the overall sign‑in experience.
For detailed configuration instructions, see Entra ID SSO configuration guide.
Default authentication behavior
With the default authentication flow, users authenticate once during the first session launch. Subsequent sessions automatically use Single Sign‑On (SSO).
This authentication method supports both on‑premises and cloud deployments.
System browser authentication behavior
When using system browser authentication, macOS displays a modal dialog that indicates:
- The domain being authenticated.
- A prompt to proceed with authentication.
You can enable system browser authentication through MDM or GACS:
- GACS configuration: In the Authentication category, set Web Browser For Authentication to System. For details, see Supported settings and their values per platform.
- MDM configuration: Use the following setting:
<key>WebBrowserForAuthentication</key><string>System</string>
<!--NeedCopy-->
Notes:
- System browser authentication doesn’t support on‑premises stores.
- When using the
SystemWithPrivateSessionoption, the browser operates in a private session without saving cookies or data, so SSO isn’t supported.
Disable Entra ID support
To disable Entra ID support for Citrix Workspace app for MAC, run the following command:
defaults write com.citrix.receiver.nomas UseLegacyTermsrvResourceUri -bool YES
<!--NeedCopy-->
In this article
- Enhancing Citrix® security with pre-populated user name
- Mandate end users to authenticate and access apps and desktops through native app
- Enhancements to the smart card reader authentication
- Support for fast smart card
- Smart card
- Conditional Access with Azure Active Directory
- User-Agent
- FIDO2 for password-less authentication
- Support for Certificate-based authentication
- Simplified authentication into on-premises store
- Support for Entra ID Single Sign‑On (SSO)